Wireless communication base station and data sending method thereof, and terminal and data reception thereof
A data transmission method and wireless communication technology are applied in the field of wireless communication base stations and data transmission methods, terminals and data reception fields, which can solve problems such as large security risks, and achieve the effect of improving security and avoiding risk loopholes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
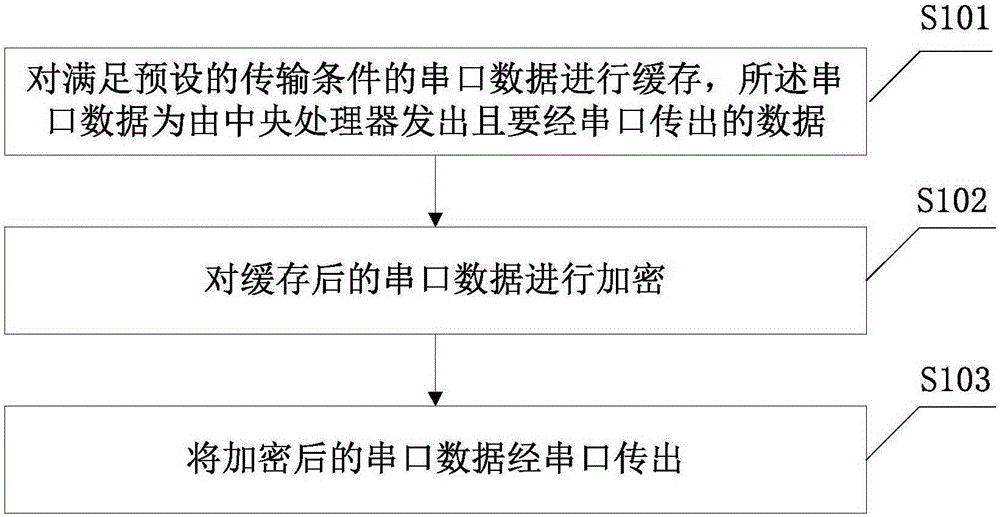
[0029] This embodiment provides a wireless communication base station data sending method, please refer to figure 1 , including the following steps:
[0030] Step S101: Buffer the serial port data that meets the preset transmission conditions, the serial port data is sent by the central processing unit and is to be transmitted through the serial port;
[0031] Before encrypting the serial port data, it is necessary to cache the serial port data that meets the preset transmission conditions. The serial port data is the data sent by the central processor and to be transmitted through the serial port; the preset transmission conditions are: the central processor has a serial port The data is sent out, while the serial port cable is connected and both ends are powered on; specifically, it is to monitor in real time whether the central processing unit (CPU) of the base station board sends out serial port data, and if it is detected that the CPU of the base station board sends out ...
Embodiment 2
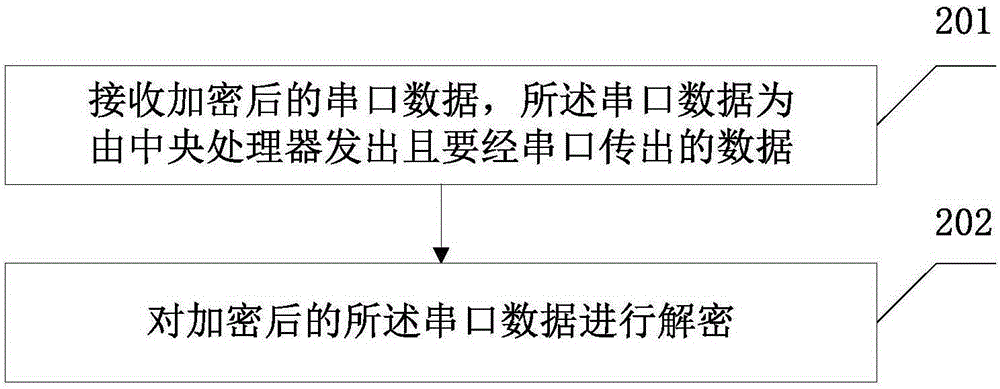
[0041] This embodiment provides a terminal data receiving method, please refer to figure 2 , including the following steps:
[0042] Step S201: receiving encrypted serial port data, the serial port data is sent by the central processing unit and will be transmitted through the serial port;
[0043] Receiving the encrypted serial port data is specifically receiving block-encrypted serial port data transmitted through the serial port.
[0044] Step S202: Decrypt the encrypted serial port data;
[0045] Decrypting the encrypted serial port data includes obtaining the decryption key required for decryption, and decrypting the serial port data in blocks through the decryption key. The decryption key corresponds to the encryption key; corresponding to Embodiment 1, this implementation For example, the asymmetric encryption algorithm RSA algorithm is preferably used for decryption, specifically, the private key of the asymmetric algorithm RSA is obtained and stored, and then the e...
Embodiment 3
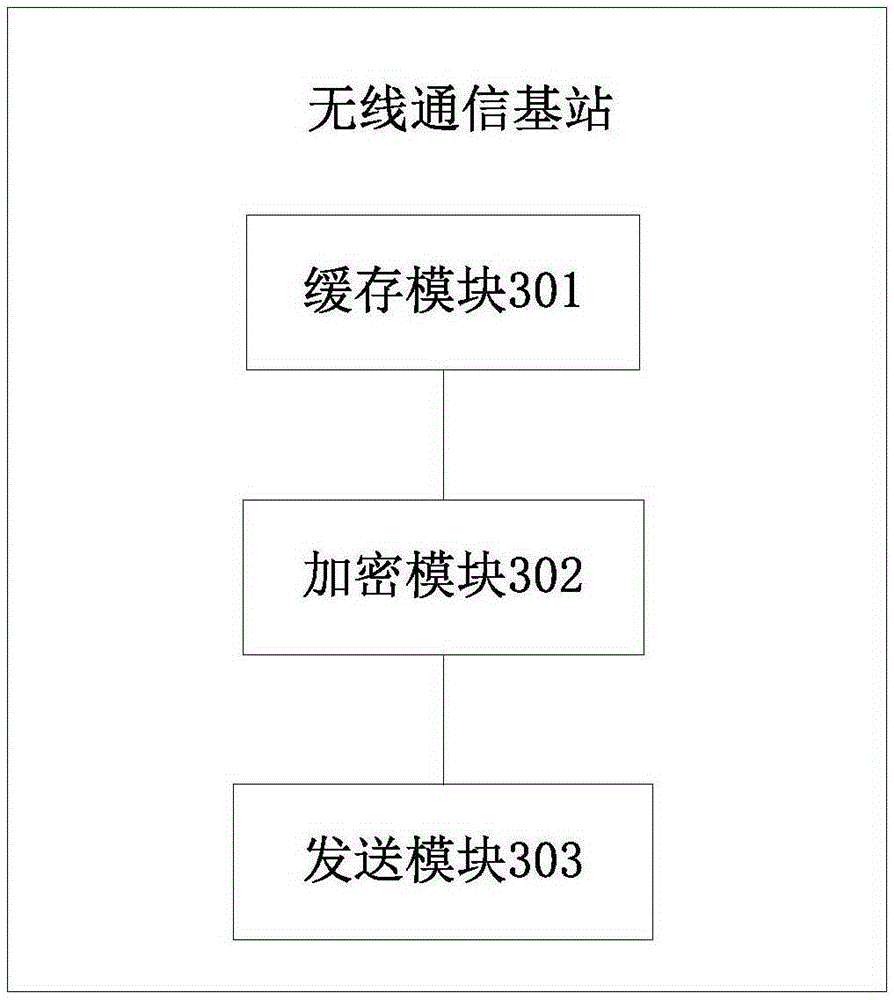
[0051] This embodiment provides a wireless communication base station, please refer to image 3 , specifically including the following modules: a cache module 301 , an encryption module 302 and a sending module 303 .
[0052] The cache module 301 is used to cache the serial port data that meets the preset transmission conditions. The serial port data is sent by the central processing unit to transmit data through the serial port. The preset transmission condition is: the central processing unit has serial port data to transmit , while the serial cable is connected and powered on at both ends; see Figure 4 , the cache module 301 also includes a judging submodule 3011 and a caching submodule 3012, the judging submodule 3011 is used to judge whether the serial port data satisfies the preset transmission condition, and the cache submodule 3012 is used to meet the preset transmission condition The serial port data is cached. Specifically, it is to determine whether the sub-modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com