Long repeating data encryption and transmission method and system
A technology for encrypted transmission and long data, which is applied in digital transmission systems, transmission systems, and key distribution, and can solve problems such as low encryption algorithm security, complex key distribution process, and slow encryption and decryption speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
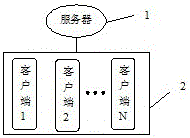
[0031] Such as figure 1 As shown, a system for repeated encrypted transmission of long data is composed of a server 1 and at least one client 2, and the server 1 and the client 2 perform network communication based on the TCP protocol to realize mutual data transmission. All the embodiments provided by the present invention are also applicable to network communication based on the UDP protocol. Since the UDP protocol does not have the concept of a server and a client, when performing network communication based on the UDP protocol, the login party and the logged-in party are respectively virtual clients. Client and server, to achieve the same role as the client and server based on TCP protocol communication.
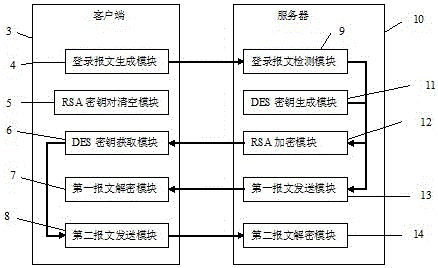
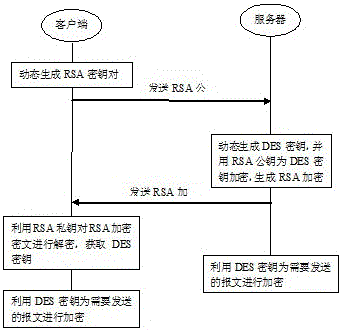
[0032] Such as figure 2 As shown, a method for repeated encrypted transmission of long data, the implementation process is as follows:
[0033] (1) The client dynamically generates an RSA key pair, which includes an RSA public key and its corresponding RSA private key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com