Method and device for judging login abnormality of account
An abnormal login and abnormal technology, applied in the computer field, can solve problems such as poor user experience and inability to confirm users, and achieve the effect of avoiding losses and improving user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
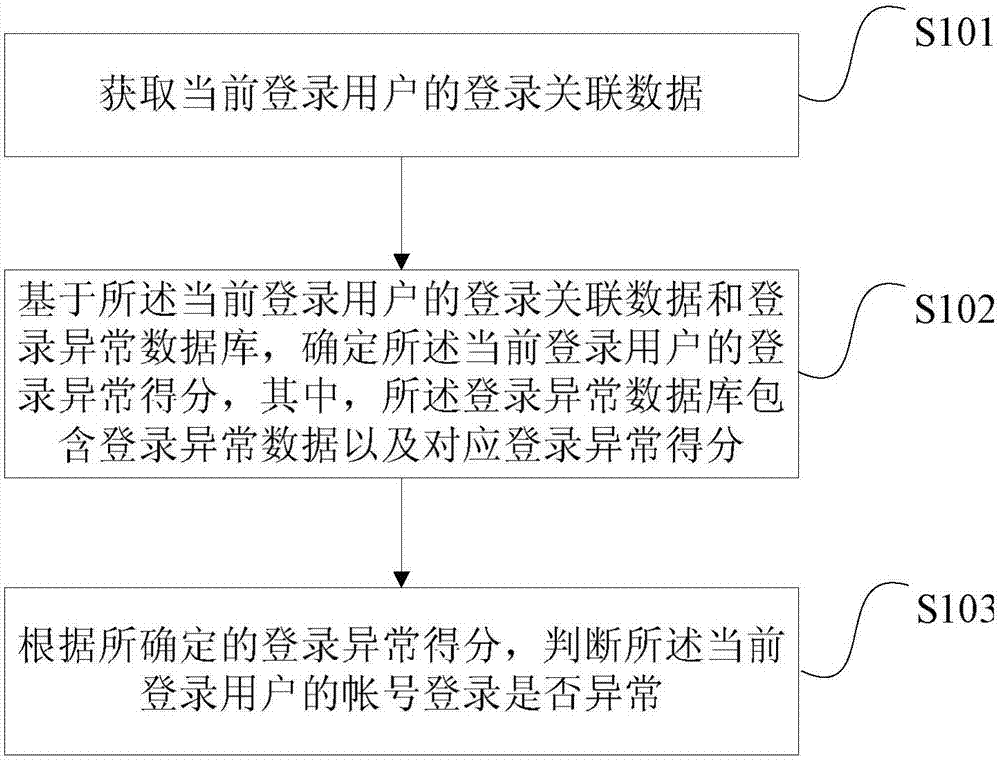
[0021] figure 1 It is a flow chart of the method for judging account abnormality provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation where the account is illegally logged in after being obtained by a phishing website. The method can be executed by the server, and specifically includes:
[0022] S101. Obtain the login association data of the currently logged-in user;
[0023] Wherein, the currently logged-in user is a user who is logging in with an account or has already logged in and is using an account. After the user logs in with the account, the obtained login-associated data of the currently logged-in user may be the login IP, login region, and login device ID at the time of current login. The login region can be automatically converted by the server from the login IP for subsequent comparison and analysis.
[0024] Here, the abnormal login device identifier may be an identification number capable of identifying a mobile term...
Embodiment 2
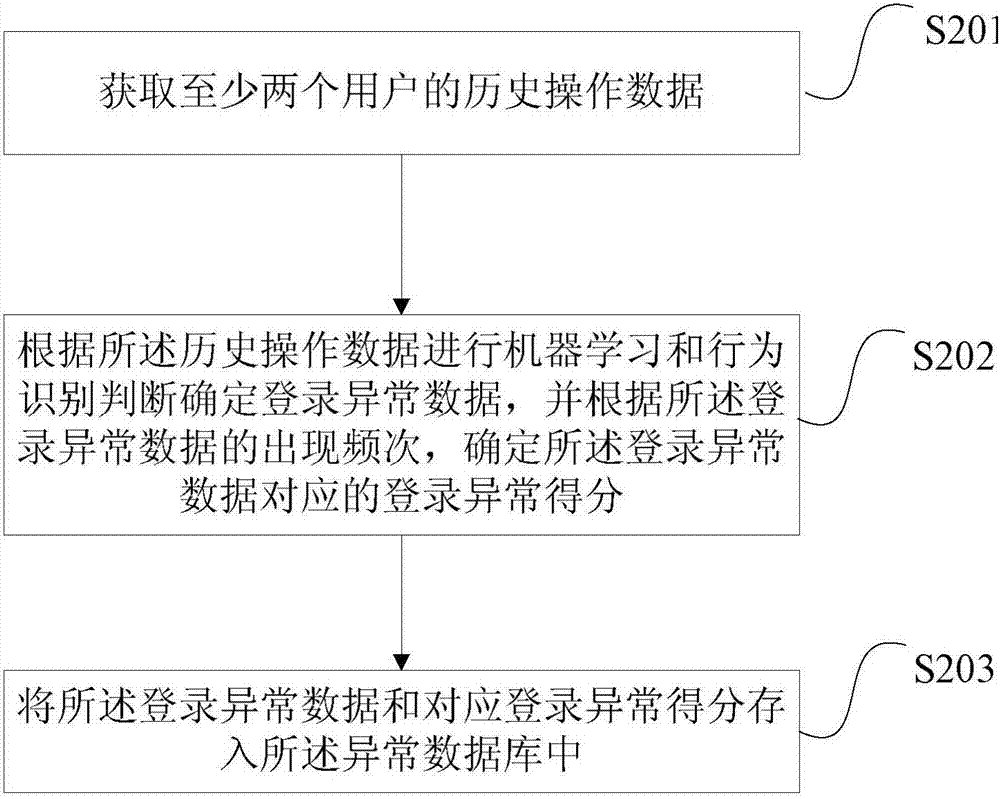
[0041] image 3 It is a flow chart of the method for judging account abnormality provided by Embodiment 2 of the present invention. This embodiment is an improved embodiment of the first embodiment. and figure 1 Compared with, in addition to adding S204 to S206 between S102 and S103, and modifying S103 to S103', the rest of the steps are the same as figure 1 same. Here, only S204 to S206 and S103' are described, and other steps are not repeated. After the abnormal login score of the currently logged-in user is determined in step S102, in S204, it is determined whether there is historical login verification information related to the user. Here, the historical login verification information may include login device identification information and login IP information. The historical login verification information may be all historical login verification information, or historical login verification information within a predetermined time period, such as historical login ver...
Embodiment 3
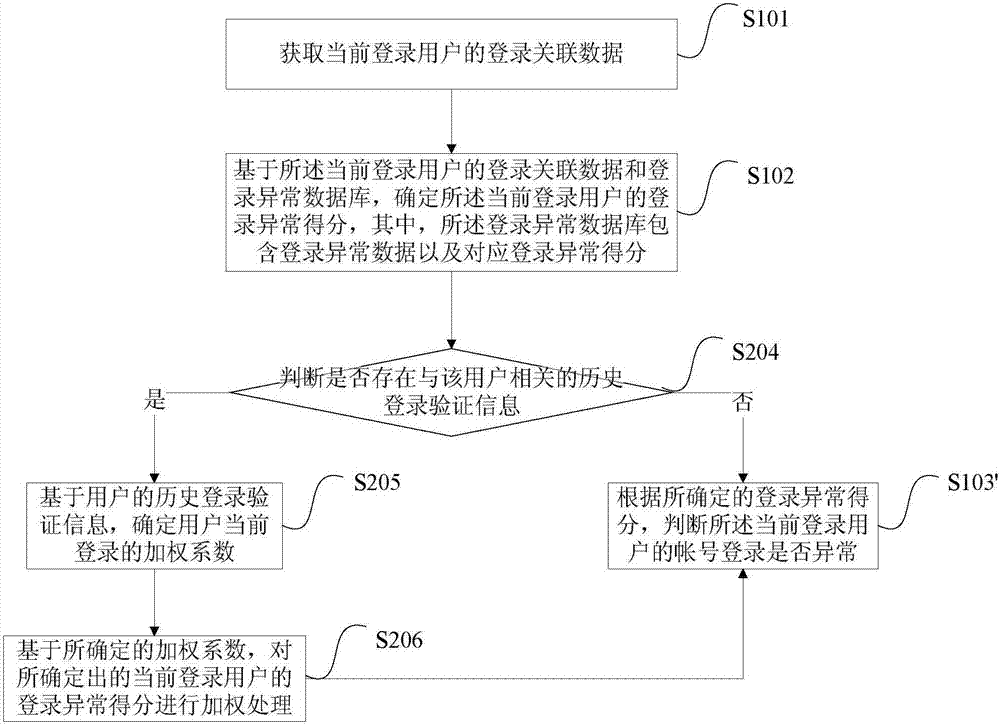
[0045] Figure 4 Shown is the flow chart of the method for judging account abnormalities provided by Embodiment 3 of the present invention. On the basis of Embodiment 1, this embodiment further adds operations to prevent repeated login processing within a certain period of time, specifically including:
[0046] S301. Obtain login association data of a currently logged-in user.
[0047] S302. Based on the login association data of the current login user and the login anomaly database, determine the login anomaly score of the current login user.
[0048] S303, based on the determined abnormal login score, determine whether the account login of the currently logged-in user is abnormal, if yes, perform S304, and if not, perform S306.
[0049] S304. When it is determined that the account login of the currently logged-in user is abnormal, determine whether corresponding processing has been performed within a predetermined time period. If no corresponding processing has been perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com