Optimal attack path planning method based on Q learning
An attack path, the best technology, applied in the field of information security, can solve problems such as state explosion, high algorithm overhead, and inability to quickly fit the best attack path.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] According to the above technical solutions, the present invention will be described in detail below in conjunction with the accompanying drawings and implementation examples.
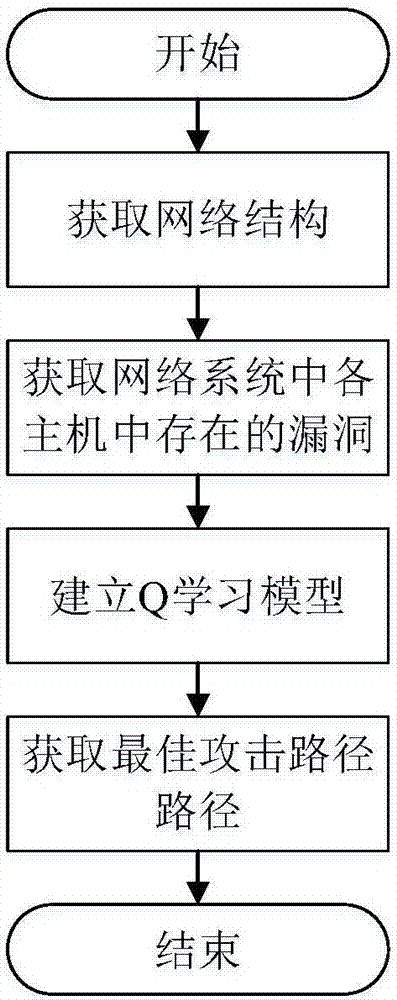
[0038] Use the Q-learning-based optimal attack path planning method proposed by the present invention to find the optimal attack path in the network system, and its operation process is as follows figure 1 As shown, the specific operation steps are as follows:
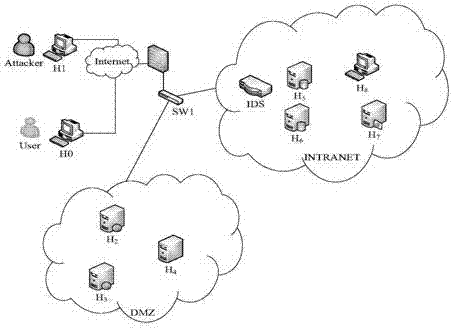
[0039] Step 1: Obtain the network structure.
[0040] Such as figure 2 As shown, the initial defense strategy is set in the network system: external network personnel can access the host H in the DMZ area 2 , H 3 and H 4 browser and DNS domain name. Host H 2 and H 3 Can access H 4 The mail service in and the H 5 and H 6 SQL service on. Host H 7 For the FTP server, except the host H 8 In addition, other hosts can only read and download public files, but cannot modify files. Host H 2 , H 3 and H 4 Access to the management ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com