Modular multiplication device and method
A kind of equipment, technology of multiplication, applied in the field of modular multiplication method and equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
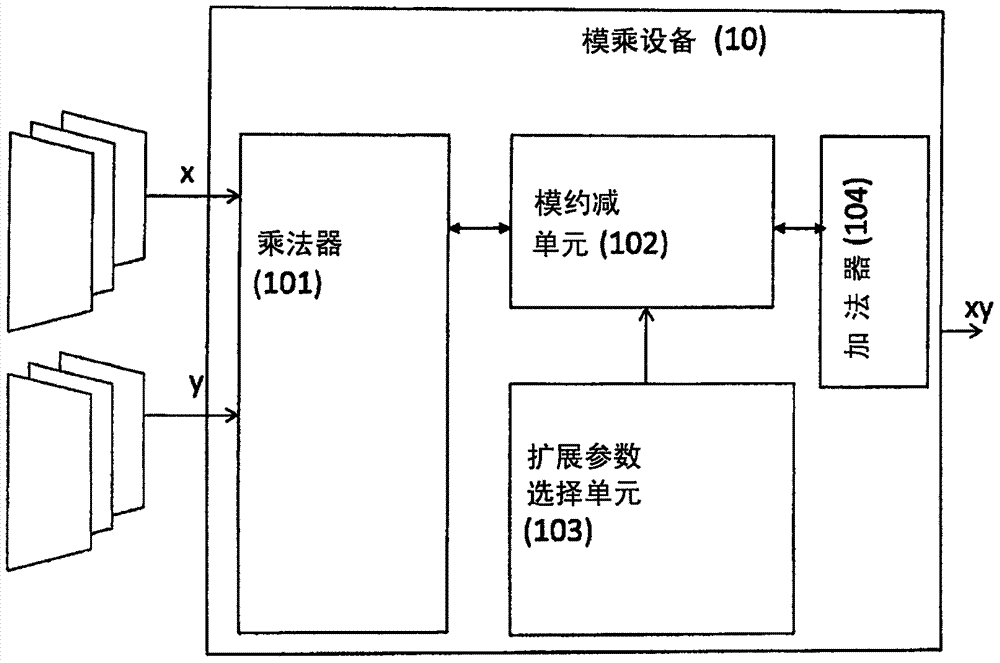
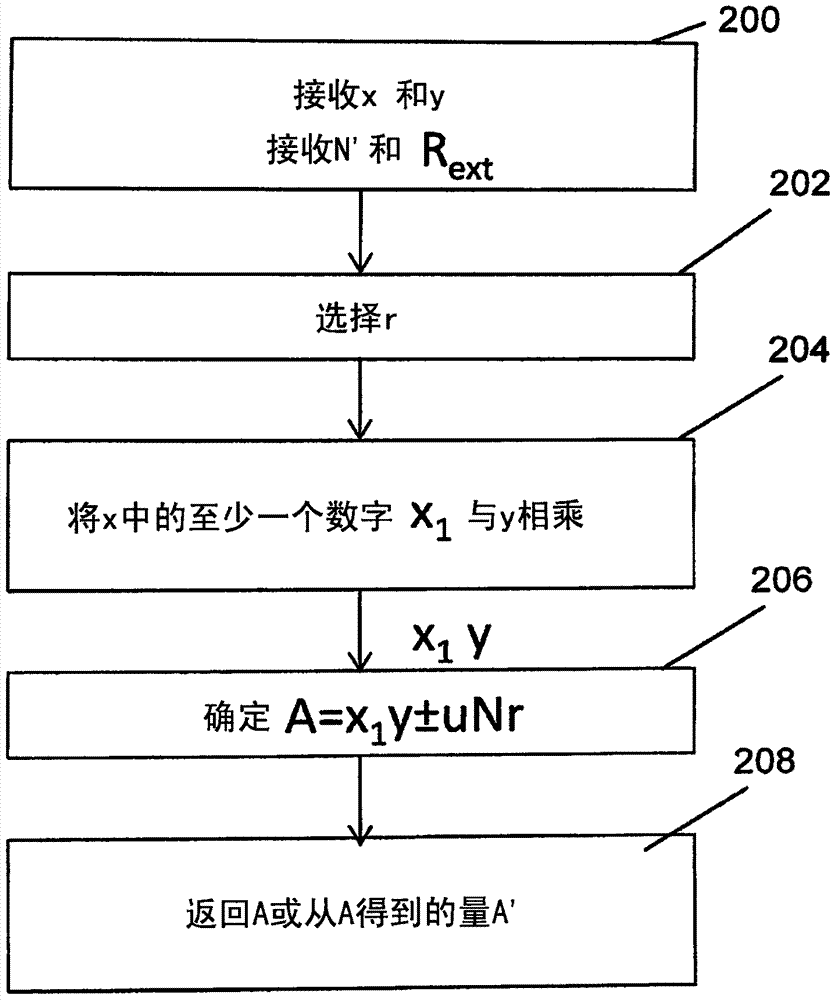
[0061] Embodiments of the present invention provide an improved modular multiplication method and apparatus for determining the result of a modular multiplication of two multiplicands, each of which includes a plurality of numbers.
[0062] Embodiments of the present invention further provide cryptographic systems and methods that use the results of such modular multiplication methods and devices in cryptographic operations to ensure protection of cryptographic systems and methods from attacks conventionally based on the observation of additional reductions. Exemplary cryptographic operations include encryption, decryption operations, signing and authentication operations. For purposes of illustration only, the following description of certain embodiments will be made with reference to, for example, encryption and / or decryption operations.
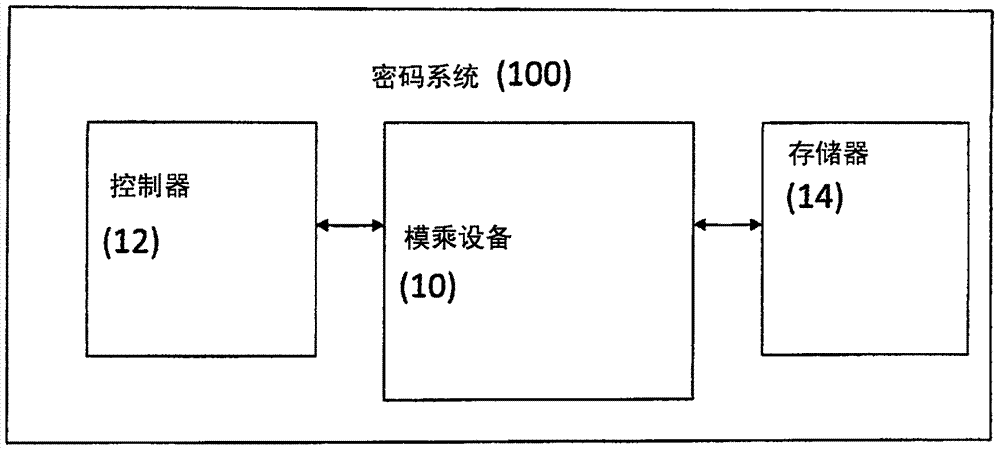
[0063] refer to figure 1 , represents a cryptographic system 100 according to some embodiments of the present invention. The cryptograp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com