Blacklist processing method and system
A processing method and blacklist technology, applied in the computer field, can solve problems such as the lack of blacklist maintenance and application standards in the system, chaotic blacklist management, and inability to realize blacklist joint defense and joint control.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
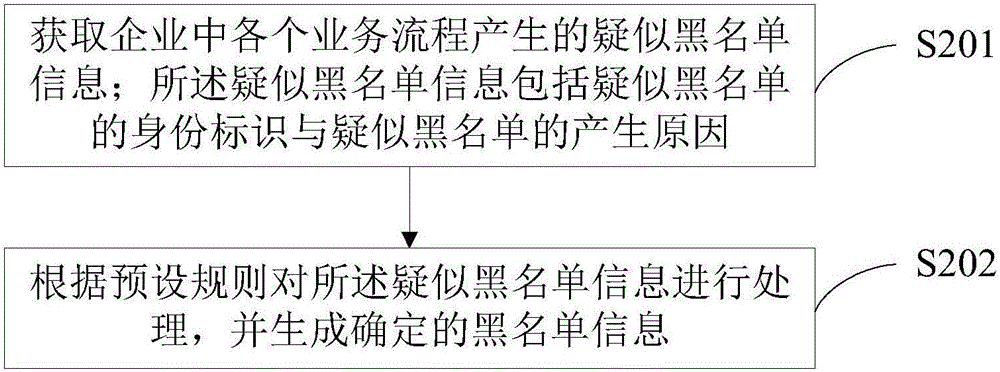
[0083] Deploy a copy of the local blacklist in the card account and channel business processing system of the bank. The copy of the local blacklist stores blacklist information. The relevant business processing system enables the blacklist information of the local blacklist copy to be updated in quasi-real time with the update of the blacklist shared database.
[0084] In the bank's card account business process, for business processes with relatively simple business links and processing methods, when processing specific businesses, access the local blacklist copy to check whether the current customer is blacklisted, if the customer is blacklisted, then according to The business process uses corresponding processing methods to process the current business, and the processing methods are denial, execution control or suspension, and do not need to access the blacklist shared database. This method of applying the blacklist in the enterprise simplifies the business processing proc...
example 2
[0086]In the bank's card account business process, when processing specific businesses, access the copy of the local blacklist to check whether the current customer is blacklisted, if the customer is blacklisted, access the blacklist shared database through the blacklist management system, and according to Describe the customer's identity and the processing method corresponding to the business link query, and process the current business according to the processing method. In the specific business of an enterprise, the probability of a customer being blacklisted is very small. If you visit the blacklist shared database every time to judge whether the current customer is blacklisted, the workload of the blacklist shared database will be increased, and the business processing efficiency will be reduced. Establish a copy of the local blacklist, and judge whether the current customer is blacklisted by accessing the copy of the local blacklist, which reduces the workload of the blac...
example 3
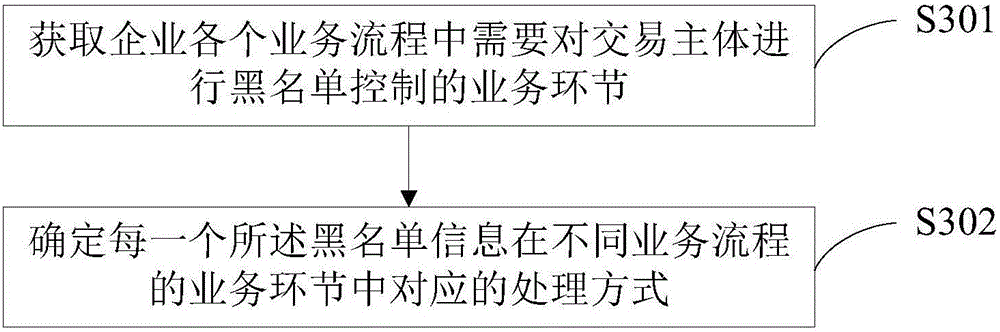
[0088] In the customer business process of the bank, regardless of whether the customer is blacklisted or not when processing customer business, relevant personnel will access the customer information system, and inputting the relevant identity will return whether the customer is blacklisted. Among them, the customer An information system is a management information system in an enterprise.
[0089] In the specific business, it is necessary to check whether the transaction subject is blacklisted multiple times, and for transactions with high response time requirements, access the blacklist shared database through the blacklist management system, and query the customer's status in all business links according to the current customer's identity The processing method is to establish a local cache of the search results, and establish a mapping relationship between the application transaction code and the business link and processing method. The application transaction code is a num...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com