Quick determination method for security boundary quantity of power distribution network
A technology of security boundary and determination method, applied in the field of distribution network, can solve problems such as cumbersome process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
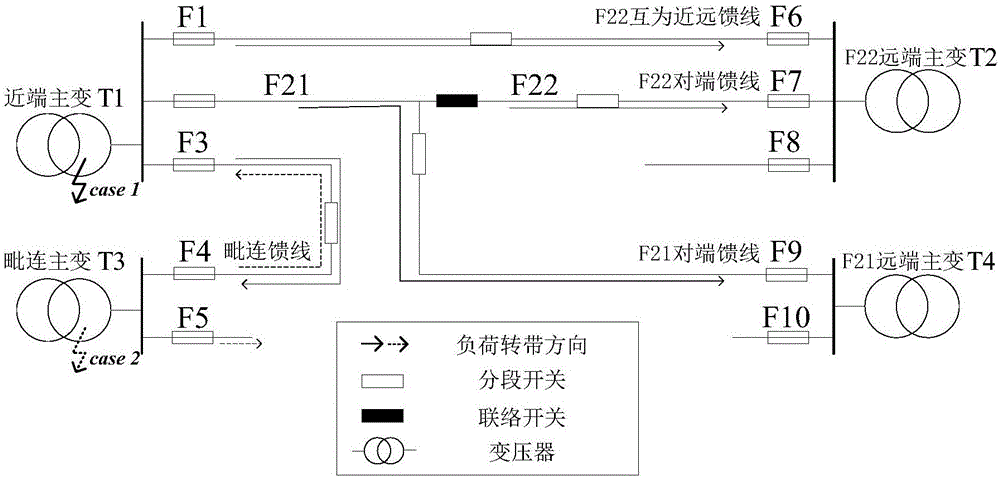
[0090] see Figure 4 , the embodiment of the present invention provides a method for quickly determining the number of distribution network security boundaries, the method includes the following steps:
[0091] 101: Select the observation feeder and judge its contact relationship;
[0092] 102: Find out the additional components of each observation feeder;
[0093] 103: According to the feeder connection relationship, select the corresponding oblique / straight boundary quantity calculation formula to determine the boundary quantity.
[0094] To sum up, the embodiment of the present invention realizes through the above steps 101 to 103 that it does not need to simulate the security domain or write the security boundary equation, and can quickly determine the security boundary only by observing the network structure of the distribution network and combining the calculation formula of the boundary quantity. The number of borders.
Embodiment 2
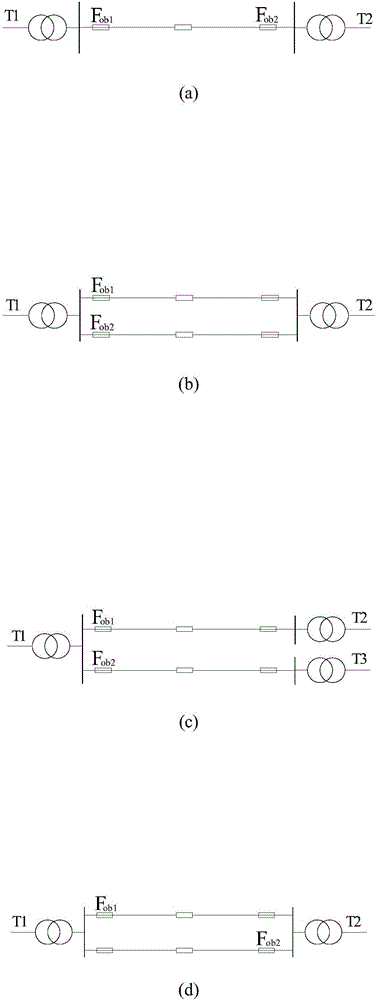
[0096] The following is combined with the specific calculation formula, Table 1-4, and appendix Figure 1-Figure 5 The scheme in Example 1 is further introduced, see the following description for details:
[0097] 201: Obtain a complete security boundary;
[0098] The embodiment of the present invention studies the complete safety boundary of the distribution network, and the types of component failures are feeder outlet failures and main transformer failures. For a distribution network with m main transformers and n feedback lines, its complete security boundary can be expressed as
[0099]
[0100] In formula (1), express fault caused The boundary corresponding to the capacity constraint; i and j are the serial numbers of the components; for faulty components; is the limiting element; CB DSSR For a complete set of security boundaries.
[0101] number of borders is equal to the set CB DSSR The number of elements in
[0102]
[0103] Among them, the two-...
Embodiment 3
[0221] The feasibility of the schemes in Examples 1 and 2 will be verified below in combination with specific calculation examples, see the description below for details:
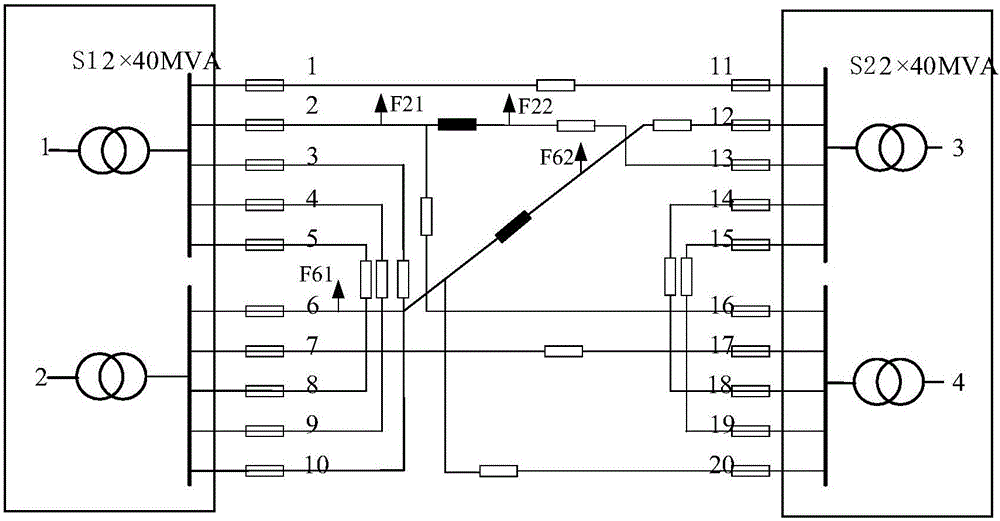
[0222] The grid structure of the example power grid is as follows: figure 1 As shown, there are 2 35kV substations, 4 main transformers, 20 circuits of 10kV feeders, 22 feeders or feeder section loads, all feeders are JKLYJ-185, and the allowable capacity is 12MVA. The main transformer data of the substation are shown in Table 4.
[0223] Table 4 Basic Information of Main Transformer
[0224]
[0225] Implementation steps of the present invention
[0226] 1) Select the observation feeder and judge its contact relationship
[0227] For example, if the feeders F8 and F9 are selected for observation, the connection relationship between the feeders is the same near and the same distance.
[0228] 2) Find out the extra elements of the observation feeder
[0229] The additional components of the feeder F8...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com