Application dynamic trusting method in file encryption
An application program and file encryption technology, applied in the field of information security, can solve problems such as error-prone, difficult to configure, heavy workload of policy configuration, etc., and achieve the effect of good prognosis and simple configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
[0014] First, the abbreviations and key terms appearing in this embodiment are explained.
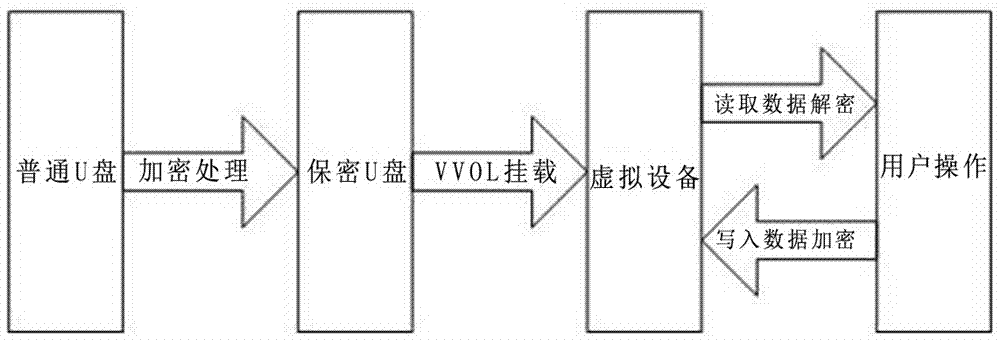
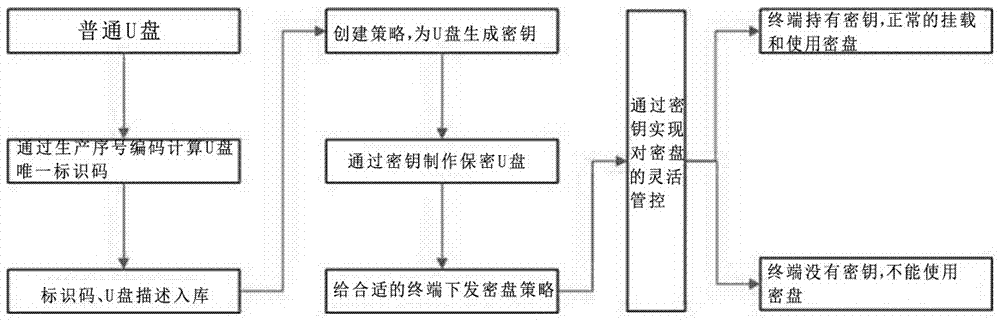
[0015] File encryption: It is a technology that automatically encrypts data written to the storage medium at the operating system layer according to requirements. Currently, the two mainstream methods are disk encryption and file content encryption. The main method of disk encryption is to encrypt the entire disk medium, and all internal data is encrypted regardless of whether it corresponds to a specific file, such as Microsoft's Bitlocker technology. File content encryption is selective encryption according to different specific files. Different files may have different encryption states, such as the file encryption technology contained in the NTFS file system.
[0016] Transparent encryption: Transparent encryption technology is a file encryption tec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com