Method and apparatus for verifying authenticity of electronic archives
An electronic file and verification method technology, applied in the field of data security, can solve the problems of inability to effectively ensure the accuracy of verification results and low security, and achieve the effect of being difficult to forge and ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
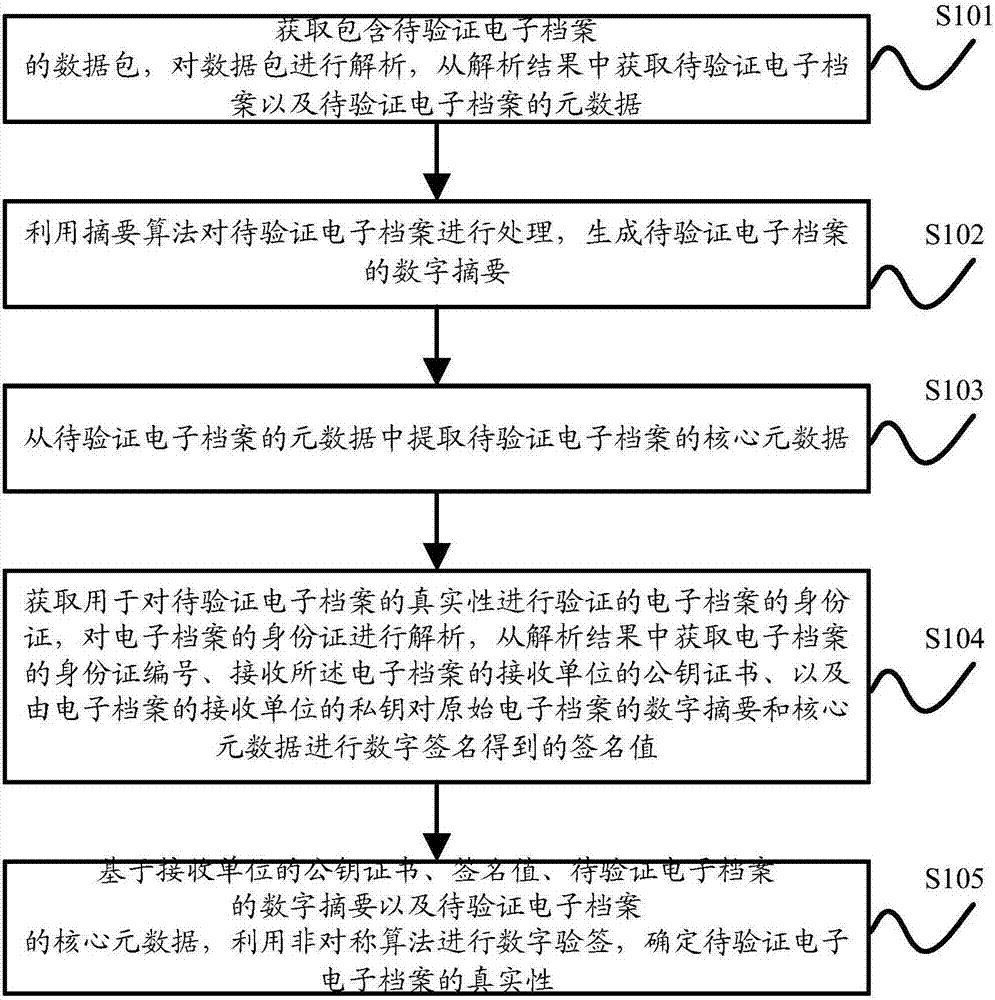
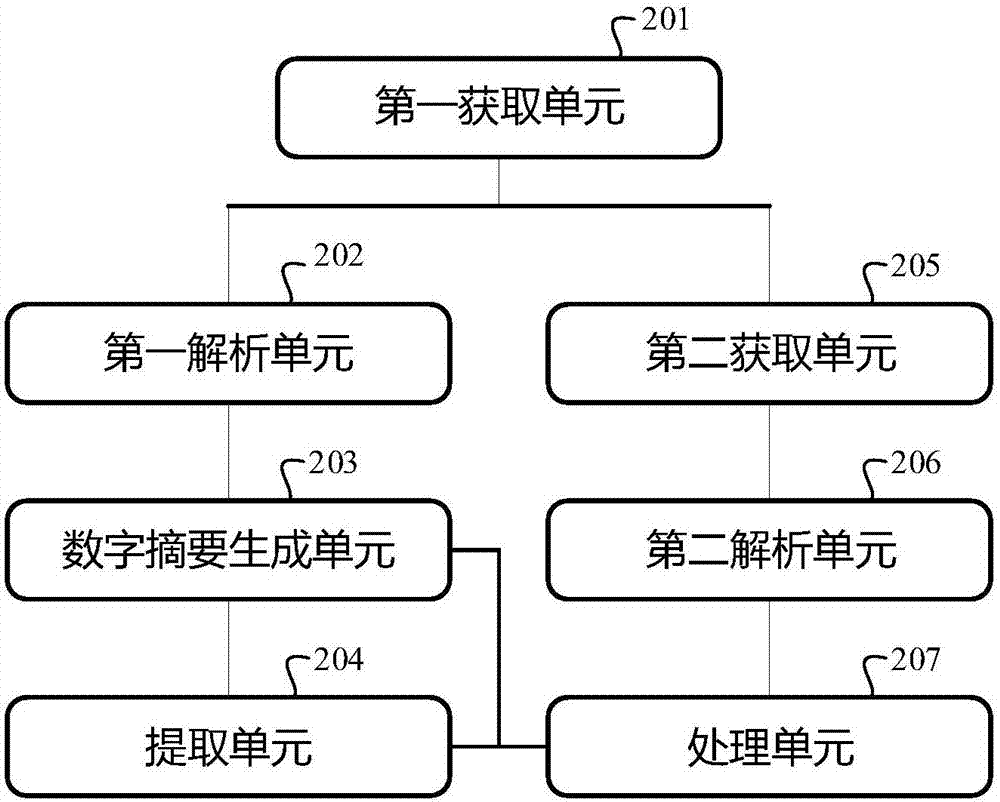
[0041] In the specific implementation step S104, when acquiring the ID card of the electronic file used for verifying the authenticity of the electronic file to be verified, the following two implementation manners are included, specifically:
Embodiment approach 1
[0042] Implementation mode one, "online" acquisition
[0043] Obtain the file number of the electronic file to be verified from the metadata of the electronic file to be verified, and obtain the ID card of the electronic file used to verify the authenticity of the electronic file to be verified from the server storing the electronic file ID according to the file number.
[0044] It should be noted that the ID card of the electronic file in this embodiment is obtained from the server, which is commonly referred to as "online" acquisition. Since the ID card of the electronic file is stored in the server, it is difficult to forge or tamper with. Therefore, this implementation The method is suitable for scenarios with high security requirements. However, the ID card of the electronic file in this embodiment is stored in the server. When obtaining the ID card of the electronic file from the server, it is necessary to access the server online to obtain it.
Embodiment approach 2
[0045] Implementation mode two, "offline" acquisition
[0046] Obtain from the data package of the electronic file to be verified the identity card of the electronic file used to verify the authenticity of the electronic file to be verified.
[0047] It should be noted that, corresponding to the “online” acquisition, in this embodiment, the ID card of the electronic file is included in the data packet of the electronic file to be verified. When the ID card of the electronic file is obtained, it can be directly obtained from the electronic file to be verified. In the process of obtaining the ID card of the electronic file, there is no need to access the server, which is commonly referred to as "offline" acquisition. The "offline" acquisition method has lower security than the "online" acquisition method in the first embodiment. Therefore, this embodiment is suitable for application scenarios with lower security requirements.
[0048] It is worth noting that, in order to further impro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com