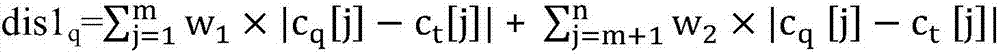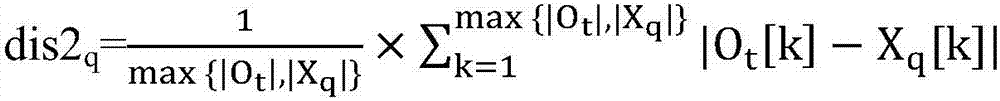Differential privacy protecting method of datastream key mode mining
A differential privacy and pattern mining technology, applied in the field of privacy protection, can solve problems such as privacy leakage, achieve the effect of improving utility and reducing computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in combination with specific examples and with reference to the accompanying drawings.
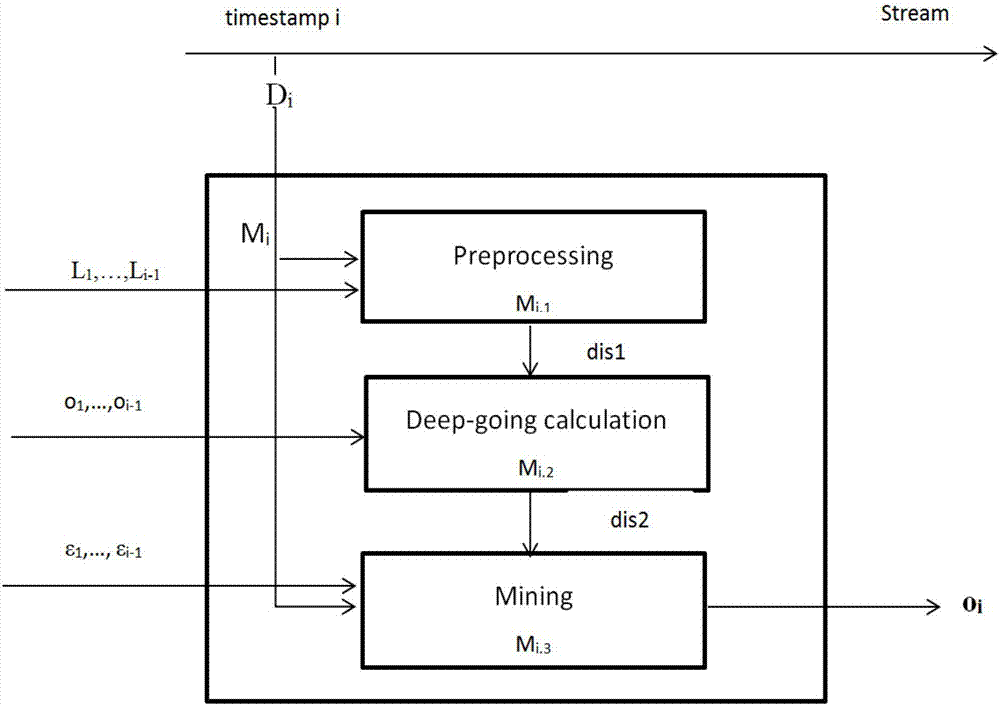
[0048] There is a problem in using the method that satisfies differential privacy in frequent patterns on key patterns: the branch number condition is not considered, and the mined key patterns do not satisfy differential privacy. The present invention proposes a differential privacy protection method for data stream key pattern mining, such as figure 1 As shown, at each timestamp we design a 3-stage mechanism to return the key patterns mined at the current timestamp (i) as either a low-noise result set (ii) or an accurate approximate result set. This mechanism includes a preprocessing stage, a deep calculation stage and a mining stage. For window sliding, in order to increase the mining time and allocate the privacy budget...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com