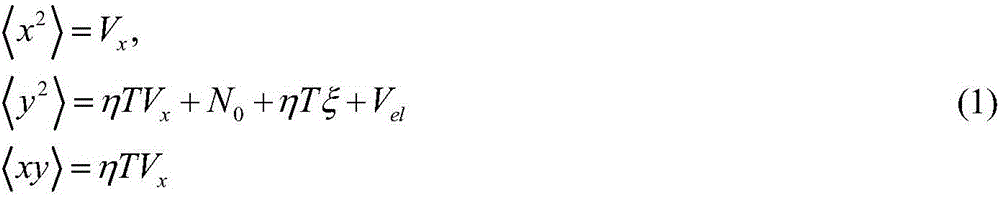Modified continuous-variable quantum key distribution method for resisting actual attack
A quantum key distribution and variable technology, applied in the field of information security, can solve the problems of increasing the complexity of the system, reducing the efficiency of the system detector, and reducing the final key rate of the system, so as to eliminate the effect of limited sampling bandwidth and improve the output encryption. Key rate, the effect of removing finite sampling bandwidth effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be described in detail below in conjunction with specific embodiments. The following examples will help those skilled in the art to further understand the present invention, but do not limit the present invention in any form. It should be noted that those skilled in the art can make several changes and improvements without departing from the concept of the present invention. These all belong to the protection scope of the present invention.
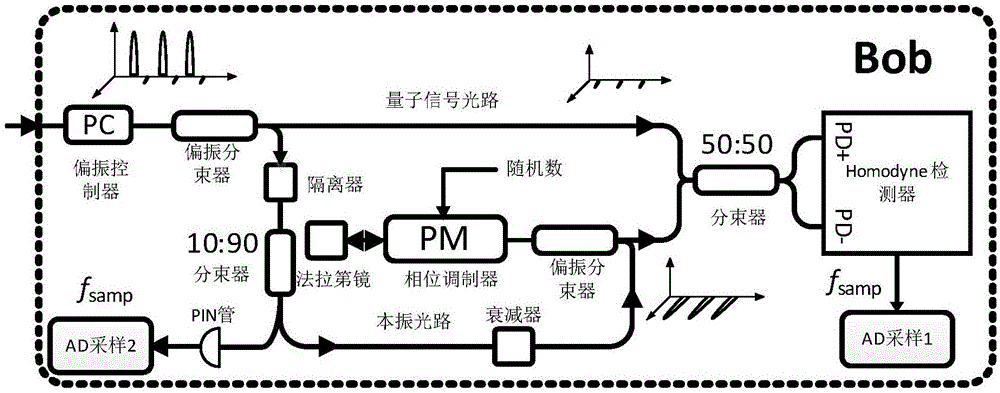
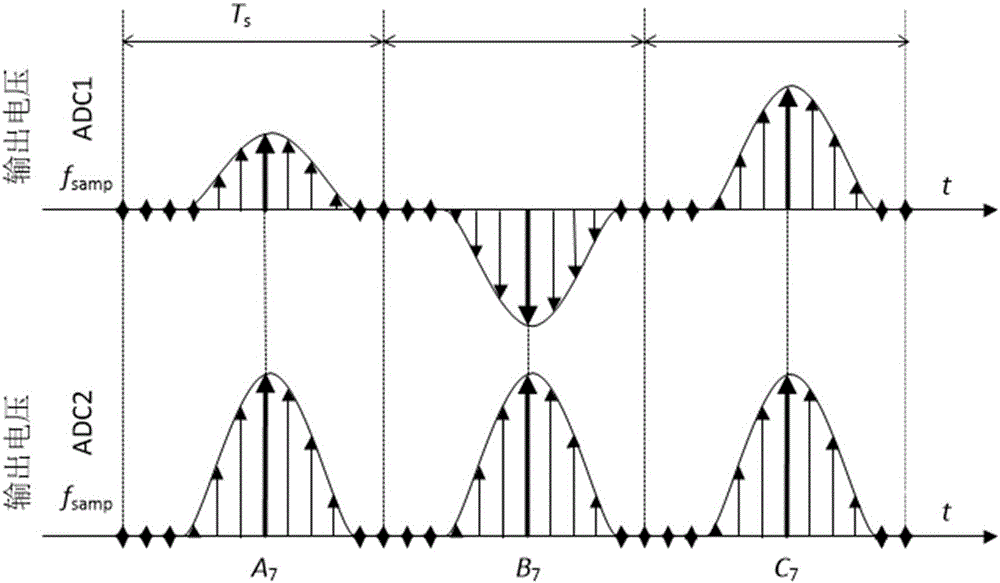
[0040] In view of the defects in the prior art, the purpose of the present invention is to provide a continuous variable quantum key distribution method that can eliminate the limited sampling bandwidth effect and resist actual attacks. The optical monitoring method and data post-processing method are used to defend against existing actual attacks. On the one hand, this method performs real-time intensity monitoring on the basis of the original monitoring of local oscillator light based on an optical pow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com