Mobile cloud data graded access control method based on credibility of mobile terminals
A mobile terminal and access control technology, applied in wireless communication, electrical components, transmission systems, etc., can solve problems such as low storage capacity and limited computing power of mobile terminals, achieve flexible classification and authority changes, and overcome cloud trusted access. into the problem and overcome the effect of limited computing power
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
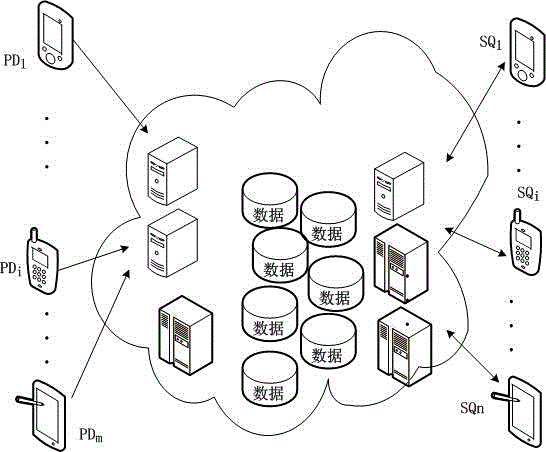
[0020] Such as figure 1 As shown, there are m mobile terminals in the system to provide data respectively denoted as PD i ,i=1,2,3,...m, the corresponding reliability is β_PD i ,i=1,2,3,..., the data provided by each mobile terminal is encrypted and stored in the cloud, and there are n mobile terminals making data access requests to the cloud, expressed as Its corresponding reliability is β_SQ i ,i=1,2,3,..., after using the data in the cloud, it evaluates the credit of the data, expressed as F i , i=1, 2, 3, . . .
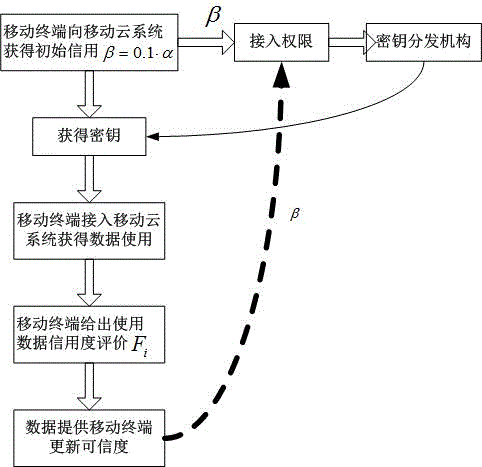
[0021] Such as figure 2 As shown, the mobile cloud data hierarchical access control method based on mobile terminal trustworthiness, it comprises the following steps:
[0022] It is assumed that each mobile terminal has...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com