Cellular automata and chaotic mapping-based digital image encryption method and decryption method thereof
A technology of chaotic mapping and encryption method, which is applied in image data processing, image data processing, instruments, etc., and can solve problems such as not satisfying real-time performance, potential safety hazards, and increasing time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
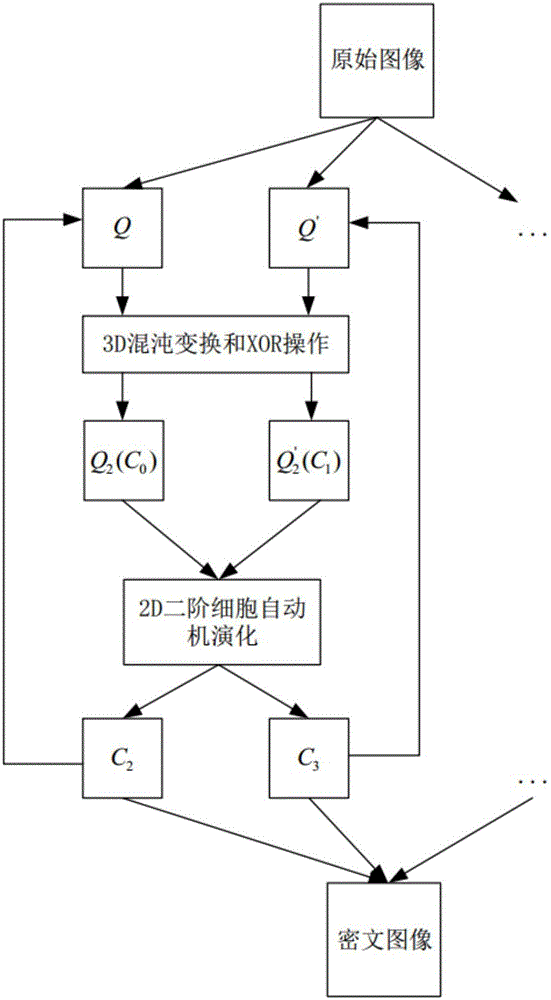
[0061] Such as figure 1 , a digital image encryption method based on cellular automata and chaotic maps, its basic process is:
[0062] (1) Key generation stage;
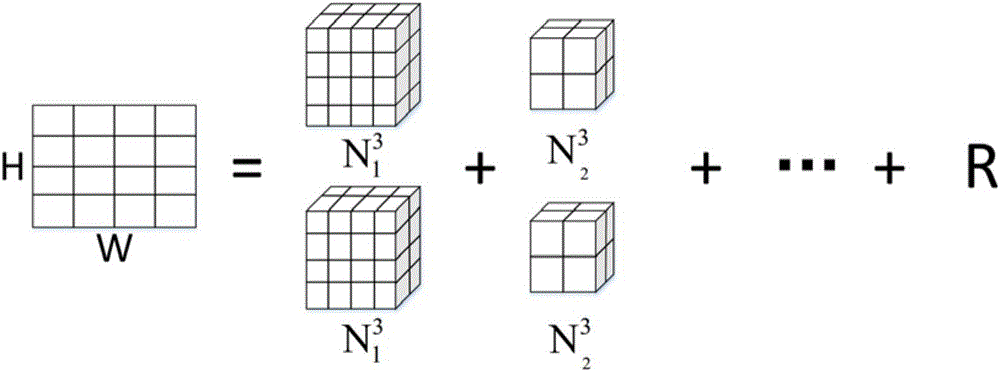
[0063] (2) Image preprocessing stage;
[0064] (3) Pixel position scrambling stage;
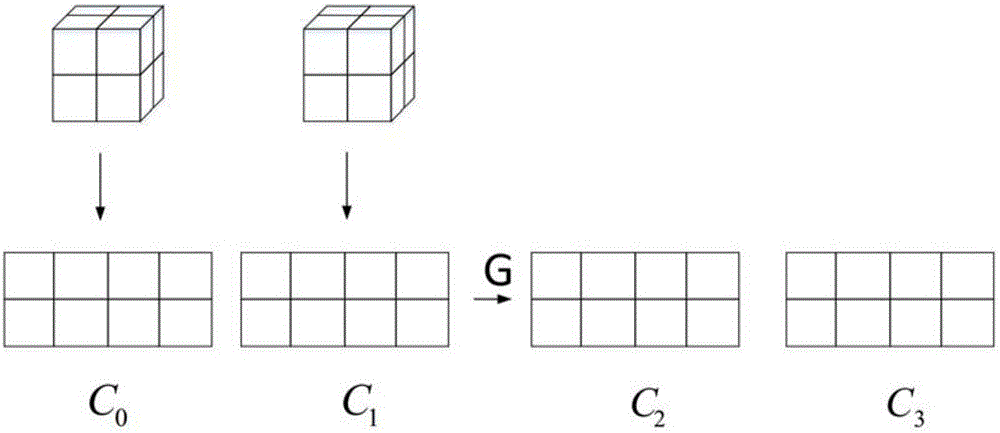
[0065] (4) The evolution stage of cellular automata;
[0066] (5) Judging the condition of the number of iterations according to step (4), and outputting the result.
[0067] The steps (1) to (5) are described in detail below:
[0068] The step of described step (1) is as follows:
[0069] key generation stage. A binary bit stream with a length of 288 bits is selected as the key, which is used to generate the coefficients of the 3D chaotic map, the number of iterations and the rule number of the evolution rules of cellular automata. The key generation algorithm is as follows: the first 7×32 bits, each 32 bits represent an integer, which are respectively used as the six coefficients of the 3D chaotic map (a x a y a z b x ...
Embodiment 2
[0110] Such as Figure 4 , the basic process of a confidential method of digital image encryption method based on cellular automata and chaotic maps is:
[0111] (1) Key generation stage;
[0112] (2) Image preprocessing stage;
[0113] (3) Pixel reverse iteration stage;
[0114] (4) Chaos map reverse operation stage;
[0115] (5) Steps (3) and (4) are executed cyclically, the condition of the number of iterations is judged, and the result is output.
[0116] The steps (1) to (5) are described in detail below:
[0117] The step of described step (1) is as follows:
[0118] key generation stage. Using the same 288-bit binary stream key key as in the encryption stage, the parameters of the 3D chaotic map and the rule numbers of the 2D second-order cellular automata are generated in the same way as in the encryption stage.
[0119] The step of described step (2) is as follows:
[0120] Image preprocessing stage. The ciphertext image is chunked by preprocessing the image ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com