Malicious application identification method and device
A malicious application and identification method technology, applied in the field of malicious application identification method and device, can solve the problems of high technical implementation and maintenance costs, low identification accuracy, etc., to improve accuracy, comprehensive and more reliable data, and reduce development and maintenance costs and time cost effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
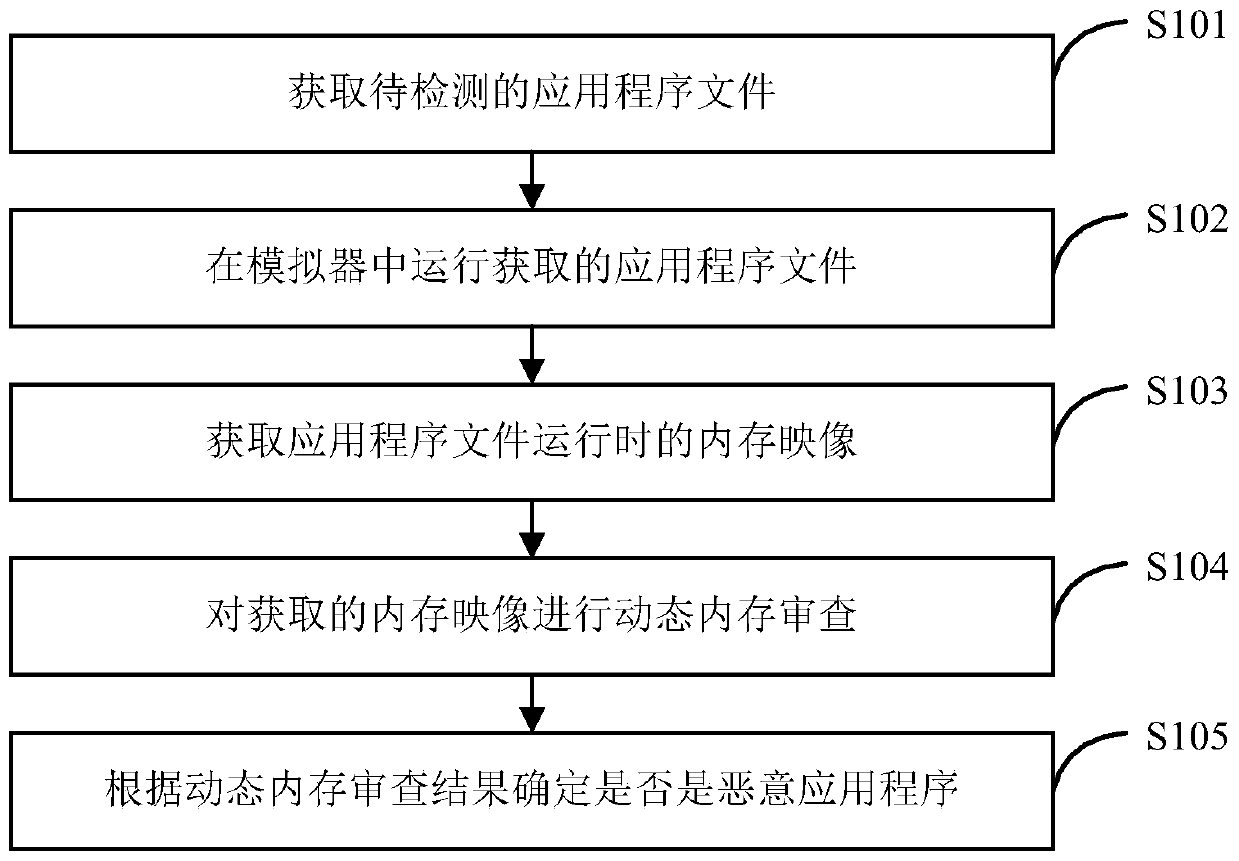
[0076] Embodiment 1 of the present invention provides a specific implementation method for the above-mentioned malicious application identification, the process of which is as follows image 3 shown, including the following steps:
[0077] Step S301: Obtain the application program file to be detected.
[0078] Step S302: Run the obtained application program file in the emulator.
[0079] Step S303: Obtain the memory image when the application file is running.
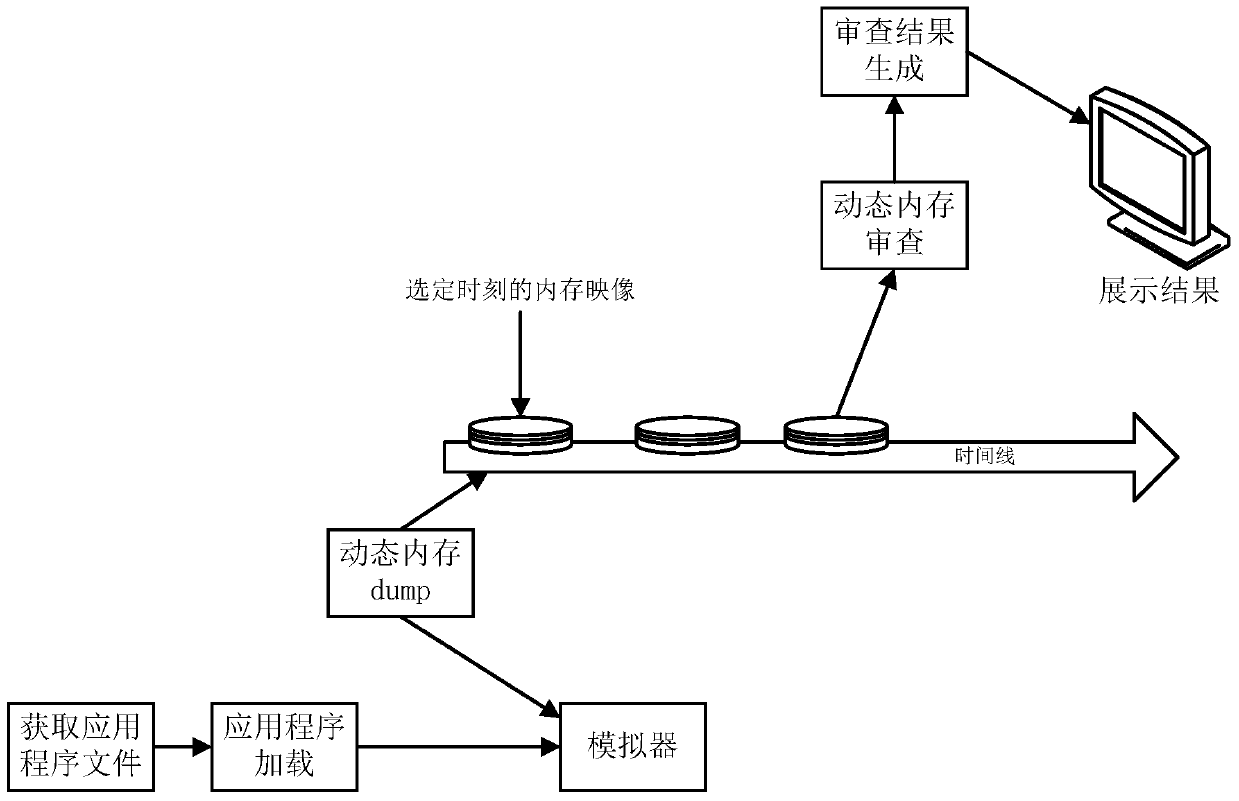
[0080] When obtaining the memory image, you can use the preset script plug-in to define the memory mapping storage address of the Dalvik virtual machine-related variables, such as common static variables, class objects, etc., so as to facilitate variable acquisition and positioning during processing (ie Where can the variables required for analysis be obtained), the script written can obtain the memory address offset of the global variable DvmGlobals object, so as to obtain the memory image of the application file fro...
Embodiment 2
[0091] Embodiment 2 of the present invention provides a specific implementation method for the above-mentioned identification of malicious applications, the process of which is as follows Figure 4 shown, including the following steps:
[0092] Step S401: Obtain the application program file to be detected.
[0093] Step S402: Run the obtained application program file in the emulator.
[0094] Step S403: Obtain the memory image of the running application file.
[0095] Step S404: Check whether the data transmitted by the application program contains sensitive information according to the dynamic information processed by the memory contained in the acquired memory image of the application program file.
[0096] For the inspection of the dynamic memory image, it can be inspected from at least one selected dimension, for example: the dimension of whether sensitive information is contained in the data transmitted from the application. Information in the transmitted data containe...
Embodiment 3
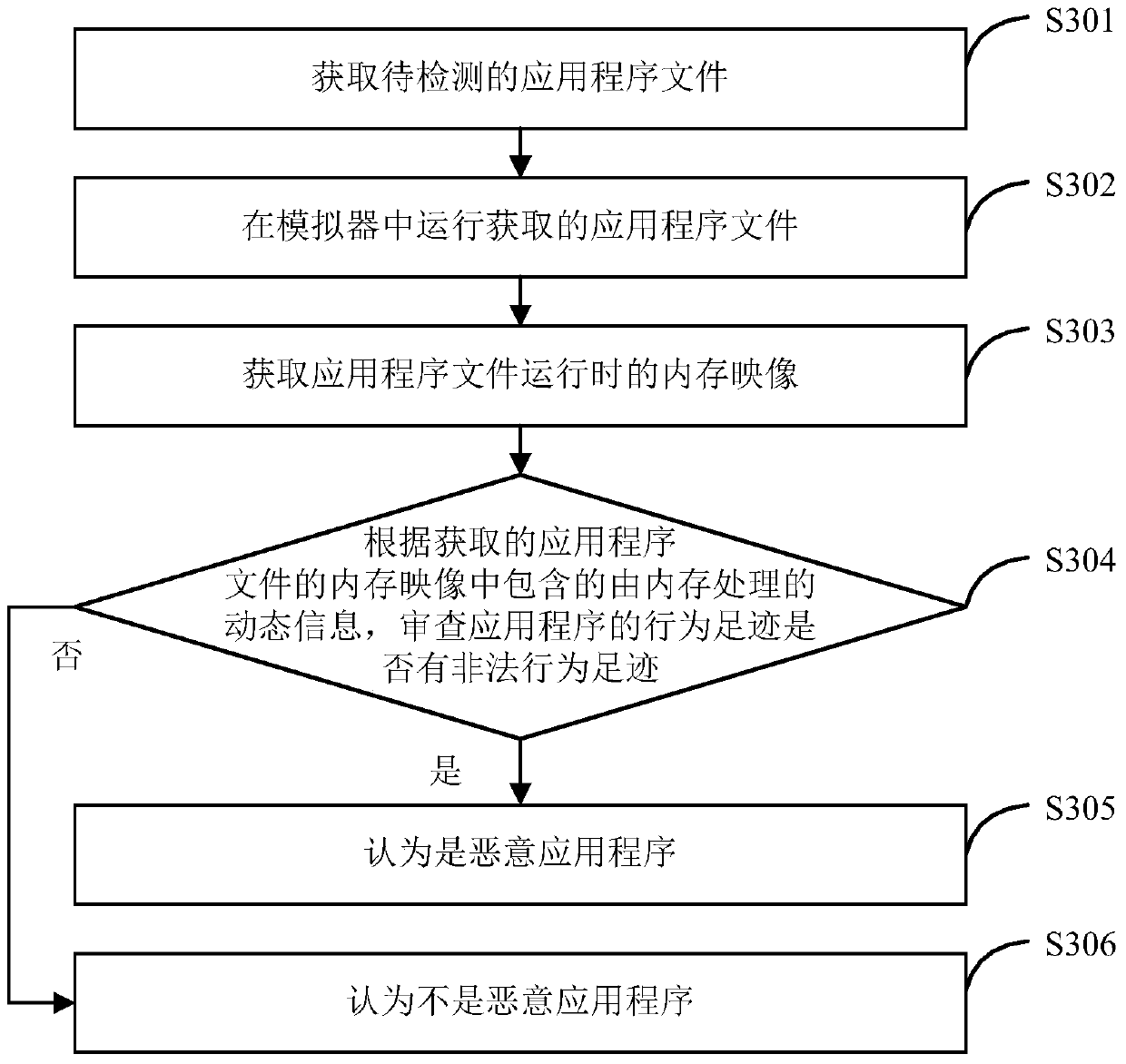
[0103] Embodiment 3 of the present invention provides a specific implementation method for the above-mentioned identification of malicious applications, the process of which is as follows Figure 5 shown, including the following steps:
[0104] Step S501: Obtain the application program file to be detected.
[0105] Step S502: Run the obtained application program file in the emulator.
[0106] Step S503: Obtain the memory image of the application file running.
[0107] Step S504: The acquired dynamic information contained in the memory image of the application file is processed by the memory.
[0108] Get the dynamic information contained in the memory image of the application file, which may include the behavior footprint of the application, the data transmitted by the application, and so on.
[0109] Step S505: Check whether the behavior footprint of the application program has any illegal behavior footprint. If yes, execute step S508; if not, execute step S506 for furthe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com