A Network Attack Target Prediction Method Based on Neighbor Similarity
A technology of neighbor similarity and network attack, which is applied in the field of network security, can solve the problems of restricting administrators' response strategies, insufficient prediction results, and attack target prediction, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
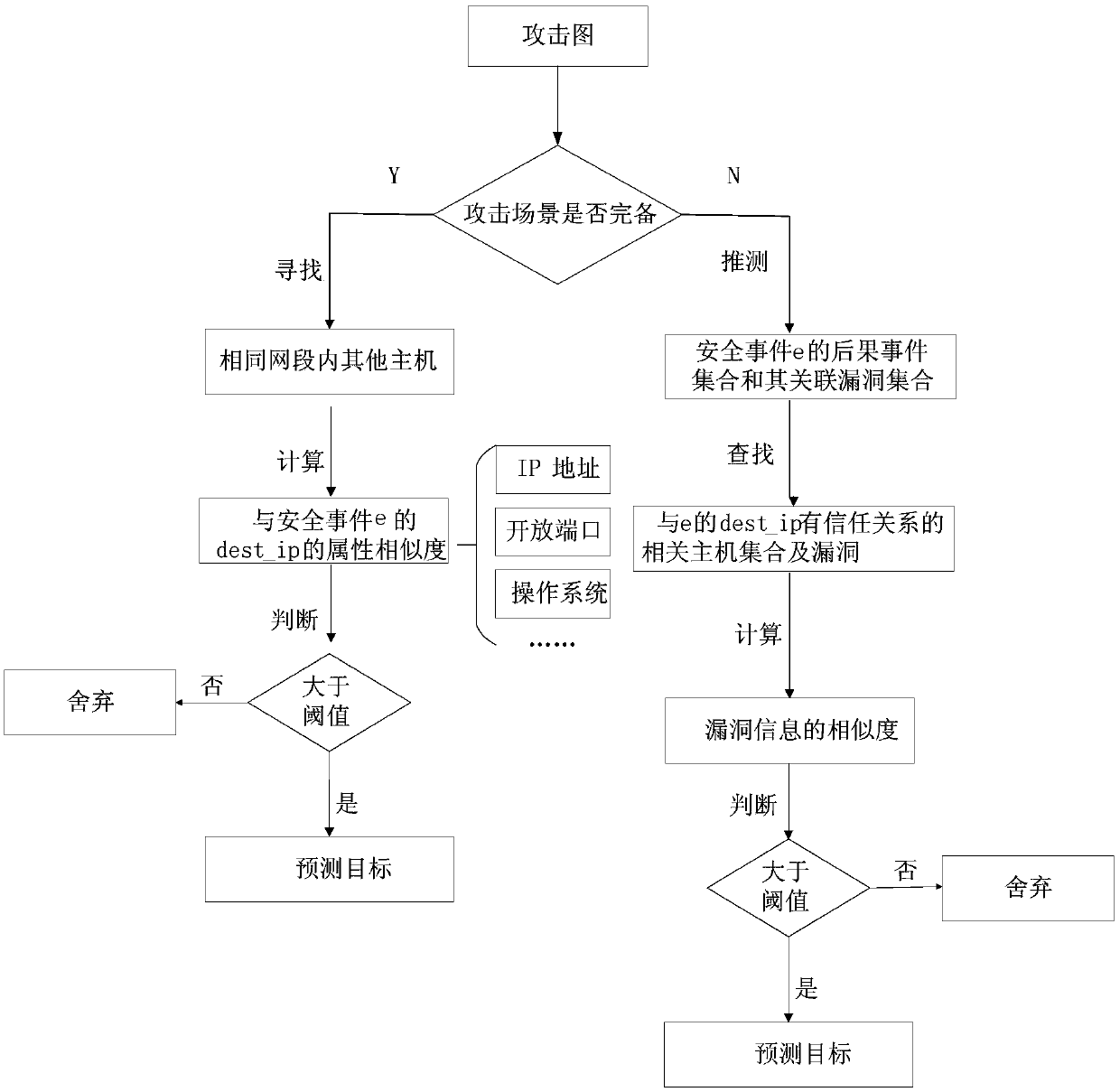
[0032] The technical solution of the present invention will be further described in detail below in conjunction with the examples. The following examples are implemented on the premise of the technical solutions of the present invention, and detailed implementation methods and processes are given, but the protection scope of the present invention is not limited to the following examples.
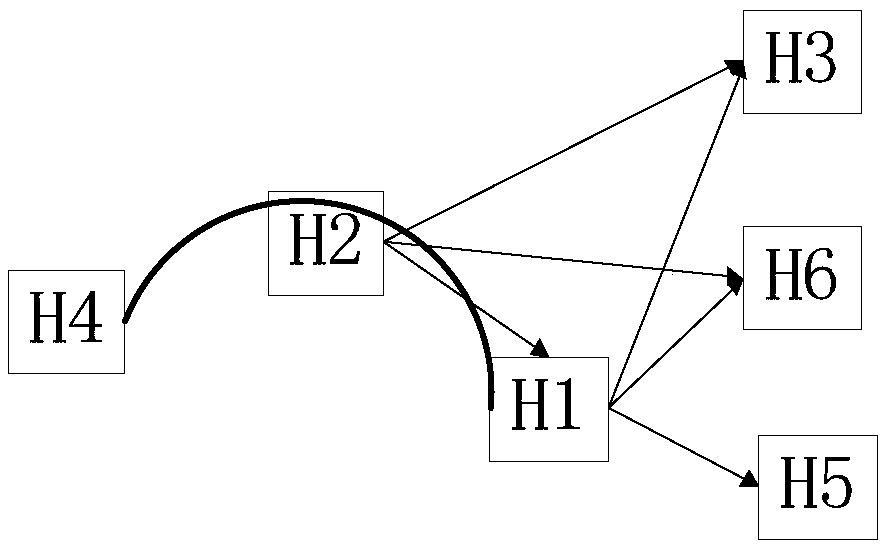
[0033]In order to better understand the method proposed in this embodiment, five hosts H1, H2, H3, H4, H5, and H6 under a network installed with an intrusion detection device are selected. Among them, H1 has a trust relationship with H3, H5, and H6, and H2 has a trust relationship with H1, H3, and H6, as shown in the table below. H4, H2, and H1 are the three hosts involved in a complete attack, and their connection relationship diagram is shown in the host relationship diagram ( figure 2 ) shown.
[0034] attack path
H4->H2->H1
H2->H1,H3,H6
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com