Cloud computing system security assessment method and device
A system security, computing system technology, applied in the direction of platform integrity maintenance, etc., can solve the problem of lack of specific implementation solutions for security assessment methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
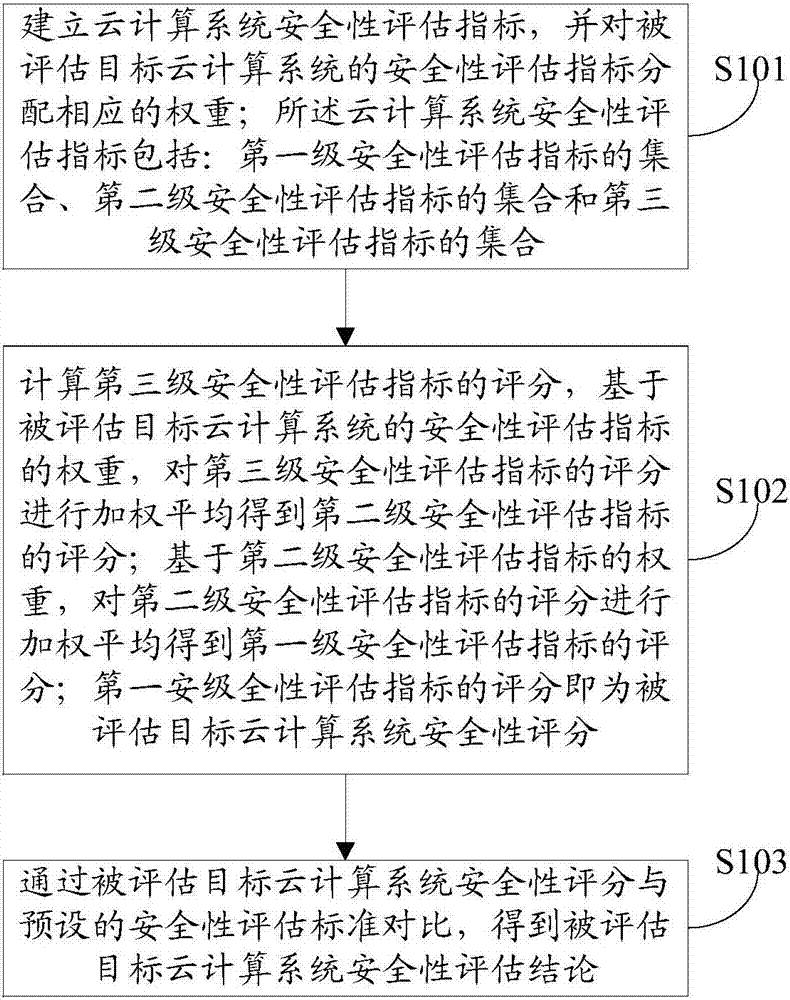
[0081] In the first embodiment of the present invention, a method for evaluating the security of a cloud computing system, such as figure 1 shown, including the following specific steps:
[0082] Step S101, establishing cloud computing system security evaluation indicators, and assigning corresponding weights to the security evaluation indicators of the evaluated target cloud computing system; the cloud computing system security evaluation indicators include: a set of first-level security evaluation indicators , a set of second-level security assessment indicators and a set of third-level security assessment indicators.
[0083] Specifically, step S101 includes:
[0084] Cloud computing system security evaluation indicators, including a collection of first-level security evaluation indicators: technical requirements evaluation indicators.
[0085] Among them, the score of the technical requirements evaluation index is obtained by the weighted average of the scores of the fol...
no. 2 example
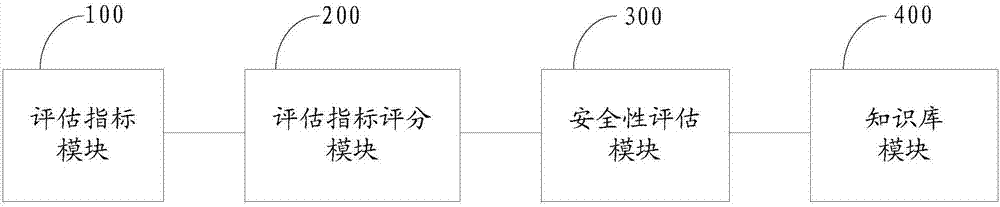
[0115] In the second embodiment of the present invention, a cloud computing system security evaluation device, such as figure 2 shown, including the following components:
[0116] The evaluation index module 100 is used to establish a cloud computing system security evaluation index, and assign corresponding weights to the security evaluation index of the evaluated target cloud computing system; the cloud computing system security evaluation index includes: a first-level security evaluation index A collection of , a collection of second-level security evaluation indicators, and a collection of third-level security evaluation indicators.
[0117] If the security evaluation indicators of the evaluated cloud computing system are independent of each other, then according to the results of repeated cloud computing system security experiments and cloud computing system simulation security experiments, assign the weight of the cloud computing system security evaluation indicators; ...
no. 3 example
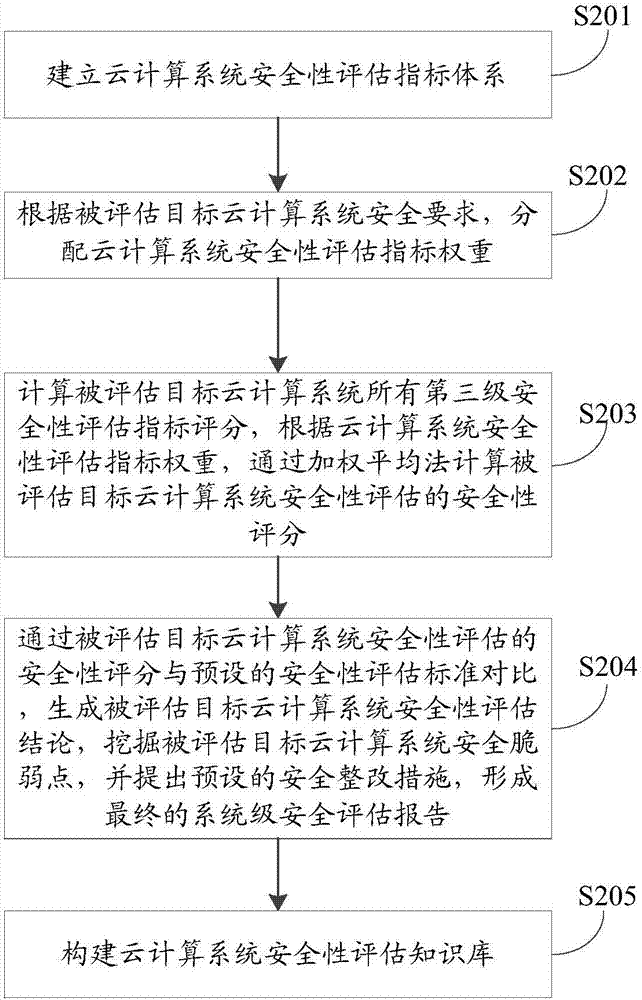
[0144] In the third embodiment of the present invention, a method for evaluating the security of a cloud computing system, such as figure 1 shown, including the following specific steps:
[0145] Step S201, establishing a cloud computing system security evaluation index system.
[0146] Specifically, step S201 includes:
[0147]Cloud computing system security evaluation index system, including the first-level security evaluation index set: technical requirements evaluation index and management requirements evaluation index;
[0148] Among them, the technical requirement evaluation index includes a set of second-level security evaluation index: IaaS evaluation index, PaaS evaluation index, SaaS evaluation index and common security evaluation index.
[0149] IaaS evaluation indicators, including a set of third-level security evaluation indicators: physical and environmental security, network security, host system security, virtualization security, and storage security;
[015...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com