Non-artificial access log filtering method and device
A filtering method and log technology, which is applied in the field of filtering non-human access logs, can solve the problems of user behavior analysis interference and low analysis value, and achieve the effect of improving the efficiency of log mining
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
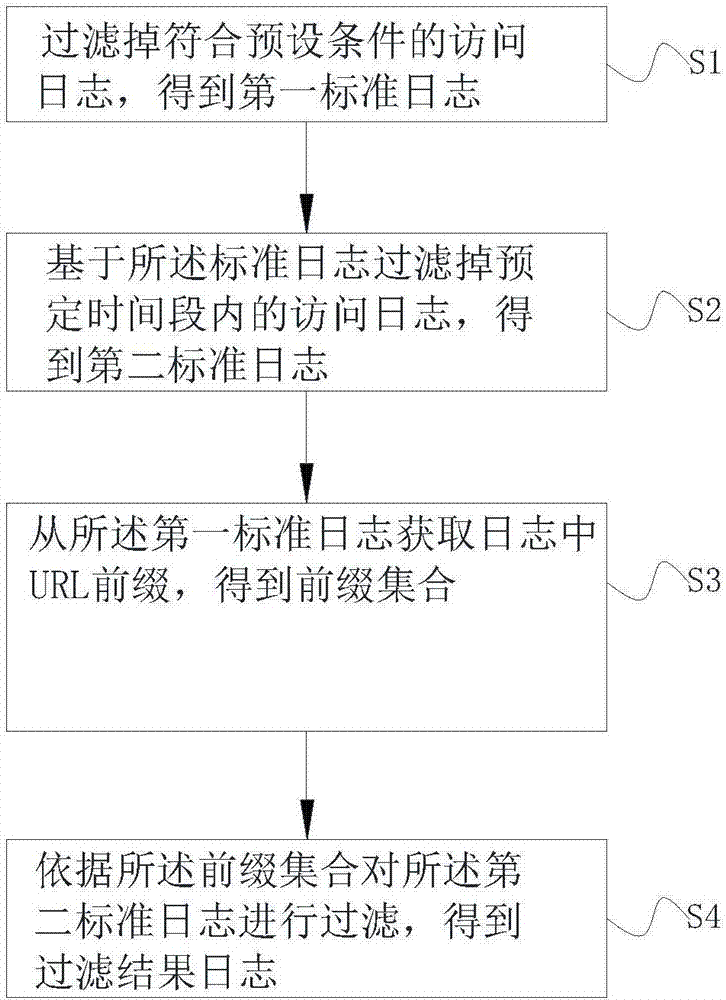
[0053] figure 1 It is a flowchart of this embodiment. according to figure 1 As shown, the first embodiment of the present invention provides a method for filtering non-human access logs, the method comprising:
[0054]S1: Filter out the access logs that meet the preset conditions to obtain the first standard log;
[0055] S2: Filter out access logs within a predetermined time period based on the first standard log to obtain a second standard log;
[0056] S3: Obtain the URL prefix in the log from the first standard log to obtain a prefix set;
[0057] S4: Filter the second standard log according to the prefix set to obtain a filter result log.
[0058] In this regard, high-frequency non-human access can be quickly and effectively filtered, which is of great significance for improving log mining efficiency, analyzing user behavior, and even detecting internal security threats.
[0059] Specifically, a method for filtering non-human access logs provided in the first embodim...
no. 2 example
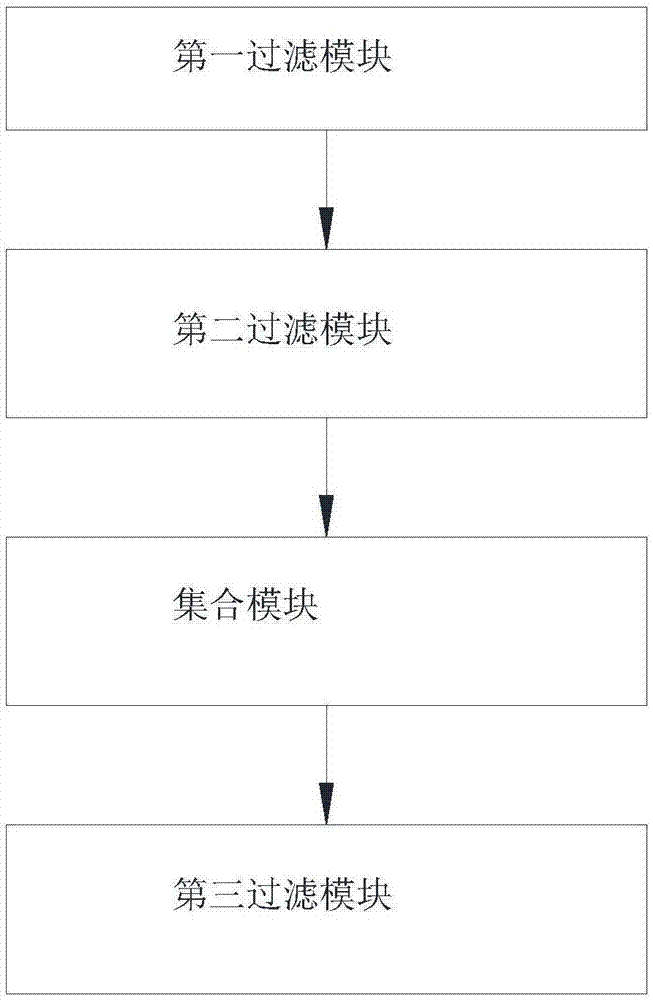
[0097] figure 2 It is a flowchart of this embodiment. according to figure 2 As shown, according to the second embodiment of the present invention, a filter device for non-human access logs is provided, the device includes:
[0098] The first filtering module is used to filter out the access logs meeting the preset conditions to obtain the first standard log;
[0099] A second filtering module, configured to filter out access logs within a predetermined period of time based on the first standard log to obtain a second standard log;
[0100] A collection module, configured to obtain URL prefixes in logs from the first standard log to obtain a prefix collection;
[0101] The third filtering module is configured to filter the second standard log according to the prefix set to obtain a filtered result log.
[0102] Optionally, the third filter module includes:
[0103] Use a hash table to traverse the URL prefix in each log of the prefix set, and use a classic linked list de...
no. 3 example
[0111] A computer device includes a processor and a memory; the memory is used to store computer instructions, and the processor is used to run the computer instructions stored in the memory to implement the above-mentioned method for filtering non-human access logs.
[0112] The methods include:
[0113] Filter out the access logs that meet the preset conditions to obtain the first standard log;
[0114] filtering out access logs within a predetermined period of time based on the first standard log to obtain a second standard log;
[0115] Obtain the URL prefix in the log from the first standard log to obtain a prefix set;
[0116] The second standard log is filtered according to the prefix set to obtain a filter result log.
[0117] Optionally, the filtering the second standard log according to the prefix set to obtain the filtered result log includes: using a hash table to traverse the URL prefix in each log of the prefix set, and using a classic linked list method Solve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com