Cloud-based secure instant messaging method and system
A secure and cloud-based technology, applied in the field of data security, can solve the problems of difficulty in fully ensuring the security of the entire communication chain, uncontrolled core keys, and not managed by users, achieving strong heterogeneity, high security, and compatibility. good effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0101] Micro police instant messaging system
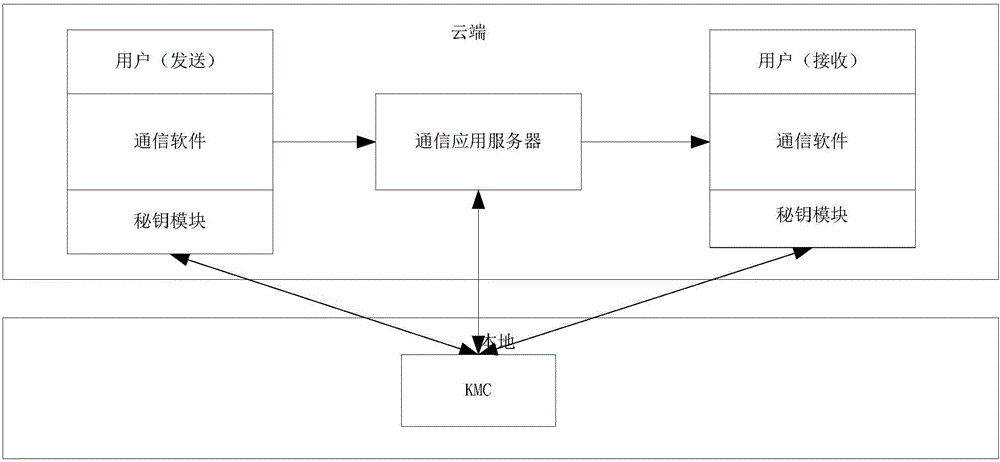
[0102] Through the micro-police app, data sharing and information exchange among police officers can be realized. However, due to the implementation based on the cloud platform, point-to-point data transmission and data storage security on the cloud platform have been greatly challenged.
[0103] Technical implementation: The overall security technical implementation is divided into three parts:
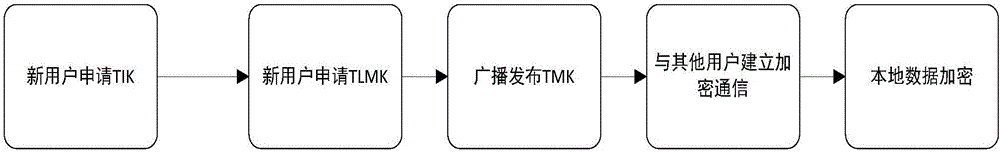
[0104] 1. User initialization process. It mainly realizes the security requirements for users to obtain TIK and TLMK.
[0105] 2. Secure communication process. It mainly realizes the security requirements for users to obtain TMK and TAK.
[0106] 3. Data encryption storage process. It mainly realizes the security requirements of users to encrypt data through TLMK.
[0107] The specific implementation process is similar to the above, and will not be repeated here.
Embodiment 2
[0109] Encrypted Call Service of Telecom Operators
[0110] 1. Card making business
[0111] 1) Insert the TF card into the KMC;
[0112] 2) KMC burns the key pair into the TF card;
[0113]3) The ID and key pair of the TF card are stored in the KMC key store, and the key is generated but not activated at this time;
[0114] 4) The TF card storing the key is completed;
[0115] 5) Transfer the TF card to the card issuing center (business hall);
[0116] 2. Card issuance business
[0117] 1) The card issuing center hands over the TF card to the user;
[0118] 2) Insert the TF card into the mobile phone;
[0119] 3) Send SMS to activate encryption service;
[0120] 4) Activate the key stored in this TF card;
[0121] 5) Card issuance is complete.
[0122] 3. Encrypted video call service
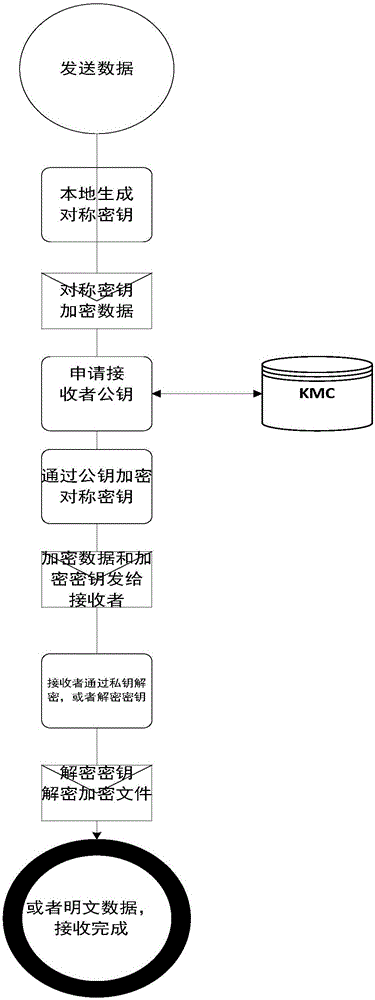
[0123] 1) Zhang San sends a data packet;
[0124] 2) Encrypt the data through the terminal session key;
[0125] 3) Li Si receives the encrypted data packet;
[0126] 4) Decrypt th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com