IOT invasion monitoring method and device
A technology of intrusion monitoring and Internet of Things, applied in the field of Internet of Things security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
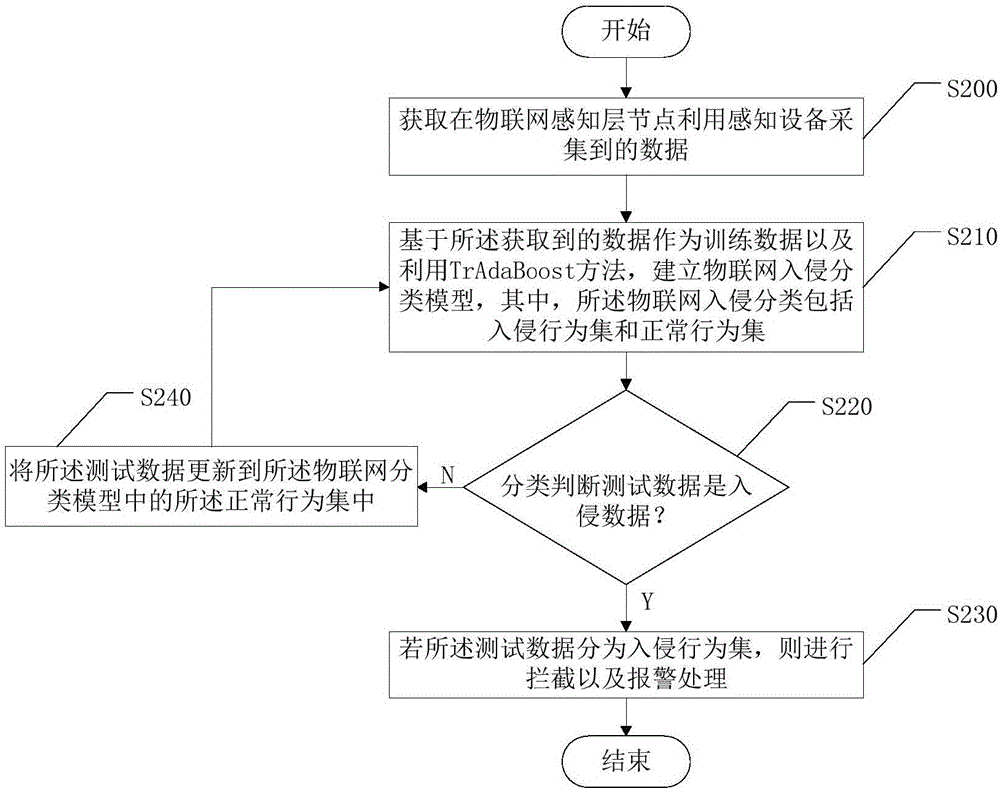
[0021] see figure 2 , the embodiment of the present invention provides a method for intrusion monitoring of the Internet of Things, the method comprising:
[0022] Step S200: Acquiring data collected by sensing devices at nodes of the sensing layer of the Internet of Things;
[0023] Step S210: Based on the obtained data as training data and using the TrAdaBoost method, an Internet of Things intrusion classification model is established, wherein the Internet of Things intrusion classification includes an intrusion behavior set and a normal behavior set;
[0024] Step S220: Obtain the test data collected by the sensing device at the sensing layer node of the Internet of Things again, and use the Internet of Things intrusion classification model to perform classification judgment;
[0025] Step S230: If the test data is divided into intrusion behavior sets, interception and alarm processing are performed;
[0026] Step S240: If the test data is classified into a normal behavi...
no. 2 example
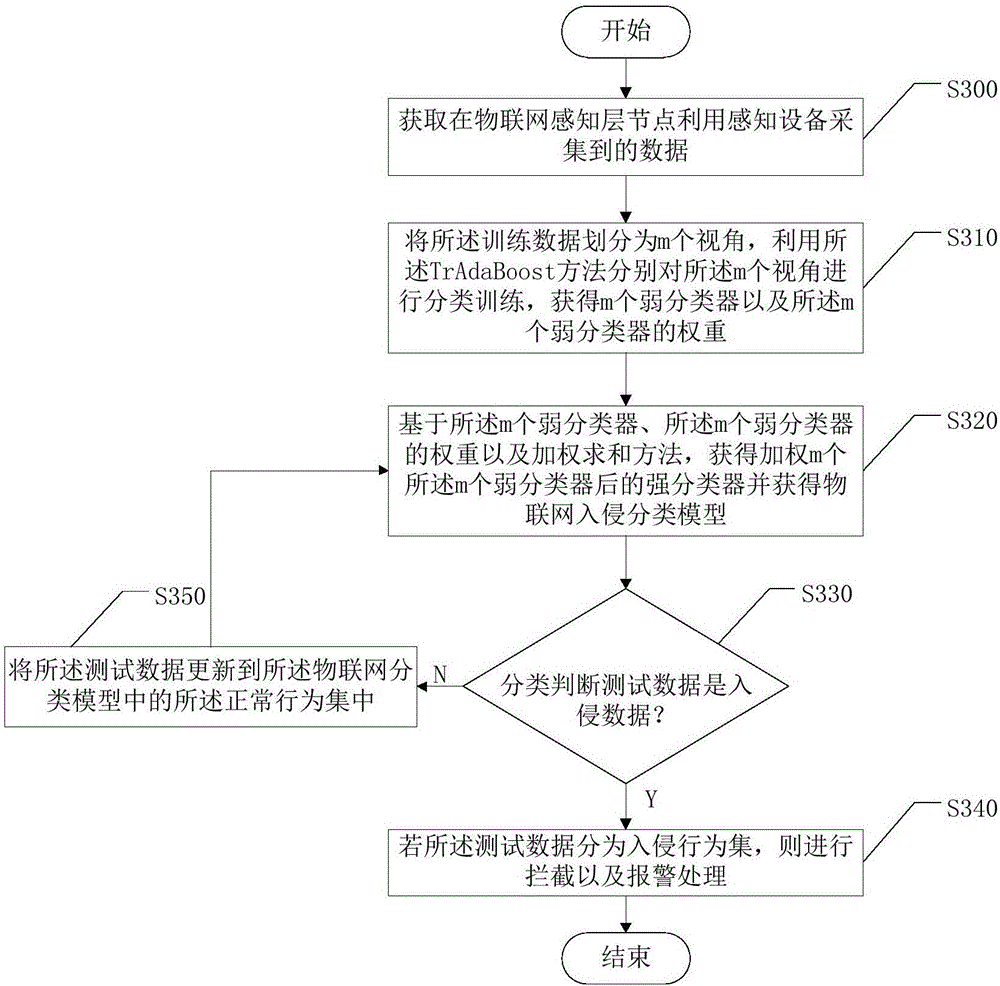
[0029] see image 3 , the embodiment of the present invention provides a method for intrusion monitoring of the Internet of Things, the method comprising:
[0030] Step S300: Acquiring data collected by sensing devices at the sensing layer nodes of the Internet of Things;
[0031] The hierarchical structure of the Internet of Things is divided into three layers, from bottom to top: the perception layer, the network layer, and the application layer. The perception layer is the core of the Internet of Things and a key part of information collection. The perception layer is located at the bottom of the three-layer structure of the Internet of Things, and its function is "perception", that is, to obtain environmental information through the sensor network. The perception layer is the core of the Internet of Things and a key part of information collection.
[0032]The perception layer includes two-dimensional code tags and readers, RFID tags and readers, cameras, GPS, sensors, M...
no. 3 example
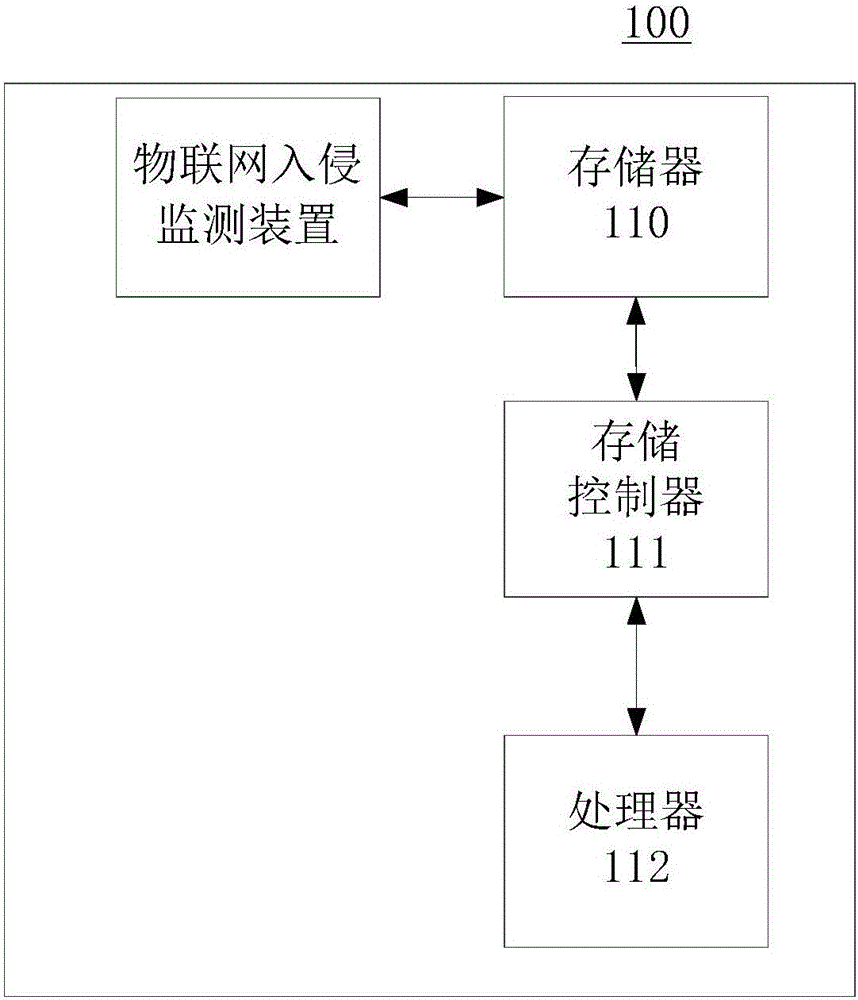
[0075] Please refer to Figure 4 , the embodiment of the present invention provides an Internet of Things intrusion monitoring device 400, the device 400 includes:
[0076]The first data acquisition unit 410 is configured to acquire data collected by sensing devices at the sensing layer nodes of the Internet of Things.
[0077] The Internet of Things intrusion classification model establishment unit 420 is configured to establish an Internet of Things intrusion classification model based on the obtained data as training data and using the TrAdaBoost method, wherein the Internet of Things intrusion classification includes an intrusion behavior set and a normal behavior set.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com