Method and device for detecting malicious code contained in non-executable file
A technique for malicious code, execution of files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
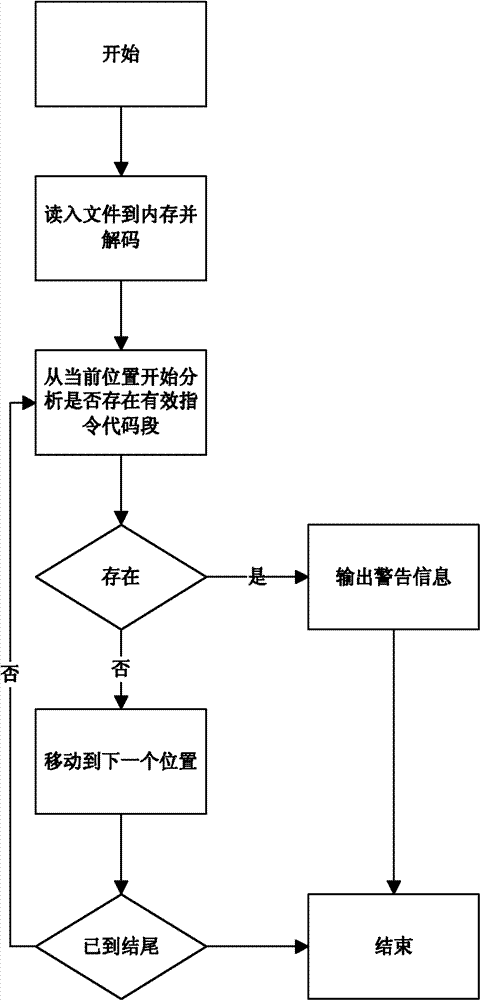
[0039] Embodiment, referring to the accompanying drawings, a detection method containing malicious code in a non-executable file of the present invention, comprising the steps:
[0040] Open the checked file, read and decode the payload data into memory;
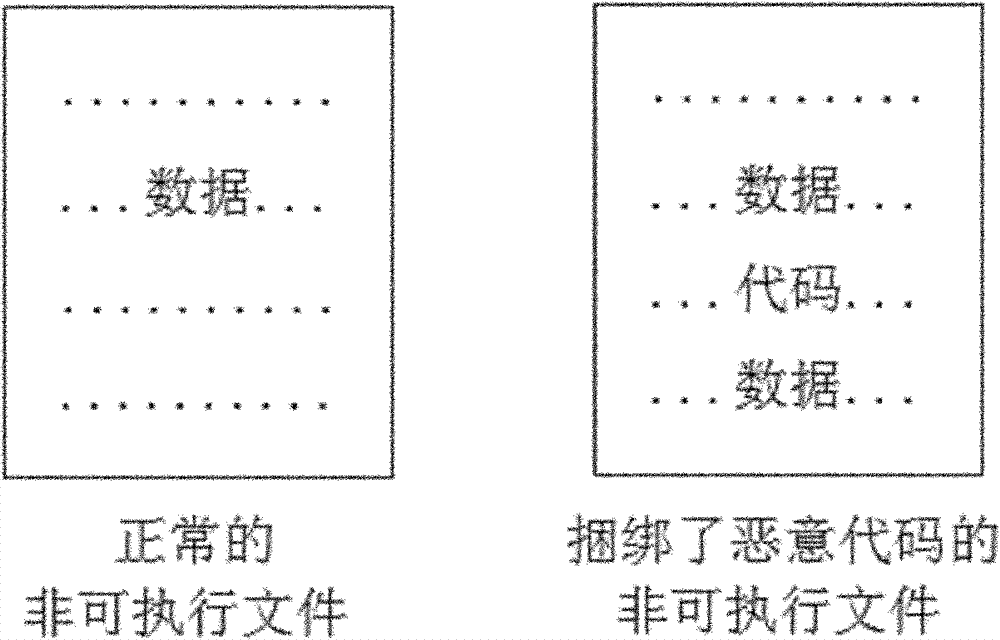
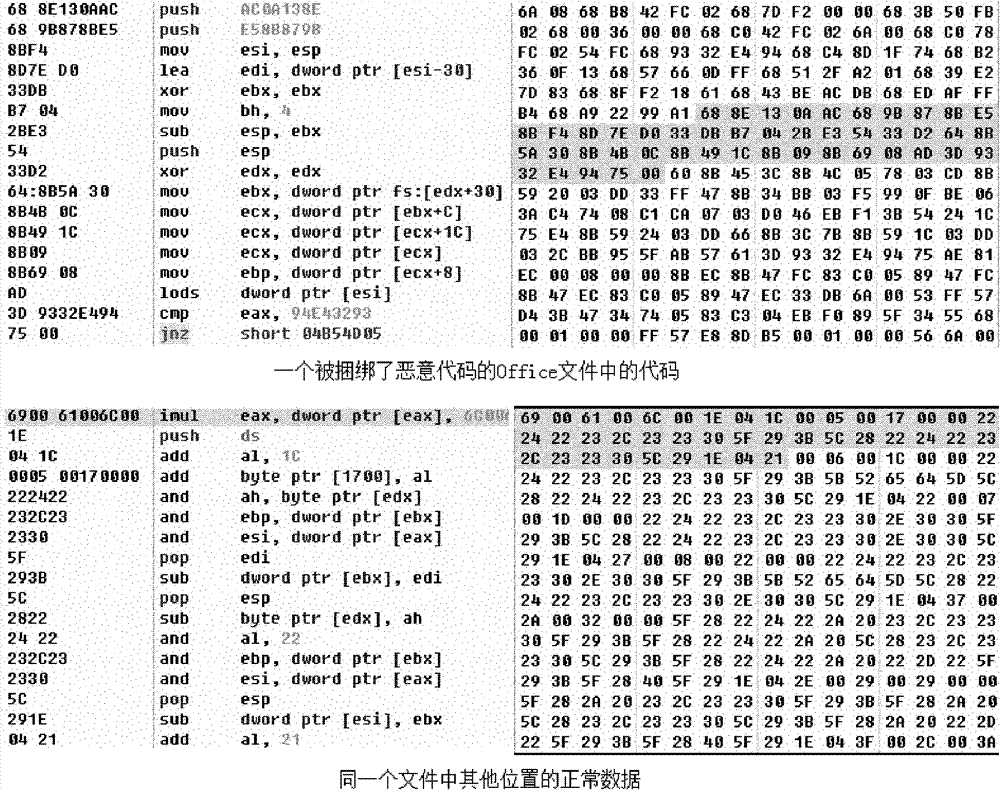
[0041] From the beginning of the data, check whether the data contains valid CPU instruction code blocks. If a certain amount of data at the current position contains valid CPU instruction code blocks, the file is considered to contain malicious code;
[0042] If the position data does not contain a valid CPU instruction code block, then move to the next data position to continue checking;
[0043] If no valid CPU instruction code block is found after checking all the data, it is considered that the file does not contain malicious code.
[0044] figure 1 It is a flow chart of the detection steps of the present invention;
[0045]First, read the file into the memory and decode it; then, analyze whether there is a valid ins...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com