Method, electronic device and computer program for providing a hash value for a piece of data
An electronic device, hash value technology, applied in digital data protection, electrical components, digital transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Certain embodiments disclosed herein relate generally to the technical field of security, and more specifically to the field of hash functions. In order to more easily understand the contribution of the present invention, an introduction to the mechanism for providing the hash function used for timestamping is presented below. To further facilitate reading of this disclosure, commonly used abbreviations are listed below.
[0031] abbreviation
[0032] abbreviation word Explanation
[0033] Expansion of BLT KSI
[0034] CRH Calendar Root Hash
[0035] GW Gateway
[0036] KSI Keyless Signature Infrastructure
[0037] HMAC specific message authentication code algorithm construction
[0038] MAC message authentication code algorithm (general)
[0039] PKI public key infrastructure
[0040] TSA Timestamp Authorization
[0041] PKI public key infrastructure
[0042] QI-KSI Quantum immune KSI, such as BLT
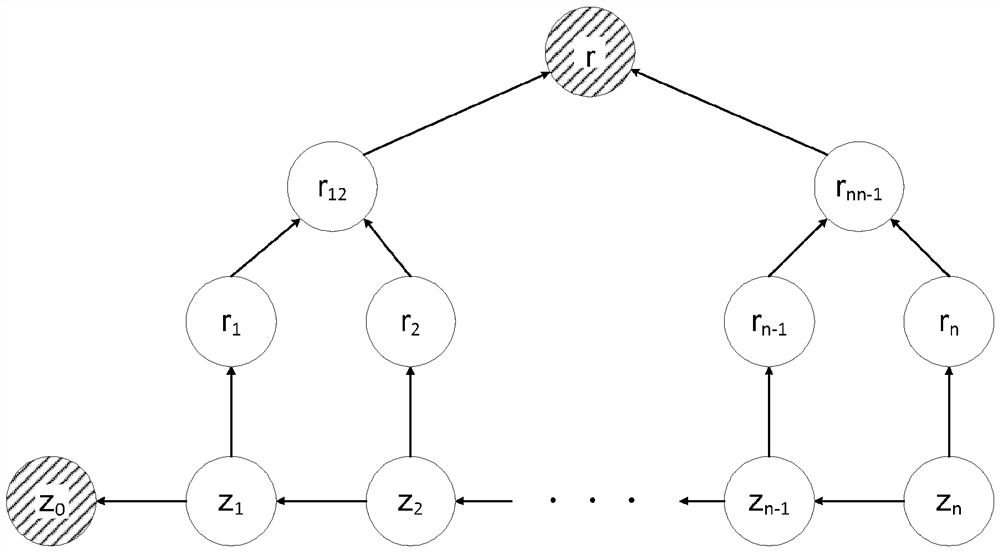
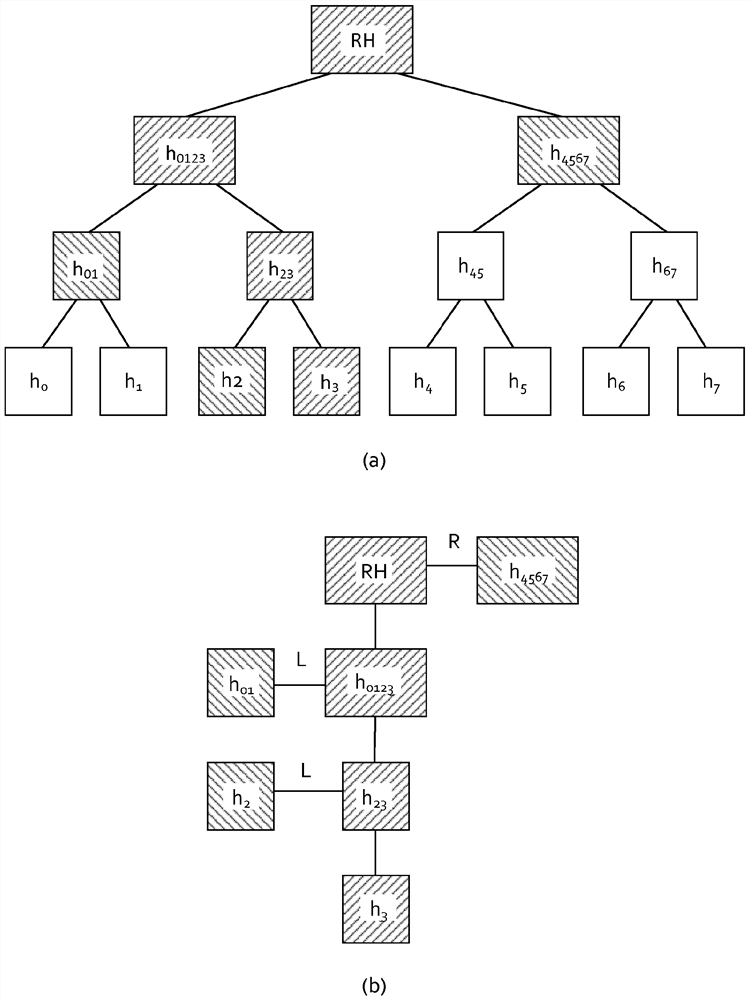
[0043] Root hash of RH Merkle type tree
[0044] Has...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com