Verification code processing method, client and user terminal
A technology of a user terminal and a processing method, applied in the field of application software, can solve the problem of multiple execution steps in a mobile phone system, and achieve the effects of reducing signaling consumption, execution steps, and operation time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] According to the embodiment of the present application, a method embodiment of a verification code processing method is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions , and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
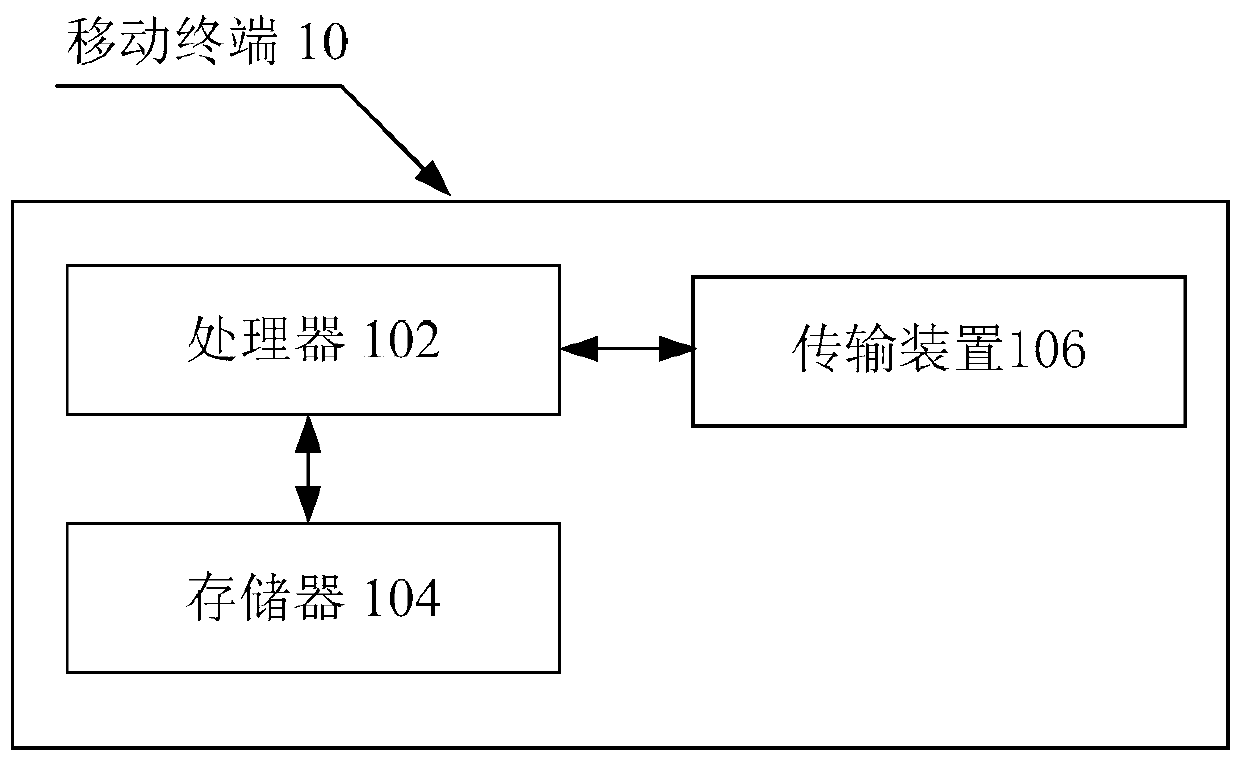
[0026] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Taking running on a mobile terminal as an example, figure 1 It is a hardware structural block diagram of a mobile terminal according to a verification code processing method according to an embodiment of the present application. Such as figure 1 As shown, the mobile terminal 10 may include one or more (only one is shown...
Embodiment 2
[0076] According to the embodiment of the present application, an embodiment of an apparatus for implementing the foregoing method embodiment is also provided, and the apparatus provided in the foregoing embodiment of the present application can run on a mobile terminal.
[0077] Figure 8 is a schematic structural diagram of a client according to an embodiment of the present application.
[0078] Such as Figure 8 As shown, the client may include a first detection unit 802 , a replication unit 804 and a processing unit 806 .
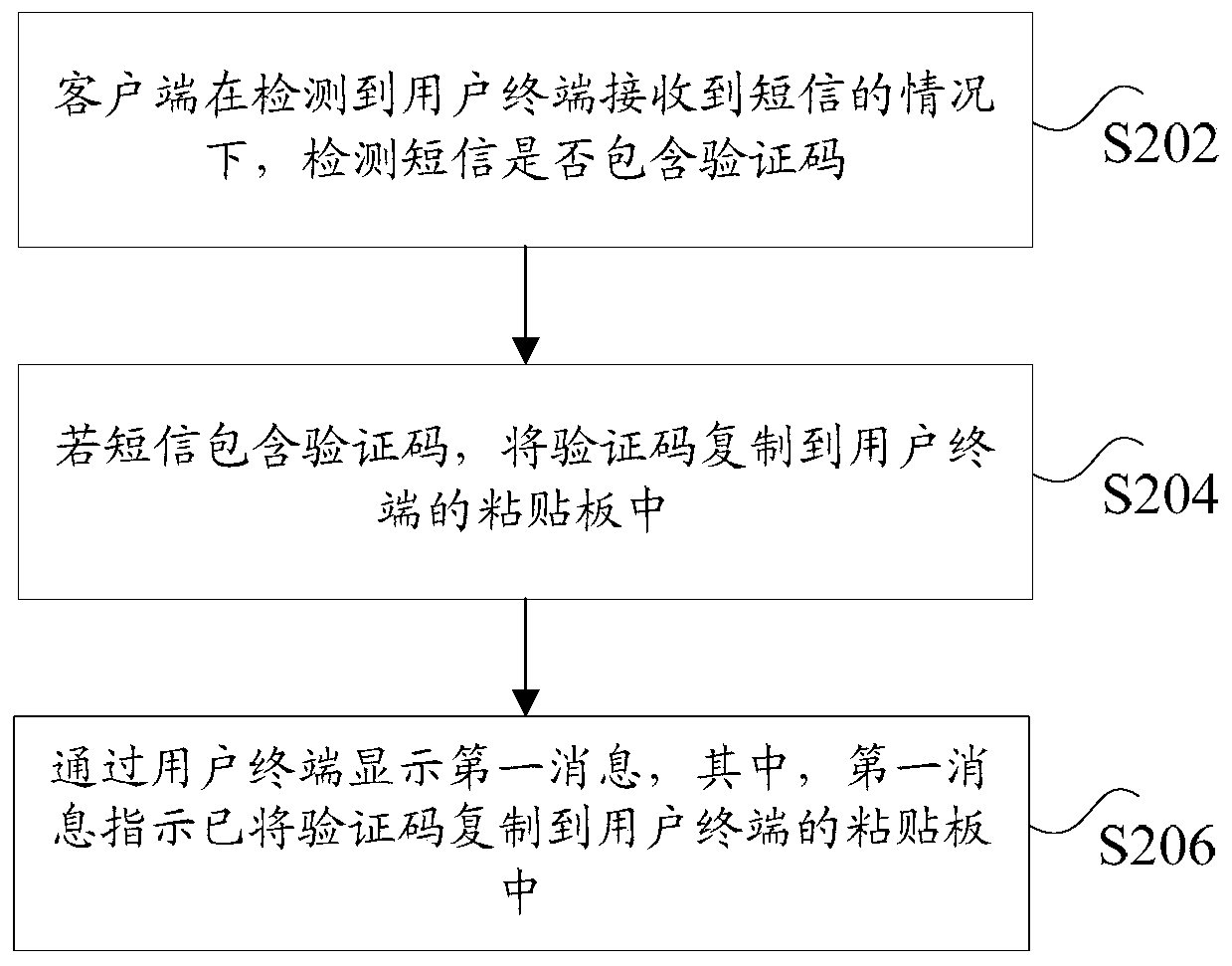
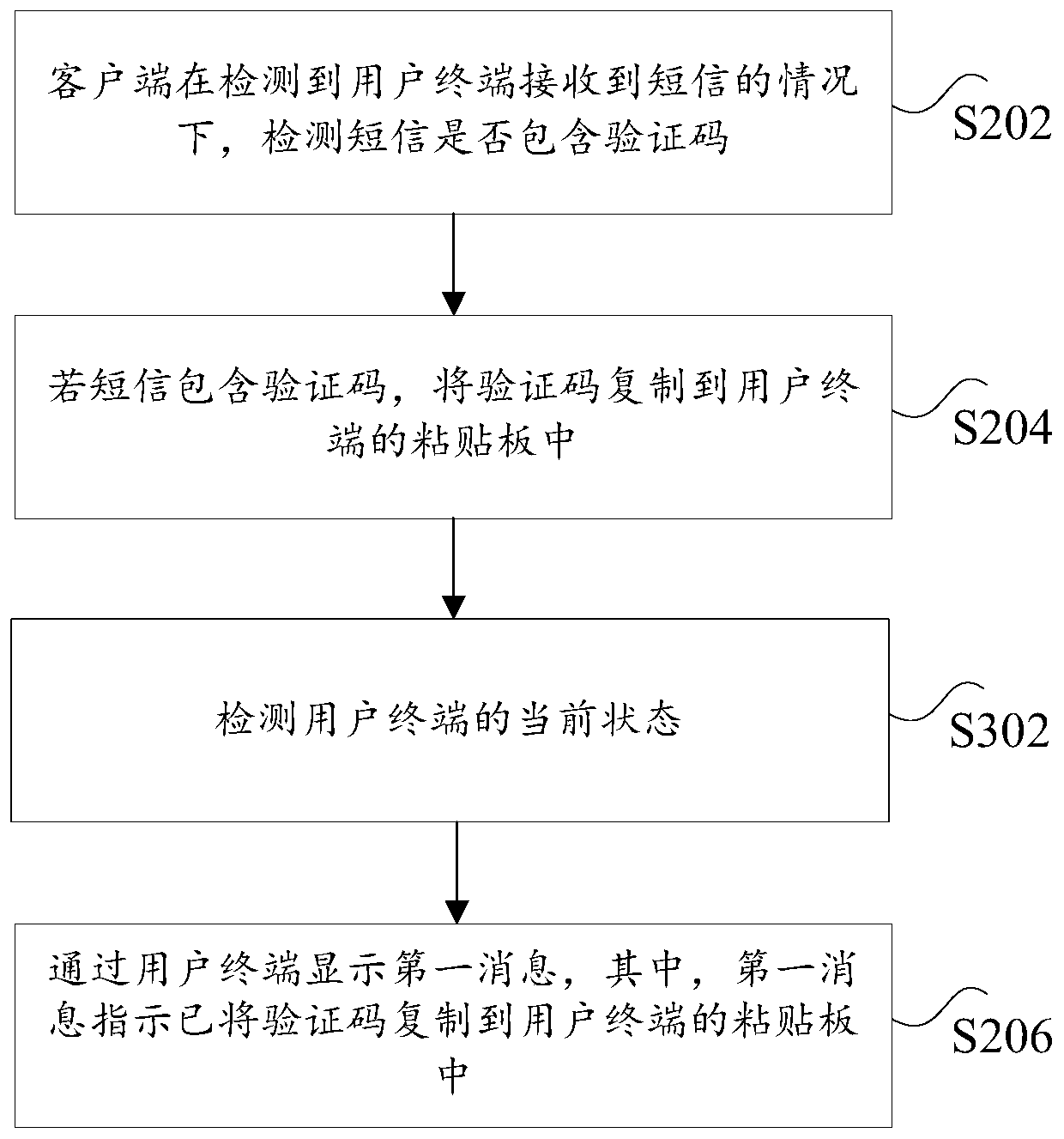
[0079] Wherein, the first detecting unit 802 is used to detect whether the short message contains a verification code when detecting that the user terminal has received the short message; the copying unit 804 is used to copy the short message if the short message contains the verification code. The verification code is copied to the clipboard of the user terminal; the processing unit 806 is configured to display a first message through the user termin...
Embodiment 3
[0100] The embodiment of the present application also provides a storage medium. Optionally, in this embodiment, the above-mentioned storage medium may be used to store the program code executed by the verification code processing method provided in the first embodiment above.
[0101] Optionally, in this embodiment, the above-mentioned storage medium may be located in any computer terminal in the group of computer terminals in the computer network, or in any mobile terminal in the group of mobile terminals.
[0102] Optionally, in this embodiment, the storage medium is configured to store program codes for performing the following steps: when the client detects that the user terminal has received a short message, detect whether the short message contains a verification code; if the The short message contains the verification code, and the verification code is copied to the pasteboard of the user terminal; the first message is displayed through the user terminal, wherein the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com