Method and device for realizing built-in rsa key operation by calling cipher card by jce
A password card and key technology, applied in the field of information security, can solve problems such as being easily stolen, and achieve the effect of simple and convenient operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] In order to make the object, technical solution and advantages of the present invention clearer, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0065] It should be noted that the subject of execution of the method in this embodiment is a terminal device, and the terminal may be a mobile phone, a tablet computer, a PDA, a notebook or a desktop computer, etc. Of course, it may also be other devices with similar functions. This embodiment is not limited.
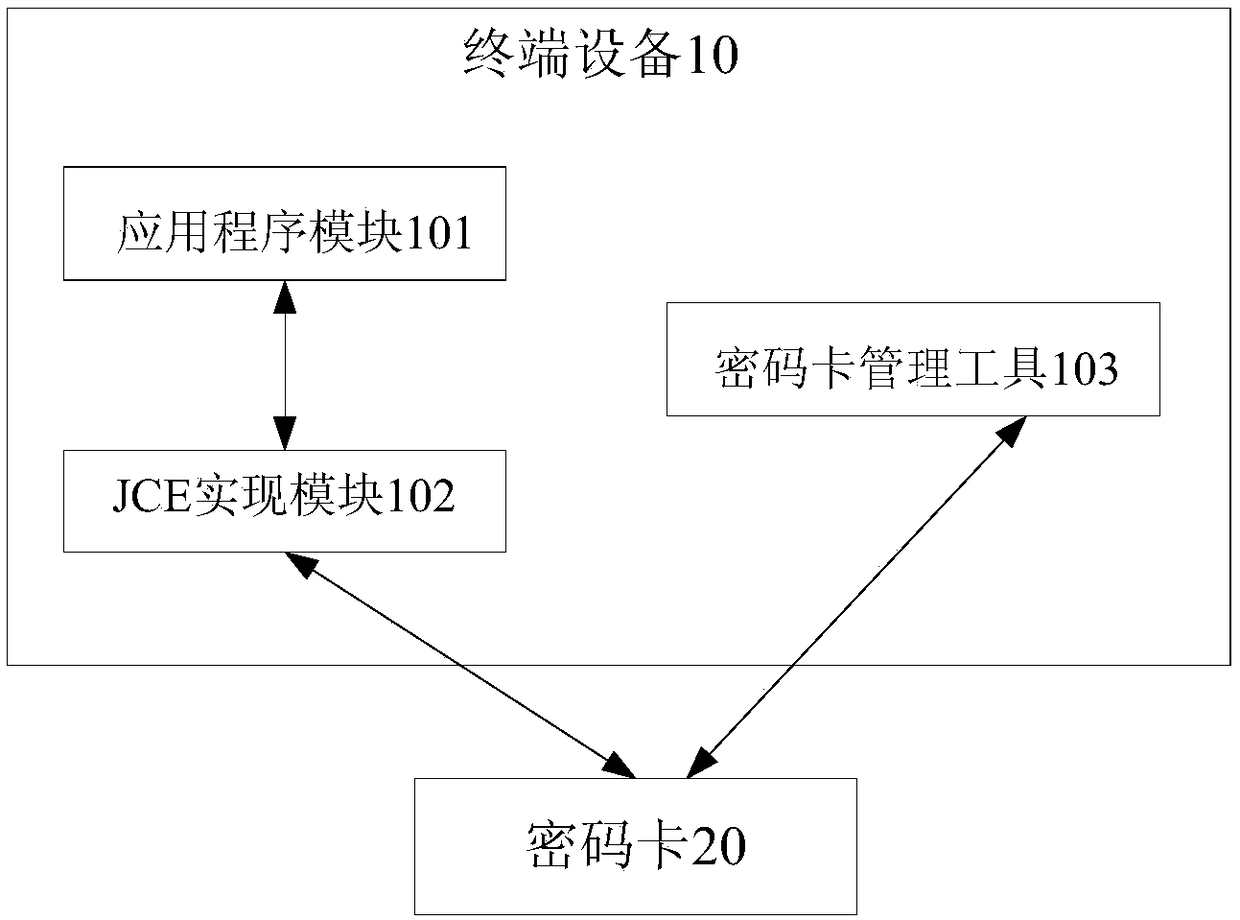
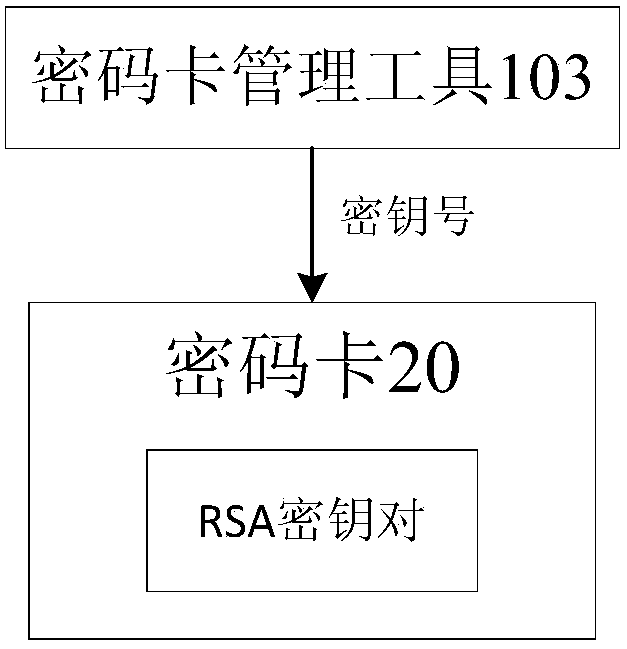
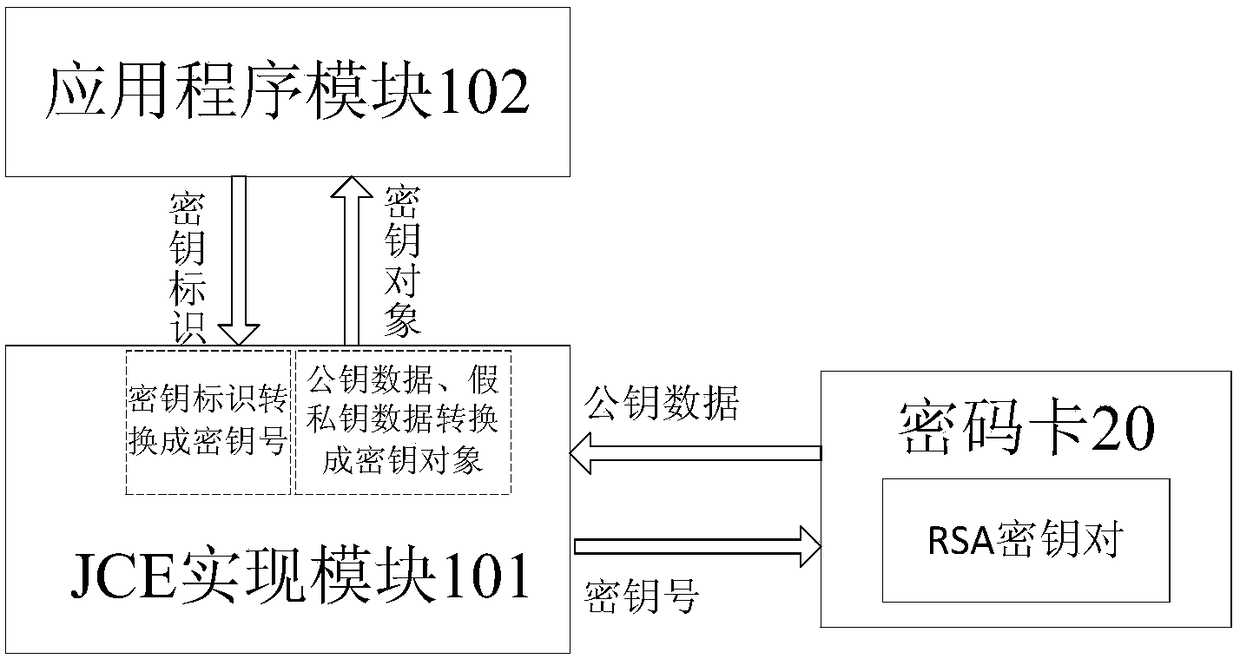
[0066] like Figures 1 to 4 As shown, a device for JCE calling a cryptographic card to implement built-in RSA key operations includes a terminal device 10 and a cryptographic card 20; The encryption card management tool 103 for specifying the key number and film length of the key pair; the encryption card 20 is inserted on the terminal device 10, connected with the encryption card management tool 103 for generating and storing the speci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com