Optimum power allocation method for untrusted relay network under bounded CSI (Channel State Information)
A relay network, optimal power technology, applied in power management, wireless communication, electrical components, etc., can solve problems such as the impossible realization of CSI, and achieve the effect of reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the accompanying drawings and embodiments, and the present invention includes but not limited to the following embodiments.
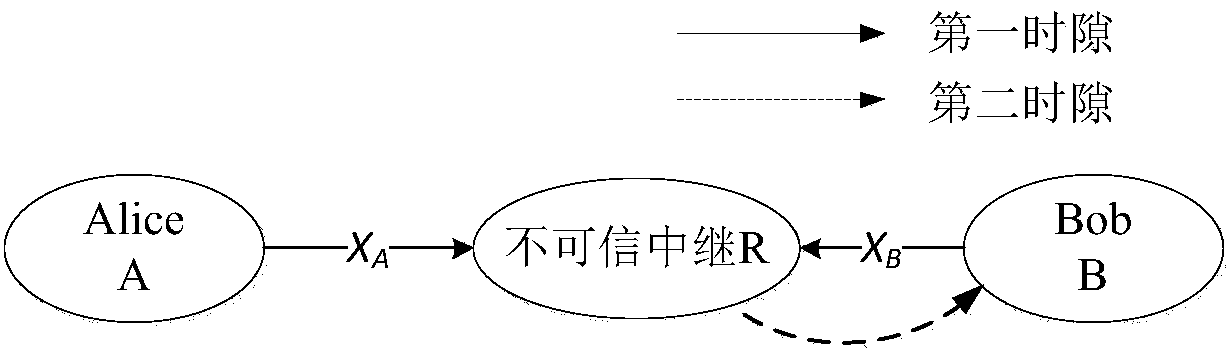
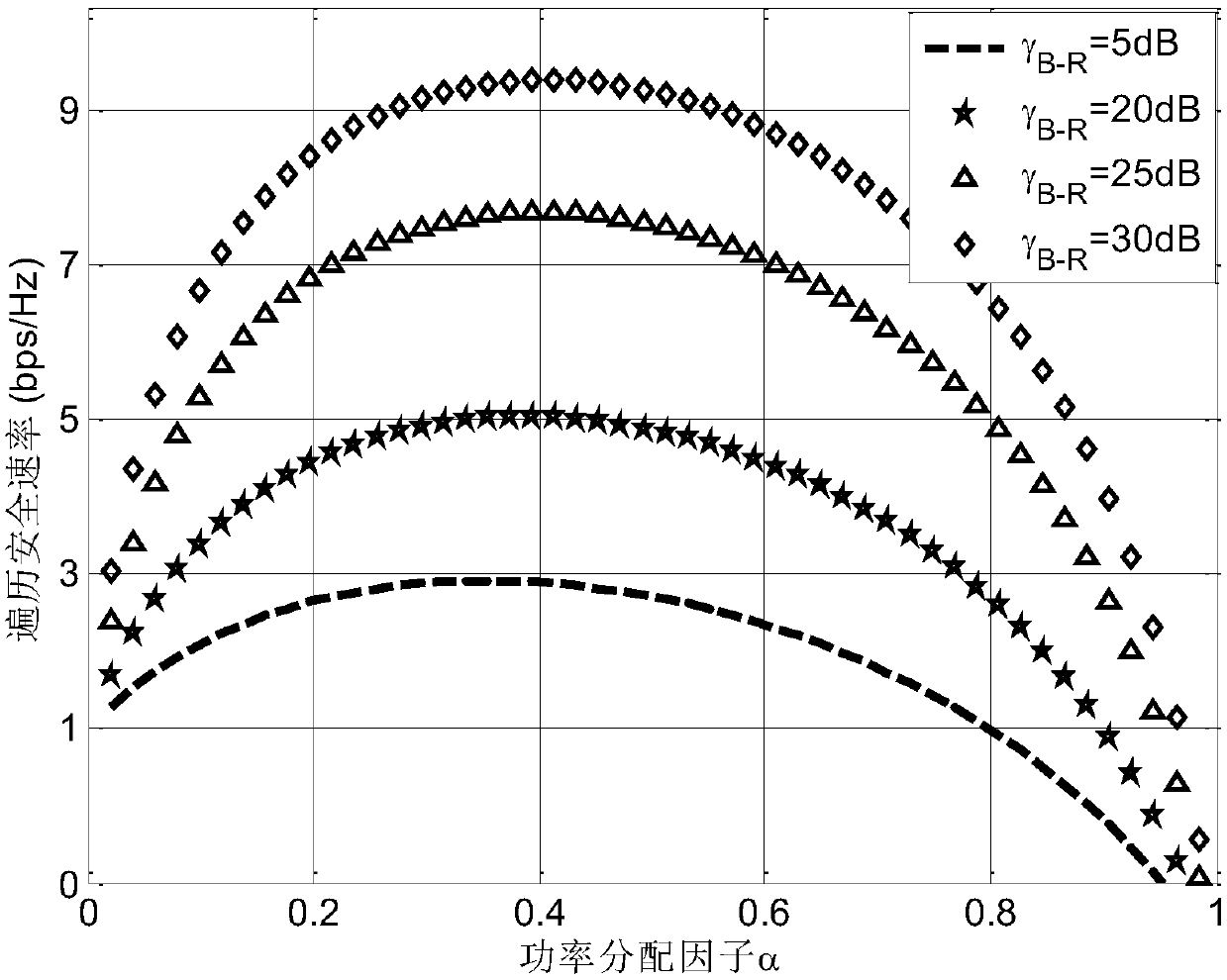
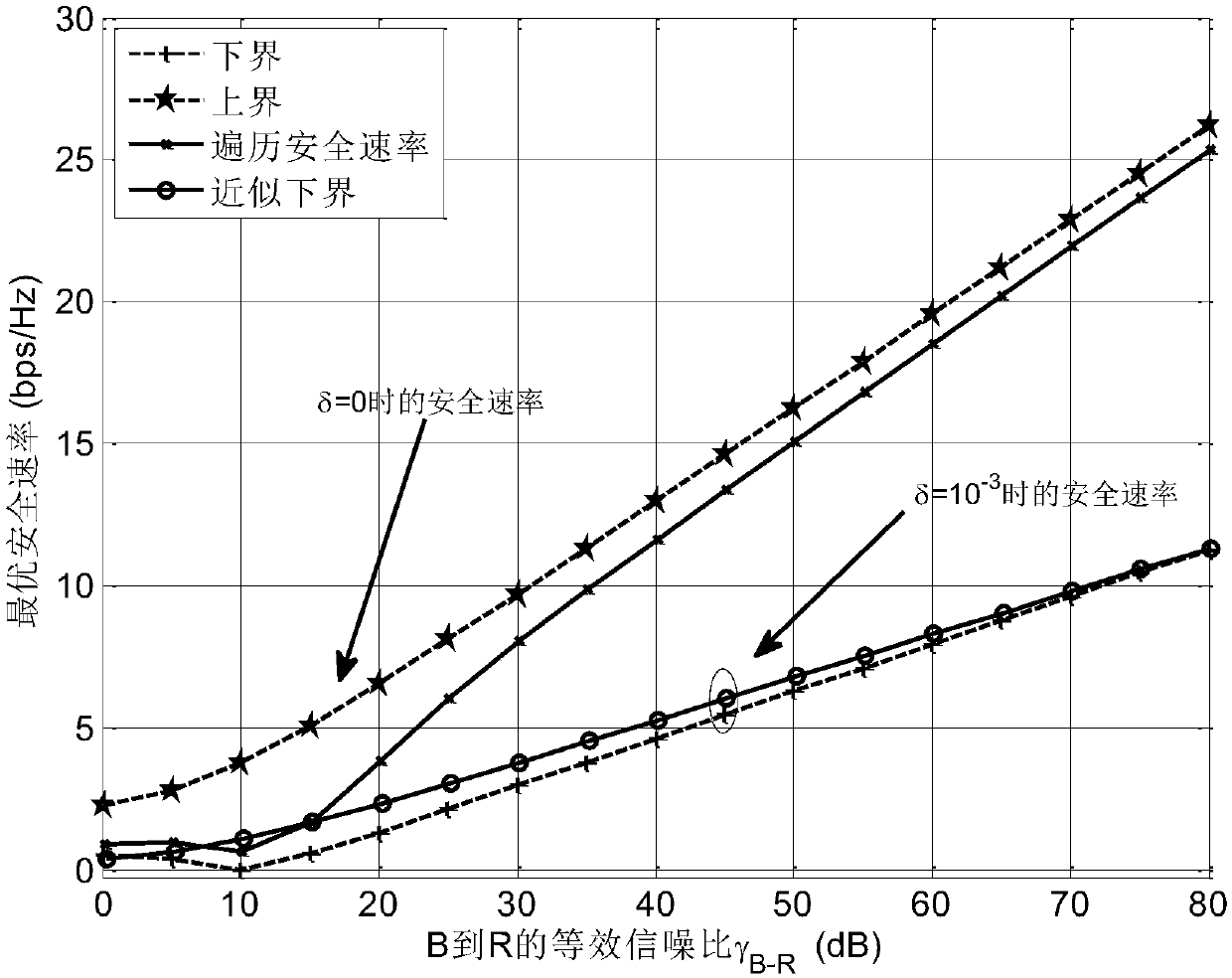
[0036] The system model used in the present invention is a relay network with three nodes, its principle is as follows figure 1 shown. The model consists of a source node (Alice), an untrusted amplify-and-forward relay node (R) and a destination node (Bob). Each node uses a single-antenna configuration, and a transmission process requires 2 time slots to complete. Assuming that there is no direct communication link between Alice and Bob due to shadow fading or too far away, they can only communicate through an untrusted relay node R. In the first time slot, Alice transmits information x to the untrusted relay node R A , at the same time Bob transmits information x to the untrusted relay node R B . In the second time slot, the relay node R re-sends the received signal to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com