Method for realization and service for trusted password module on ARM platform
A cryptographic module and service method technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of insufficient consideration of computing resources and hardware platform scalability, and cannot meet the needs of easy expansion of mobile devices and efficient and reliable services, etc., to achieve strong scalability performance, improve efficiency, and ensure safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
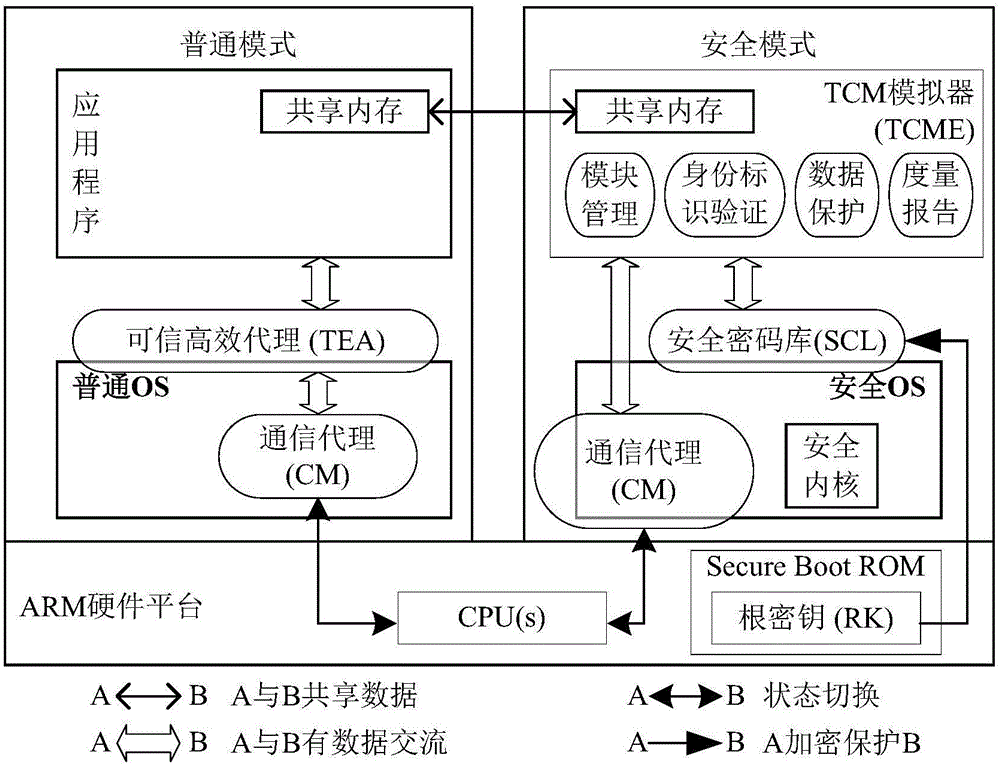
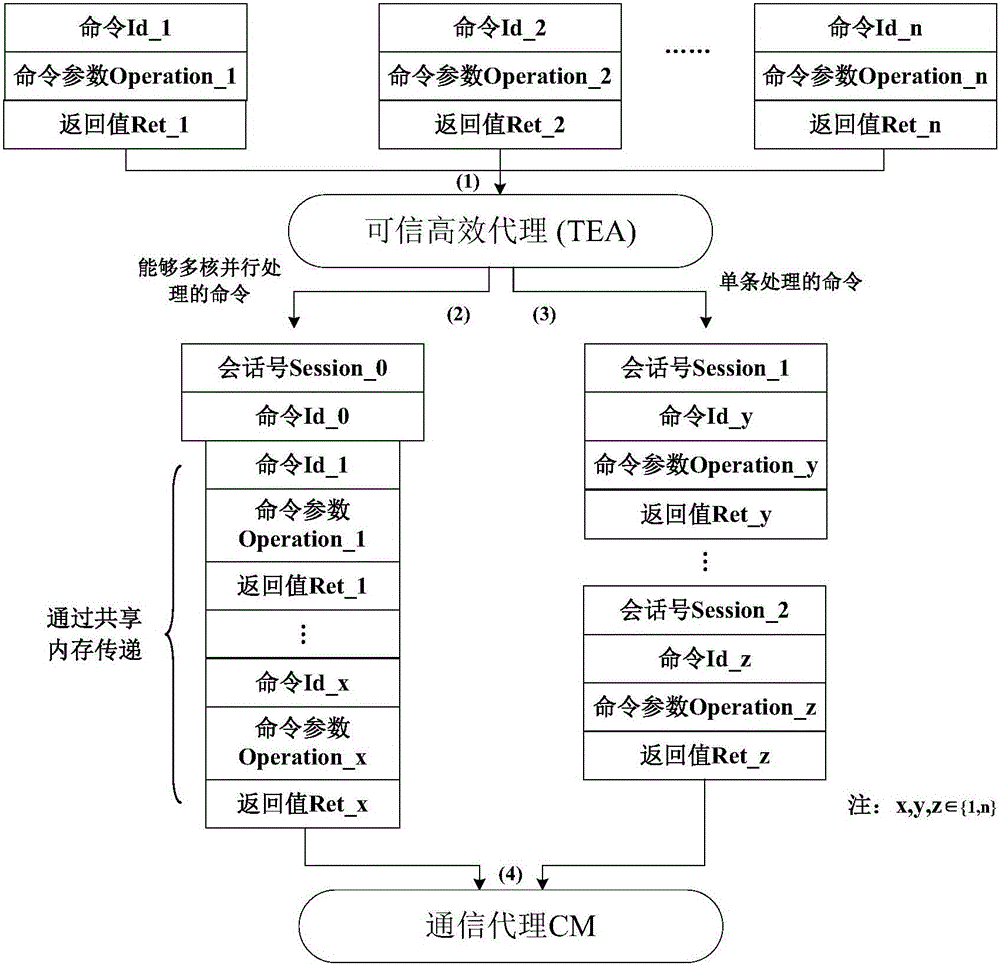
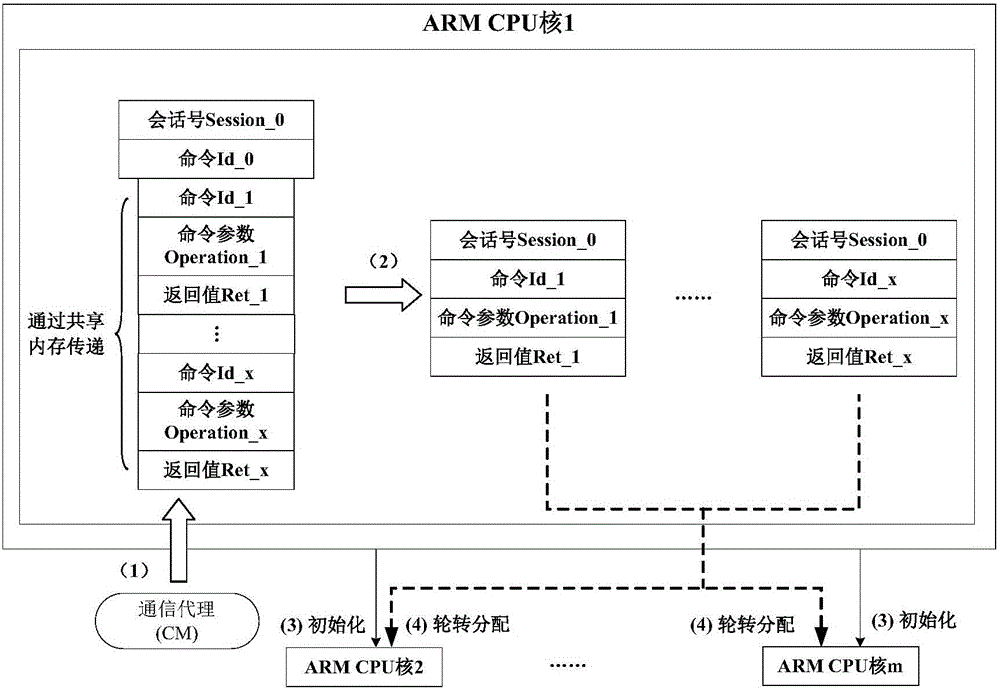
[0020] The present invention is based on the TrustZone technology of the ARM processor, and provides a method for realizing trusted cryptographic modules and efficient services through software simulation in the "secure world", such as figure 1 As shown: the trusted efficient agent TEA receives trusted service requests from applications, preprocesses these requests to form trusted service request packets that can be processed by multiple cores in parallel or single core, TEA calls the communication agent CM and The request packet is passed to the CM; the CM saves and switches the main processing CPU core and the working status of the entire platform, and forwards the trusted service request to the trusted cryptographic module emulator TCME, and TCME performs module management, identity identification and verification, and data protection according to the request type Multi-core parallel or single-core processing of the measurement report; finally, the secure cryptographic libra...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap