Face identification method and system, terminal and server
A face recognition and server technology, applied in the field of identity authentication, can solve the problem of low security of face recognition and achieve the effect of improving security and practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
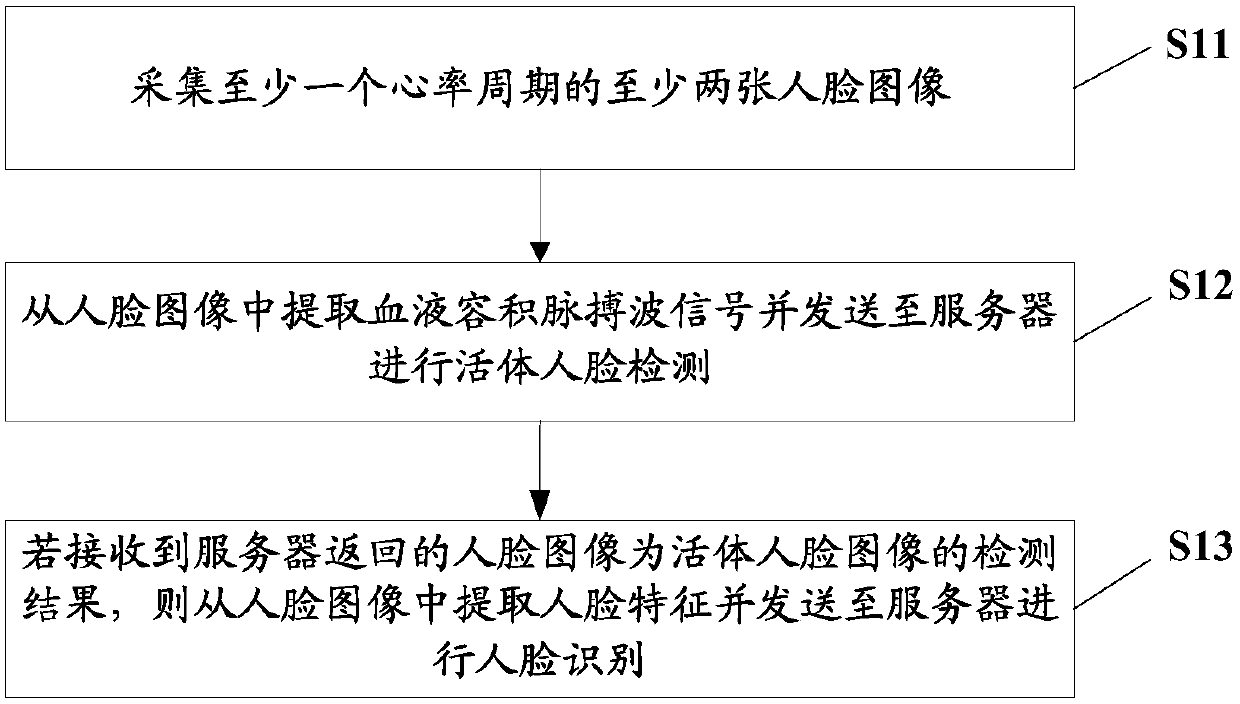
[0058] In order to solve the technical problem that the existing face recognition technology cannot effectively avoid the low security of face recognition caused by inanimate prosthesis deception, the embodiment of the present invention provides a face recognition method, which combines the face recognition process with the living body detection The process is combined, and the face recognition process is completed when the living body detection is passed, so as to effectively identify the current counterfeiting and deception methods and ensure the security and practicability of face recognition authentication.
[0059] In this embodiment, the embodiment of the present invention is described by taking the identification process performed on the terminal side as an example, where the terminals include mobile terminals such as mobile phones and tablet computers, and fixed terminals such as desktop computers. For details, please refer to figure 1 , figure 1 The flow chart of the...
Embodiment 2
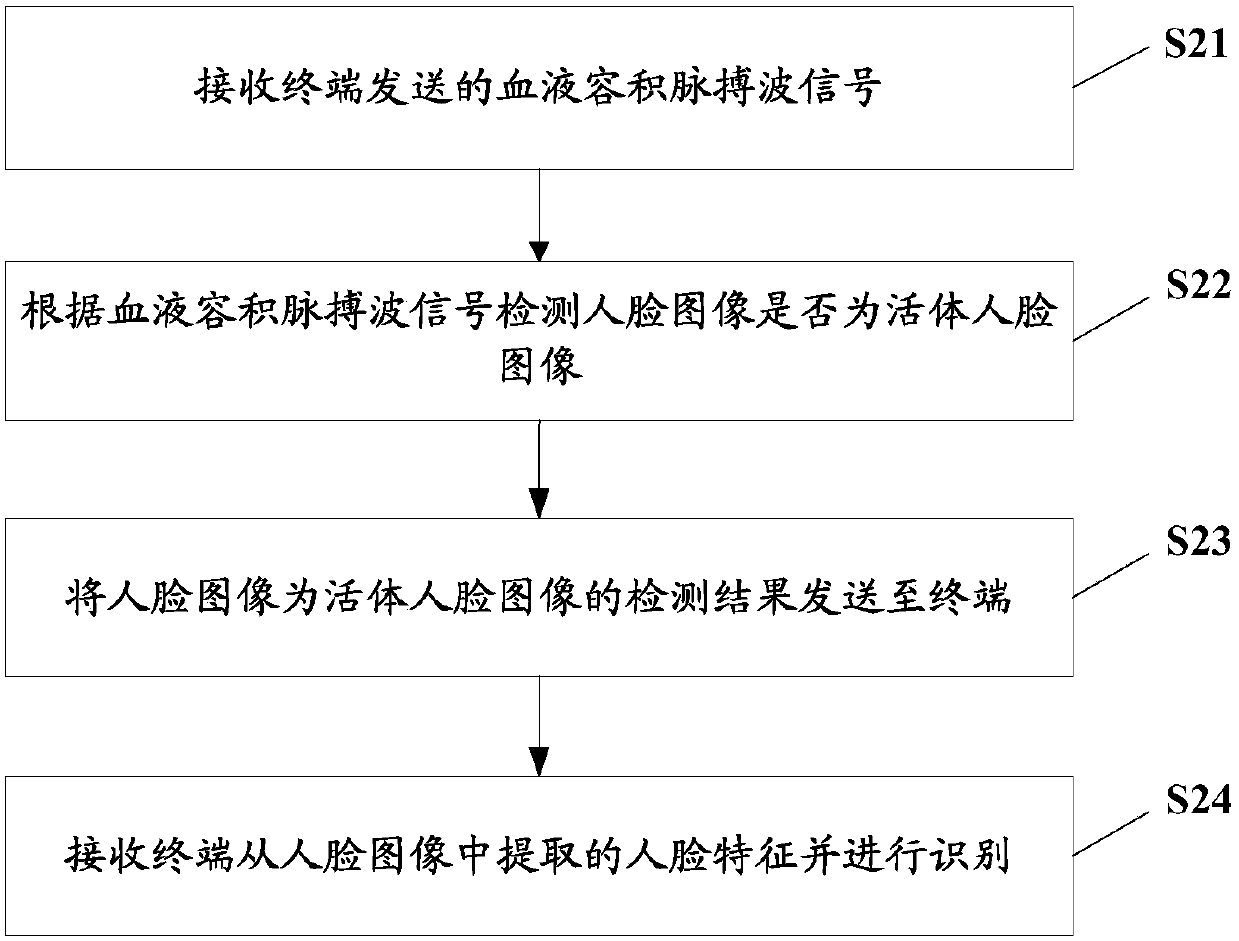
[0083] In this embodiment, the embodiment of the present invention is described by taking the recognition process executed on the server side as an example. See figure 2 , figure 2 Another face recognition method flow chart provided in this embodiment, the specific recognition steps are as follows:
[0084] S21. Receive the blood volume pulse wave signal sent by the terminal.
[0085] Specifically, for the concept related to the blood volume pulse wave signal, please refer to the relevant part in the first embodiment, and details will not be repeated here. When the terminal sends the blood volume pulse wave signal to the server, the signal data can be compressed, and then decompressed by the server to obtain the blood volume pulse wave signal, and the server filters the blood volume pulse wave signal to filter out the baseline drift in the signal and high frequency noise.
[0086] S22. Detect whether the face image is a live face image according to the blood volume pulse...
Embodiment 3
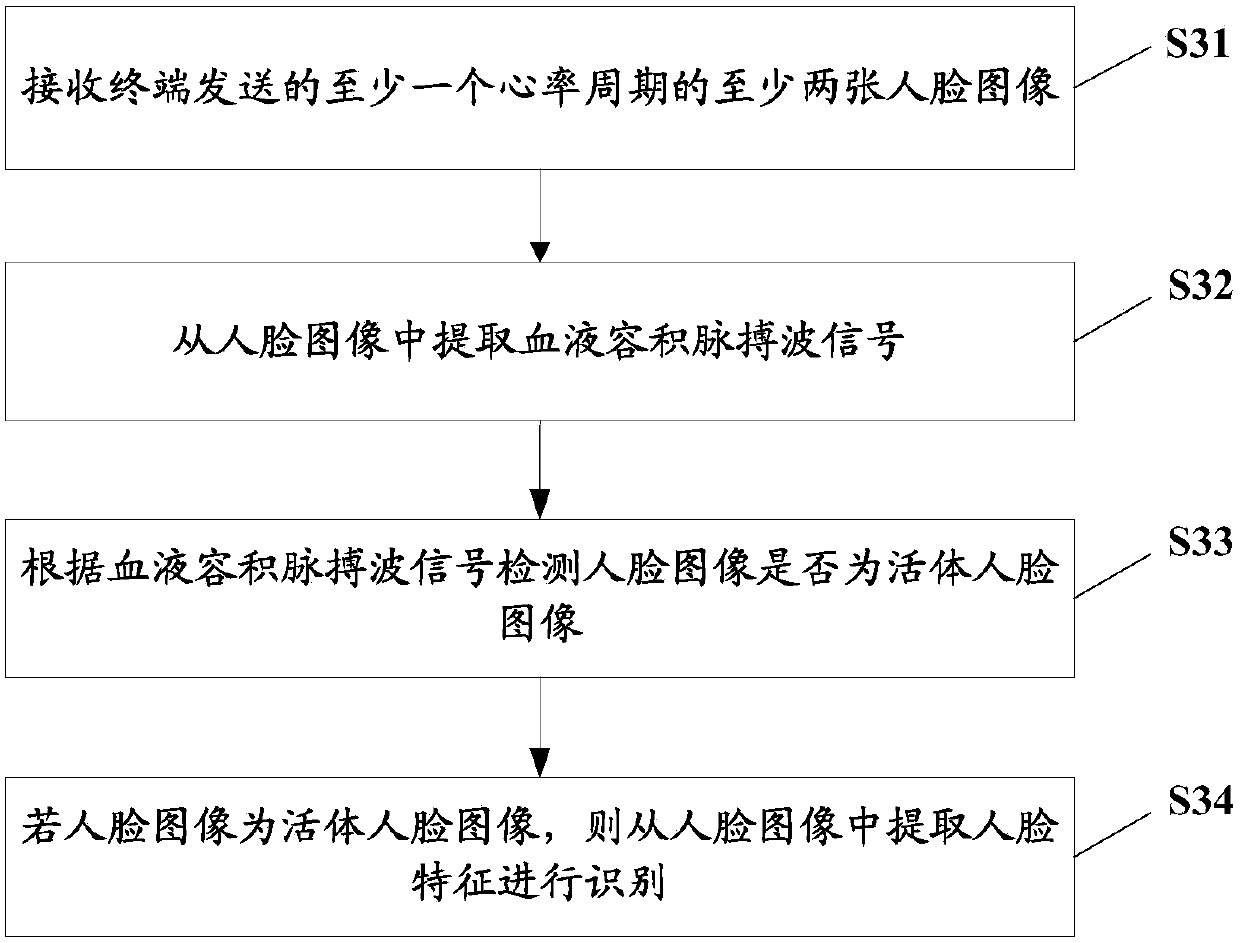
[0095] In this embodiment, the embodiment of the present invention is described by taking the recognition process executed on the server side as an example. Compared with the recognition process performed on the server side in Embodiment 2, the face recognition method proposed in this embodiment is mainly aimed at the situation that the terminal image processing capability is limited. Please refer to image 3 , image 3 Another face recognition method flow chart provided in this embodiment, the specific recognition process is as follows:
[0096] S31, receiving at least two face images of at least one heart rate cycle sent by the terminal;
[0097] S32, extracting a blood volume pulse wave signal from the face image;
[0098] S33, detecting whether the face image is a live face image according to the blood volume pulse wave signal;
[0099] S34. If the face image is a live face image, extracting face features from the face image for recognition.
[0100] Compared with the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com