Method and device for intercepting malicious website access
A malicious URL and purpose technology, applied in the Internet field, can solve problems such as difficulty in extracting URLs, inapplicability, etc., and achieve the effect of improving security performance, preventing malicious network access behavior, and avoiding malicious URL access behavior.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
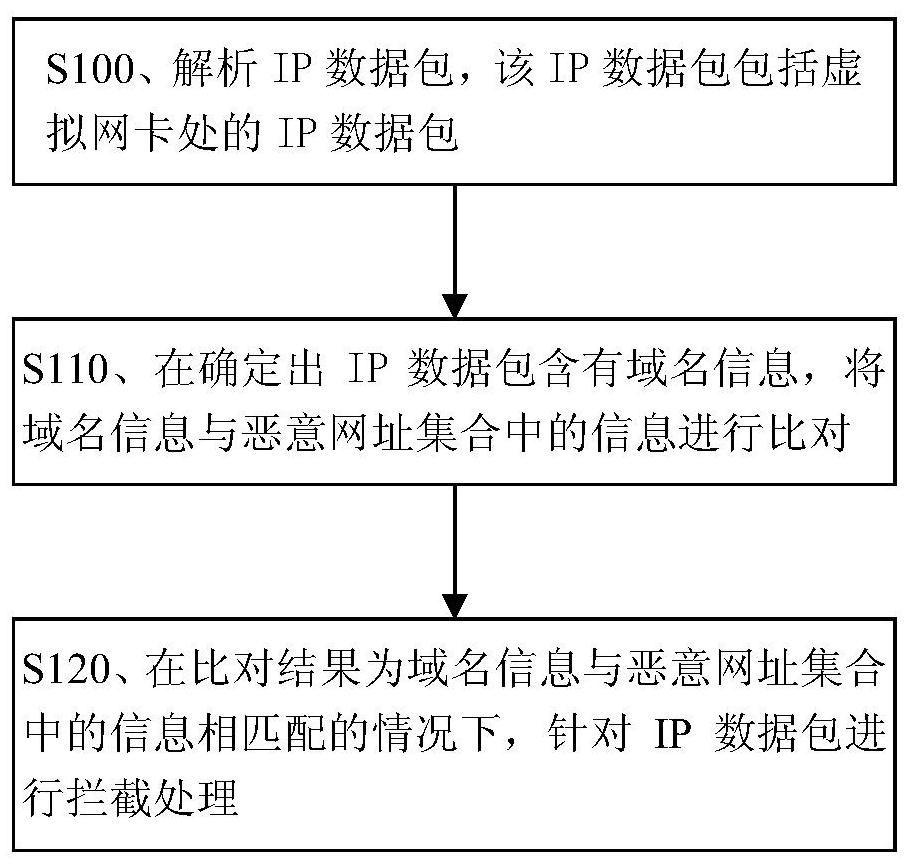
[0037] Embodiment 1. A method for intercepting malicious website access.
[0038] figure 1 It is a flow chart of the method for intercepting malicious website access in this embodiment. Such as figure 1 As shown, the method of this embodiment mainly includes: step S100, step S110 and step S120. The method described in this embodiment is usually executed in smart electronic devices. Preferably, the method described in this embodiment is usually executed in smart electronic mobile devices such as smart mobile phones and tablet computers (ie user mobile devices). .
[0039] next to figure 1 Each step is described in detail.
[0040] S100. Analyzing IP (Internet Protocol, Internet Protocol) data packets.
[0041] Specifically, the IP data packet in this embodiment includes the IP data packet at the virtual network card place. Further, the IP data packet in this embodiment includes the IP data packet at the virtual network card place based on VPN (Virtual Private Network, vir...
Embodiment 2
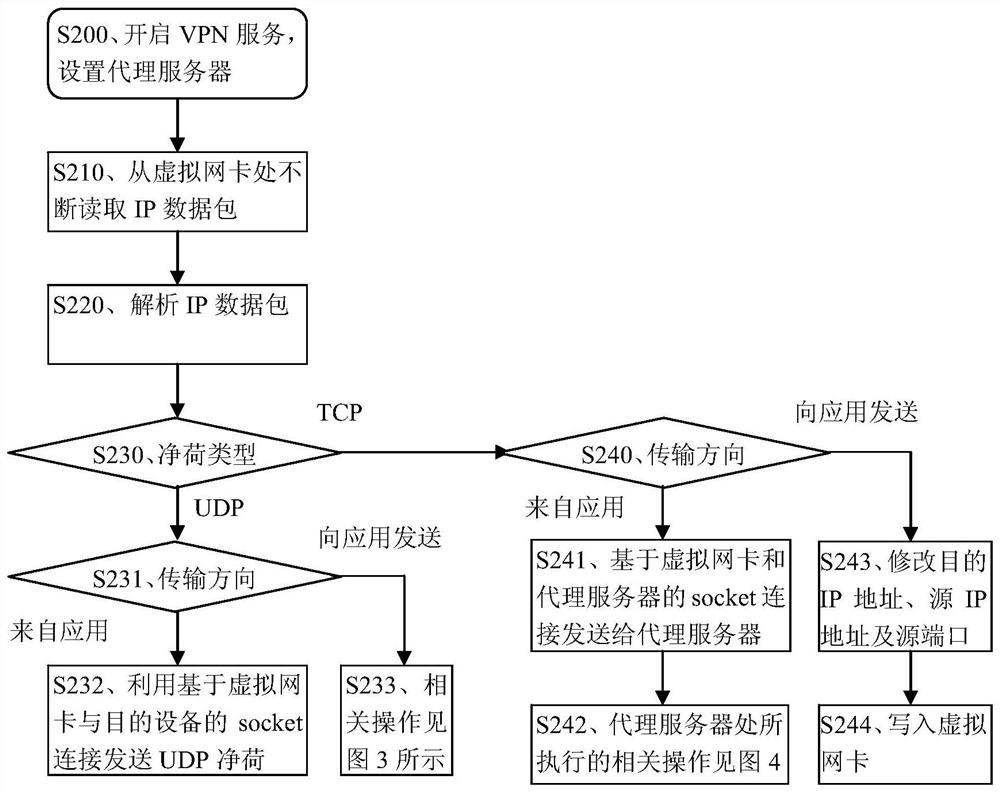
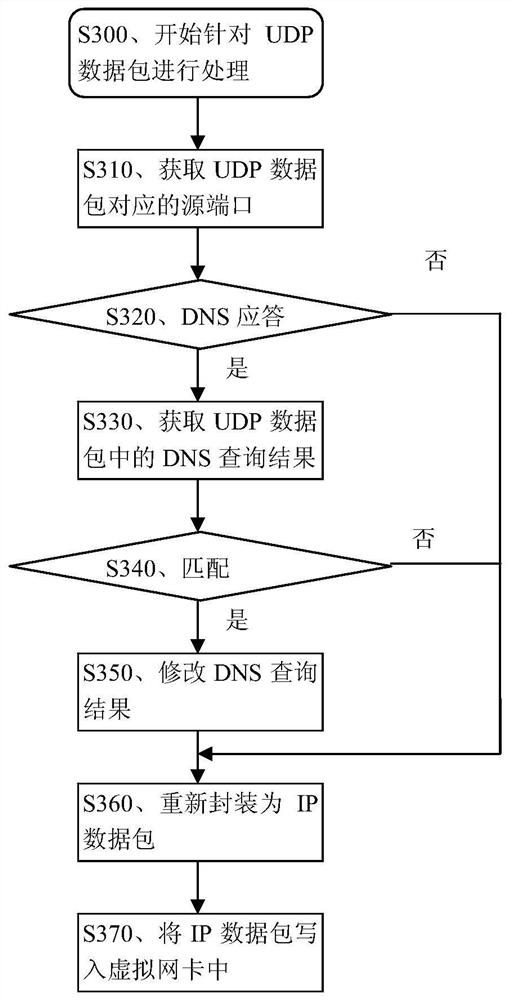
[0086] Embodiment 2, a method for intercepting malicious website access. The procedure of this method is as follows Figure 2-Figure 4 shown.
[0087] figure 2 In, S200, open the VPN service supported by the Andriod operating system in the intelligent electronic device, set the relevant parameters of the virtual network card, set the IP address of the virtual network card to be VirtualIP; set the proxy server in the intelligent electronic device, and set the proxy server The IP address and port are ProxyIp and ProxyPort respectively. to S210.
[0088] The proxy server in this embodiment is mainly used for listening to the socket connection request, and when listening to the socket connection request, agrees the socket connection or rejects the answer of the socket connection to the socket connection request; the proxy server is also used for agreeing the socket connection Afterwards, a TCP session (TCP session) is established for the socket connection, so that operations ...
Embodiment 3
[0116] Embodiment 3, the implementation device for intercepting malicious website access.
[0117] The structure of the implementation device for intercepting malicious website access in this embodiment is as follows: Figure 5-Figure 12 shown.
[0118] Figure 5 The device mainly includes: a resolution module 510, a domain name information comparison module 540, and an interception processing module 550. Optionally, the device may further include: any one or more of a reading module 500 , a first judging module 520 , a first transmission processing module 530 , a second transmission processing module 560 and a third judging module 570 .
[0119] The parsing module 510 is mainly used for parsing IP data packets. The parsing module 510 in this embodiment can be independent of Figure 12 The virtual network card packet processing module in the network can be set independently, of course, it can also be set in Figure 12 In the virtual network card packet processing module. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com