Multilevel security access control model based on information flow
A security access control and security access technology, which is applied in the field of multi-level security access control model based on information flow, can solve the problems of strict restrictions on actual information flow transmission of the model, inability to apply information flow transmission, and small application scope, and achieve good accessibility. Reliability measurement effect, overcoming monotonicity defect, extending the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
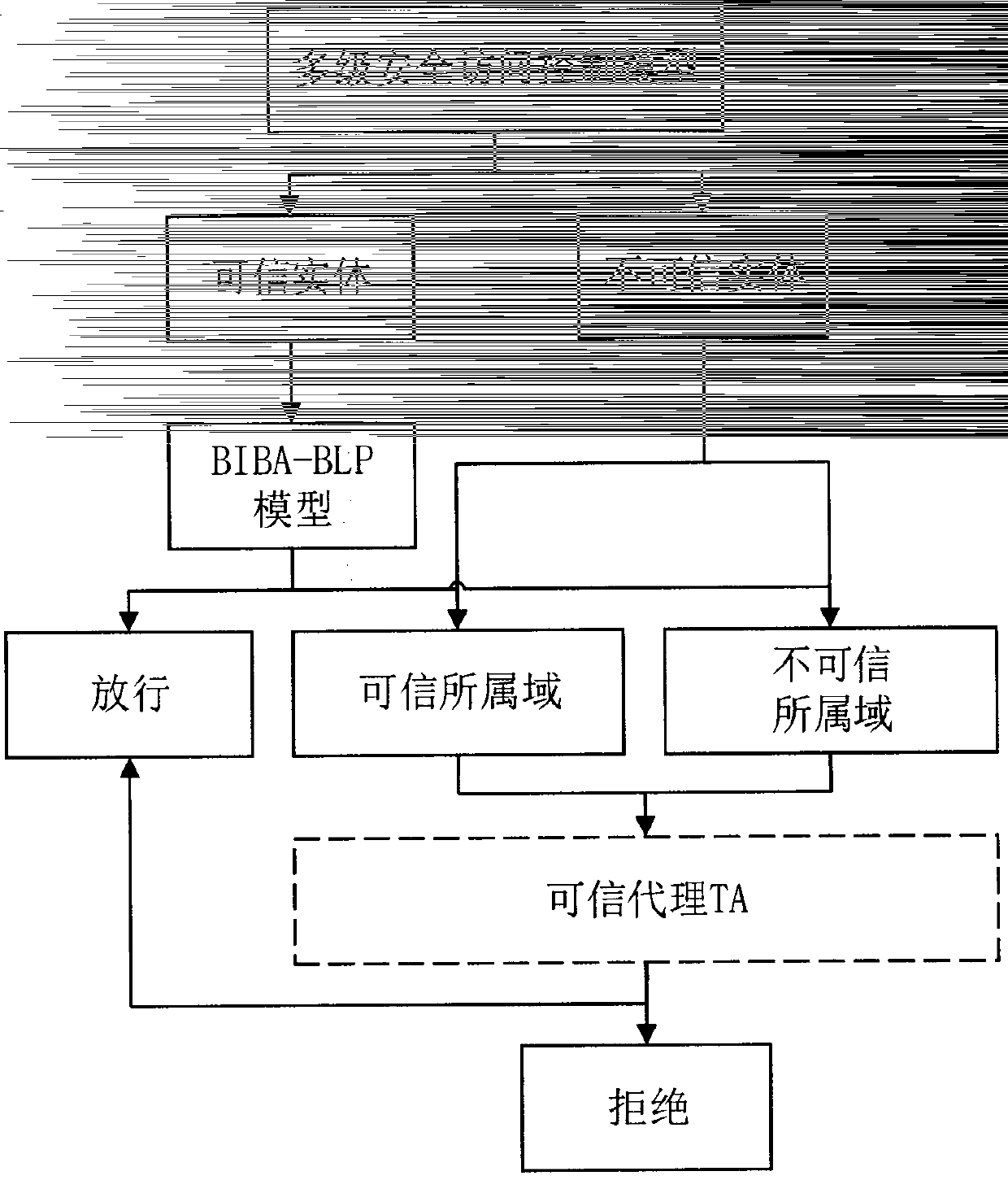
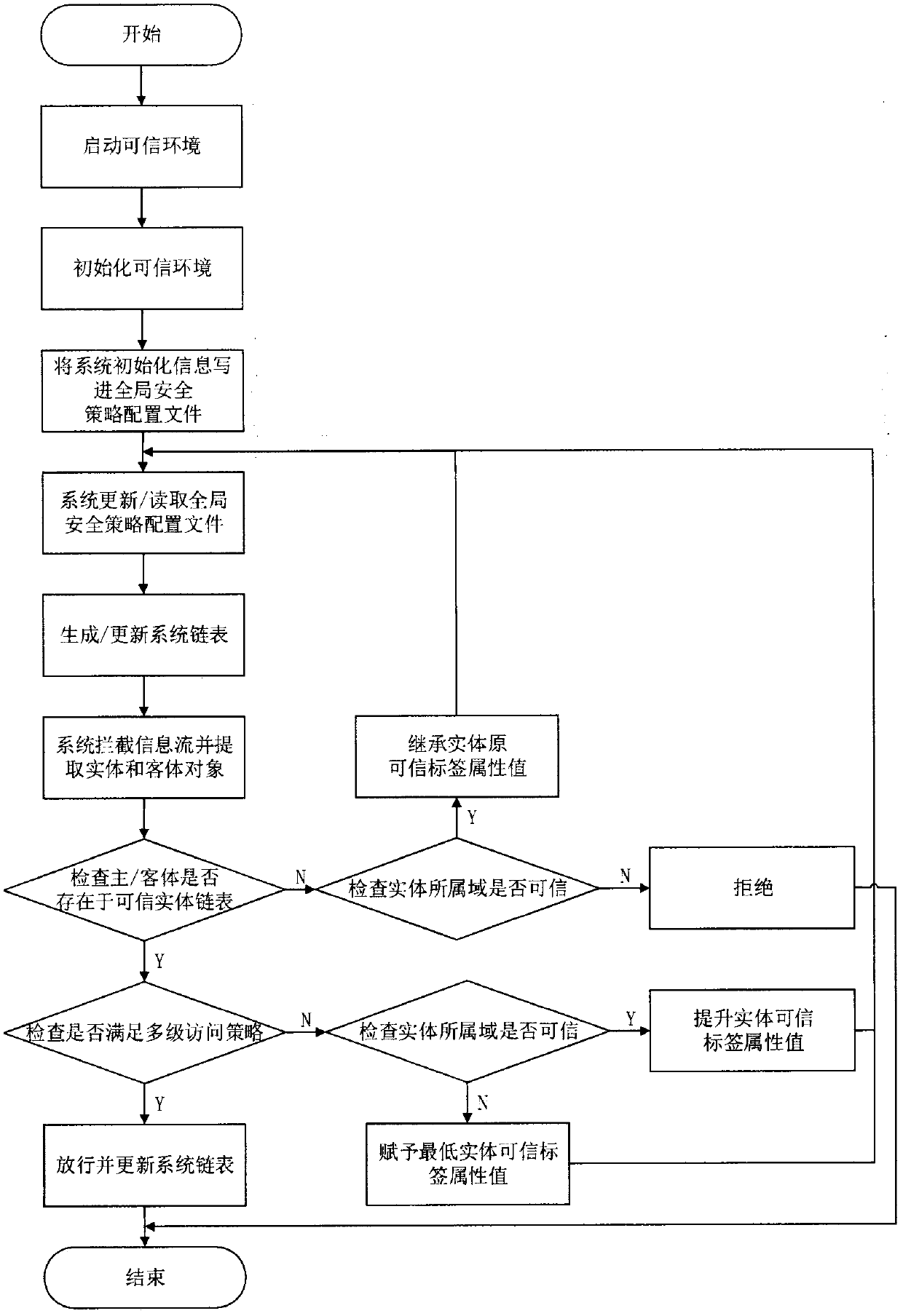
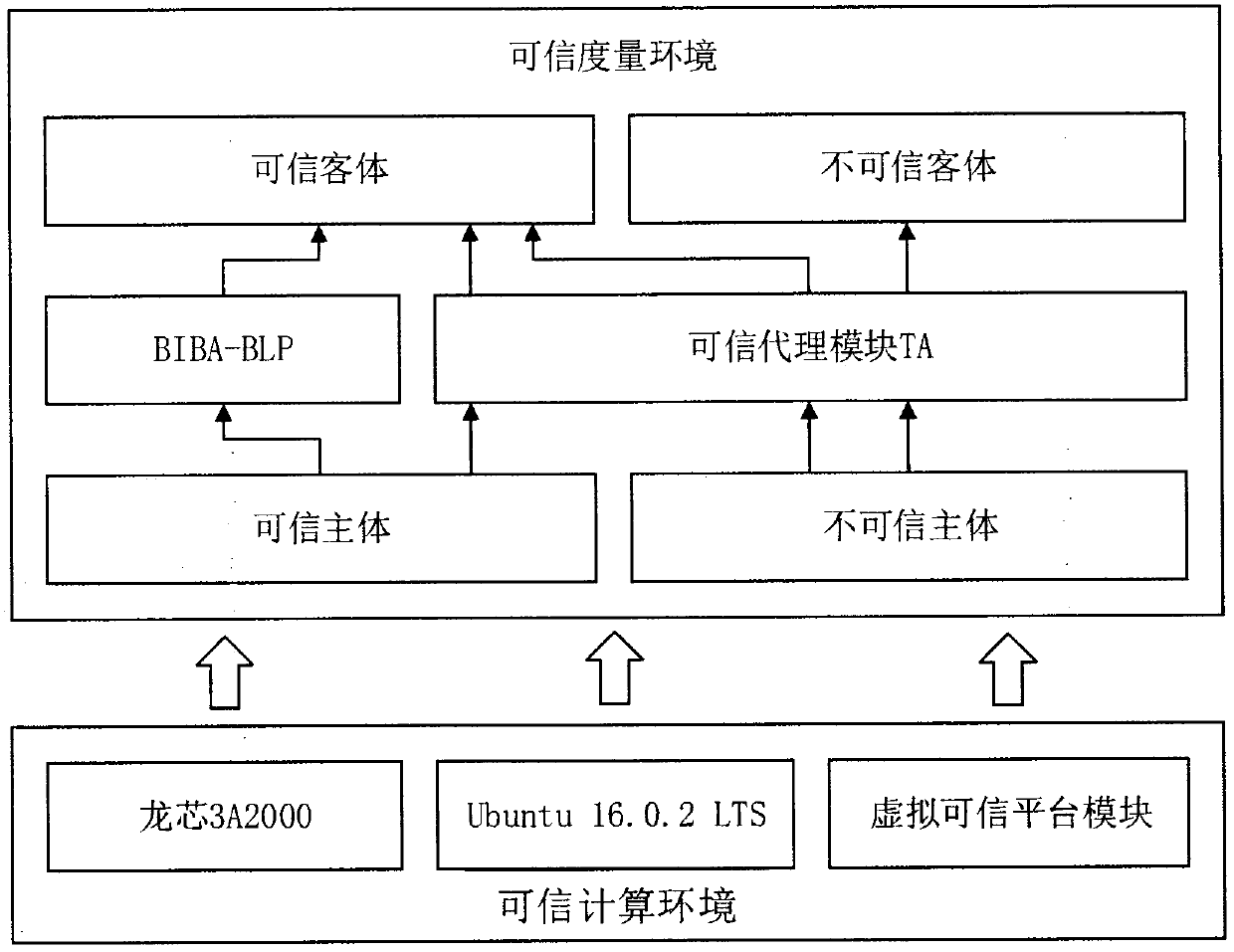
[0057] The embodiment of the present invention introduces the specific realization of the multi-level security access control model based on information flow, and its realization architecture is as follows image 3 shown, including:
[0058] This embodiment is carried out on the hardware trusted platform based on the Godson 3A2000 processor, the software environment is the Ubuntu Core 16.0.2 LTS streamlined operating system integrated with the virtual trusted platform module, and the trusted computing environment before the system starts is constructed, and the After startup, static trustworthiness measurement is performed for the first time to ensure the trustworthiness of the environment before the system runs. An embodiment selects a trusted entity A in the initial trusted environment, trusted entities B and C from the same trusted domain of the trusted entity A, and an untrusted entity D from the trusted domain. Among them, the mandatory security access control rules are ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com