Desensitization system and desensitization method used for big data
A big data and desensitization technology, applied in digital data protection, electronic digital data processing, instruments, etc., can solve problems such as increasing user burden, missing sensitive data, and lack of mature methods and processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0084] In order to better understand the present invention, the present invention will be described in detail below in conjunction with the accompanying drawings.
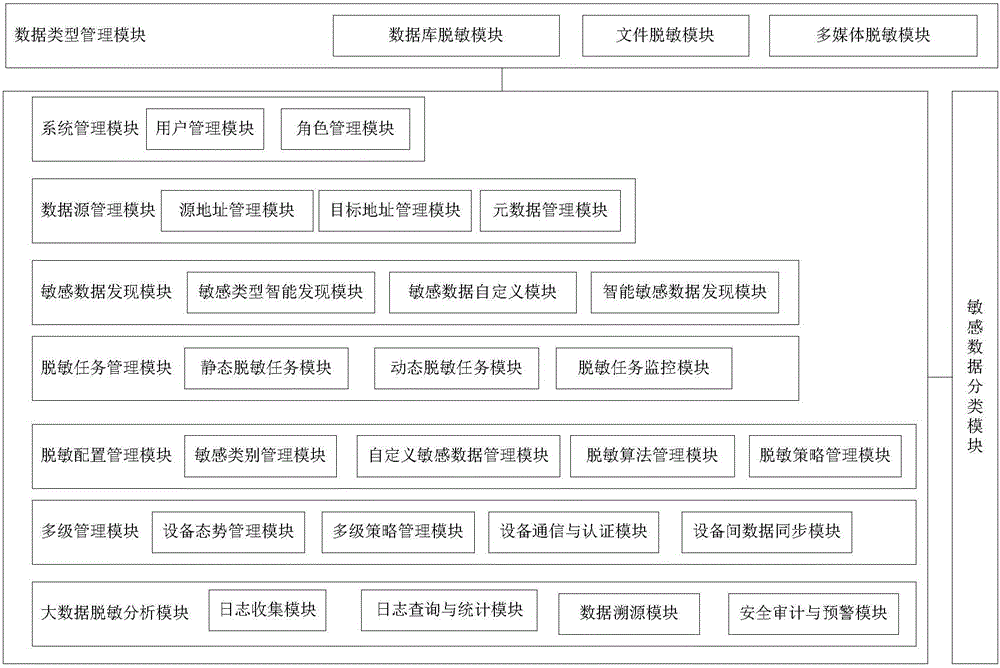
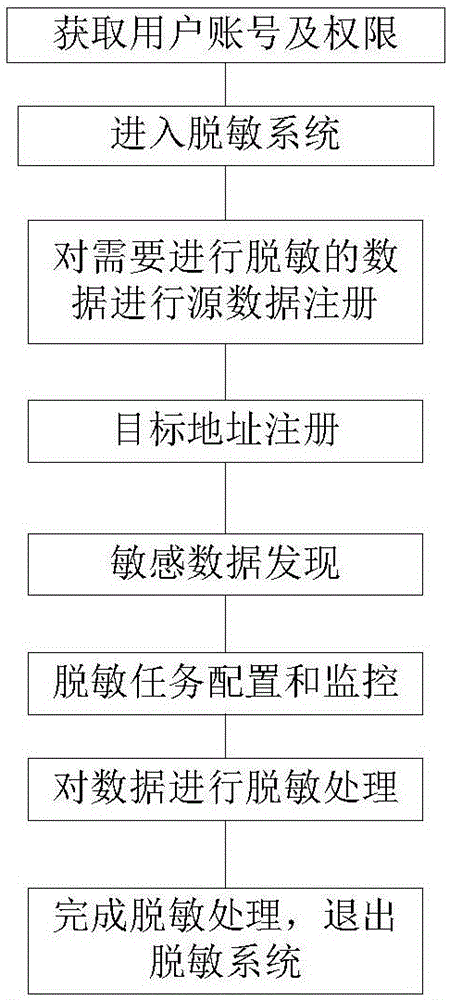
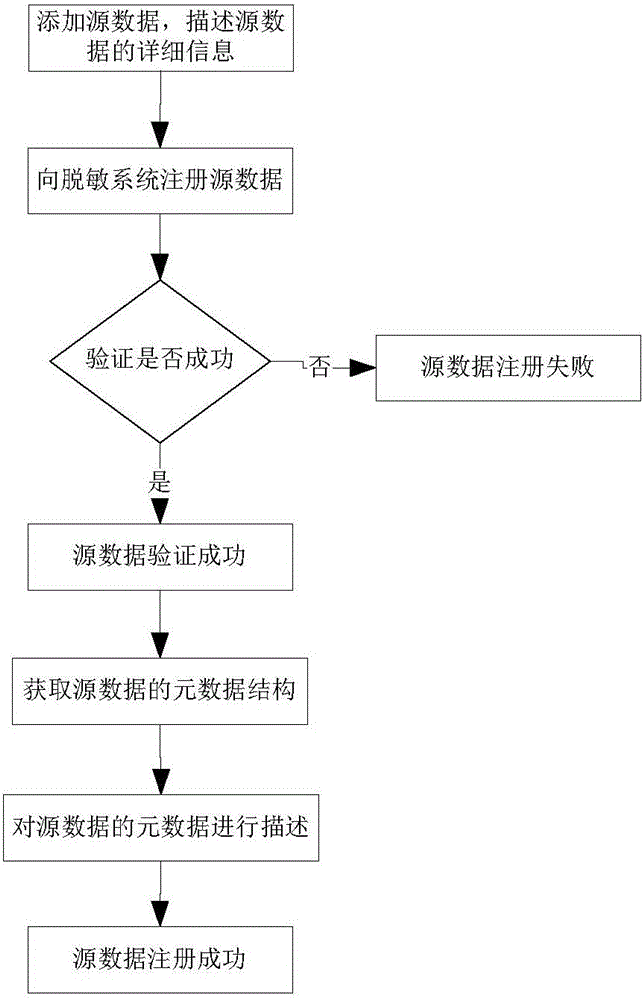
[0085] Such as figure 1 As shown, a desensitization system for big data of the present invention includes a database type management module for managing desensitized data types, a system management module for building roles for the desensitization system and performing functional authorization and management on roles, and a system management module for desensitization The sensitive system provides a data source management module for data source management, a sensitive data discovery module that automatically discovers sensitive data in data sources and submits it to users for adjustment and confirmation, and configures and manages the desensitization tasks of the big data desensitization system Masking task management module, masking configuration management module that manages and defines sensitive data and perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com