Method and device for implementing application program security detection
An application program and security technology, applied in the field of application program security detection, can solve the problems of increased consumption of resources, consumption of large computing resources, and increased costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] like figure 1 As shown, it is a flow chart of the main steps of a method for implementing application program security detection in an embodiment of the present invention, and the method includes:
[0051] Step 101, acquiring web page characteristic data of a specified website.
[0052] It should be noted that the designated website refers to the website used to download the application installation package. The application installation package can be the installation package (APK) of the application program of the Android operating system, the installation package of the application program of the Apple operating system, or the installation package of the Windows operating system. The installation package of the operating application program, the web page feature data includes the application name and / or application description information of the application program to be detected.
[0053] Step 102, according to the characteristic data of the web page and the pre-set...
Embodiment 2
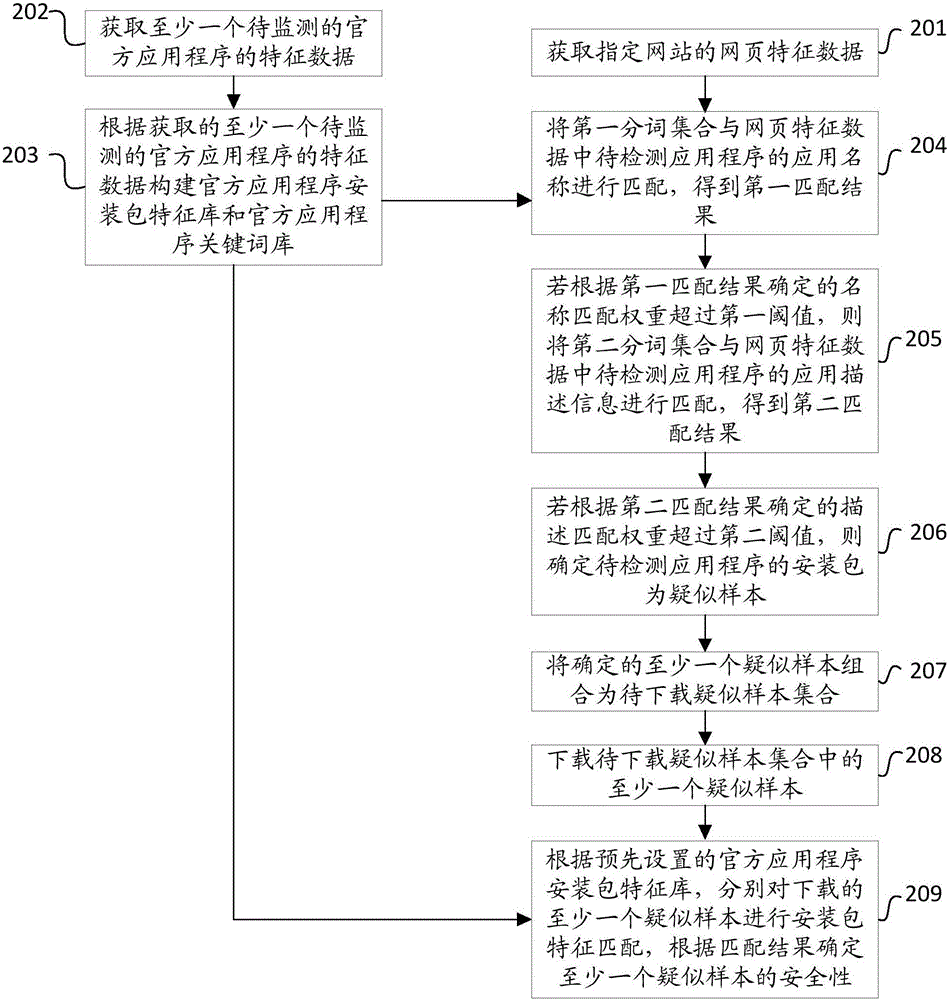
[0061] like figure 2 As shown, it is a detailed step-by-step flowchart of a method for implementing application program security detection in an embodiment of the present invention, which mainly includes the following steps:
[0062] Step 201, acquiring web page characteristic data of a specified website.
[0063] In this step, the web page feature data of the specified website is obtained. It should be noted that the specified website refers to a website for downloading an application installation package, and the application installation package may be an application installation package (APK ), the installation package of the application program of the Apple operating system or the installation package of the application program operated by Windows, the web page feature data includes the application name and application description information of the application program to be detected.
[0064] Specifically, a crawler program may be used to crawl the web page feature data...
Embodiment 3
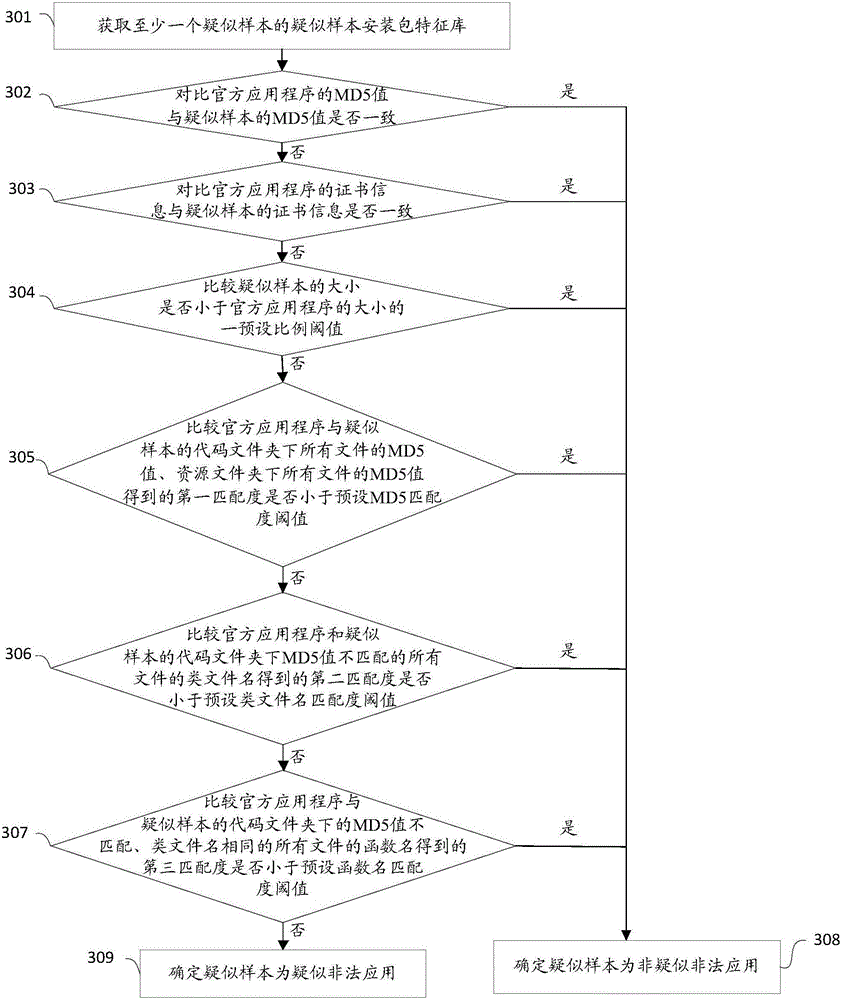
[0154] see image 3 , the specific step-by-step flowchart of step 104 is shown in the figure, and the specific steps are as follows:
[0155] Step 301 , obtain at least one suspected sample installation package signature database of suspected samples, and then go to step 302 .
[0156] In this step, the obtained suspected sample installation package feature library of at least one suspected sample includes: the MD5 value of the suspected sample, the certificate information of the suspected sample, the size of the suspected sample, and the IDs of all files in the decompiled code folder of the suspected sample. One or more of the MD5 value and function name list, and the MD5 values of all files under the resource folder. Specifically, the suspected sample installation package feature library may also include the version number of the suspected sample. Specifically, after obtaining at least one suspected sample installation package feature library of suspected samples,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com