Two-Dimensional Code Authentication System Based on Quantum Communication Network
A quantum communication and authentication system technology, applied in the field of two-dimensional code authentication system, can solve problems such as insufficient security, inconvenient management, and potential safety hazards, and achieve the effect of convenient and fast verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
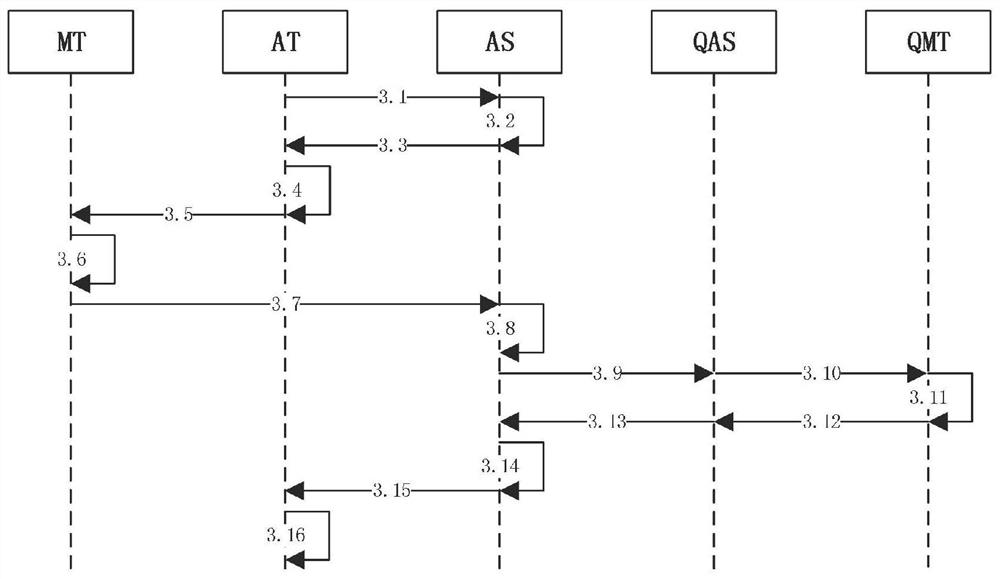
[0062] QR code authentication process QRA_FLOW
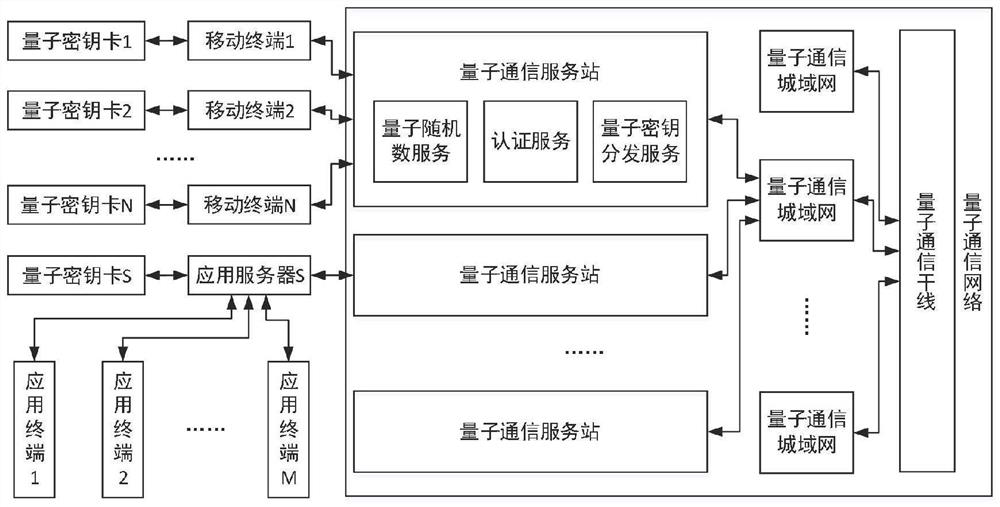
[0063] The parties directly involved in QRA_FLOW include the mobile terminal MT (the current quantum key card is MTK, and its identification number is MTKID), the application terminal AT, and the application server AS (the current quantum key card is ASK, and its identification number is ASKID), The authentication service module QMT of the quantum communication service station corresponding to the current key of MTK (its identification number is QMTID), and the authentication service module QAS of the quantum communication service station corresponding to the current key of ASK (its identification number is QASID). AT users hold MT, and MT is currently paired with MTK, so AT users hold MTK.
[0064] AT users hold MTK to register with AS. The identification number assigned by AS to AT users is UID; the identification number of the bound quantum key card is MTKID. The AS stores the UID and its corresponding MTKID to the account ...
Embodiment 2
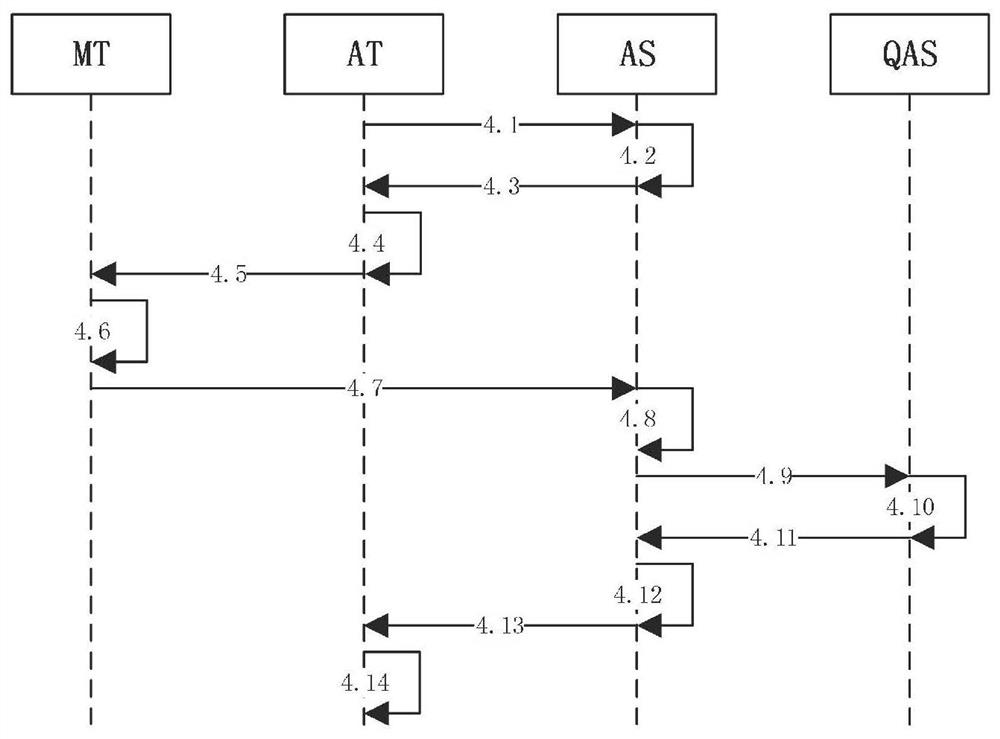
[0122] QR code authentication simplified process QRA_SFLOW
[0123] The special case of QRA_FLOW is that when the quantum communication service station corresponding to the quantum key card used by the application server and the mobile terminal is the same, that is, when there is only QAS and no QMT, the process is appropriately simplified. Its specific process is similar to the QRA_FLOW of Embodiment 1, only a few steps of communication between QAS and QMT are omitted.
[0124] See image 3 , QRA_SFLOW is as follows:
[0125] 4.1 AT sends user access request to AS;
[0126] 4.2 AS processes user access requests;
[0127] 4.3 AS sends the QR code picture to AT;
[0128] 4.4 AT displays the QR code picture;
[0129] 4.5 MT collects QR code pictures and obtains relevant information;
[0130] 4.6 MT generates a QR code response value;
[0131] 4.7 MT sends a response to AS, including QR code ID, MTKID, and QR code response value;
[0132] 4.8 AS judges the legality of the...
Embodiment 3
[0146] Simplified operation of QR code authentication process SQRA_FLOW
[0147] For the aforementioned QRA_FLOW and QRA_SFLOW, the first step needs to input the UID to the AT. If the input of the UID is complicated, the operation will be inconvenient. To further facilitate user operation, the following flow SQRA_FLOW that does not require AT users to input UID can be used.
[0148] The parties directly involved in SQRA_FLOW are the same as QRA_FLOW.
[0149] The AT user holds MTK to register with the AS, and the AS records the MTKID in the account database of the AS, which is recorded as SQRA_FLOW_REG; or not registered, which is recorded as SQRA_FLOW_UNREG. In the case of SQRA_FLOW_REG, AS can also store the user's biological characteristics corresponding to MTKID to the account database, such as fingerprint characteristics, iris characteristics, face characteristics, vein characteristics, palmprint characteristics, etc.
[0150] See Figure 4 , SQRA_FLOW is as follows: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com