User behavior control method and system, and safe desktop
A control method and control system technology, applied in the Internet field, can solve problems such as affecting the normal learning of minors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
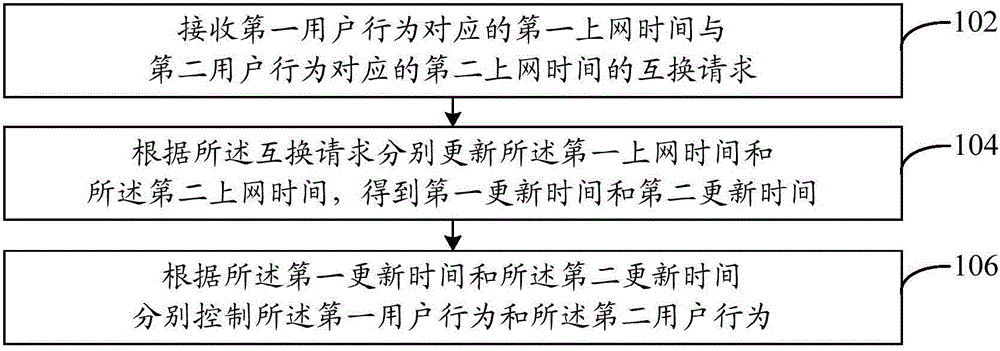
[0106] refer to figure 1 , shows a schematic flowchart of steps of a user behavior control method in Embodiment 1 of the present invention. In this embodiment, the user behavior control method includes:
[0107] Step 102, receiving a request for exchanging the first online time corresponding to the first user behavior with the second online time corresponding to the second user behavior.
[0108] With the development of the Internet, users can accomplish more and more things through the Internet, such as online learning, online office, browsing various web pages, playing games, listening to songs and watching movies, etc. through the Internet. The activities performed by users through the Internet can be defined as user behaviors.
[0109] In this embodiment, user behaviors can be divided into two categories: first user behaviors and second user behaviors. Among them, activities such as online learning, online office, and searching for work or study materials through the In...
Embodiment 2
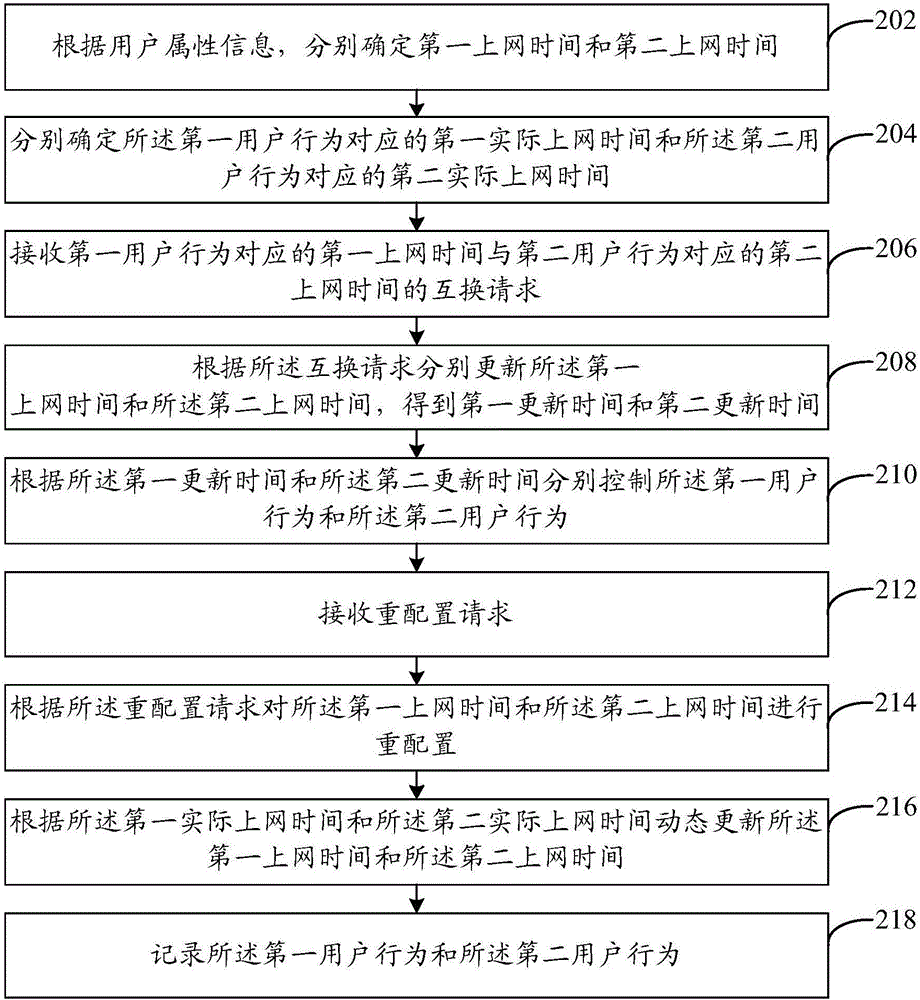
[0120] refer to figure 2 , which shows a schematic flowchart of steps of a user behavior control method in Embodiment 2 of the present invention. In this embodiment, the user behavior control method can be applied to a third-party desktop. Wherein, the third-party desktop has a management mode and at least one managed mode, and the management mode can be used to control the first user behavior and the second user behavior corresponding to the at least one managed mode.
[0121] Wherein, the user behavior control method includes:
[0122] Step 202, respectively determine the first online time and the second online time according to the user attribute information.
[0123] In this embodiment, the first surfing time may specifically be the surfing time corresponding to the first user behavior, and the second surfing time may specifically be the surfing time corresponding to the second user behavior. Wherein, the first user behavior includes but not limited to: work and / or stu...
Embodiment 3
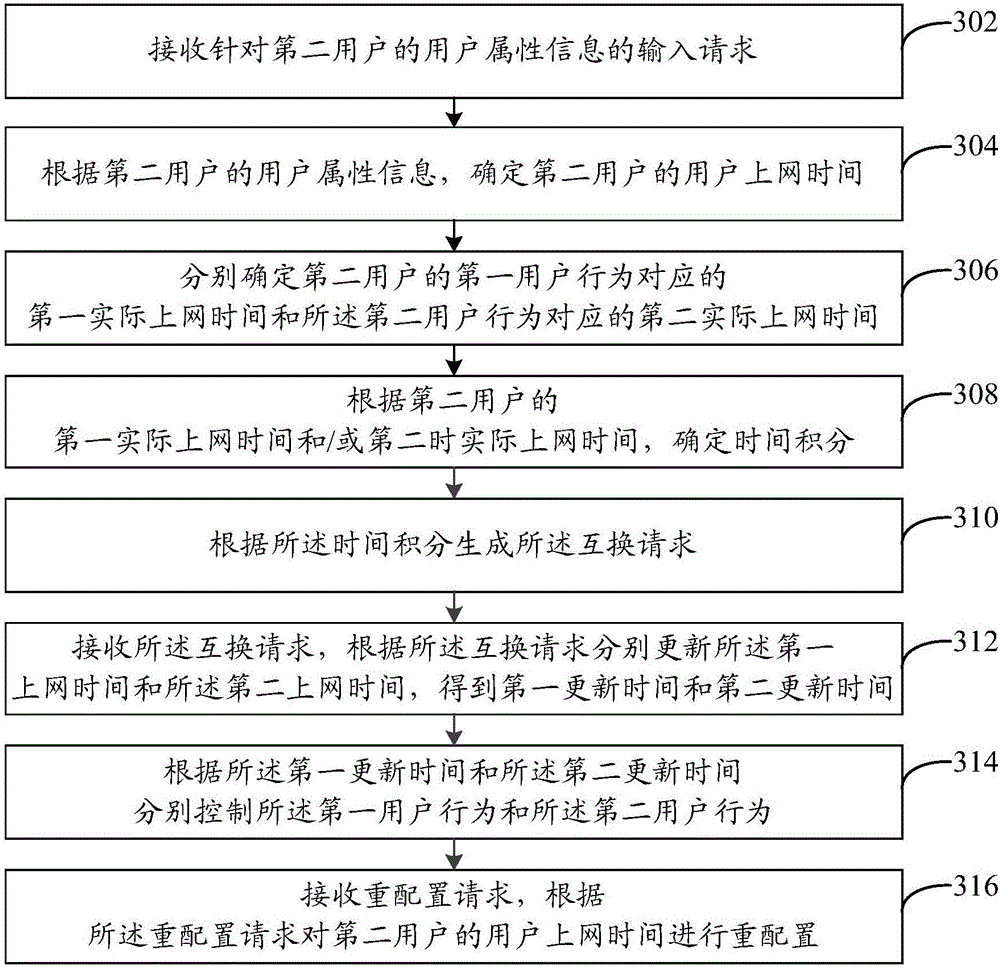
[0169] In combination with the foregoing embodiments, this embodiment uses a specific example to describe the user behavior control method in detail. In this embodiment, the user behavior control method can be specifically implemented through a third-party desktop set in the terminal, the third-party desktop includes a control mode and a controlled mode, and its specific application scenario is the first user-the first user Two users, the first user may be a parent, and the second user may be a child.
[0170] refer to image 3 , which shows a schematic flowchart of steps of a user behavior control method in Embodiment 3 of the present invention. In this embodiment, the user behavior control method may specifically include:
[0171] Step 302, receiving an input request for user attribute information of a second user.
[0172] In this embodiment, the first user can log in to the management and control mode of the third-party desktop by inputting a login password, and in the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com