Communication hub and method for verifying message among applications thereof
An application program and information verification technology, applied in the direction of inter-program communication, multi-program device, program control design, etc., to achieve the effect of preventing illegal access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
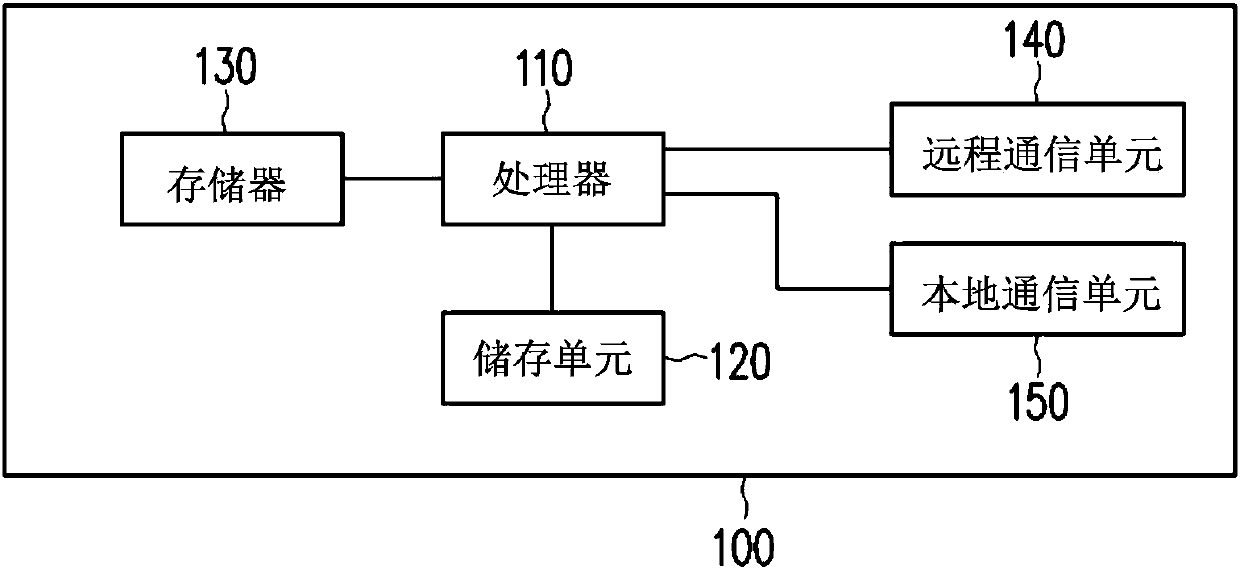
[0029] figure 1 is a block diagram of a communication hub according to an embodiment of the present invention. Please refer to figure 1 , the communication hub 100 includes a processor 110 , a storage unit 120 , a memory 130 , a remote communication unit 140 and a local communication unit 150 . The processor 110 is coupled to the storage unit 120 , the memory 130 , the remote communication unit 140 and the local communication unit 150 .
[0030] The processor 110 is, for example, a central processing unit (Central Processing Unit, CPU), an image processing unit (Graphic Processing Unit, GPU), a physical processing unit (Physics Processing Unit, PPU), a programmable microprocessor (Microprocessor), an embedded Control chip, digital signal processor (Digital Signal Processor, DSP), application specific integrated circuit (Application Specific Integrated Circuits, ASIC) or other similar devices. The processor 110 is used to execute hardware, firmware and process data in the co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com