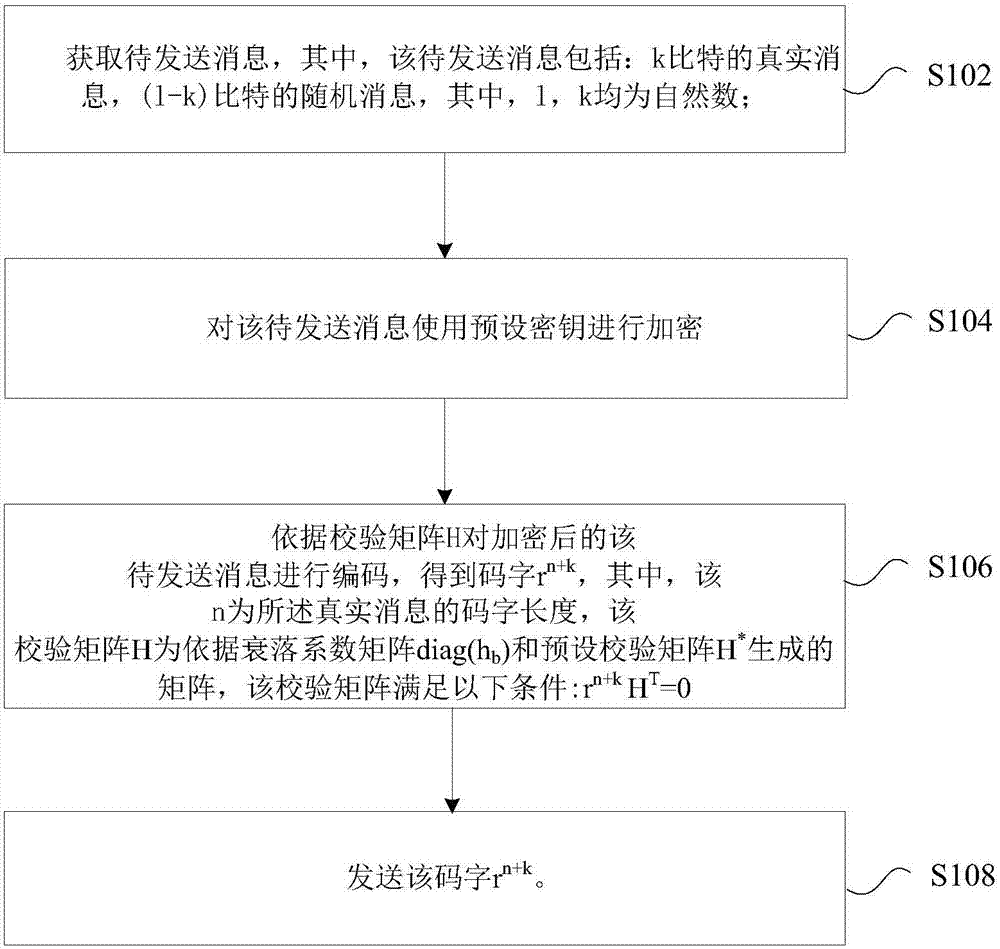
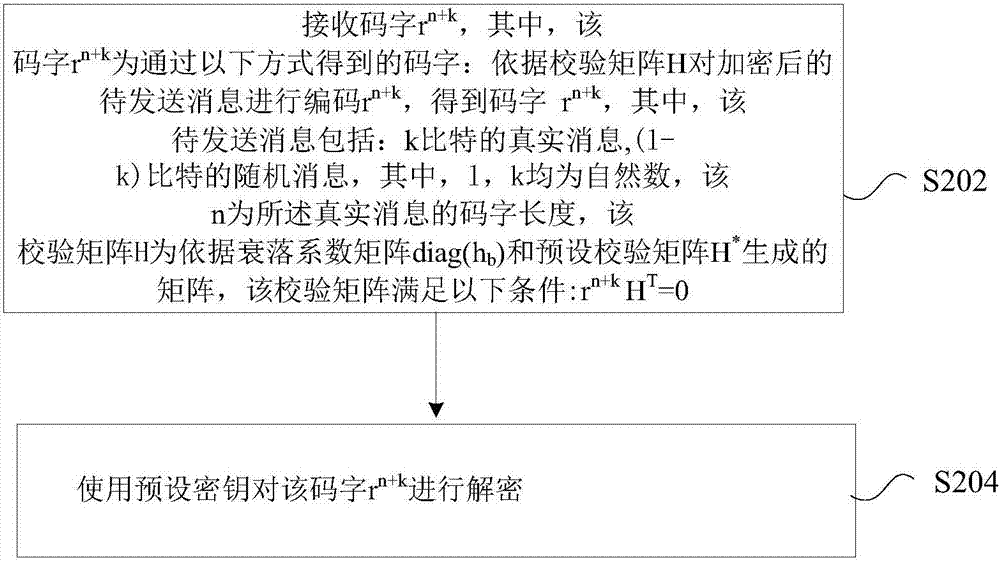
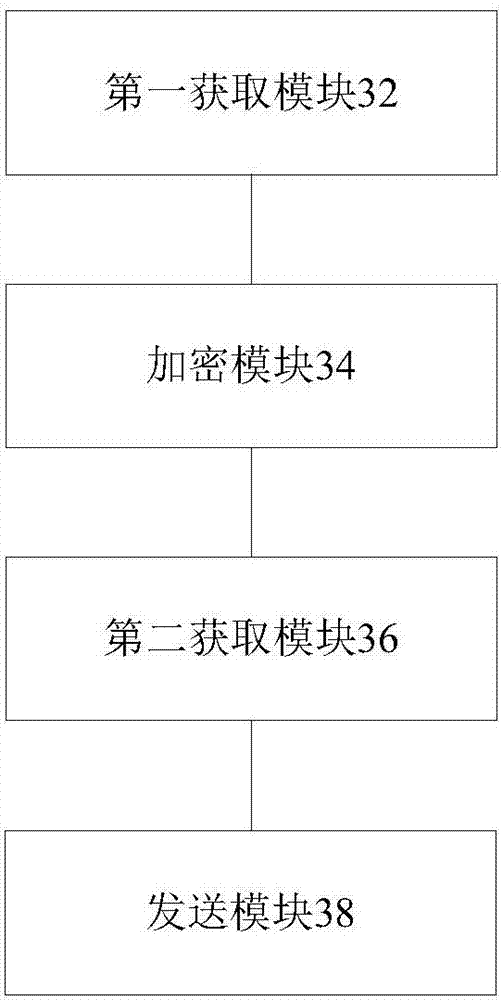
Encoding method, encoding device, decoding method and decoding device
A coding method and coding technology, applied in the field of communication, can solve the problem that coding technology cannot achieve the security of information theory meaning, and achieve the effect of safe coding and decoding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0134] Example: Rule (3,2) LDPC security code using BP decoding algorithm
[0135] First, when n=280, k=20, l=100 (the actual code word rate is 0.33 at this time), and the signal-to-noise ratio of the legal user is 14, the simulation results show that the bit error rate of the legal user is 4 ×10 -9 , which is the same as the bit error rate of legal users without feedback (the bit error rate of legal users corresponding to this codeword is also 4×10 -9 ). Figure 6 is the curve according to the preferred embodiment of the present invention Figure 1 ,Such as Figure 6 As shown, when n=280, k=20, l=100, the relationship between the ratio of the signal-to-noise ratio of the main channel and the eavesdropping channel and the bit error rate of the eavesdropper is given. From the simulation results and Figure 6 We can see that the feedback can increase the decoding error probability of an eavesdropper, thereby improving the security of the system.
[0136] Next, we reduce th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com