Optical image encryption method based on row multiplexing compressed ghost imaging and XOR operation
An encryption method and optical image technology, applied in image coding, image data processing, computing and other directions, can solve the problems of limited optical device accuracy, information loss, large storage and network bandwidth, etc., to reduce key space redundancy, The effect of reducing information loss and increasing encryption capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
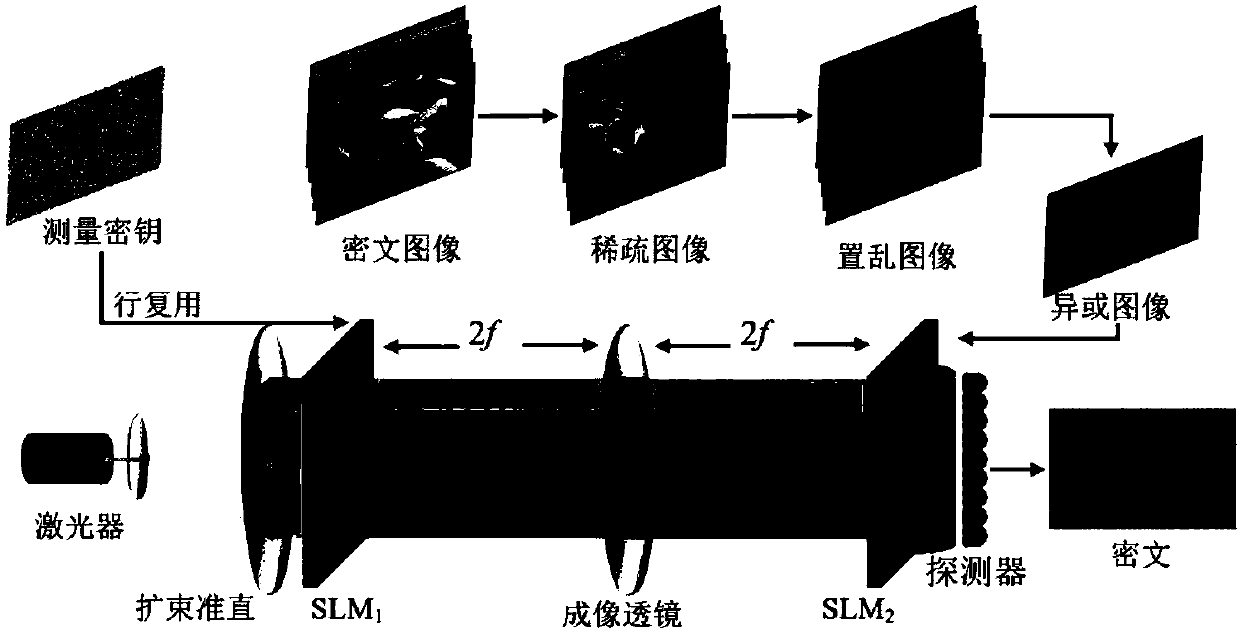
[0035] The present invention includes two processes of optical encryption and computational decryption, wherein figure 1 The principle of the optical encryption process is given, Figure 9 is a flowchart showing the calculation and decryption process.
[0036] Such as figure 1 , taking the encryption of six images as an example, the detailed process of the optical encryption process is as follows:
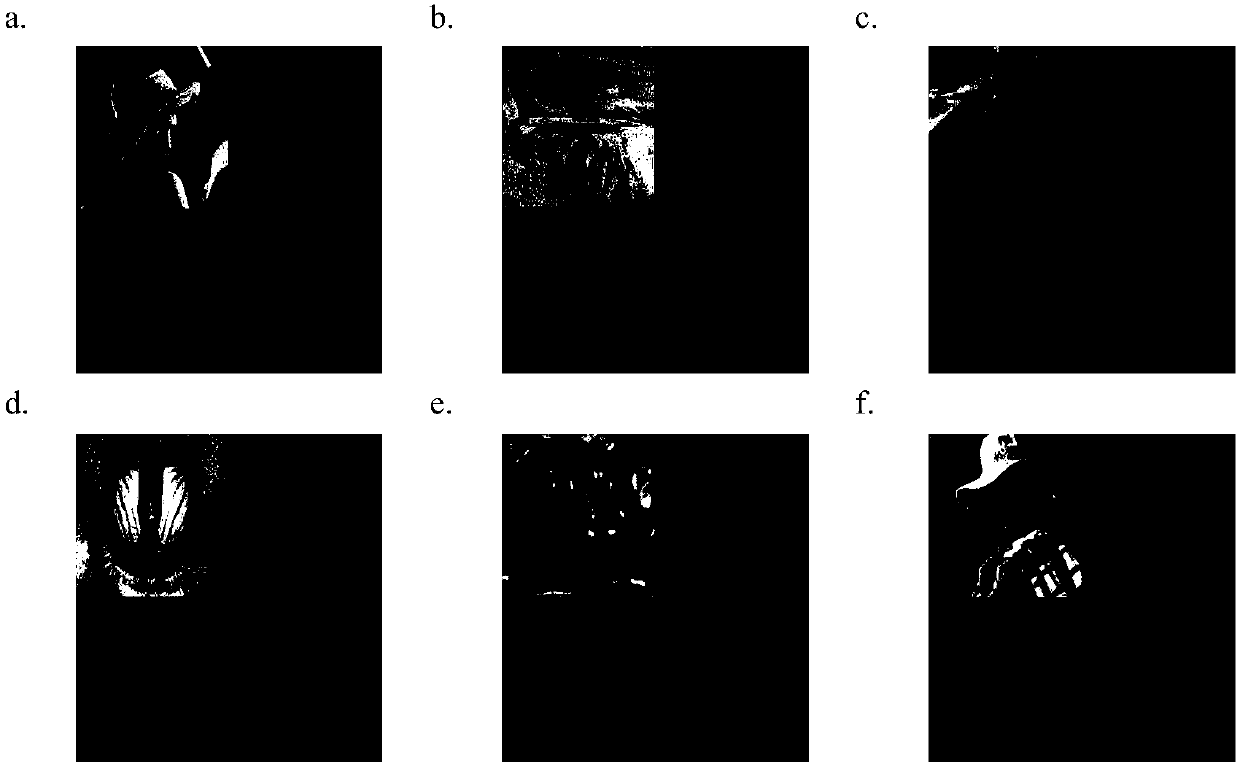
[0037] (1) figure 2 are six images to be encrypted with different information, denoted as I i (i∈[1:6]), whose size is N×N. The encryptor performs integer wavelet transformation on the six images to be encrypted in turn, transforms the image into the wavelet domain, selects an appropriate threshold, and sets all the coefficients in the image in the wavelet domain that are smaller than the threshold to 0, and then all remaining The number of coefficients that are 0 is the sparsity of the image, denoted as K, and different wavelet coefficients are selected for each image, so th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com