Fine grained streaming media video encryption and decryption method based on HLS protocol
An encryption method and fine-grained technology, applied in electrical components, transmission systems, etc., can solve problems such as no security considerations, achieve the effect of reducing key management and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
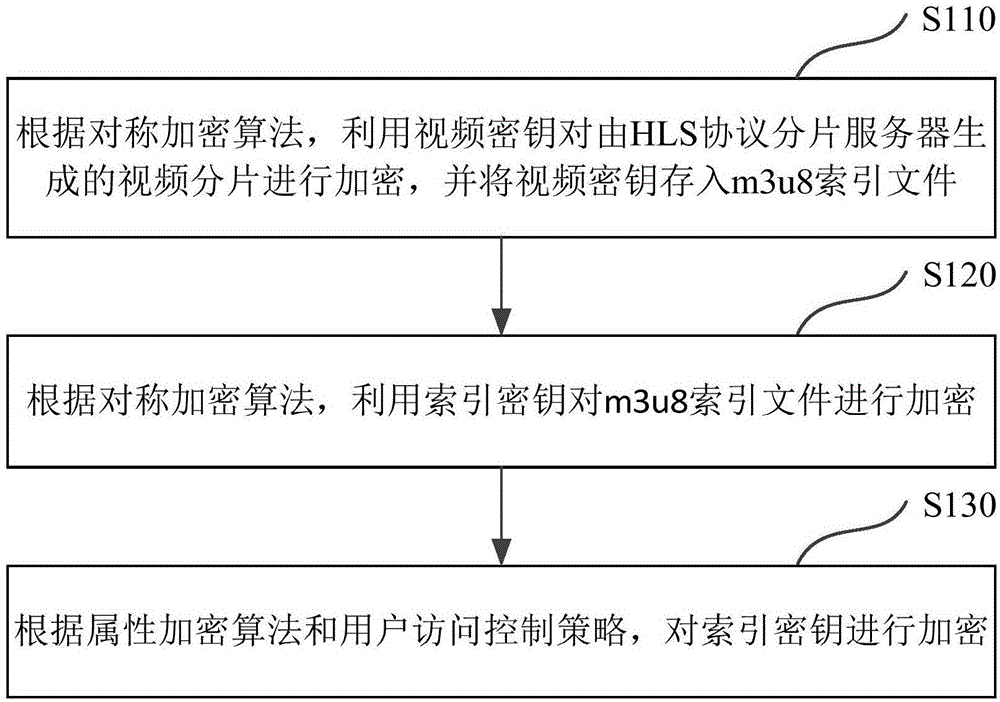
[0045] figure 1 It is a flowchart of a fine-grained stream media video encryption method based on the HLS protocol in an embodiment of the present invention. Combine below figure 1 Describe in detail the steps and principles of streaming video encryption.
[0046] Step S110, the first-layer encryption step, uses the video key to encrypt the video segments generated by the HLS protocol segment server according to the symmetric encryption algorithm, and stores the video key into the m3u8 index file.
[0047]In this step, it is preferable to use a traditional block encryption or stream encryption algorithm to encrypt the video fragment content generated through HLS protocol fragmentation. Further, this layer prefers traditional selective video encryption schemes. Since the video stream format of the HLS protocol fragmentation is ts, the video structure of ts is analyzed in a targeted manner, and the video fragmentation is preferably encrypted with I frame or DCT coefficients, ...
Embodiment 2
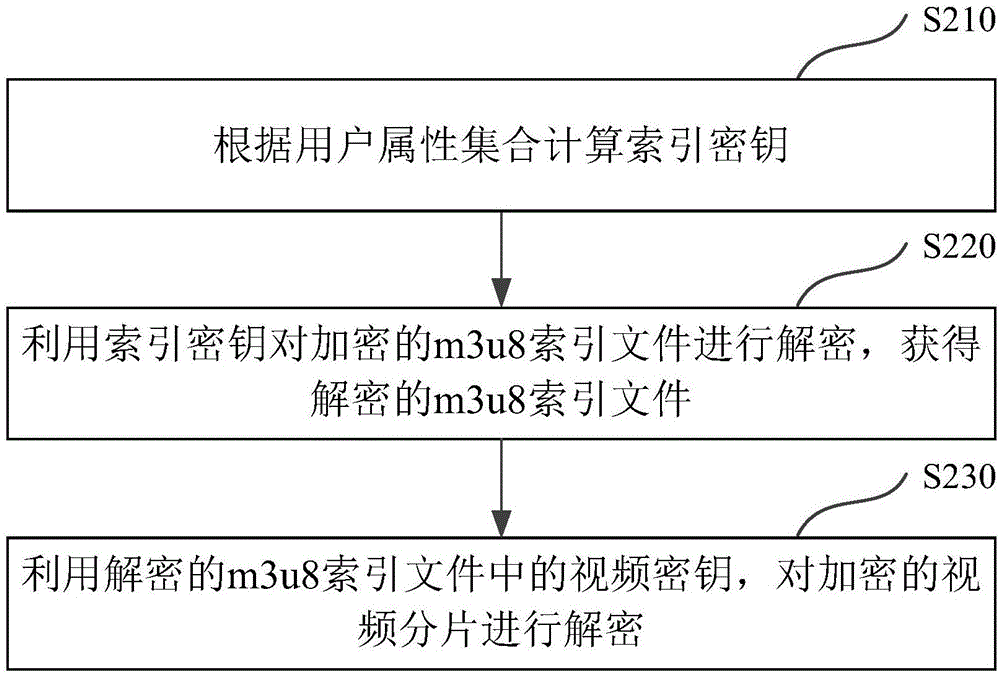
[0074] Figure 4 It is a flow chart of the entire encryption and decryption method for fine-grained streaming media video based on the HLS protocol in an embodiment of the present invention. Combine below Figure 4 Each step and its principle are described in detail from two perspectives of server encryption and terminal decryption.
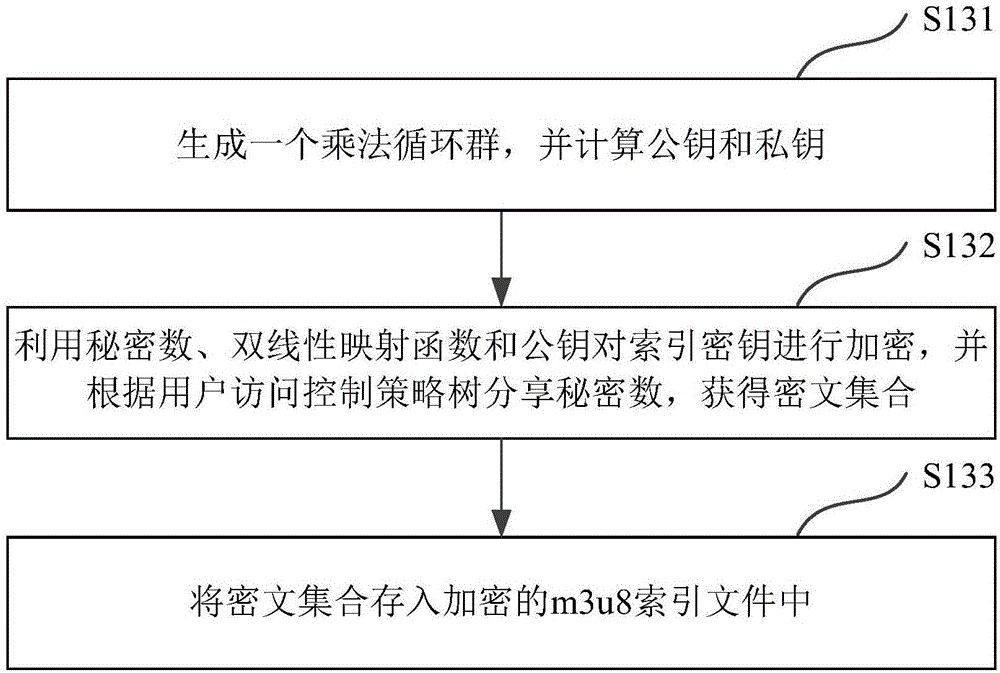
[0075] Figure 5 A flow chart of a fine-grained stream media video encryption method based on the HLS protocol in an embodiment of the present invention is shown. Combine below Figure 4 and Figure 5 From the perspective of server encryption, the steps and principles of encrypting streaming video are explained in detail.
[0076] The first layer of encryption steps: the encryption object is a video segment, the encryption algorithm is preferably the Advanced Encryption Standard (AES, Advanced Encryption Standard) algorithm, and the video encryption key is key video Randomly generated, the specific process of encryption is as follows:
[0...
Embodiment 3
[0104] Taking an ordinary user to order a super-clear video as an example, the working process of the method for encrypting and decrypting streaming media video in the present invention will be described in detail below.
[0105] In order to clearly demonstrate the solutions and beneficial effects of the embodiments of the present invention, before describing the third specific embodiment of the present invention, some definitions of video attributes and user attributes are firstly defined, as shown in Table 1. From this, it is possible to determine the scope of authority for different users to watch videos.
[0106] Table 1 Definition of video attributes and user attributes
[0107]
[0108] Encryption process:
[0109] For an ultra-clear video, after dividing it into different video segments according to the HLS protocol, each video segment selects a different video encryption key for encryption. Save the encrypted video fragments and save the video encryption key at th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com