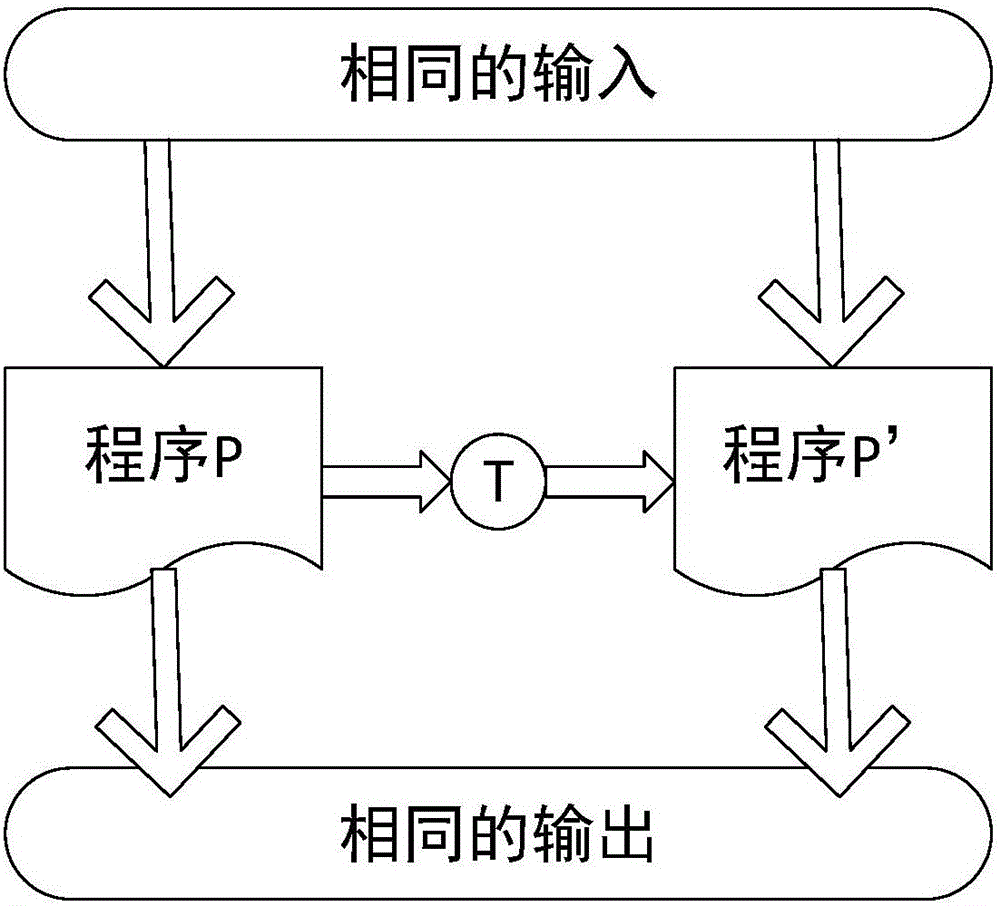
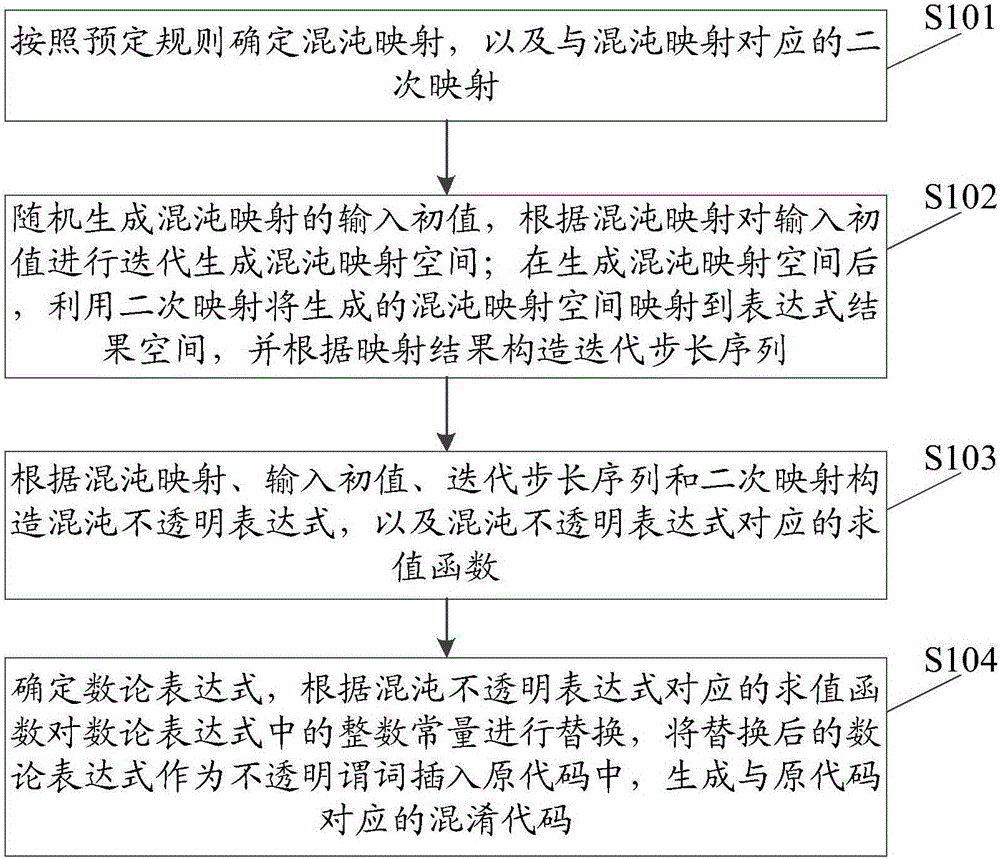
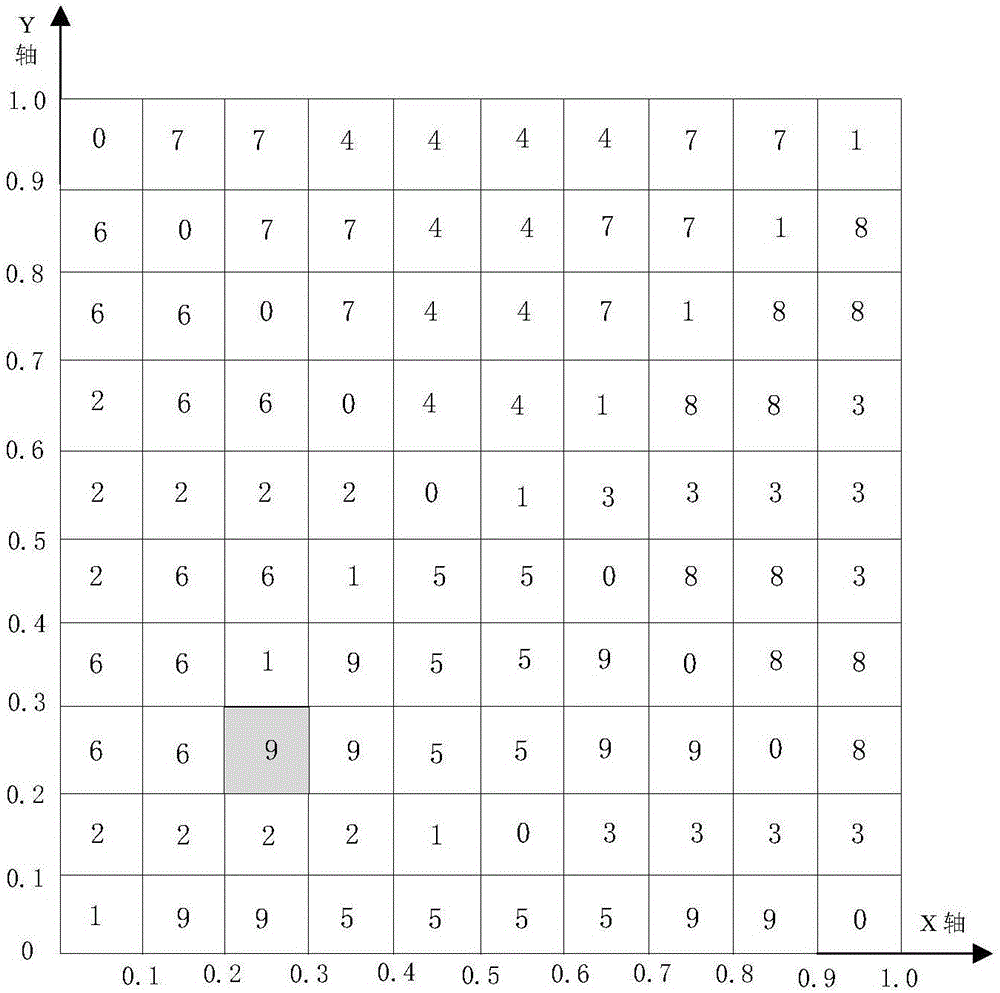
Code obfuscation method and device based on chaotic opaque predicates
A code obfuscation and transparent technology, applied in the direction of program/content distribution protection, etc., can solve the problem of low versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0083]
[0084]
[0085]Collberg et al. first proposed opaque predicates based on the difficulty of alias analysis and concurrency analysis. The two construction methods of opaque predicates increase the difficulty of deciphering opaque predicates to a certain extent. Then Arboit used the quadratic remainder theory to construct opaque predicates, and combined software digital watermarking technology to design a Java program watermarking scheme based on opaque predicates, but after analysis and evaluation verification, the cryptographic security of this scheme was not good; later Yuan Zheng proposed to use congruence equations in elementary number theory to construct opaque predicates, which are more superior in terms of security and cost than the quadratic remainder method. Anirban Majumdar et al. proposed a new method that combines the open problem of distributed global state detection with the well-known hard composition problem to make opaque predicates to solve the p...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap