Method and device for browser to access smart key equipment
A technology of intelligent key device and browser, applied in the field of communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
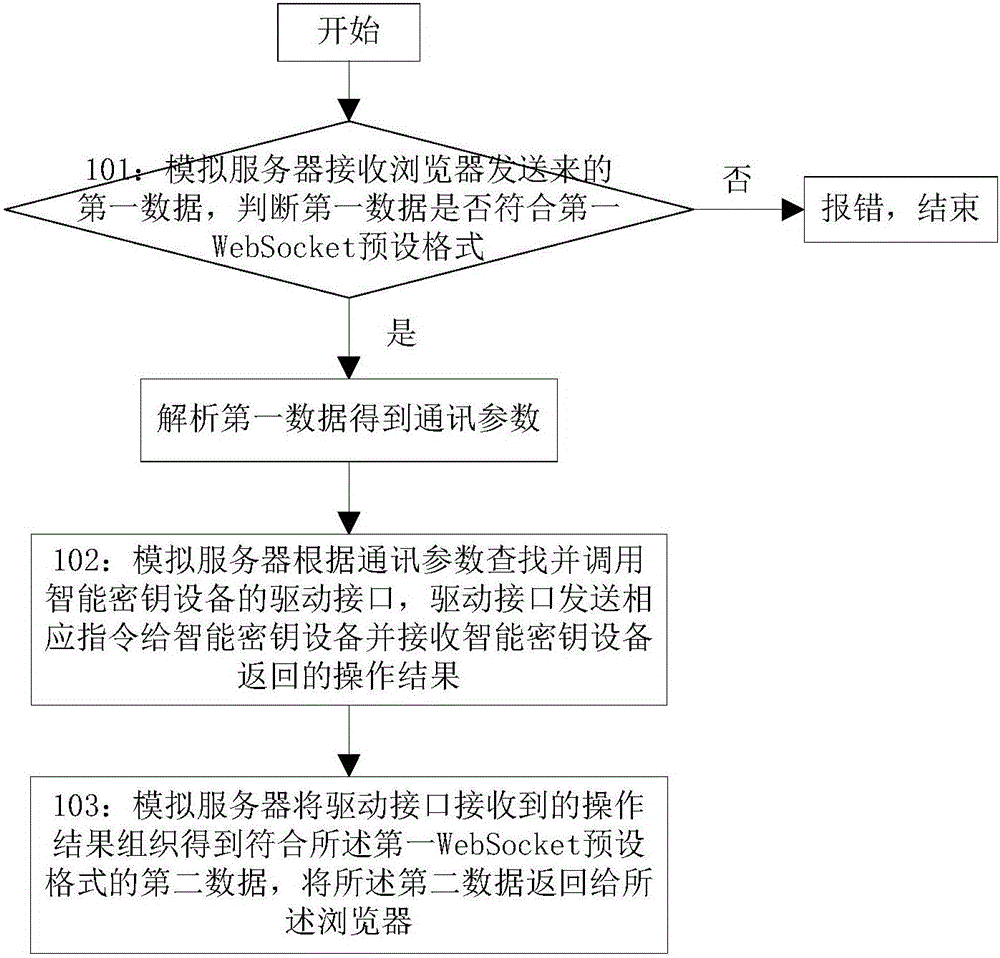
[0114] Embodiment 1 of the present invention provides a method for implementing browser access to smart key devices, such as figure 1 shown, including:
[0115] Step 101: The simulated server receives the first data sent by the browser, and judges whether the first data conforms to the first WebSocket preset format, and if so, parses the first data to obtain communication parameters, and executes step 102, otherwise reports an error and ends;
[0116] In this embodiment, before step 101, it also includes:
[0117] Step a: Create a WebSocket connection between the simulated server and the browser;
[0118] In this embodiment, step a specifically includes:
[0119] Step a1: The simulated server receives the connection request sent by the browser, and judges whether the connection request conforms to the second WebSocket preset format. 2. The connection request response data in the preset format of WebSocket, otherwise an error will be reported and the end will be completed; ...
Embodiment 2
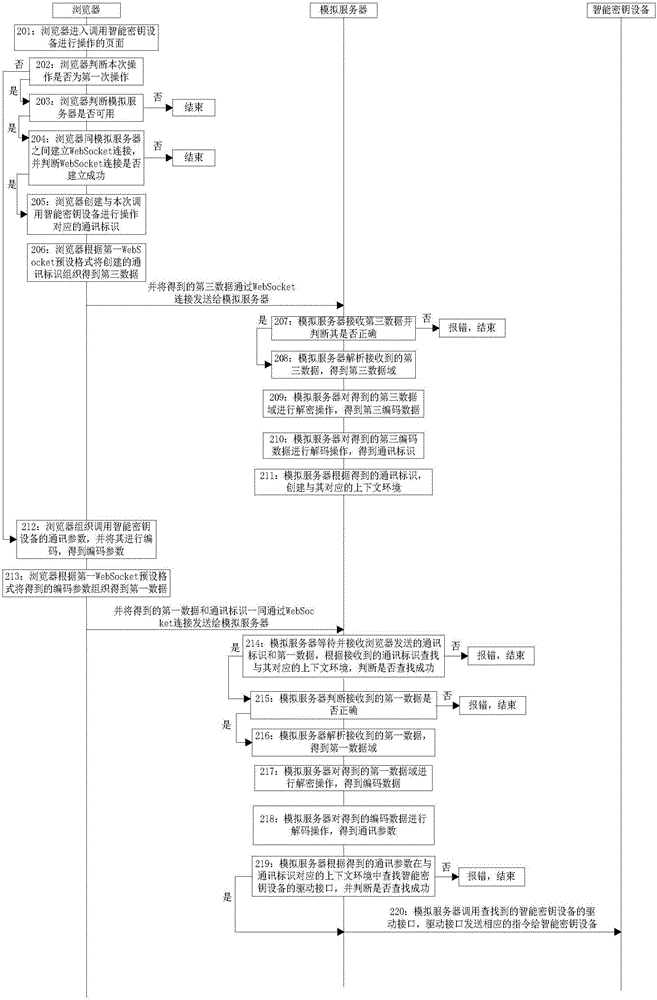
[0164] Embodiment 2 of the present invention provides a method for implementing a browser to access a smart key device, such as figure 2 and image 3 shown, including:
[0165] Step 201: the browser enters the page for invoking the smart key device for operation;
[0166] For example: online banking login page, password modification page, signature page, etc.;
[0167] Preferably, in this embodiment, the acquisition of the serial number of the smart key device is taken as an example for description, and the browser enters the page for obtaining the serial number of the smart key device.
[0168] Step 202: The browser judges whether this operation is the first operation, if so, execute step 203, otherwise execute step 212;
[0169] Specifically, the browser judges whether the WebSocket connection flag is set, and if so, confirms that this operation is not the first operation, otherwise confirms that this operation is the first operation;
[0170] Preferably, in this embodi...
Embodiment 3
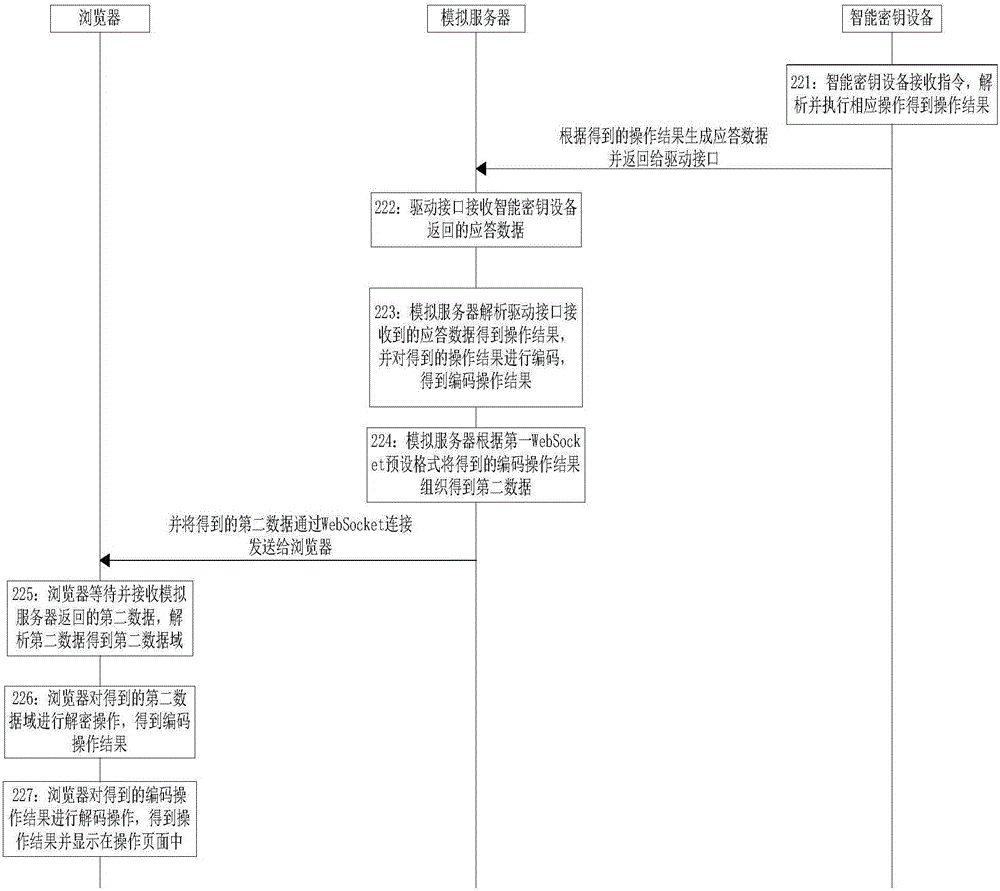
[0270] Embodiment 3 of the present invention provides a workflow of simulating the server in the implementation method of browser access to the smart key device. In this embodiment, the serial number of the smart key device is taken as an example for illustration. When the establishment is successful, the browser creates the communication identification related to the access to the smart key device, and organizes the created communication identification according to the first WebSocket preset format to obtain the third data, and sends the obtained third data to the mock server; Figure 4 As shown, the mock server does the following:
[0271] Step 301: The simulated server waits for and receives the third data sent by the browser, and after receiving the third data, executes Step 302;
[0272] Preferably, in this embodiment, the received third data is: 81 9c 9b b8 cc 5c e0 9a 98 33f0 dd a2 7e a1 9a 8d 18 a8 8c 8a 1f ac 8c fe 6f af 88 8e 18 df 8b ee 21 .
[0273] Step 302: th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com