Identity security verification review method
A technology of security verification and identity authentication, applied in the fields of identity security verification and review, information and data security, it can solve the problems of low security, high access cost, adverse effects of private network security, etc., and achieve high security and convenient operation. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
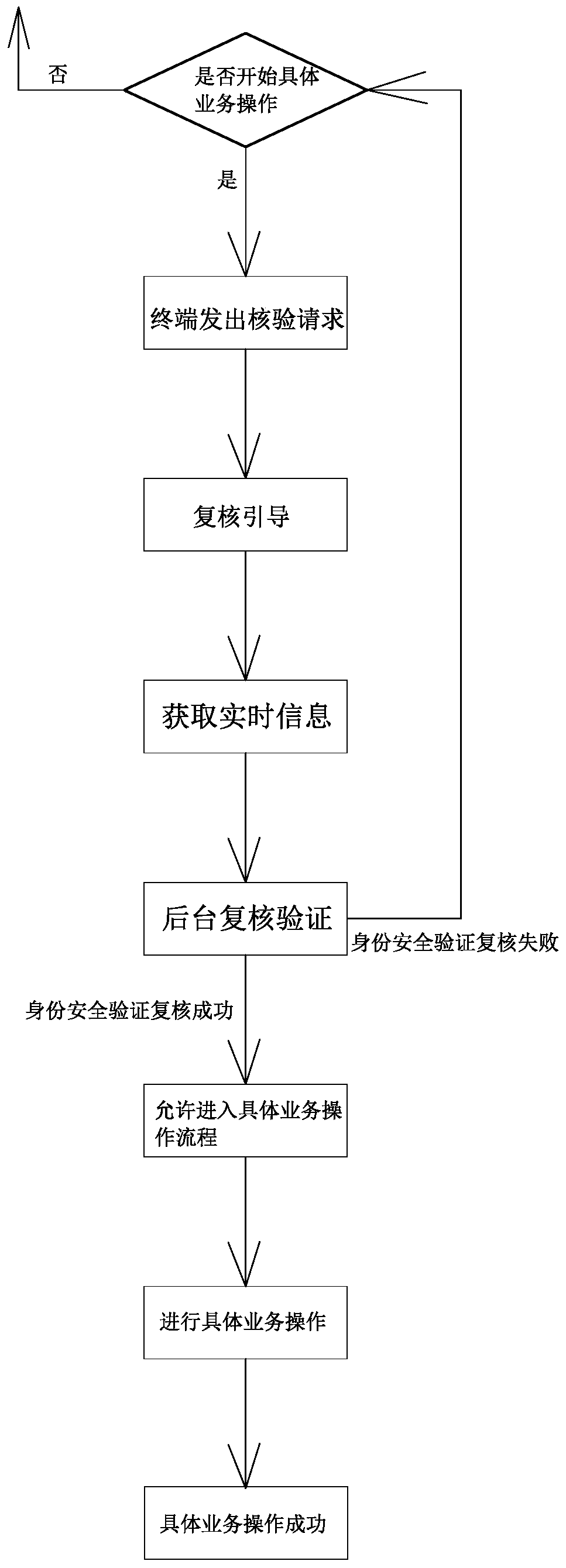
[0039] Such as figure 1 and 3 As shown, this identity security verification review method includes the following steps:
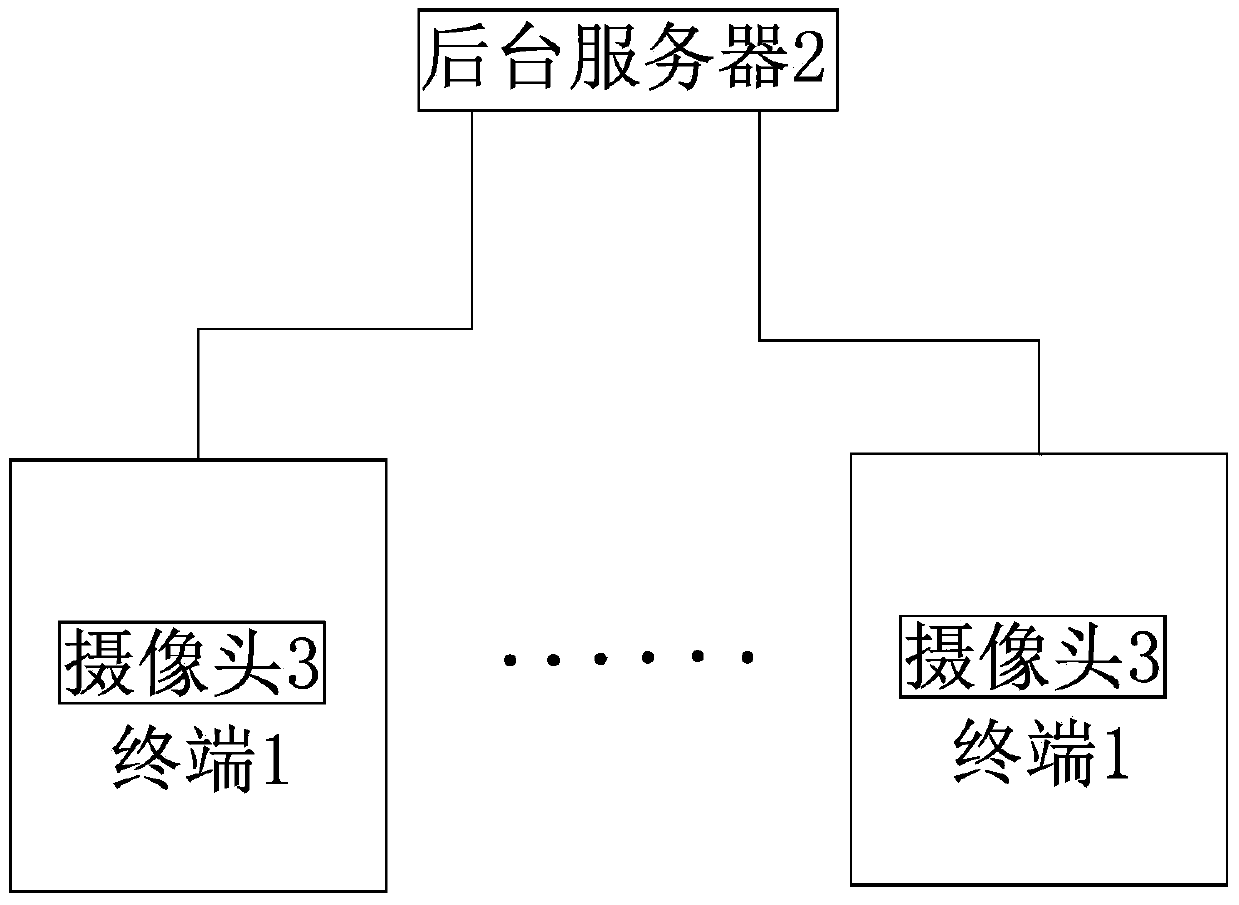
[0040] A. Review guidance: the background server 2 generates review guidance information and sends it to the corresponding terminal 1 to guide the user to place the verification document 4 to be verified on the terminal 1 in the form required by the review guidance information according to the review guidance information. Real-time collection of information that can be collected Area; B. Obtain real-time information: Terminal 1 collects real-time review and verification information containing the information of the document to be verified and the real-time form information of the document to be verified, and transmits the real-time review and verification information to the background server 2; C. Background review and verification: background server 2 According to the real-time review and verification information and review guidance information, verify th...
Embodiment 2
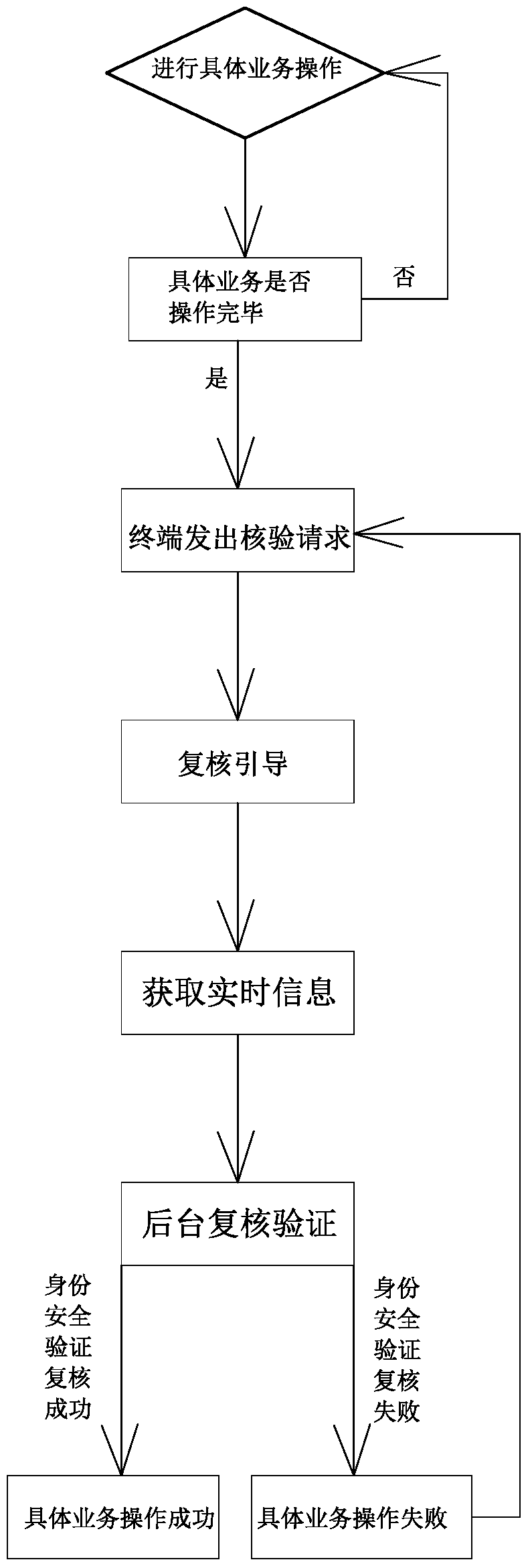
[0071] Such as figure 2 As shown, in this embodiment, the identity security verification review is performed when the specific business operation reaches the last step. At this time, the terminal 1 sends a verification request to the background server 2, and the background server 2 randomly generates the verification request after receiving the verification request from the terminal 1. Review the boot information. Then verify the identity security verification review. If the identity security verification is successful, the specific business operation is successful; if the identity security verification fails, the specific business operation fails. The rest are similar to those in Example 1, and will not be described in detail.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com