Method and device for strategy self-learning and optimization based on random forest
A random forest algorithm and random forest technology are applied in the field of strategy self-learning and optimization methods and devices based on random forest, which can solve problems such as poor accuracy of security inspection results, so as to alleviate poor accuracy and reduce false negatives and false positives. The effect of reporting probabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
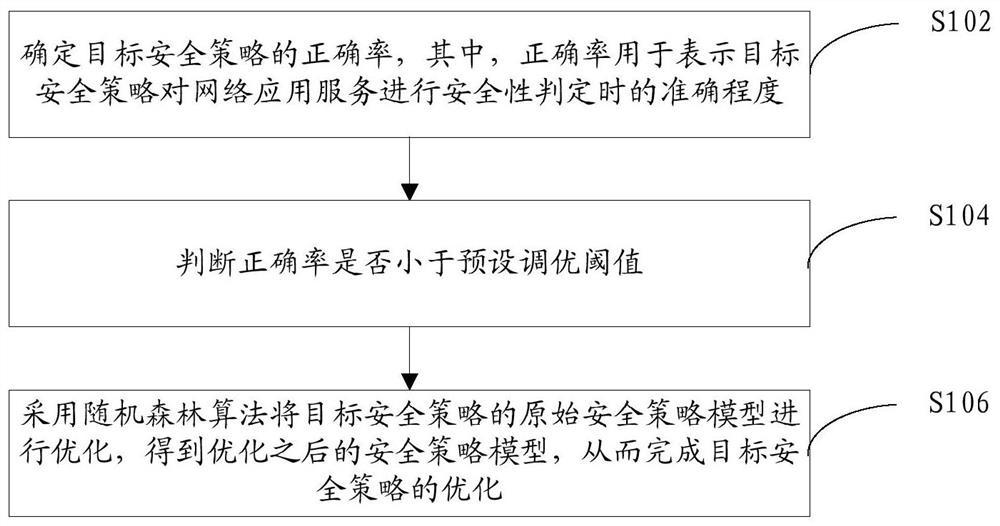
[0047] A random forest-based strategy self-learning and optimization method provided by the embodiment of the present invention, such as figure 1 shown, including:
[0048] Step S102, determining the correct rate of the target security policy, wherein the correct rate is used to indicate the accuracy of the target security policy when making a security judgment on the network application service;
[0049] Step S104, judging whether the accuracy rate is less than a preset tuning threshold;
[0050] In step S106, when the correct rate is less than the preset tuning threshold, the random forest algorithm is used to optimize the original security policy model of the target security policy to obtain the optimized security policy model, thereby completing the optimization of the target security policy.
[0051] Specifically, the target security policy has an original security policy model to determine the correct rate of the target security policy, that is, to determine the correct...
Embodiment 2
[0094] A random forest-based policy self-learning and optimization device provided by an embodiment of the present invention, such as Figure 4 shown, including:
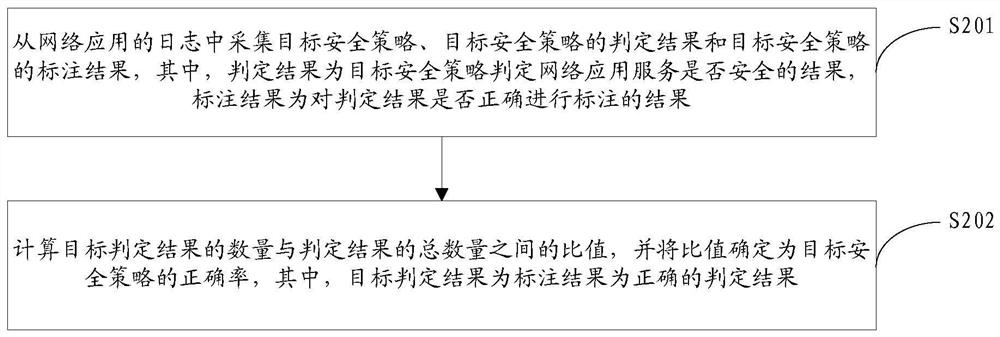
[0095] The first determination module 100 is configured to determine the correct rate of the target security policy, wherein the correct rate is used to indicate the accuracy of the target security policy when making a security judgment on the network application service;
[0096] A judging module 200, configured to judge whether the accuracy rate is less than a preset tuning threshold;
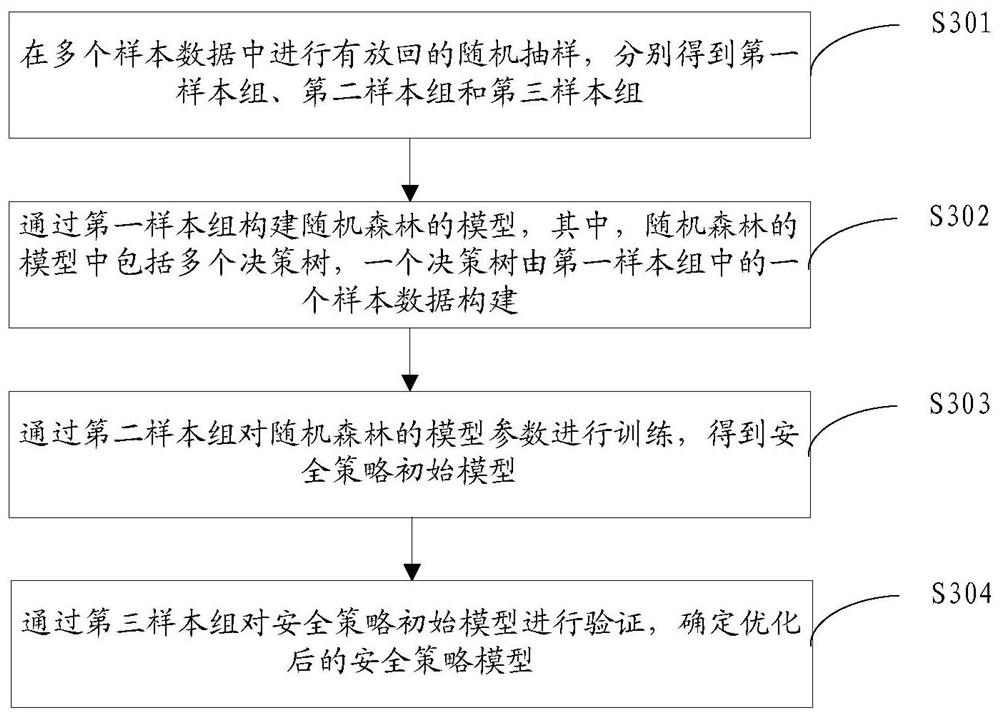
[0097] The second determination module 300 is configured to use the random forest algorithm to optimize the original security policy model of the target security policy when the accuracy rate is less than the preset tuning threshold, to obtain the optimized security policy model, thereby completing the target security policy Optimization.
[0098] In the embodiment of the present invention, the first determination module 100 dete...
Embodiment 3
[0117] An embodiment of the present invention provides a computer-readable medium having a non-volatile program code executable by a processor, and the program code causes the processor to execute the method of Embodiment 1.
[0118] Specifically, the storage medium includes: a USB flash drive, a mobile hard disk, a read-only memory (ROM, Read-Only Memory), a random access memory (RAM, Random Access Memory), a magnetic disk or an optical disk, and other media that can store program codes. .
[0119] In this embodiment of the present invention, the program code causes the processor to execute the method of Embodiment 1, that is, firstly determine the accuracy rate of the target security policy, where the accuracy rate is used to indicate the security rate of the target security policy when making a security judgment on the network application service. degree of accuracy; then, it is judged whether the correct rate is less than the preset tuning threshold; finally, when the corr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com