Digital signature method, device and cryptographic device
A digital signature and signature generation technology, applied in the field of cryptography, can solve problems such as failure of the buffer mechanism, no data in the buffer, difficulty in meeting signature requirements, etc., and achieve the effects of resisting linear attacks, high computing efficiency, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
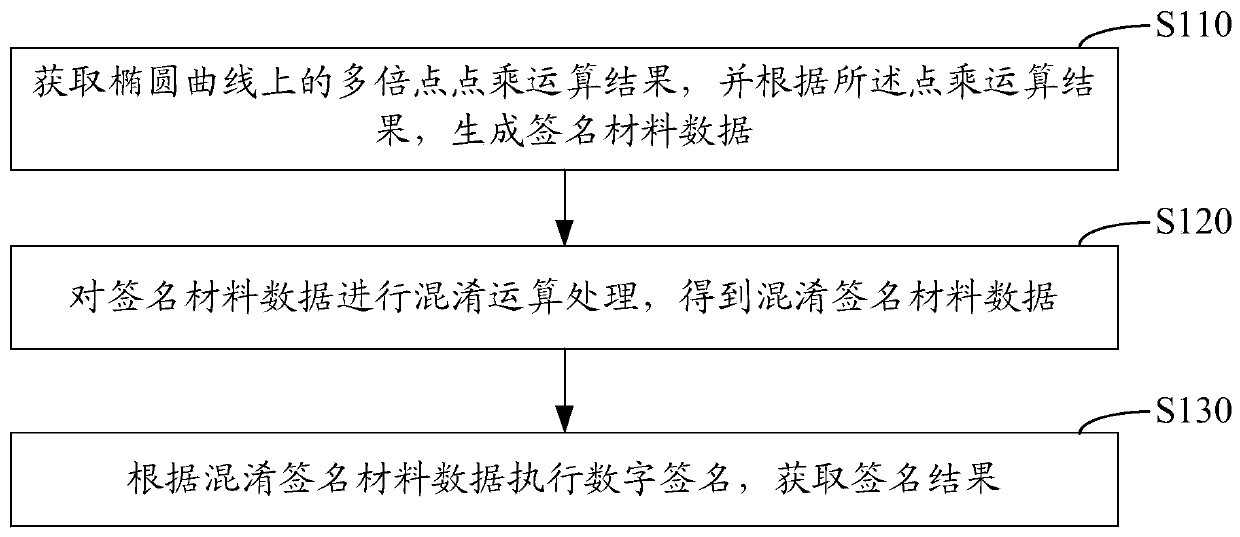
[0074] In order to solve the problem that the traditional technology has weaknesses in resisting linear attacks, and is limited by the performance of hardware devices, it is difficult to meet the signature requirements of a large number of users concurrently executed, which restricts the efficiency of digital signatures, the present invention provides an embodiment of a digital signature method 1; figure 1 It is a schematic flow chart of Embodiment 1 of the digital signature method of the present invention; as figure 1 As shown, the following steps may be included:
[0075] Step S110: Obtain the result of multiplication point multiplication on the elliptic curve, and generate signature material data according to the result of point multiplication;
[0076] Step S120: Obfuscate the signature material data to obtain the obfuscated signature material data;
[0077] Step S130: Perform digital signature according to the obfuscated signature material data, and obtain the signature...
Embodiment 2
[0174] In order to solve the problem that traditional technology has weaknesses in resisting linear attacks, and is limited by the performance of hardware devices, it is difficult to meet the concurrent signature requirements of a large number of users and restrict the efficiency of digital signatures. At the same time, based on the above technical ideas of digital signature methods, this paper The invention also provides Embodiment 2 of a digital signature cryptographic device; Figure 8 It is a schematic structural diagram of Embodiment 2 of the digital signature cryptographic device of the present invention; as Figure 8 As shown, may include a cryptographic card and a graphics processor; the cryptographic card includes a signature component; the graphics processor includes a signature material generator and an obfuscation multiplier;
[0175] The signature material generator obtains the result of the multi-point multiplication operation on the elliptic curve, and generates...
Embodiment 3
[0178] In order to solve the problem that traditional technology has weaknesses in resisting linear attacks, and is limited by the performance of hardware devices, it is difficult to meet the concurrent signature requirements of a large number of users and restrict the efficiency of digital signatures. At the same time, based on the above technical ideas of digital signature methods, this paper The invention also provides Embodiment 3 of a digital signature cryptographic device; Figure 9 It is a schematic structural diagram of Embodiment 3 of the digital signature cryptographic device of the present invention; as image 3 As shown, the functions of signature material generator, confusion multiplier and signature component can also be implemented in the same cryptographic device, such as a cryptographic card. If the signature material generator is implemented outside the password card, and then sent to the inside of the password card to complete the subsequent processing, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com