Method, apparatus and system for decrypting cloud payment limiting key
A cloud payment and key technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., to resist malicious attacks and solve security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0069] refer to figure 1 , figure 1 A flowchart of an embodiment of a method for decrypting a cloud payment restriction key provided by the present invention is shown. The method of this embodiment is applied to a server, and the method includes: Step S110.
[0070] In step S110, use multiple private key fragments to iteratively restore the elliptic curve points and then perform private key decryption; the calculation results of the multiple private key fragments are equivalent to the corresponding private key calculation results, and the decryption process is not complete. The private key appears.
[0071] Due to the fragility of mobile terminals, there is a risk of private key exposure no matter whether the private key is stored or used. In the technical solution of the present invention, there is no complete private key in the decryption process, which solves the security of the key in an untrusted environment, so that the key does not appear completely in the process of...
Embodiment 2
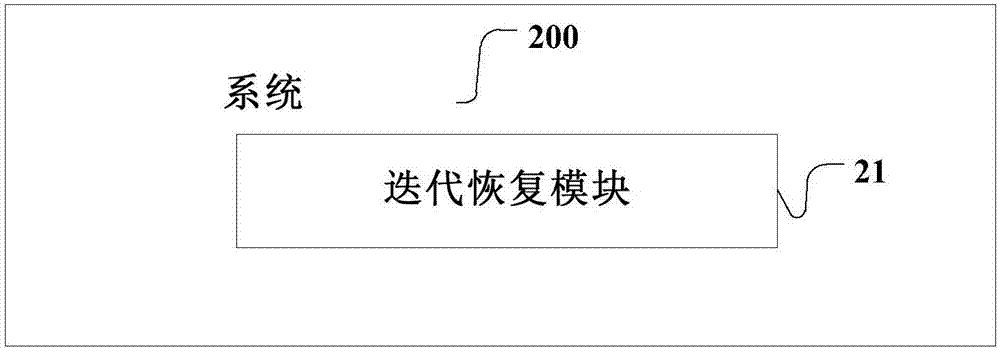
[0115] refer to figure 2 , figure 2 A structural block diagram of an embodiment of a system 200 for decrypting a cloud payment restriction key provided by the present invention is shown. The method of this embodiment is applied in the server, including:
[0116] The iterative recovery module 21 is used to iteratively restore the elliptic curve points using a plurality of private key fragments to perform private key decryption; the operation results of the respective iterations of the plurality of private key fragments are equivalent to the operation results of the corresponding private key, and the decryption process No full private key present. The functions and implementation methods of this module can refer to Embodiment 1 and figure 1 .
[0117] Further, the iterative recovery module includes:
[0118] a receiving unit, configured to receive the elliptic curve points sent by the input device;
[0119] a judging unit for sequentially judging the type of the private ...
Embodiment 3
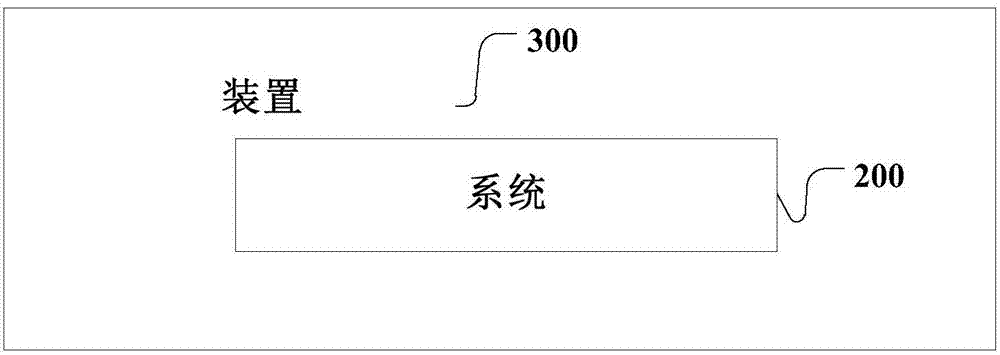
[0139] refer to image 3 , image 3 It shows an apparatus 300 for decrypting a cloud payment restriction key provided by the present invention, including the system 200 described in any one of the second embodiment.
[0140] Embodiment 3 of the present invention provides a device for decrypting the cloud payment restriction key, which uses multiple private key fragments to iteratively restore the elliptic curve point and then performs private key decryption; the multiple private key fragments respectively iterate the operation The result is equivalent to the operation result of the corresponding private key, and there is no technical solution for the complete private key in the decryption process, which can effectively resist malicious attacks of unauthorized access to private data. The technology of multi-fragment iterative operation is adopted, and no complete private key appears in the whole decryption process, thereby solving the security problem of mobile terminal privat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com