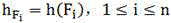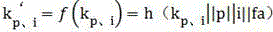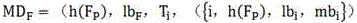Encrypted data dereplication method for cloud storage
A technology for encrypting data and cloud storage. It is used in digital data protection, electronic digital data processing, and special data processing applications. It can solve problems such as deduplication of ciphertext data and achieve the effect of protecting confidentiality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] In order to make the whole invention clear, the present invention is specifically explained in conjunction with the following steps:
[0012] Step 1: Generate file identification and conduct preliminary verification. The specific content is as follows:
[0013] The user's file F is not encrypted before uploading. First, the file properties (property) including file type, file name, file summary and other information are hashed to obtain the file's property label: h(F P ), if there is the same attribute tag in the cloud space, it will prompt whether to confirm the upload, and if the upload continues, it will enter the follow-up process.
[0014] Step 2: Divide the file into blocks and generate the feature set of the data block. The specific content is as follows:
[0015] Divide the file F into n data blocks {F i}, 1≤i≤n, and then calculate the hash value of each data block that is the identity:
[0016]
[0017] Represents the characteristics of the i-th data bl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com