User identification system based on keystroke rhythm and identification method thereof
A user identification and identification module technology, applied in the field of user identification, can solve the problems of increasing difficulty and requirements of user identification, inability to prevent illegal operations of operators in time, and inability to perceive changes in operator identification, and achieve enhanced resistance The ability of illegal intrusion, the reduction of access thresholds, and the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The examples are described in detail below in conjunction with the accompanying drawings.
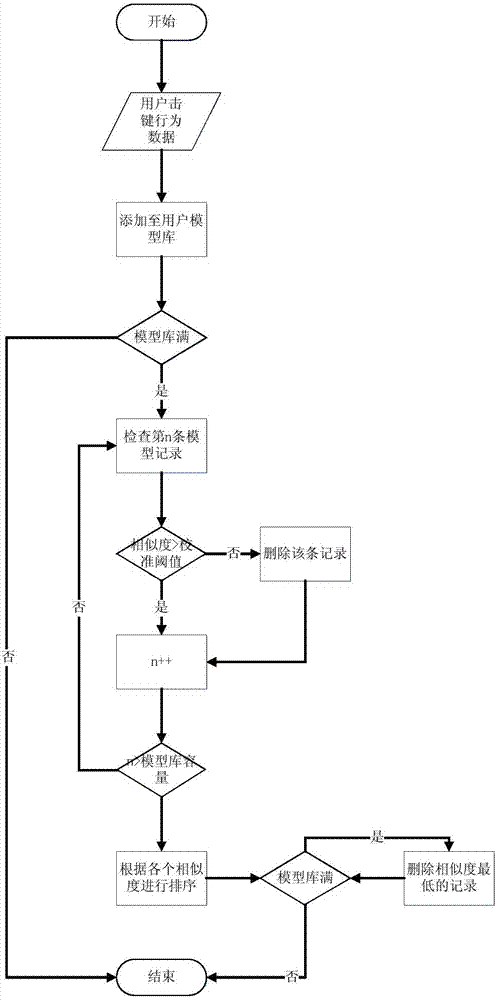
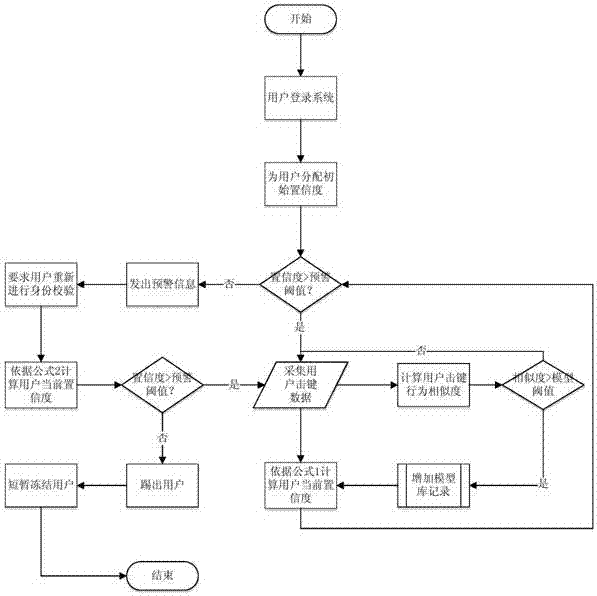
[0046] The present invention proposes a user identification system based on the keystroke rhythm of the user. After the user logs in, the system will continuously collect and analyze all the keystroke operation data of the user during the login period, and perform confidence detection according to the user feature database. If the user's confidence is lower than the preset early warning threshold, the system will The third-party business system will be notified to re-verify the user's identity, and at the same time, the user's behavior will be controlled according to the verification result.
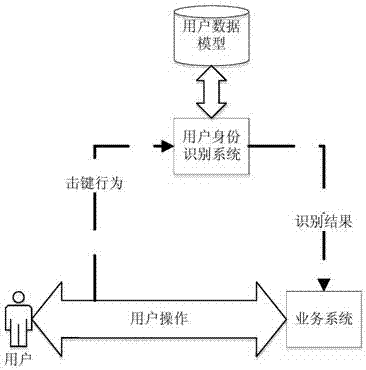
[0047] figure 1 Shown is a schematic diagram of integration between this system and a third-party business system. The user identification system integrates with third-party business systems in a plug-and-play modular form. The user identification system collects the user's keystroke ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com