Biological feature password authentication method and device
A biometric and password authentication technology, applied in the field of information security, can solve the problem of biometrics being easily stolen, and achieve the effect of ensuring independence and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
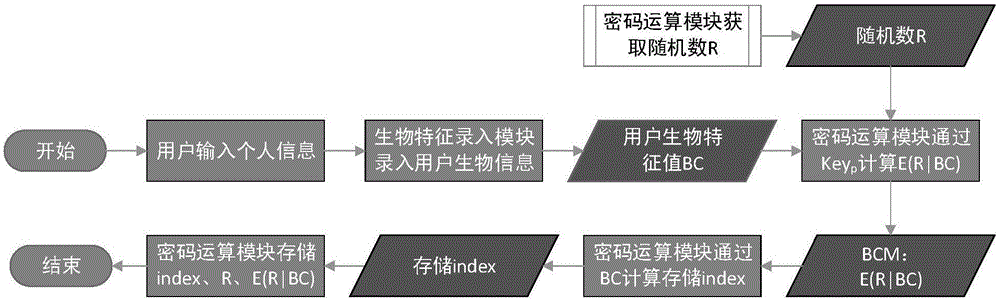
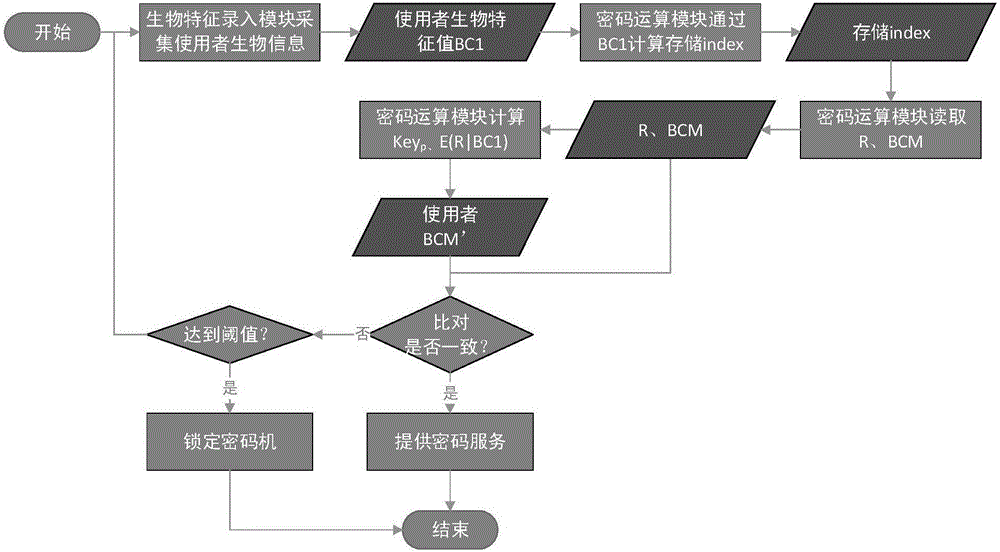
[0044] Such as figure 1 and figure 2 As shown, a biometric password authentication method provided in this embodiment includes a biometric initial feature entry step and a biometric authentication step. Extract the initial biometric feature BC0 from the biological information; at the same time, obtain the random number R0 through the noise source, and use the random number R0 to generate the protection key key p 0, store random number R0, the random number R0 is the component of the biometric template, and obtaining the random number R0 through the noise source can guarantee the randomness and uniqueness of the random number R0; then, use the protection key key p 0 pair (R0|BC0) is encrypted, and the encrypted ciphertext E(R0|BC0) is used as the biometric template BCM to store the biometric template BCM. The encryption algorithm can be a symmetric encryption algorithm, and E(R0|BC0) identifies the encrypted The ciphertext; the index index0 is generated through the initial b...
Embodiment 2
[0050] Such as figure 1 and figure 2 As shown, this embodiment provides a biometric password authentication device, specifically, a cryptographic machine, which includes a biometric feature input module and a cryptographic operation module. The biometric feature entry module is used to collect biometric information and extract biometric features BC. The biometric feature entry module can be externally connected to the cipher machine or embedded in the cipher machine. User registration and identity verification must go through the biometric feature entry module, and the user When registering, the user's initial biological characteristics must be entered and the initial biological characteristics steps are performed; the cryptographic operation module is used to encrypt the biological characteristics, encrypt the data and store indexes, random numbers and biological characteristic templates. The biometric password authentication device may also include a storage module for sto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com