Computer virus spreading source tracing method based on complex network
A computer virus and complex network technology, applied in the field of computer virus transmission source seeking based on complex network, can solve the problem that the virus transmission cannot be suppressed from the source, and achieve the effect of enriching the defense system and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings.
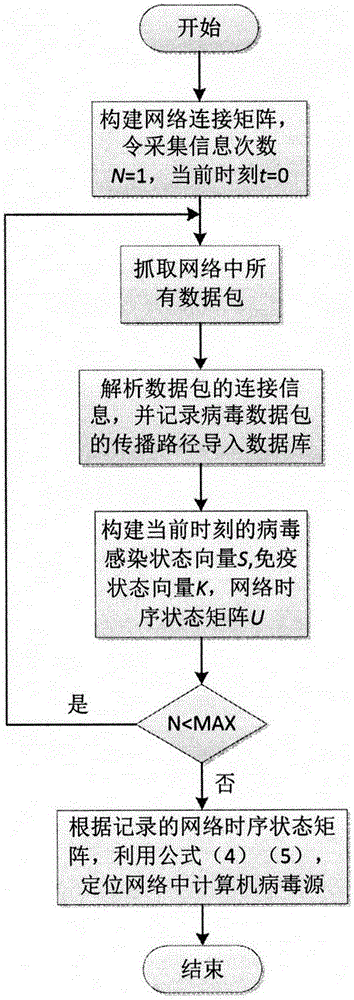
[0026] Such as figure 1 , 2 , 3, 4, and 5, the present invention comprises the following steps:
[0027] ①. Construct a network diagram of computer virus transmission;
[0028] ②. Construct virus infection state vector;
[0029] ③. Construct immune state vector;
[0030] ④. Construct the network timing state matrix.
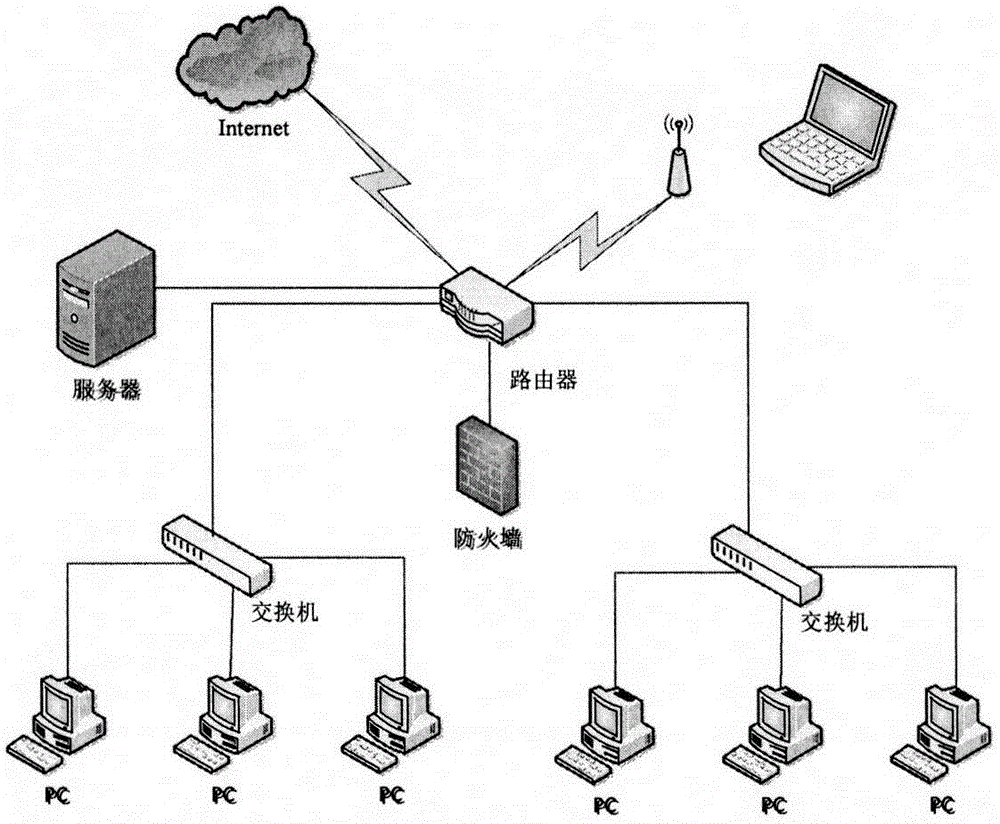
[0031] The step ① adopts connection matrix E n×n Describe the connectivity of the network, where e ij = 1 means node v i and node v j directly connected in the network, e ij = 0 means node v i and node v j are not connected in the network, and e ij = e ji .
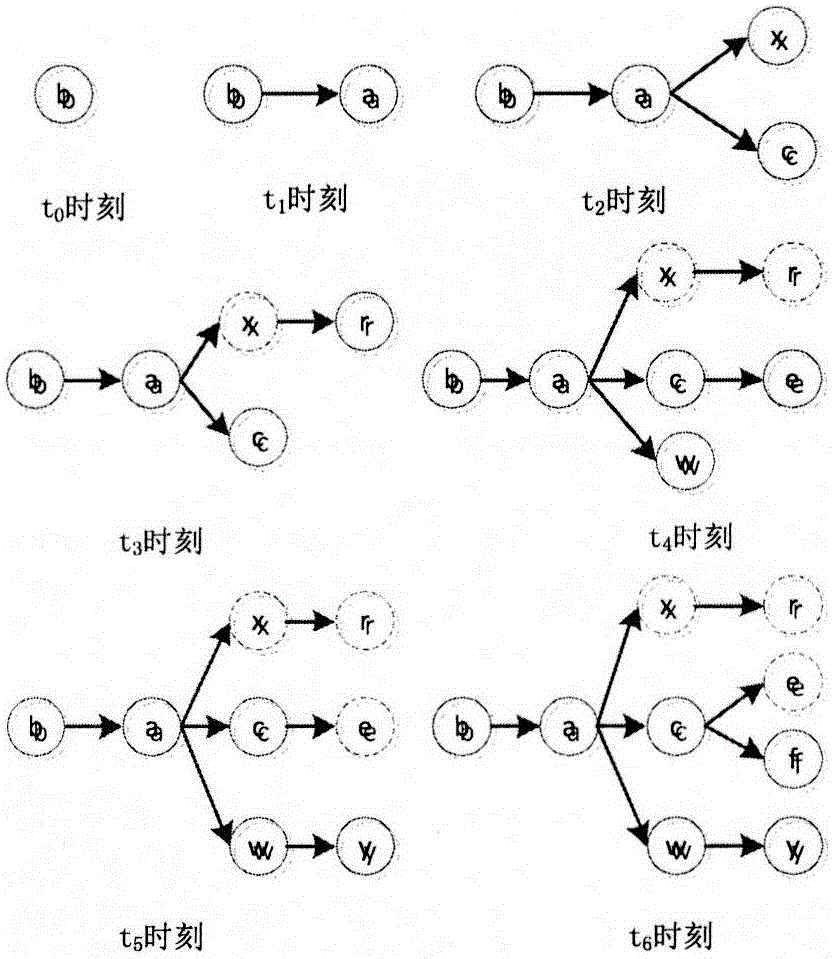
[0032] The step ② uses the SIR model to study the propagation characteristics of computer viruses in the network.
[0033] The step ③ is specifically to use the immune state vector to store the computer nodes that have been killed in the network. It is assumed that as long as the com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com