Access control method and communication node
A communication node and access control technology, applied in the field of wireless communication, can solve problems such as access congestion, and achieve the effect of improving the success rate of access and avoiding the phenomenon of access congestion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0083] Such as figure 1 As shown, this embodiment provides an access control method, the method comprising:
[0084] Step S100: the first type of node sends indication information through a downlink channel; wherein, the indication information includes at least configuration information of a first physical random access channel (PRACH) resource. The indication information may be used to control the second type of nodes to access the first type of nodes.
[0085] The access control method described in the embodiment of the present invention can be applied to a first type of node, and the first type of node can include a macro base station (Macrocell), a micro base station (Microcell), a pico base station (Picocell), and a femto base station ( Femtocell) is also called home base station, low power node (LPN) and relay station (Relay) and other communication nodes.
[0086] The first PRACH resource is a PRACH resource newly configured by the node of the first type after the pre...
Embodiment 2
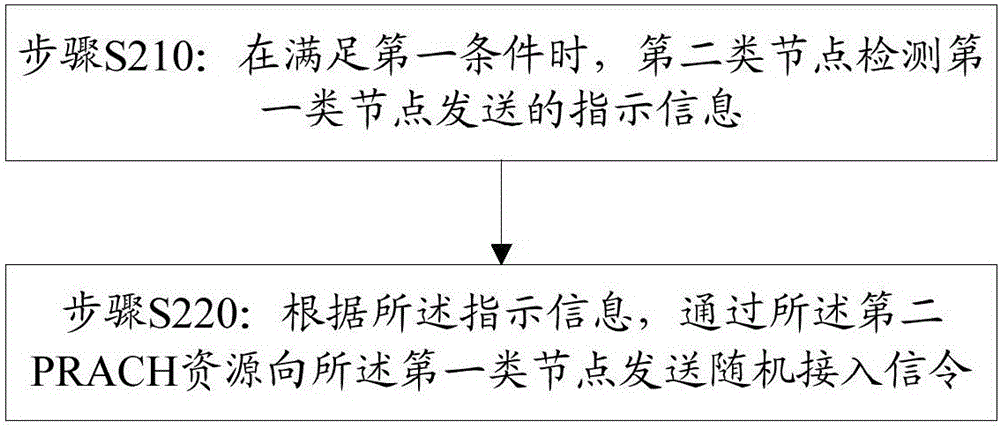
[0122] Such as figure 2 As shown, this embodiment provides an access control method, the method comprising:
[0123] Step S210: When the first condition is met, the second type of node detects the indication information sent by the first type of node; wherein, the indication information includes at least the configuration information of the first physical random access channel PRACH resource
[0124] Step S220: According to the indication information, send random access signaling to the first type of node through the first PRACH resource.
[0125] The access control method described in this embodiment can be applied to a second type of node, and the second type of node can be a second type of node of human-to-human H2H, a second type of node of machine-to-machine M2M, or a vehicle-to-vehicle V2V The second type of node or the second type of node for device-to-device D2D. Typical representatives of the second type of H2H nodes may include mobile phones and the like. The sec...
example 1
[0192] The first type of node sends indication information to the second type of node through a downlink channel, wherein the second indication information includes at least one of the following:
[0193] First PRACH resource configuration information.
[0194] The indication information may be sent in a random access response message.
[0195] The configuration information of the first PRACH resource includes at least one of the following:
[0196] Time-frequency resource configuration information of the first PRACH resource;
[0197] Carrier information corresponding to the first PRACH resource;
[0198] Index information of the random access sequence of the first PRACH resource;
[0199] Duration information of the first PRACH resource;
[0200] Enabling time information of the first PRACH resource;
[0201] Disabling time information of the first PRACH resource;
[0202] Furthermore, the disabling time information included in the disabling time information of the fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com