Information processing method and device
A technology for configuring information and private information, applied in the field of information processing, can solve problems such as peeking at private information, suddenly receiving text messages or emails, and user privacy cannot be protected, so as to achieve the effect of protecting privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
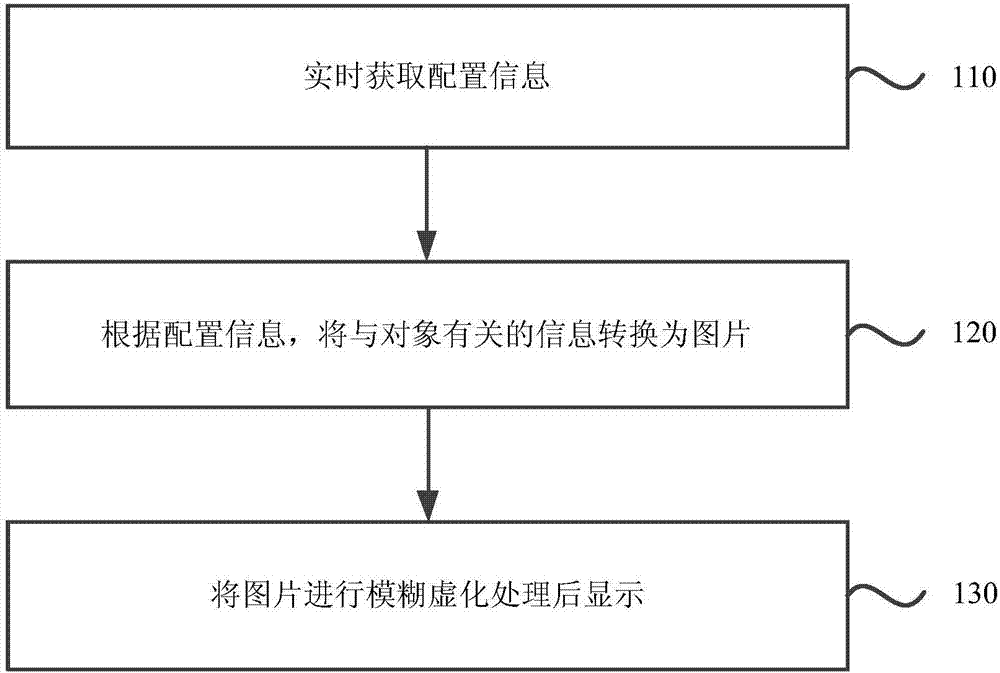
[0020] figure 1 It is a flow chart of an information processing method provided by Embodiment 1 of the present invention. This embodiment is applicable to situations where information in electronic equipment needs to be protected. The method can be executed by an information processing device, which can be implemented by software and\or hardware, and generally can be integrated in electronic equipment. The method provided in this embodiment specifically includes the following steps:
[0021] Step 110, obtaining configuration information in real time.
[0022] Wherein, the configuration information is used to configure the object of the private information.
[0023] Optionally, a setting list of privacy information objects may be set in the electronic device, wherein the options in the setting list may include preset applications, and sub-options may also be included under the options of each preset application , where the sub-options can include the contact accounts in the ...
Embodiment 2
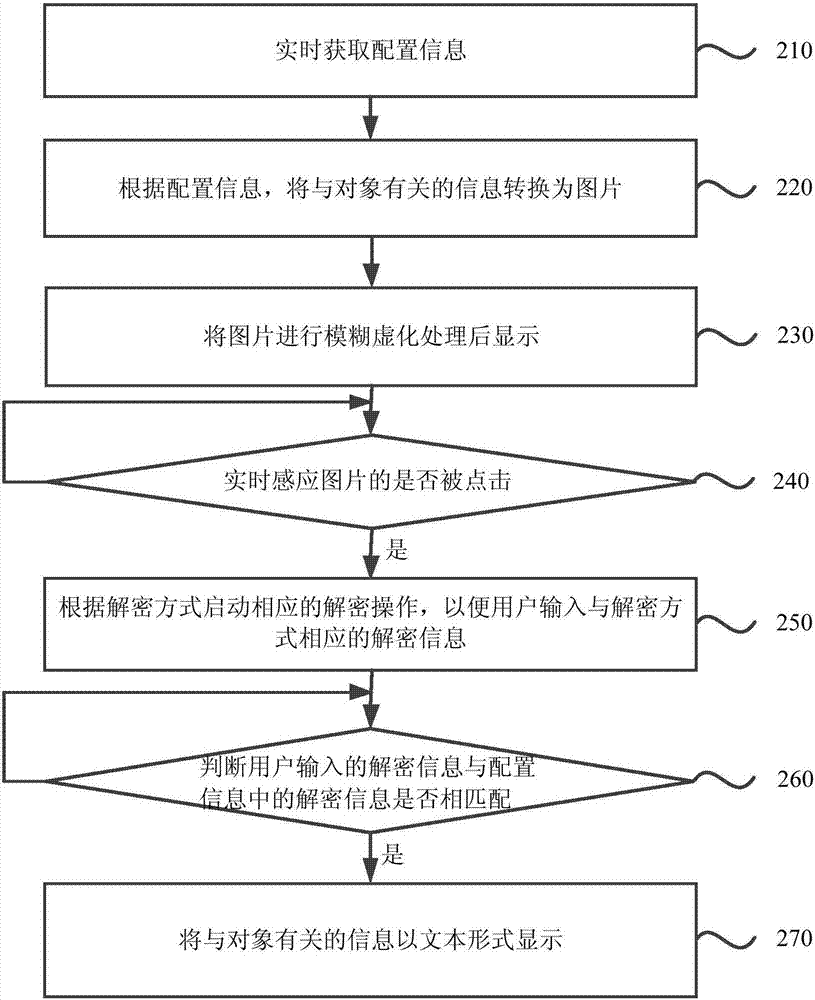
[0041] figure 2 It is a flow chart of an information processing method provided by Embodiment 2 of the present invention. This embodiment is for further optimization on the basis of the above embodiments. The method provided by this embodiment includes:
[0042] Step 210, obtaining configuration information in real time.
[0043] Wherein, the configuration information is used to configure the object of the private information, configure the decryption method of the private information and the corresponding decryption information.
[0044] Preferably, after the object of the private information is set, the corresponding decryption method and corresponding decryption information can also be set.
[0045] Wherein, different private information may be configured with the same decryption method and corresponding decryption information, or may be configured with different decryption methods and corresponding decryption information, which is not limited in the present invention.
[...
Embodiment 3
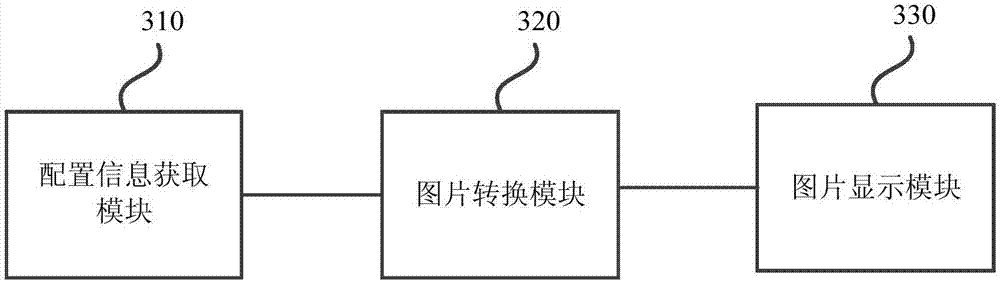
[0066] image 3 It is a structural block diagram of an information processing device provided by Embodiment 3 of the present invention. The device is suitable for protecting information in electronic equipment, can be composed of software and / or hardware, and can generally be integrated in electronic equipment. The device provided in this embodiment includes: a configuration information acquisition module 310, a picture conversion module 320 and a picture display module 330, wherein,
[0067] The configuration information acquisition module 310 is configured to acquire configuration information in real time, and the configuration information is used to configure objects of private information;
[0068] A picture conversion module 320, configured to convert information related to the object into a picture according to the configuration information;
[0069] The picture display module 330 is configured to perform blurring and blurring on the picture and then display it.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com