Patents
Literature
63 results about "Web usage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
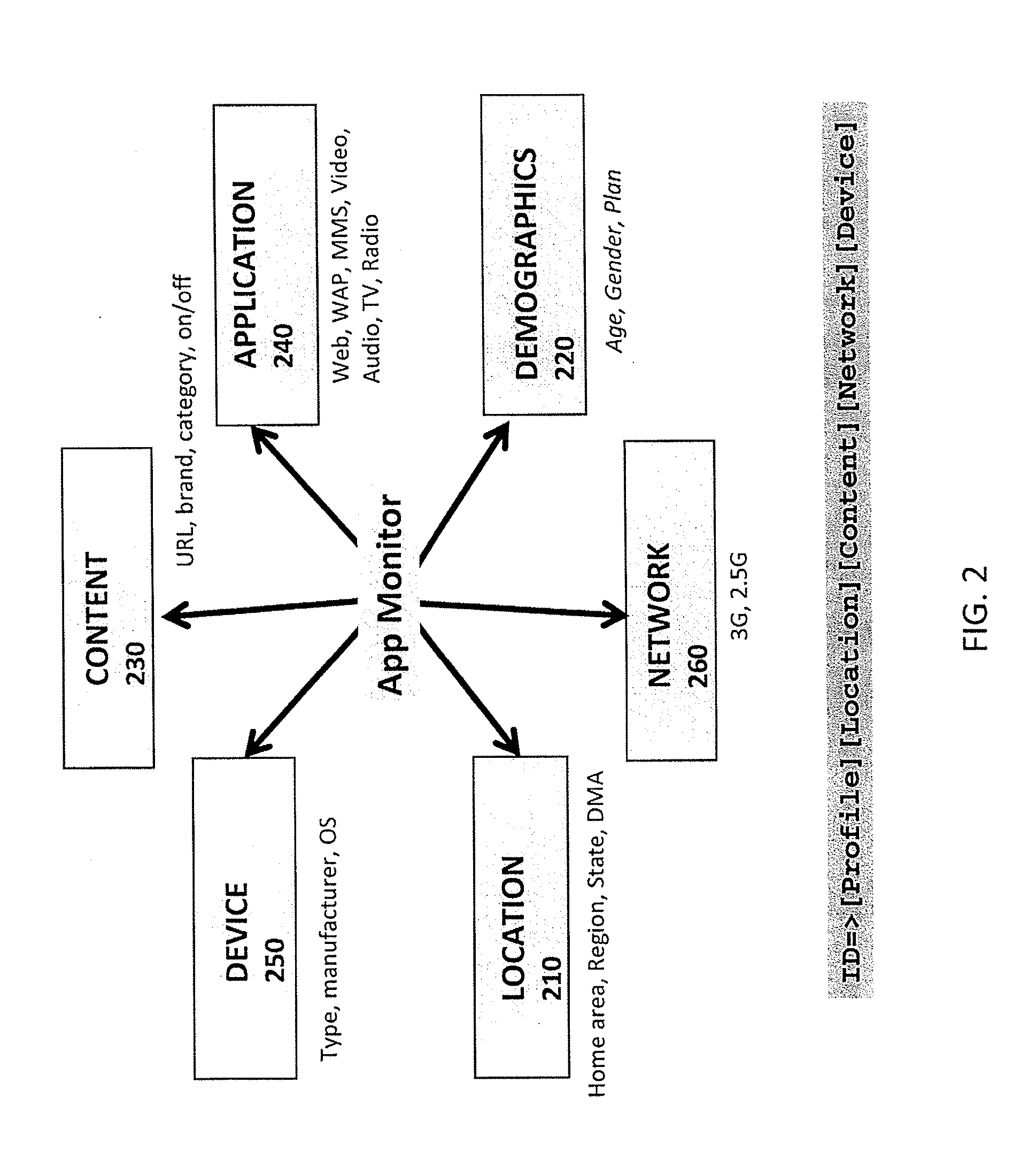
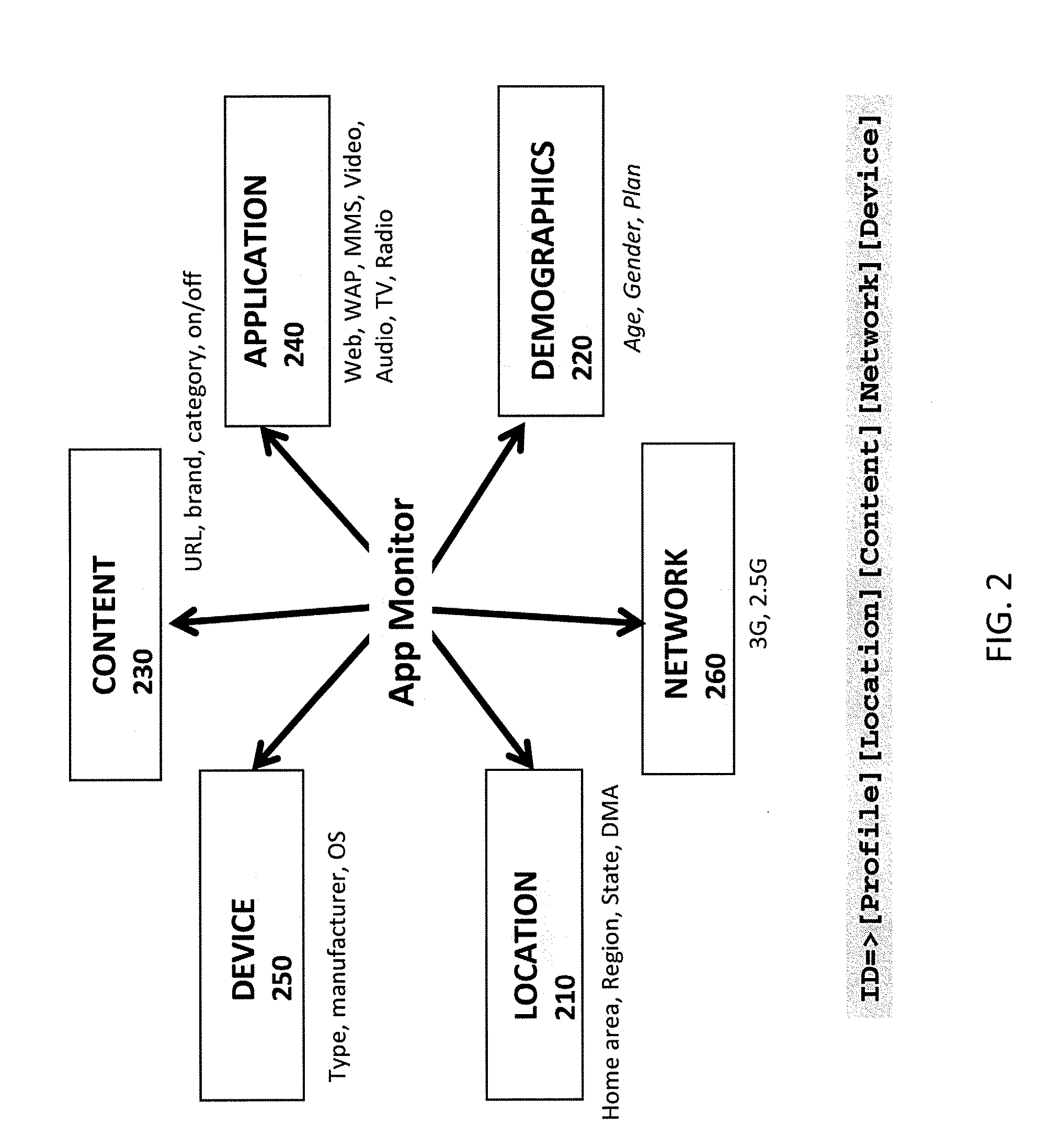
Web usage mining is the application of data mining techniques to discover usage patterns from Web data, in order to understand and better serve the needs of Web-based applications. Web usage mining consists of three phases, namely preprocessing, pattern discovery, and pattern analysis.
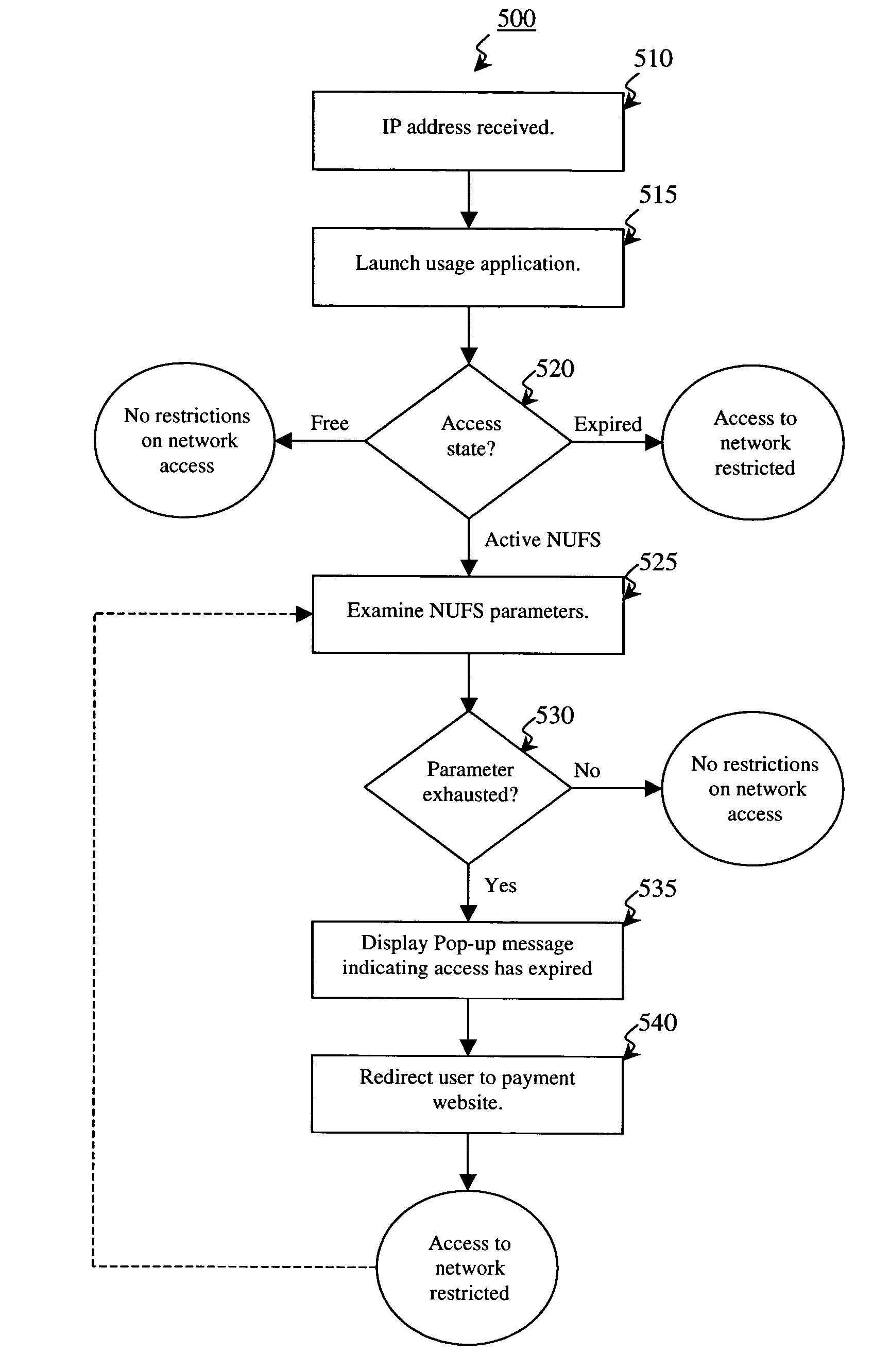
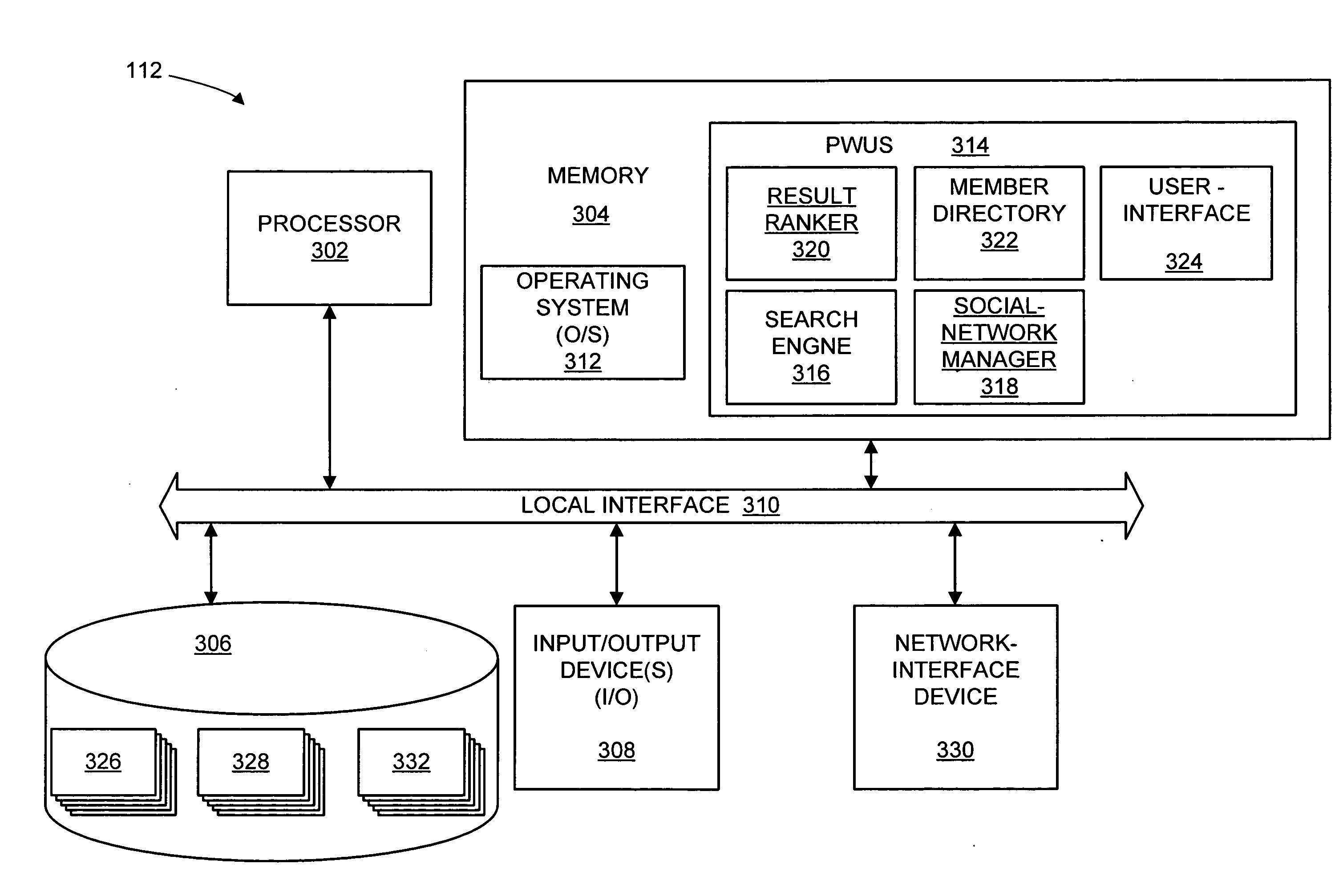
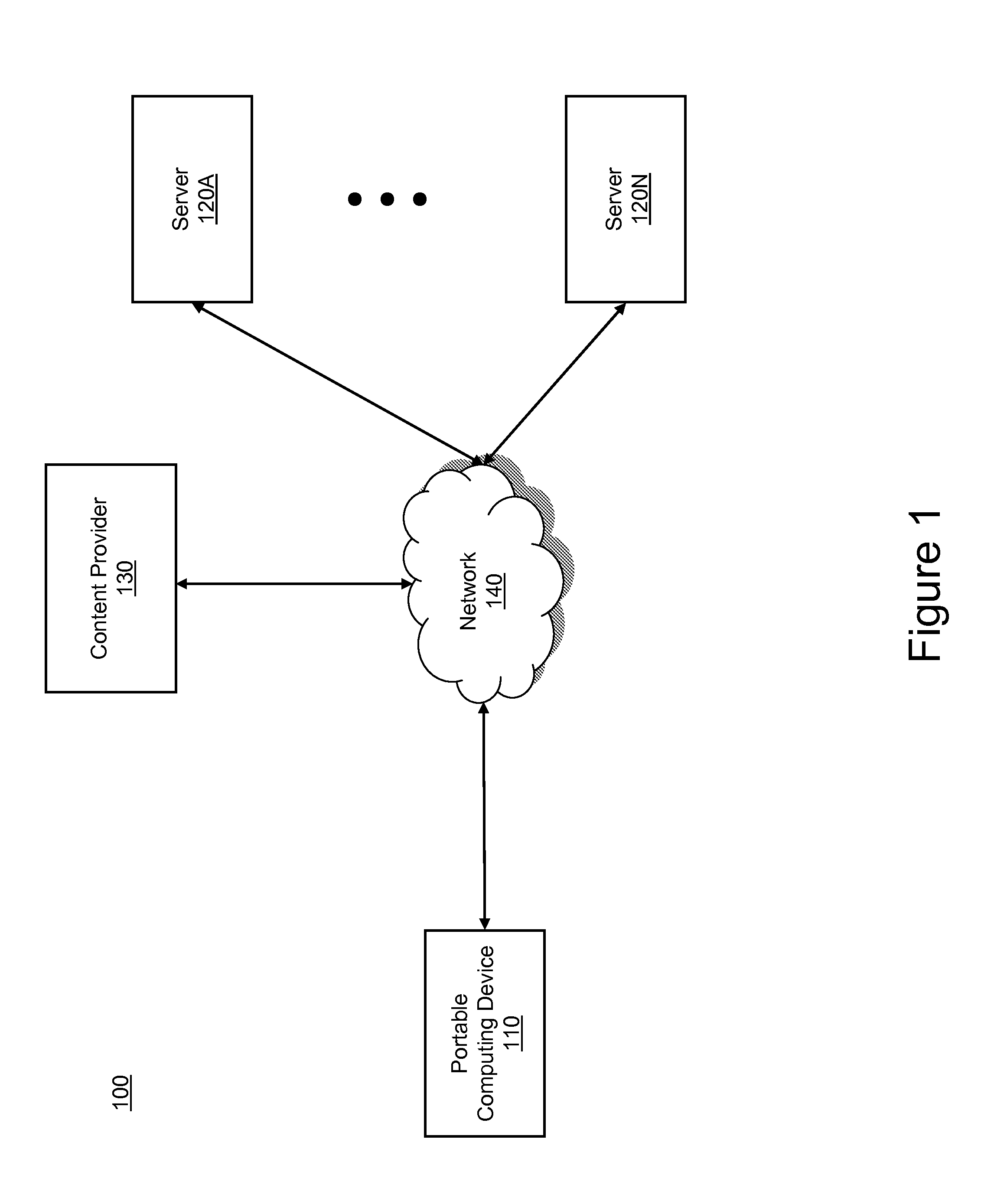
Self-managed network access using localized access management
ActiveUS7574731B2Provide usageAvoid modificationRandom number generatorsUser identity/authority verificationProgram planningBack end server
The invention provides a method and system for locally tracking network usage and enforcing usage plans at a client device. In an embodiment of the invention, a unique physical key, or token, is installed at a client device of one or more networks. The key comprises a usage application and one or more access parameters designated the conditions and / or limits of a particular network usage plan. Upon initial connection to the network, the usage application grants or denies access to the network based on an analysis of the current values of the access parameters. Therefore, network usage tracking and enforcement is made simple and automatic without requiring any back-end servers on the network while still providing ultimate flexibility in changing billing plans for any number of users at any time.
Owner:KOOLSPAN
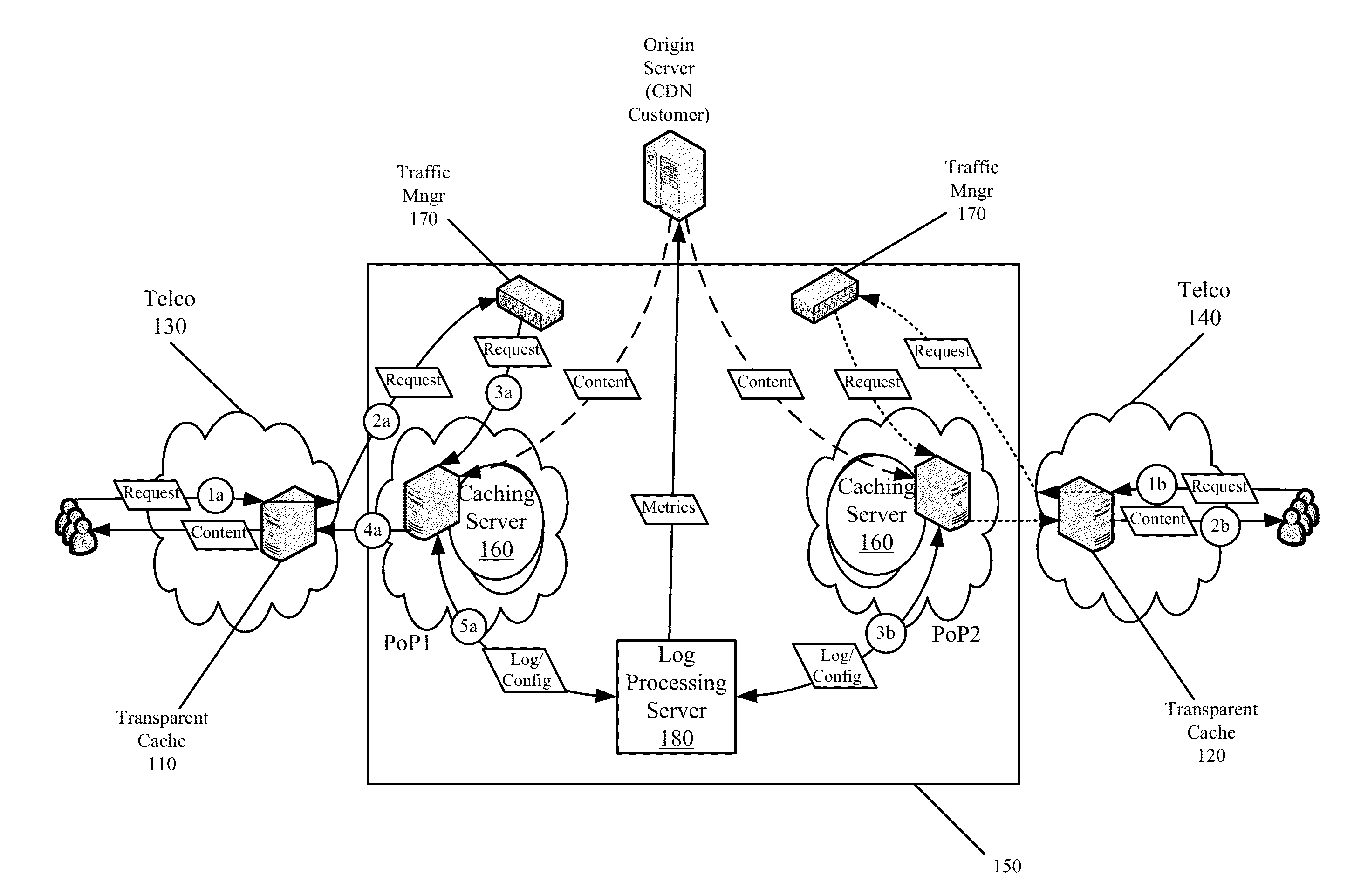
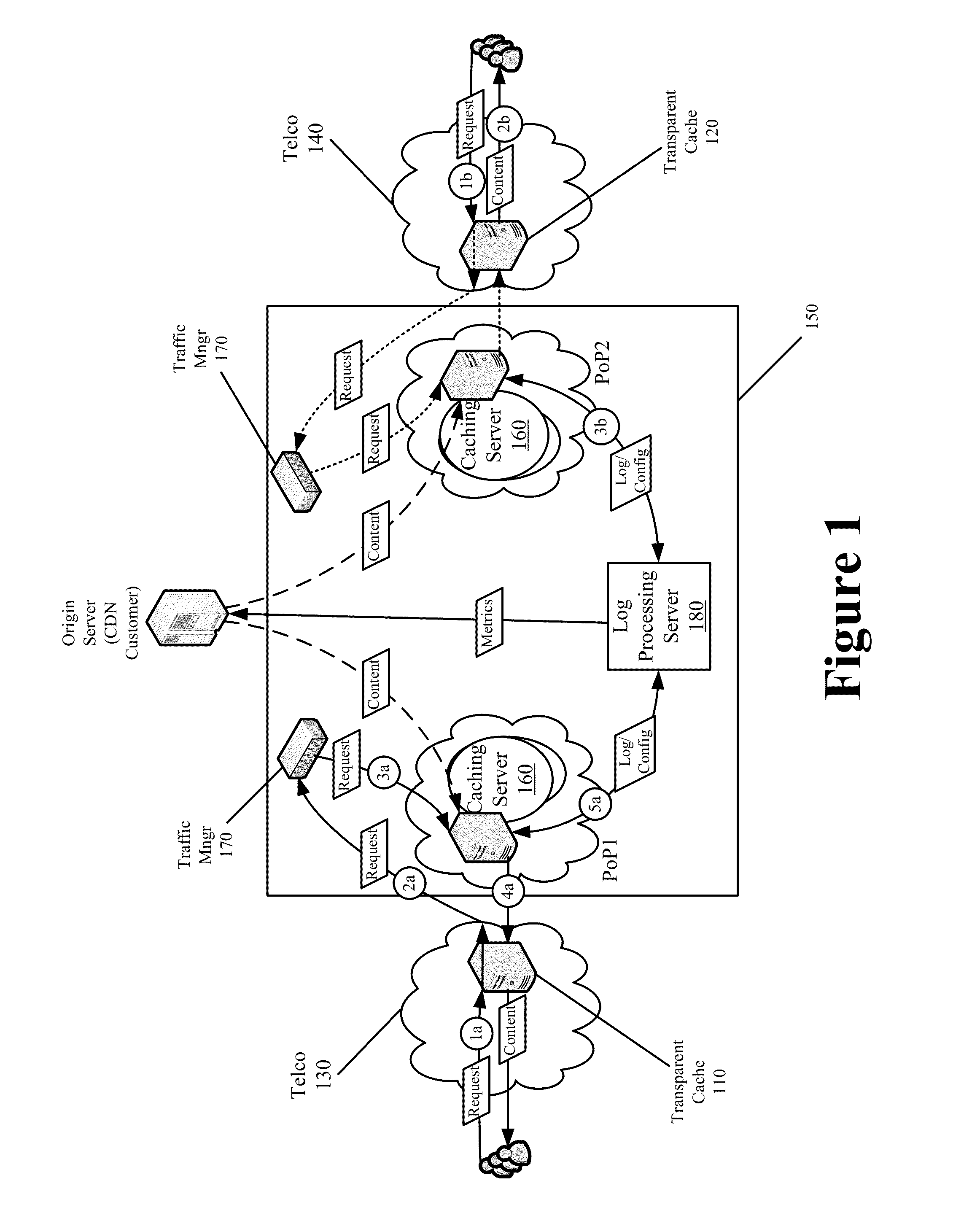
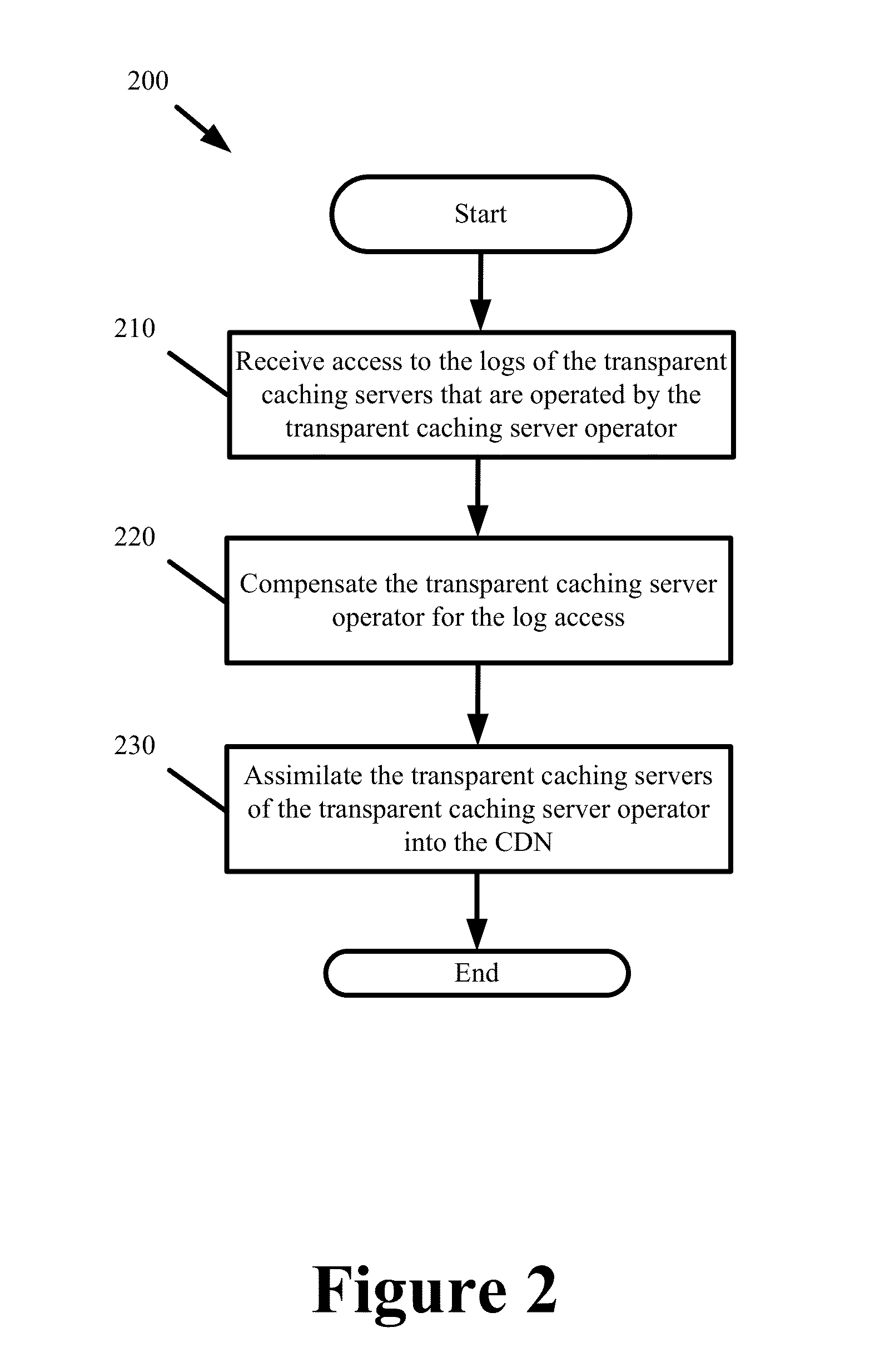
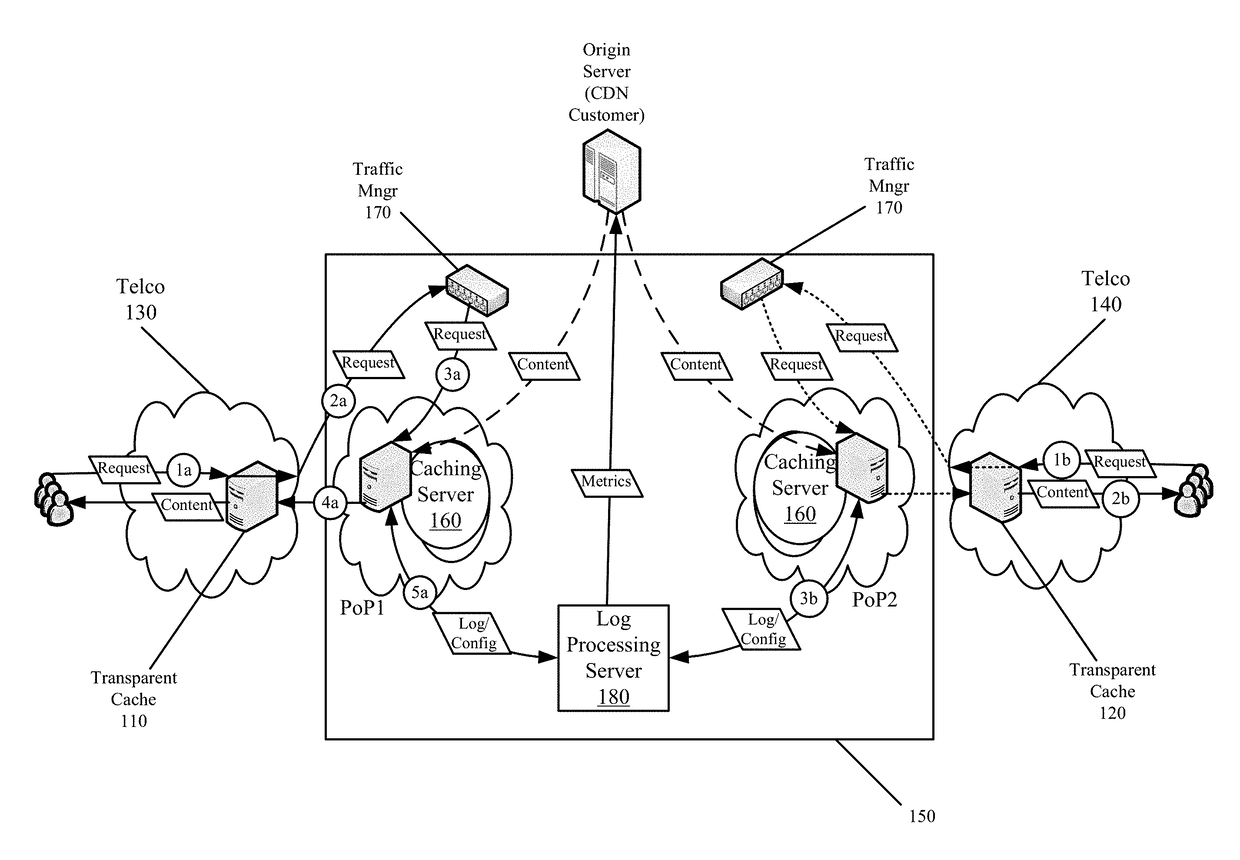
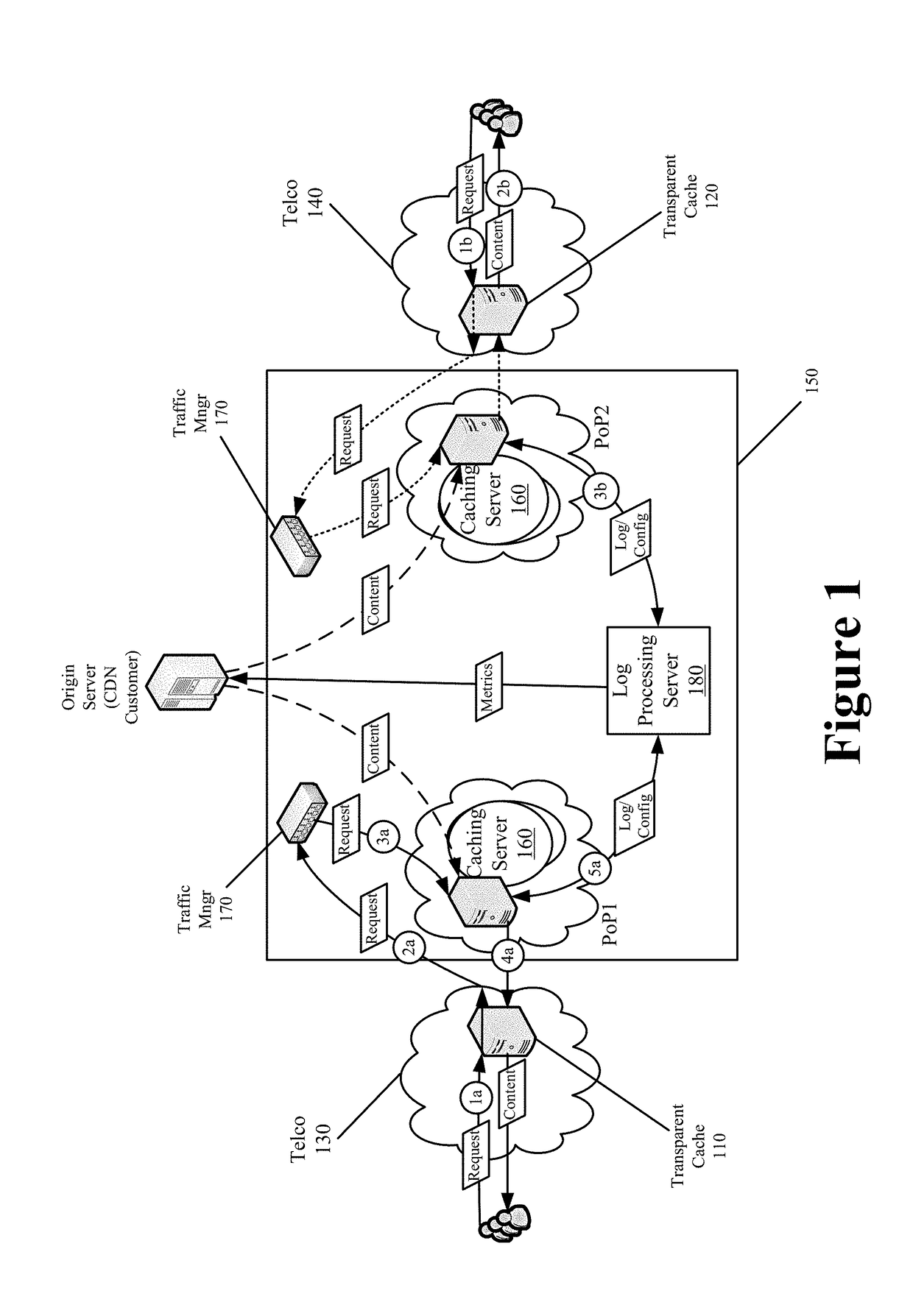
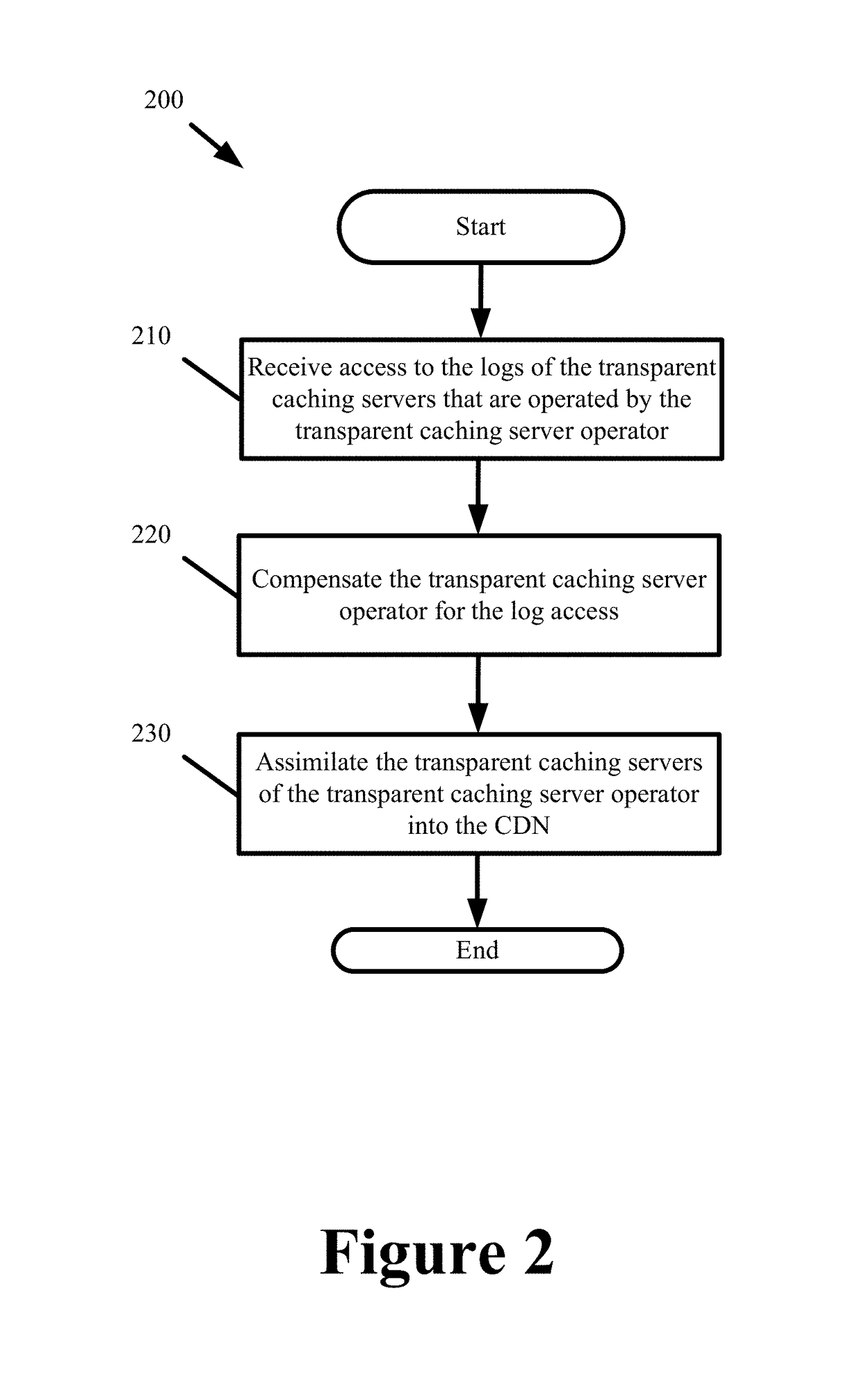
End-to-End Content Delivery Network Incorporating Independently Operated Transparent Caches and Proxy Caches
ActiveUS20130046883A1Accurately and comprehensively track and report metricImproves content deliveryDigital data information retrievalDigital computer detailsServer logCache server
Some embodiments provide an end-to-end federated CDN solution that assimilates a transparent caching server that is operated by a transparent caching server operator into a CDN that independently operates CDN caching servers. Specifically, the logs from the transparent caching server are assimilated into the CDN by aggregating the logs from the transparent caching server and processing the transparent caching server logs to identify network usage for content of a CDN content provider customer that is delivered by the transparent caching server. The network usage is then combined with the network usage that tracked by the CDN caching servers in order to provide comprehensive report metrics for the content provider customer and to bill the content provider customer for all network usage related to delivering the content provider customer's content irrespective of whether the content was delivered by a transparent caching server or a CDN caching server.
Owner:EDGIO INC
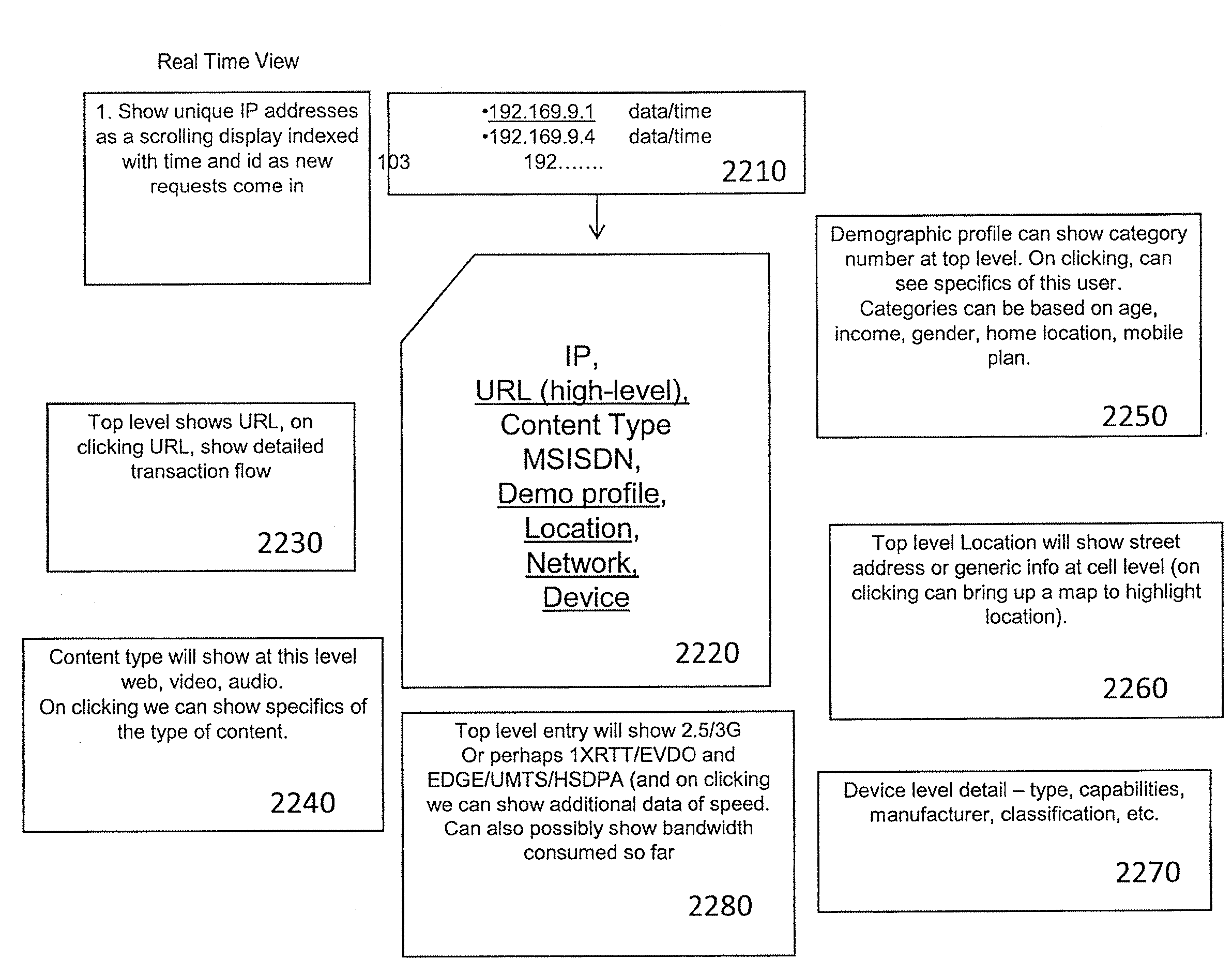
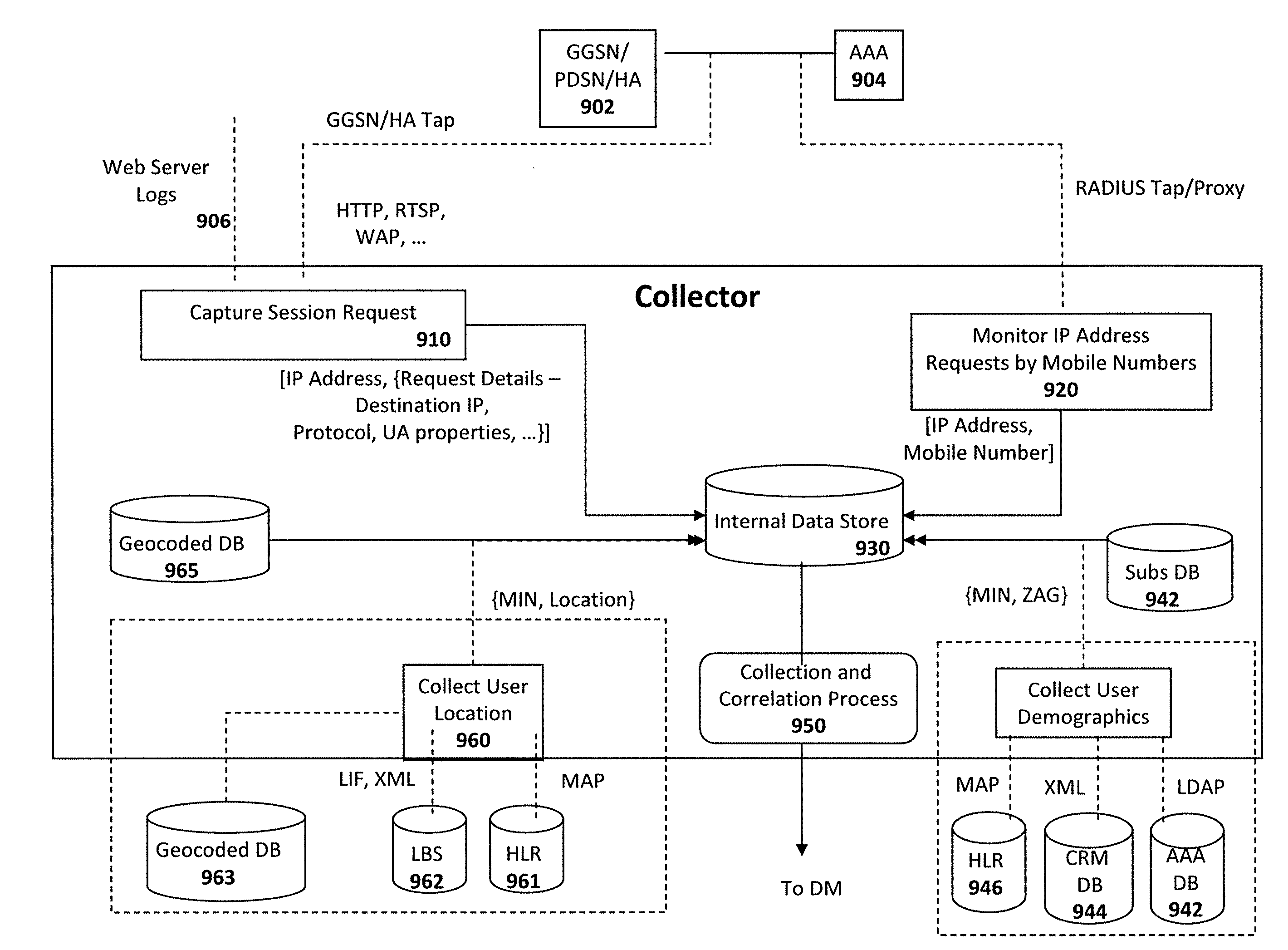
Method and apparatus for storing data on application-level activity and other user information to enable real-time multi-dimensional reporting about user of a mobile data network
A method and apparatus for storing data on application-level activity and other user information to enable real-time multi-dimensional reporting about a user of a mobile data network. A data manager receives information about application-level activity from a mobile data network and stores the information to provide dynamic real-time reporting on network usage. The data manager comprises a database, data processing module, and analytics module. The database stores the application-level data for a predetermined period of time. The data processing module monitors the data to determine if it corresponds to a set of defined reports. If the data is relevant, the processing module updates the defined reports. The analytics module accesses the database to retrieve information satisfying operator queries about network usage. If the operator chooses to convert the query into a defined report, the analytics module creates a newly defined report and populates it accordingly.
Owner:RIBBON COMM SECURITIES CORP
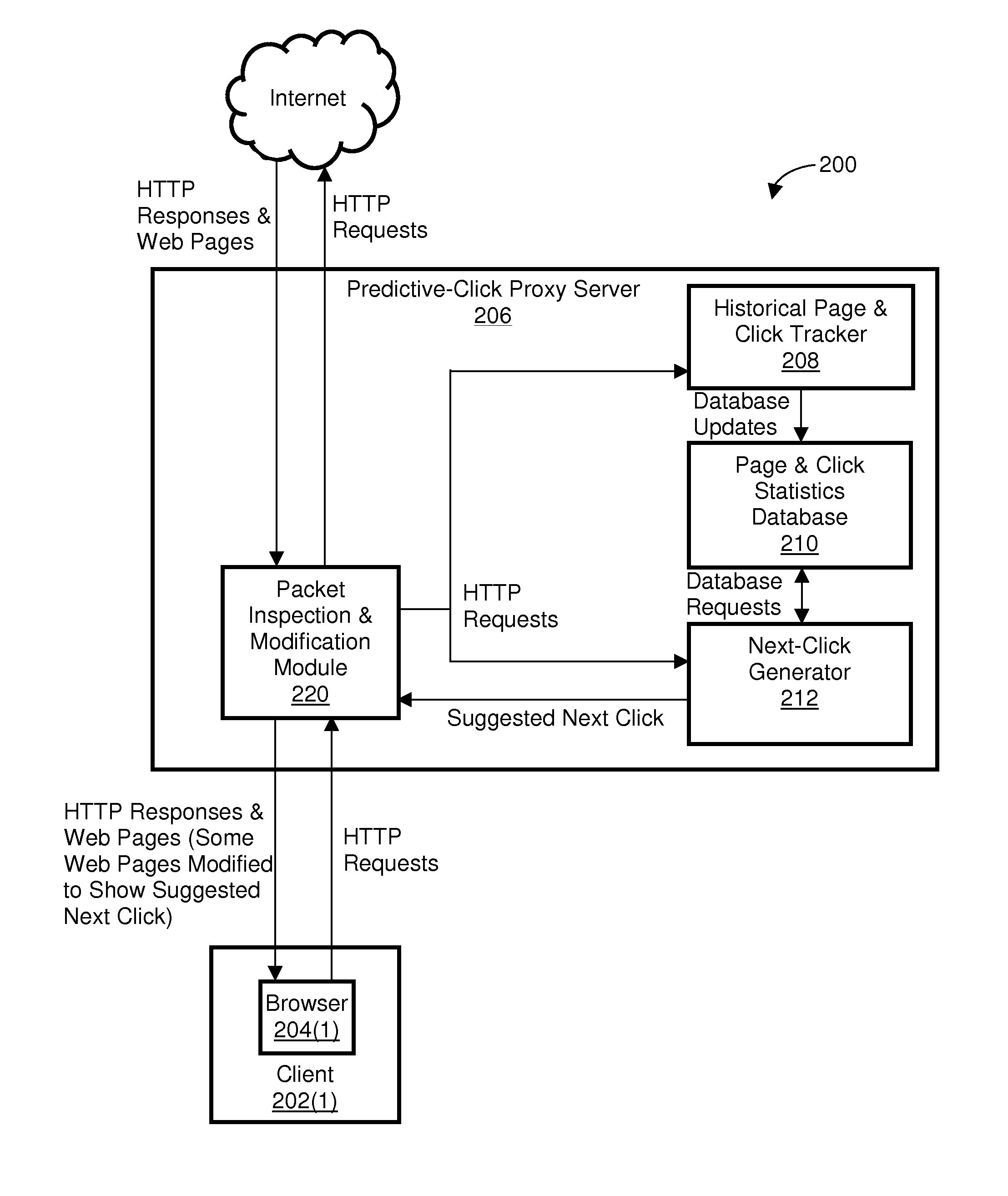
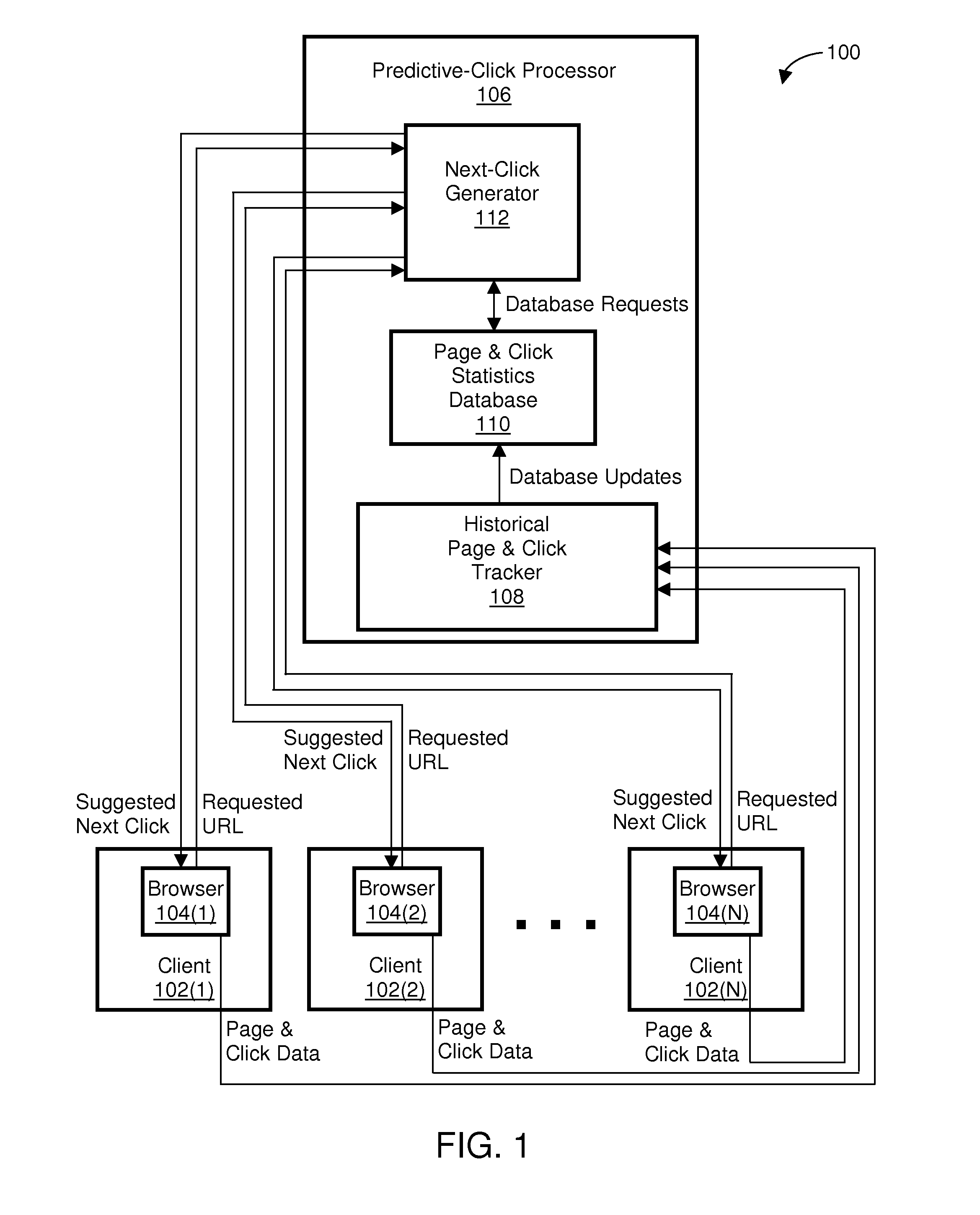
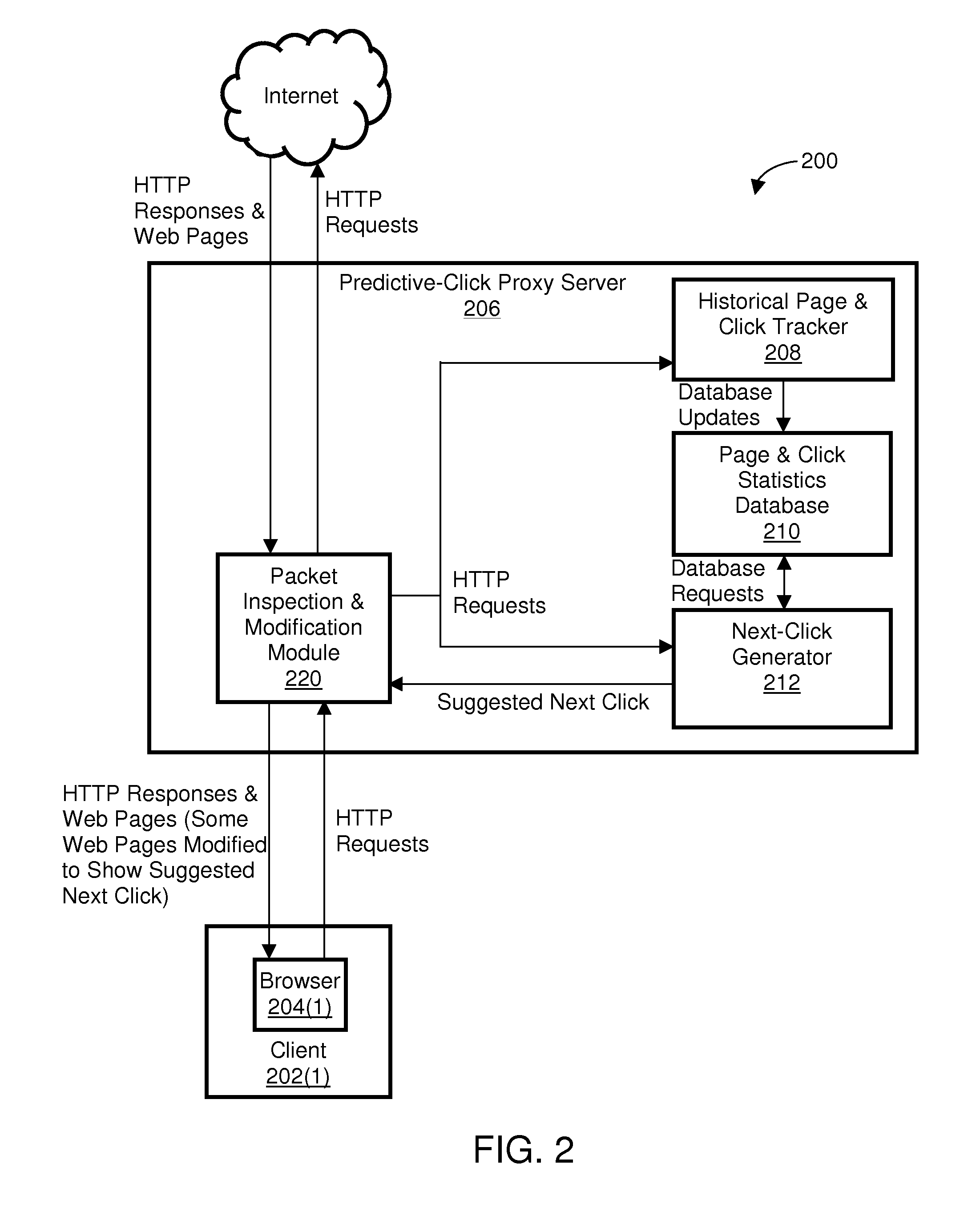
Enabling predictive web browsing
InactiveUS20120137201A1Altering its appearanceSpecial data processing applicationsWeb data browsing optimisationEeg dataWeb page
A system and method for determining and displaying, in a predictive manner, relevant “next clicks” based upon historical web-usage patterns of previous visitors (the browsing user and / or other users) to referring web pages. In one embodiment, identification of one or more links selected by previous visitors on a plurality of referring web pages is stored in a database. When the browsing user initiates a request to view a referring web page for which one or more links exist in the database, the appearance of those links on the referring web page is altered to suggest those links to the browsing user. Thus, the browsing user is given suggestions as to the most probable path (based upon his / her own history and / or the history of others) through each referring web page for which one or more links are stored in the database, thereby streamlining the browsing process.
Owner:ALCATEL LUCENT SAS
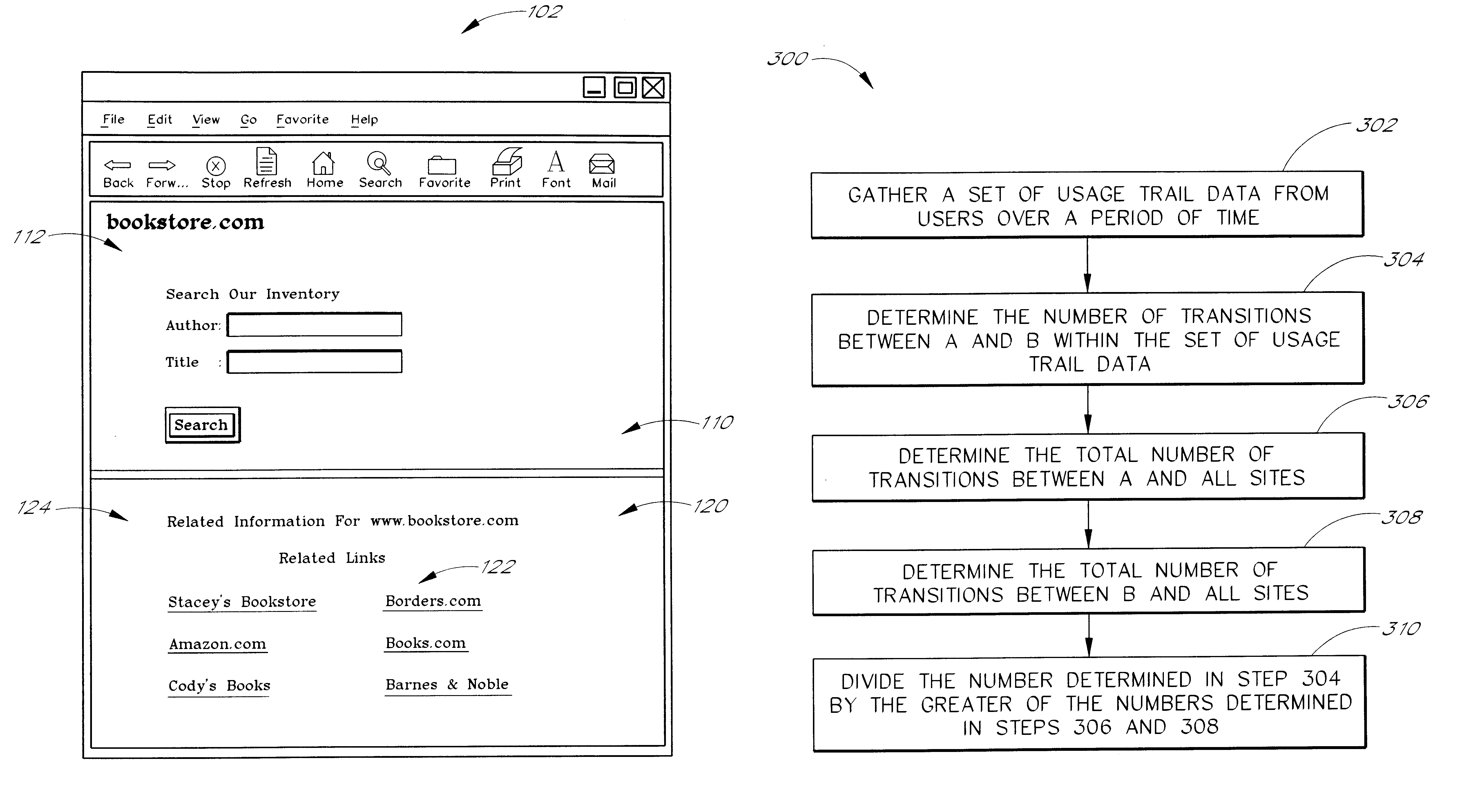
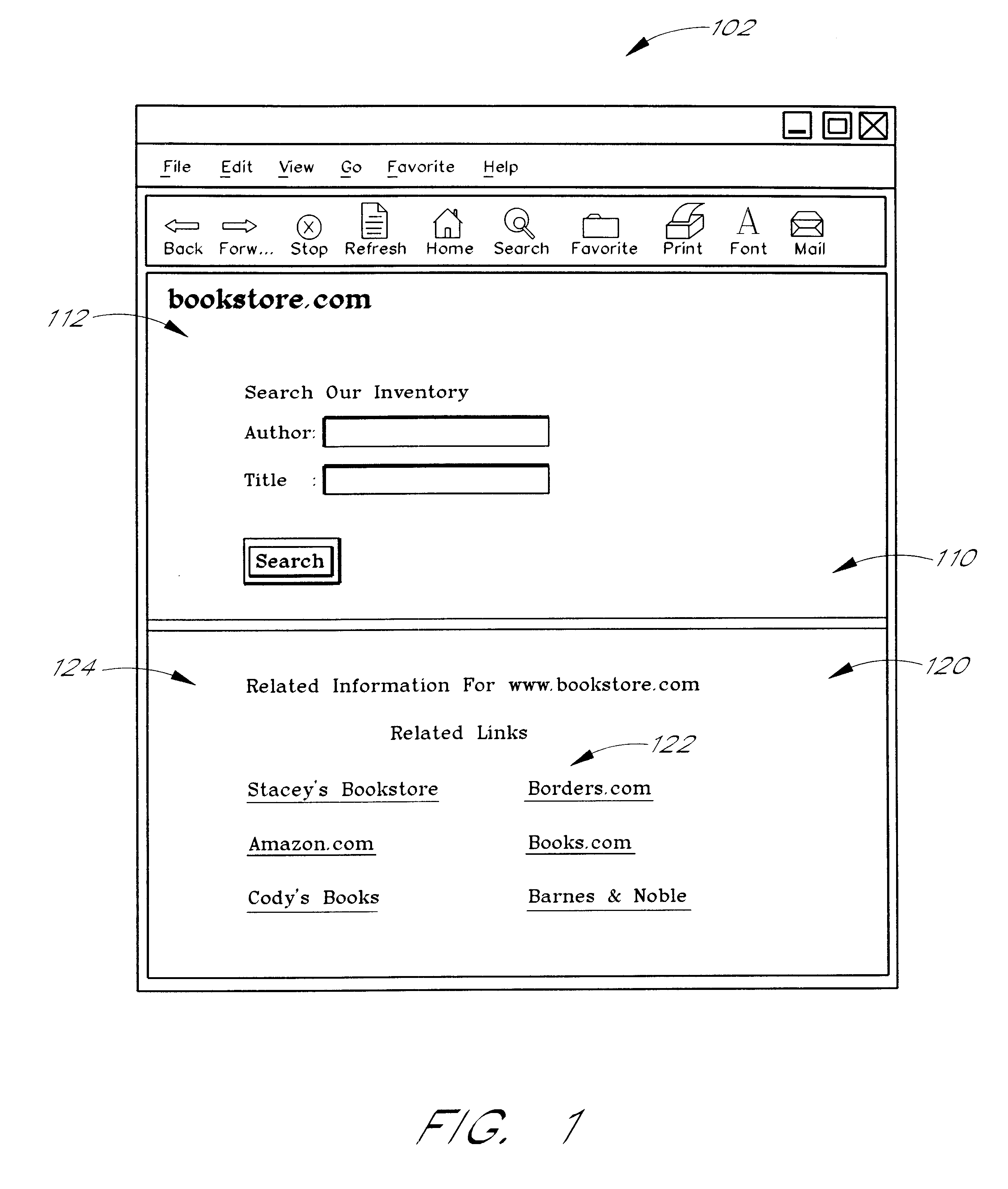
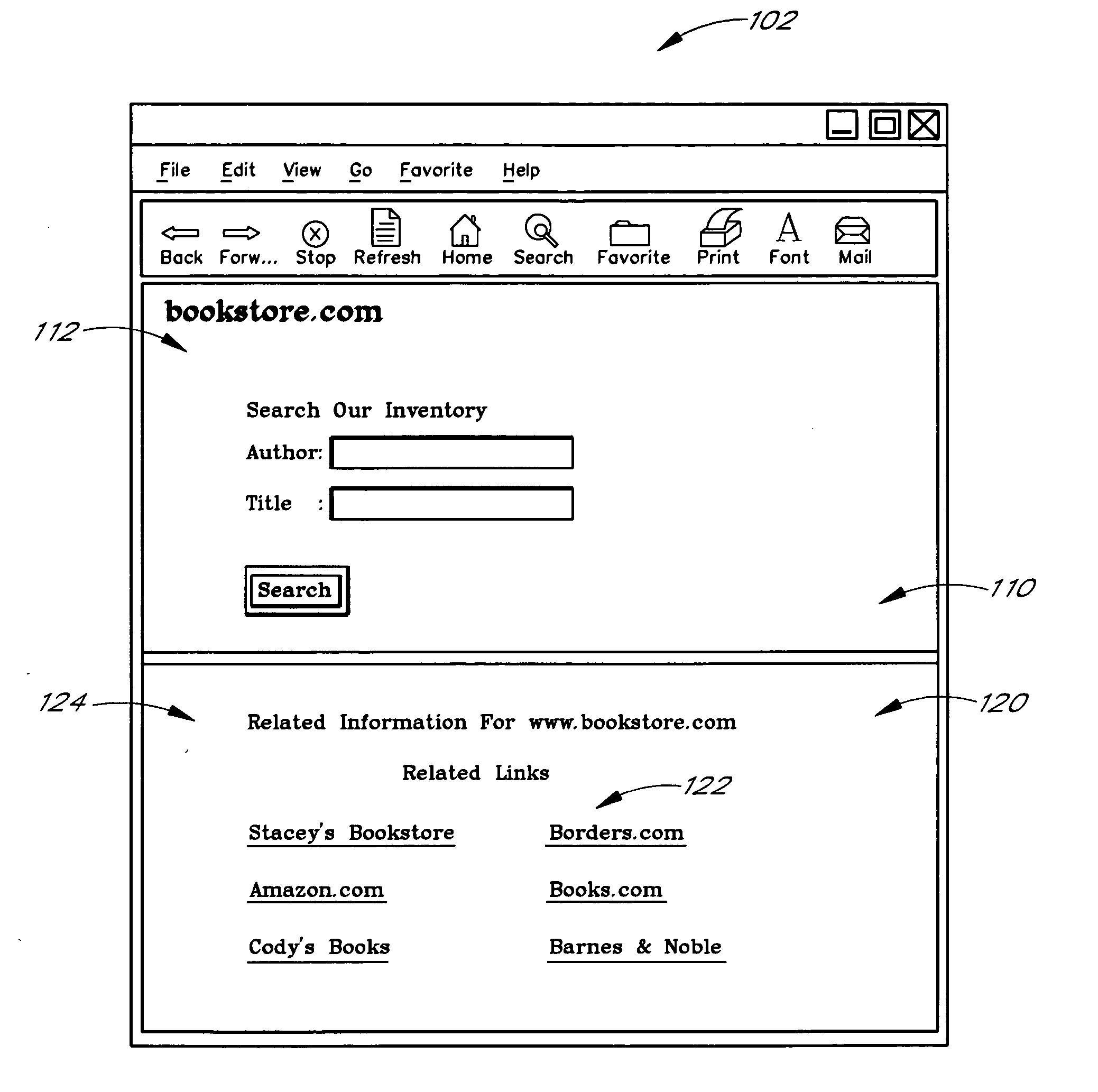
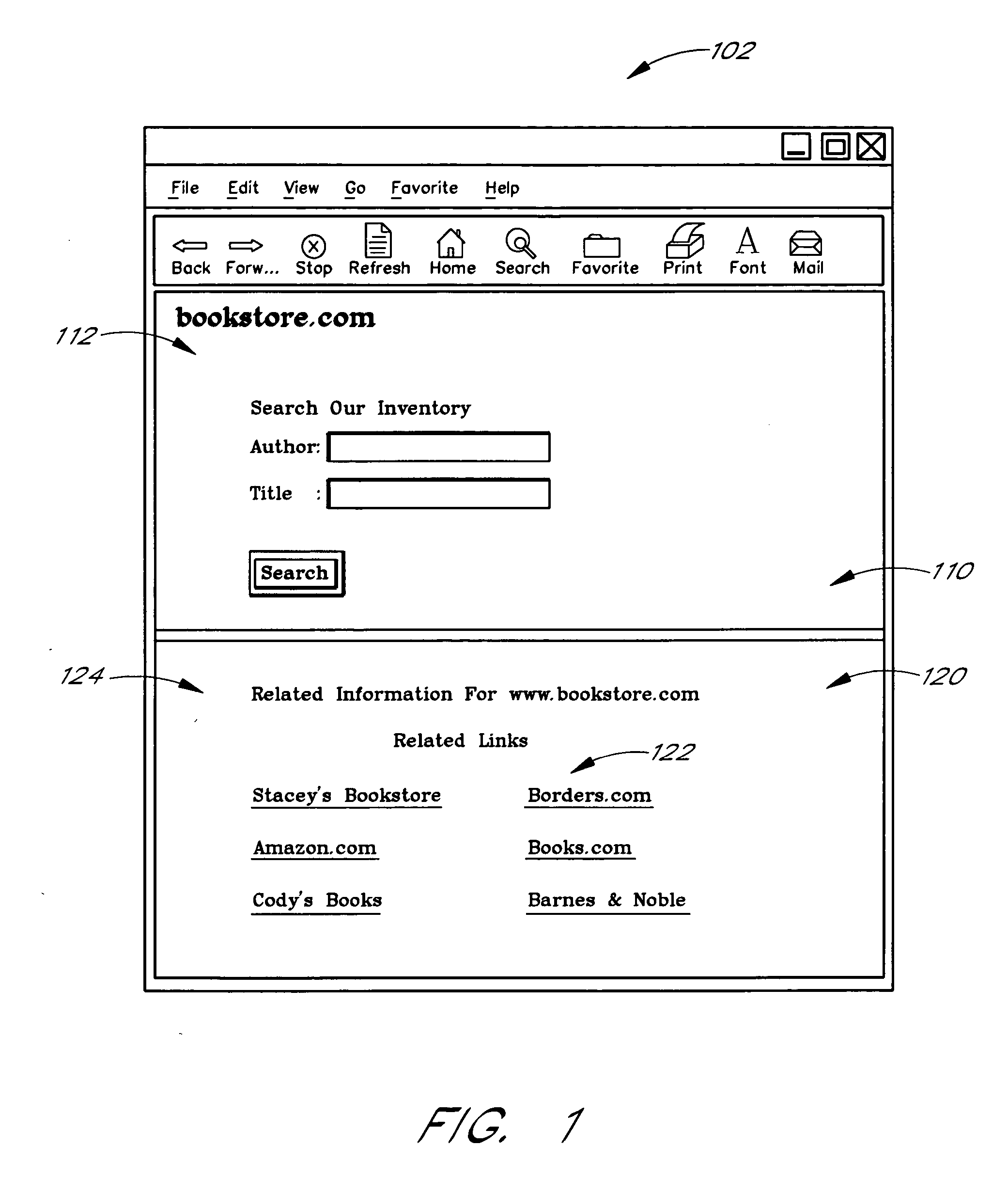
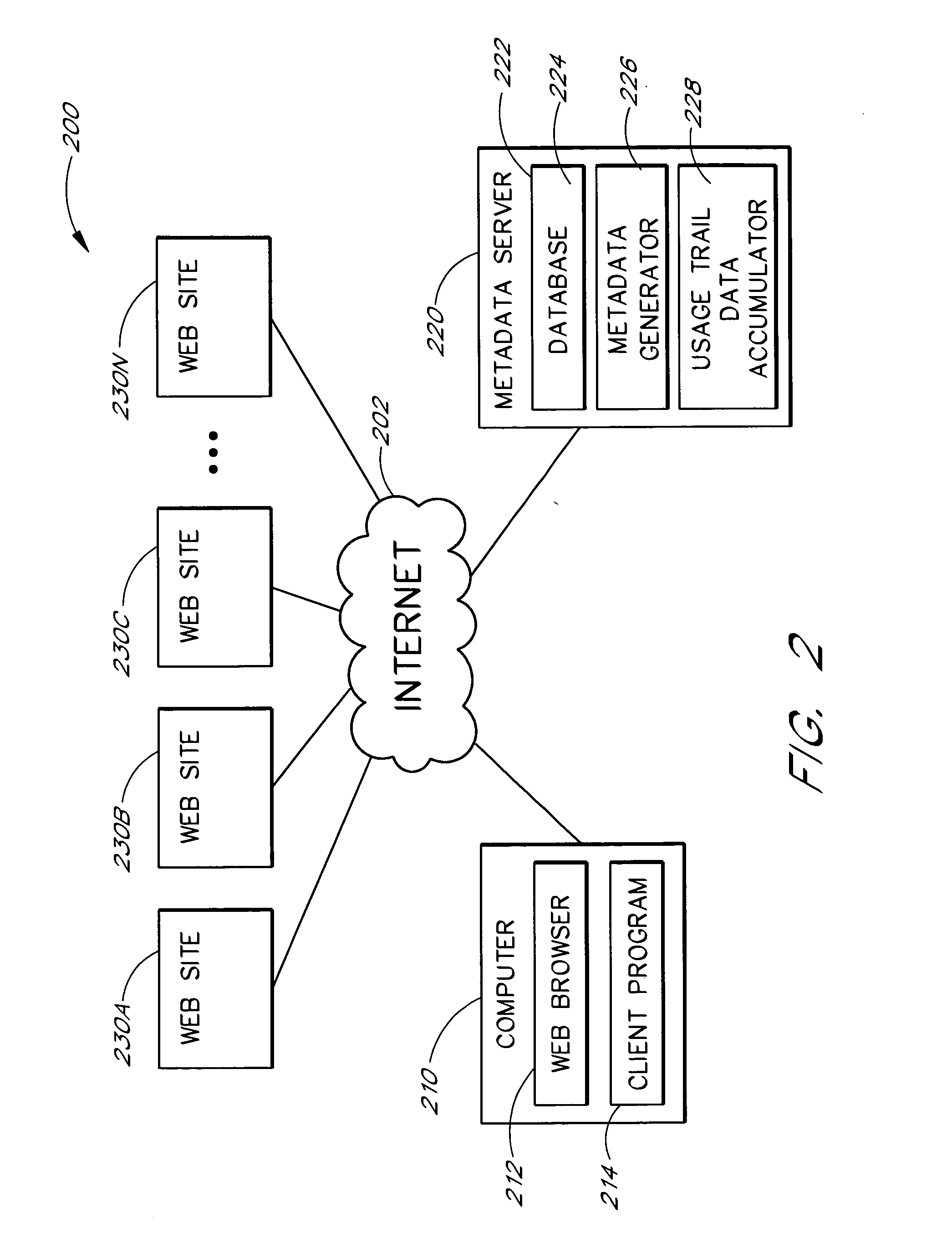
Use of web usage trail data to identify related links
Related links for web sites or web pages are determined from the web usage trails of a population of users. Each usage trail is preferably in the general form of a sequence of URLs accessed by a user during a browsing session. The usage trails are preferably collected using a special client application that operates in conjunction with a web browser and reports the navigation activities of users. In a preferred embodiment, the relatedness of two web sites or pages A and B is determined using a minimum sensitivity calculation that takes into consideration the number of transitions that occurred between A and B relative to the total number of transitions that involved A and / or B. More specifically, the minimum sensitivity between A and B for a set of usage trail data is preferably determined by dividing the number of transitions between A and B by the greater of (i) the total number of transitions between A and all web sites and (ii) the total number of transitions between B and all web sites. The method may be used independently, or may be used in combination with other methods for identifying related links.
Owner:ALEXA
Video manager and organizer
ActiveUS20080172615A1Large inventoryTelevision system detailsMetadata video data retrievalHyperlinkWeb page
An online video search system, including a tag discoverer including a web encyclopedia crawler for (i) accessing a web encyclopedia to find web pages related to at least one designated reference topic, and (ii) retrieving a plurality of web pages by performing an n-level depth recursive traversal of the web pages found, and web pages that are hyper-linked thereto, a concept extractor for extracting important concepts founds in the retrieved plurality of web pages, and a user interface for providing at least of the important concepts extracted by the web page processor to an online video search engine. A method and a computer-readable storage medium are also described and claimed.
Owner:GULA CONSULTING LLC
Web browser embedded button for structured data extraction and sharing via a social network
InactiveUS20130311875A1Efficient searchNatural language data processingSpecial data processing applicationsWeb siteWeb browser
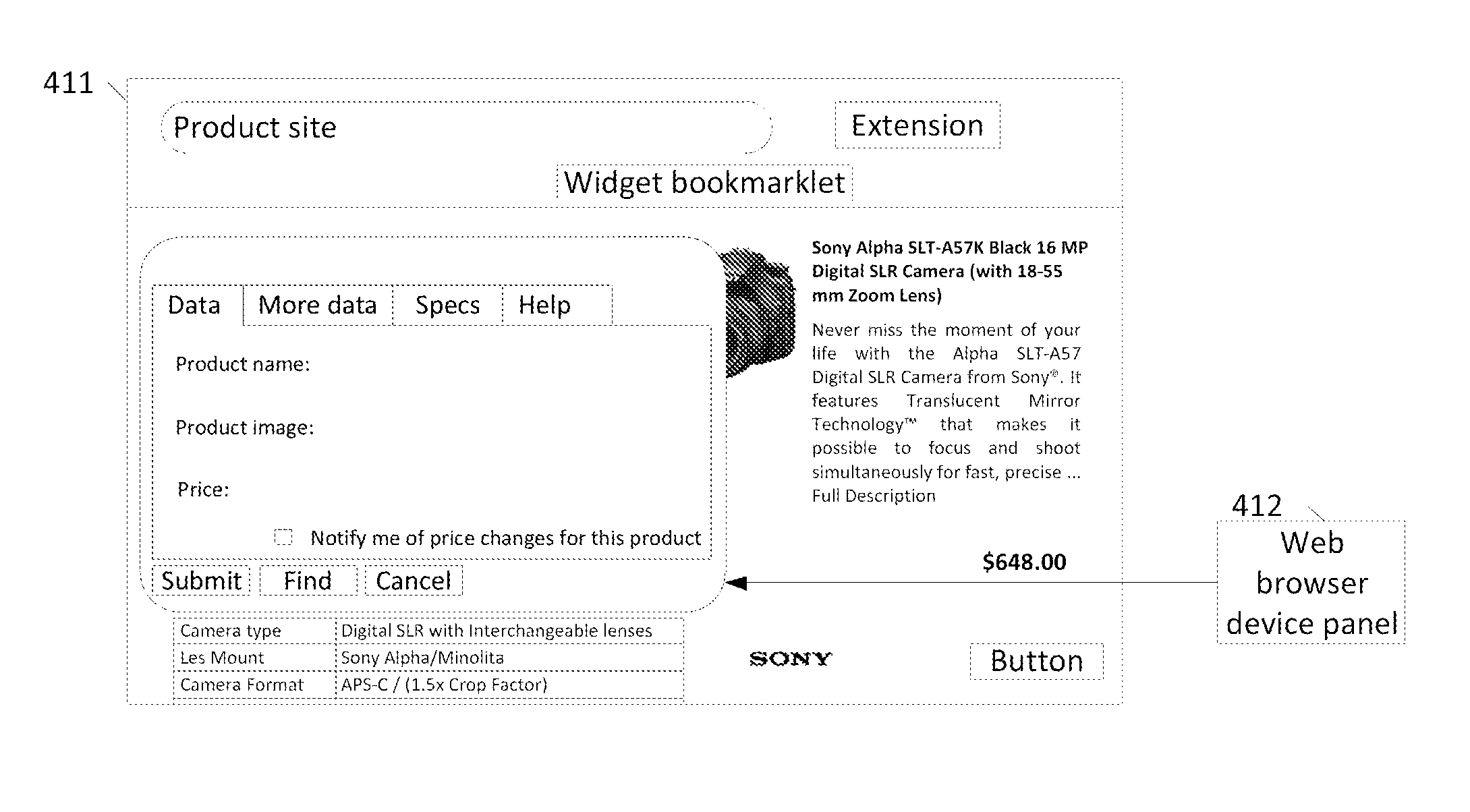
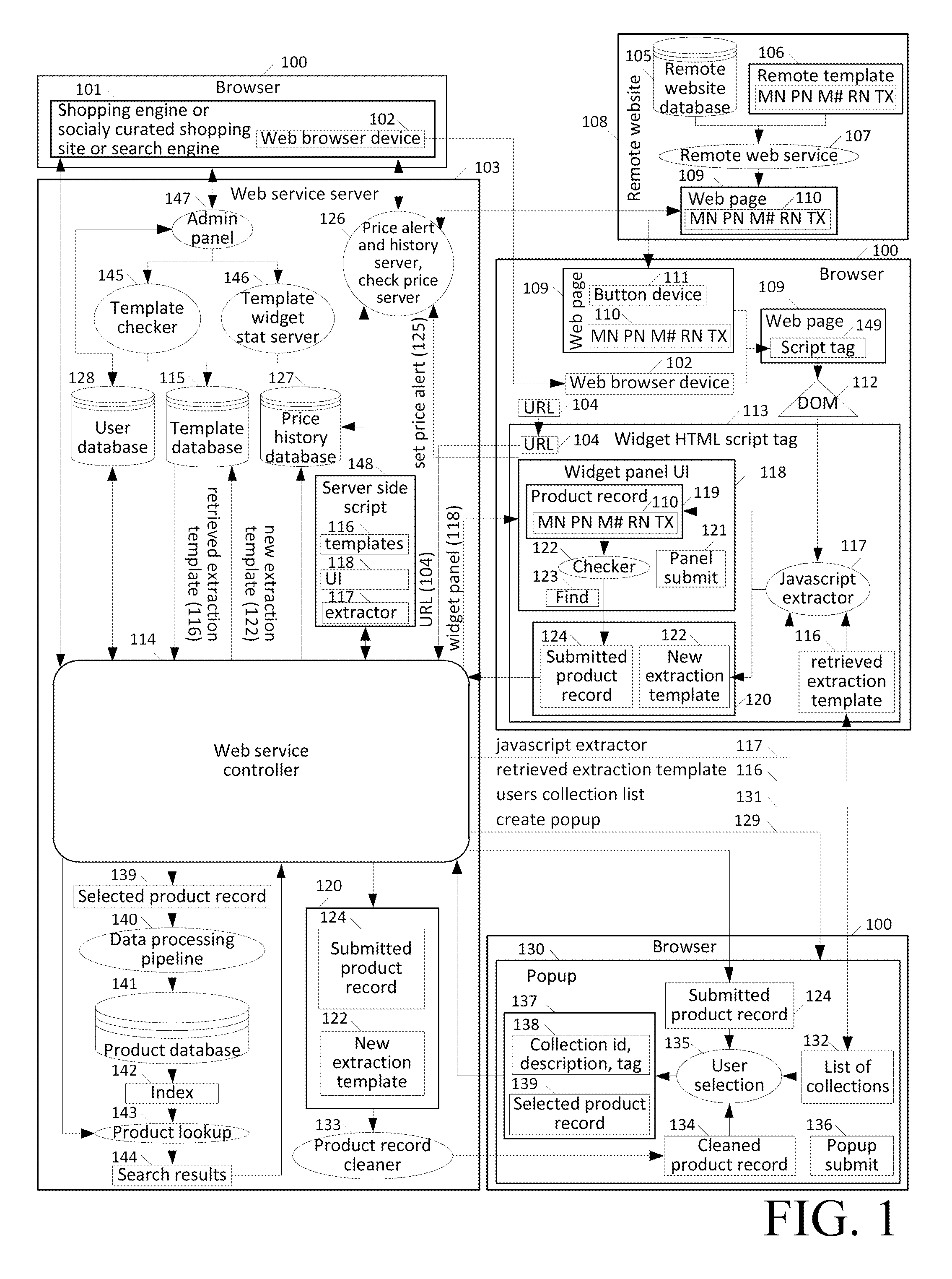
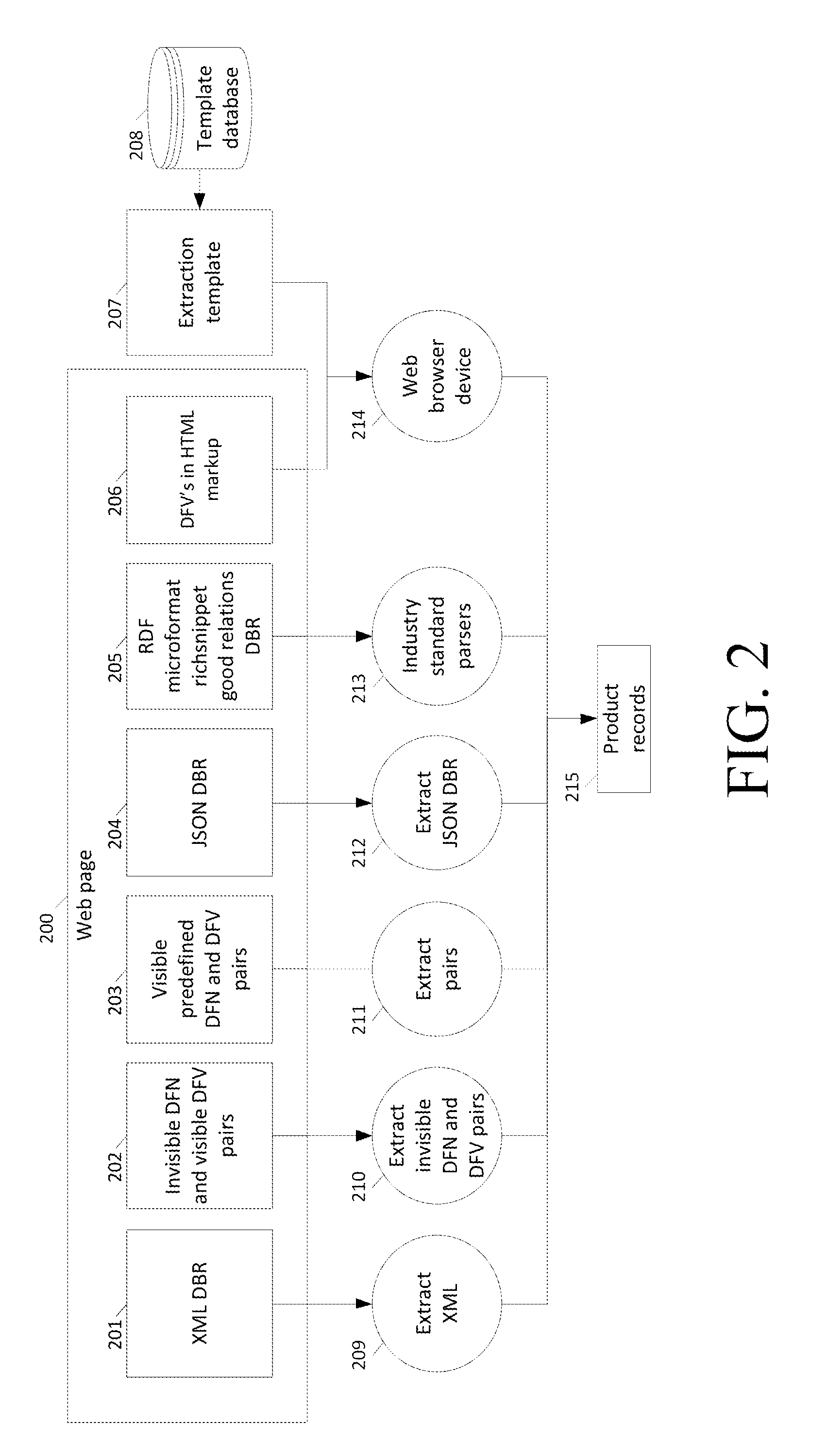
The present invention is directed to a system and method which users can use to identify data base elements in a web page, store the extraction template representing the location and type of elements on the page, extract and store the product record in their collection, use the extraction template to automatically extract all the data from the web site and constantly check the extraction templates for correctness and update the extraction templates if necessary. Additionally, the present invention system provides crowd sourced web page data record extraction template creation to build a database of web page extraction templates which could then be used by others to extract the information from the web pages at the site where the extraction template(s) were created, and to save the information to a social network. Moreover, crowd based web page data record extraction template creation and storage system can be used to create extraction templates for batch extraction of information from remote web sites. Also, the data record information extracted from the web page to find the same or similar products at other web sites can be sited in a central product record data base that is created with the previously mentioned batch extraction system.
Owner:PAPPAS DEREK EDWIN +1
System and Method to Determine Network Usage
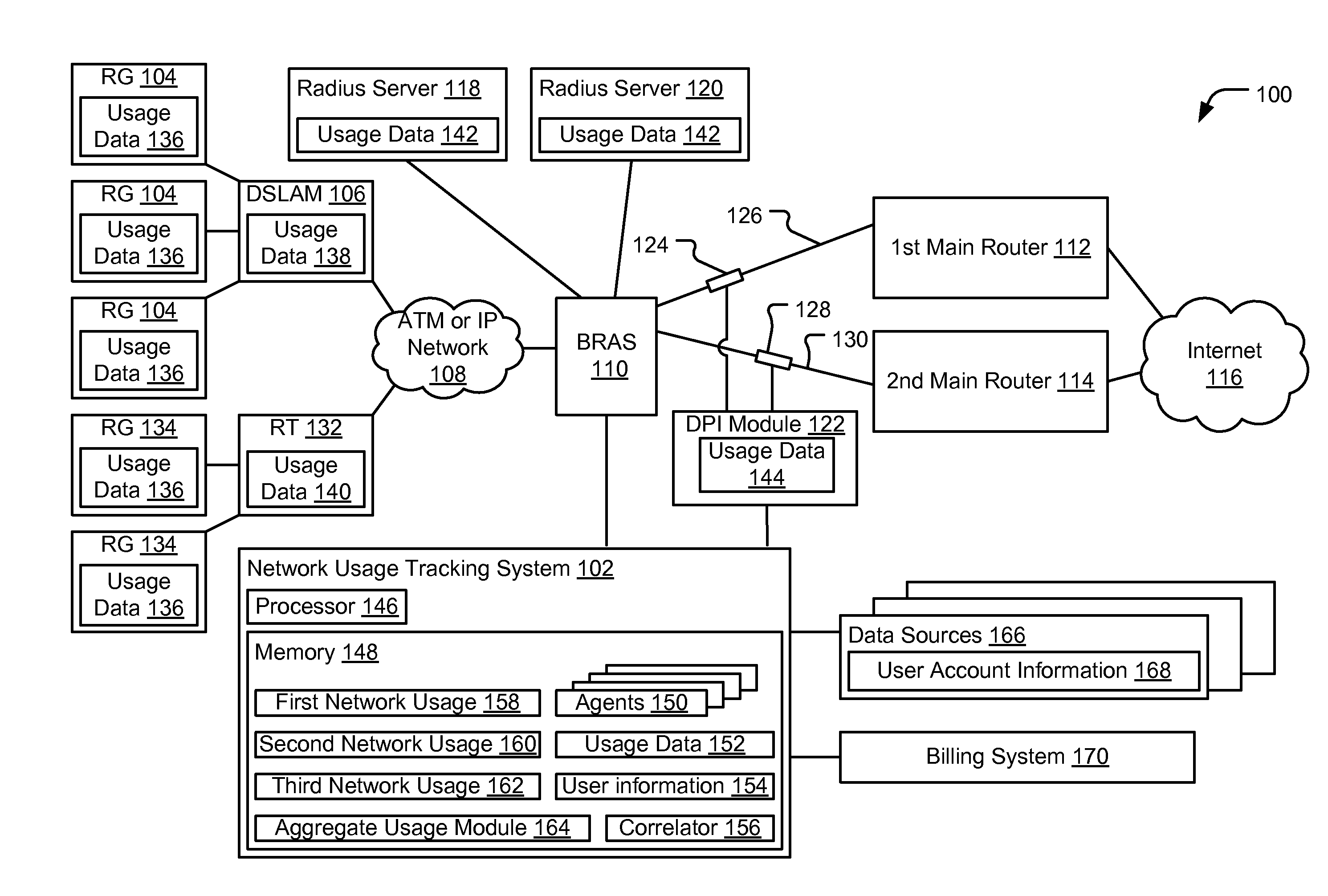
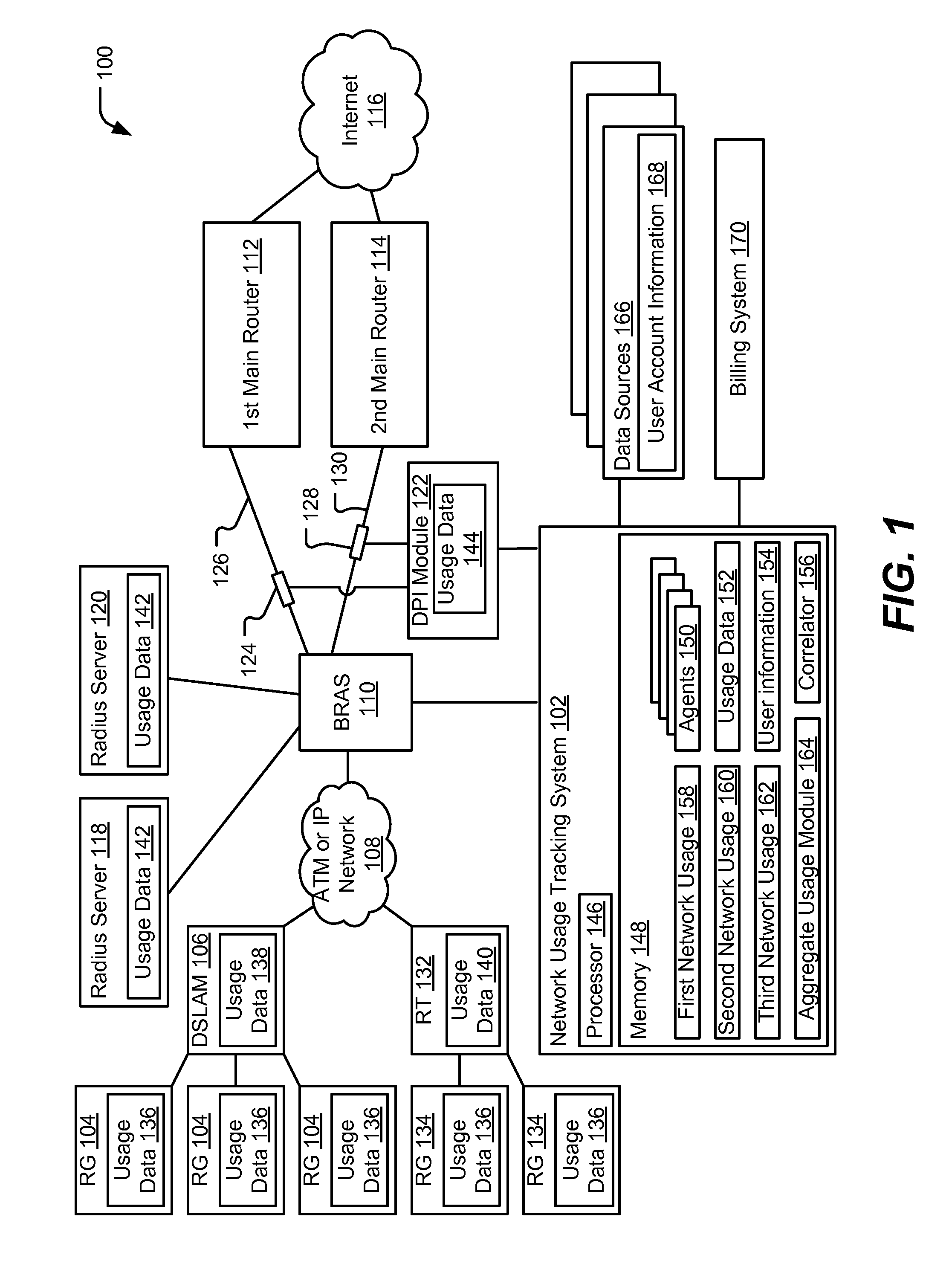
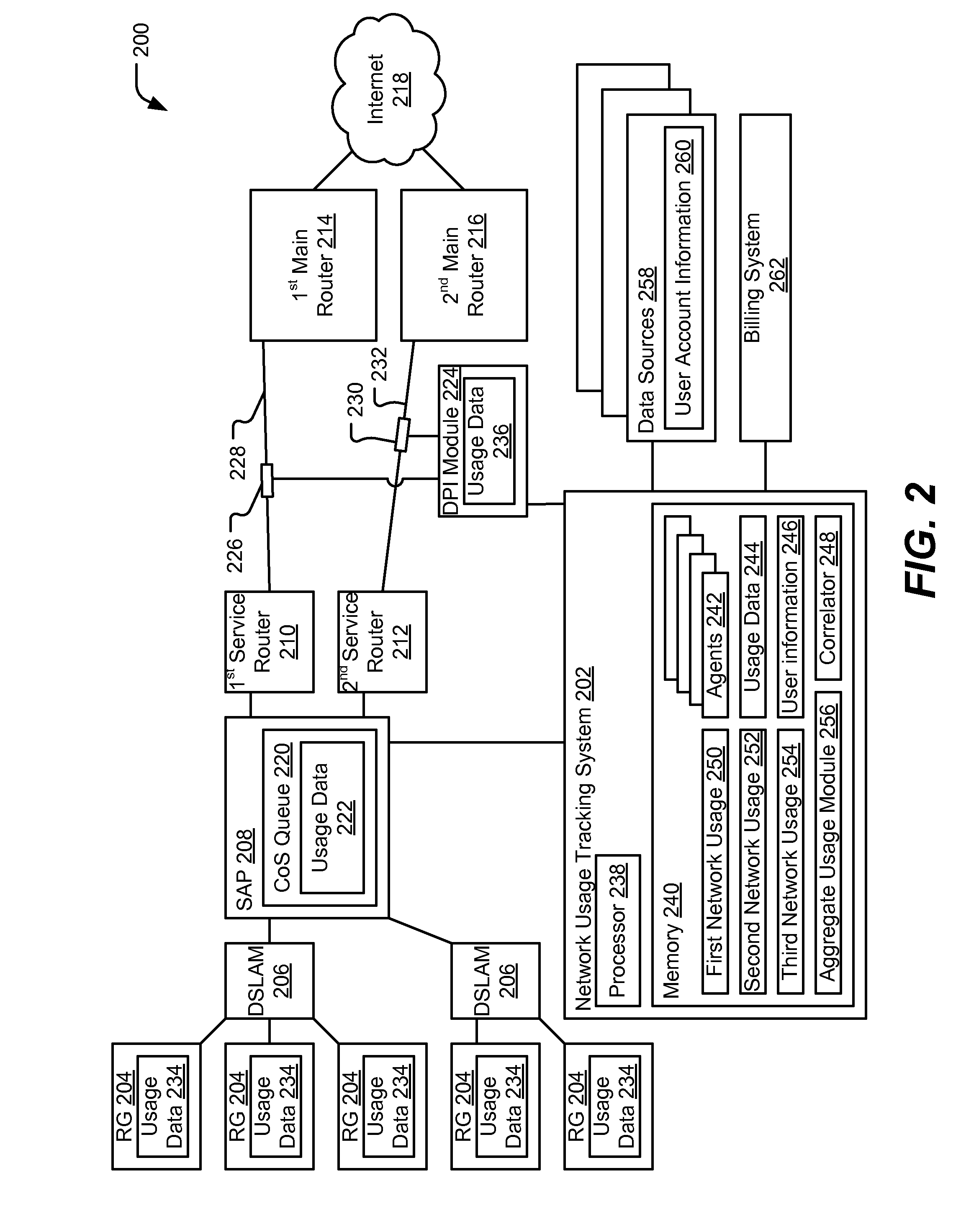
InactiveUS20100318647A1Metering/charging/biilling arrangementsError preventionData matchingUsage data
Systems and methods to measure network usage are provided. A particular method includes collecting first usage data from a first network device of a network at a network usage tracking system. The first network device determines the first usage data based on an inband measurement of data passing through the first network device. The method includes collecting second usage data from a second network device of the network at the network usage tracking system. The first network device and the second network device are different network devices. The method includes matching the first usage data and the second usage data to user accounts. The network usage data is determined based on the first usage data, the second usage data, and the user accounts.
Owner:AT&T INTPROP I L P
Use of browser history file to determine web site reach
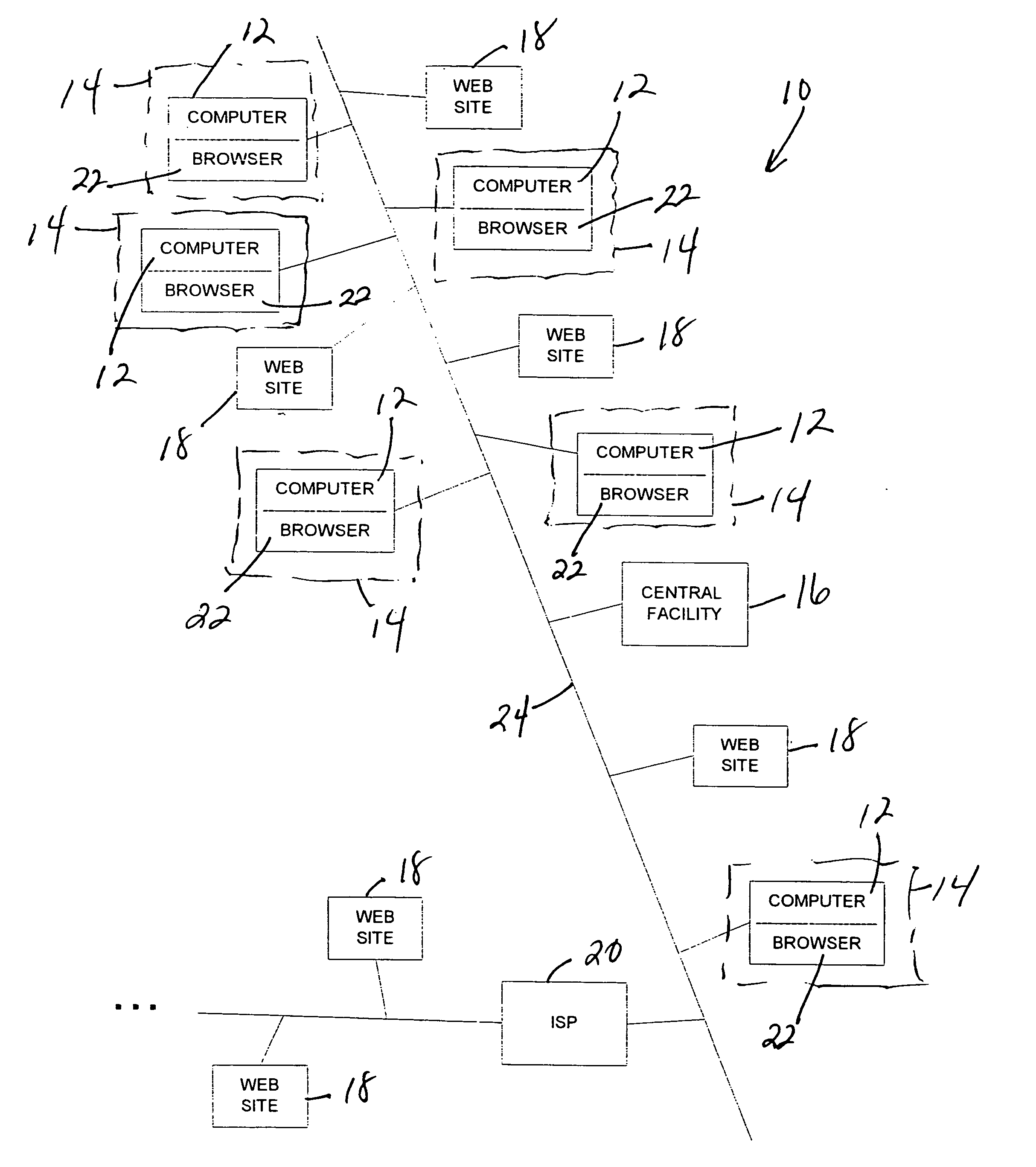
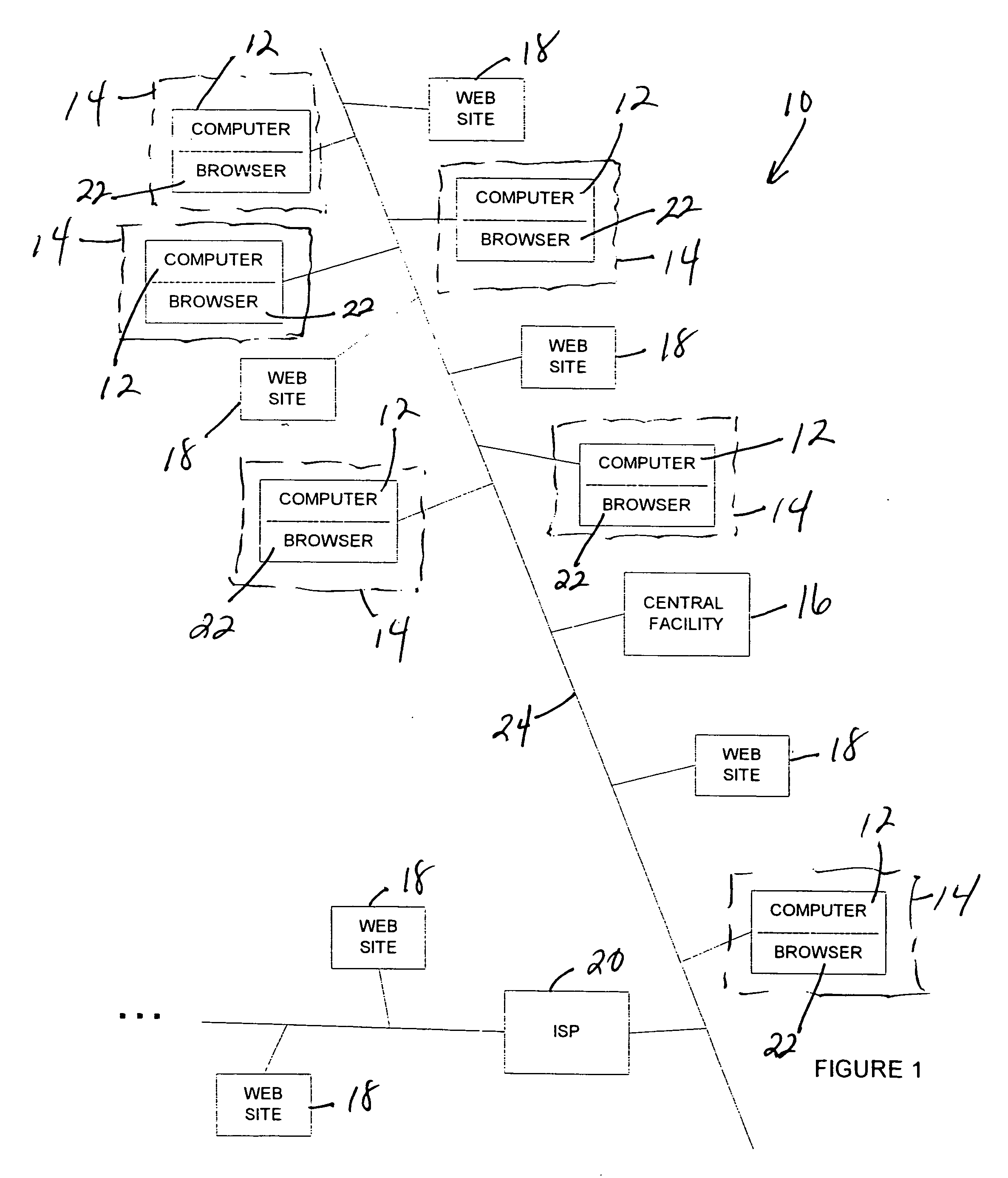
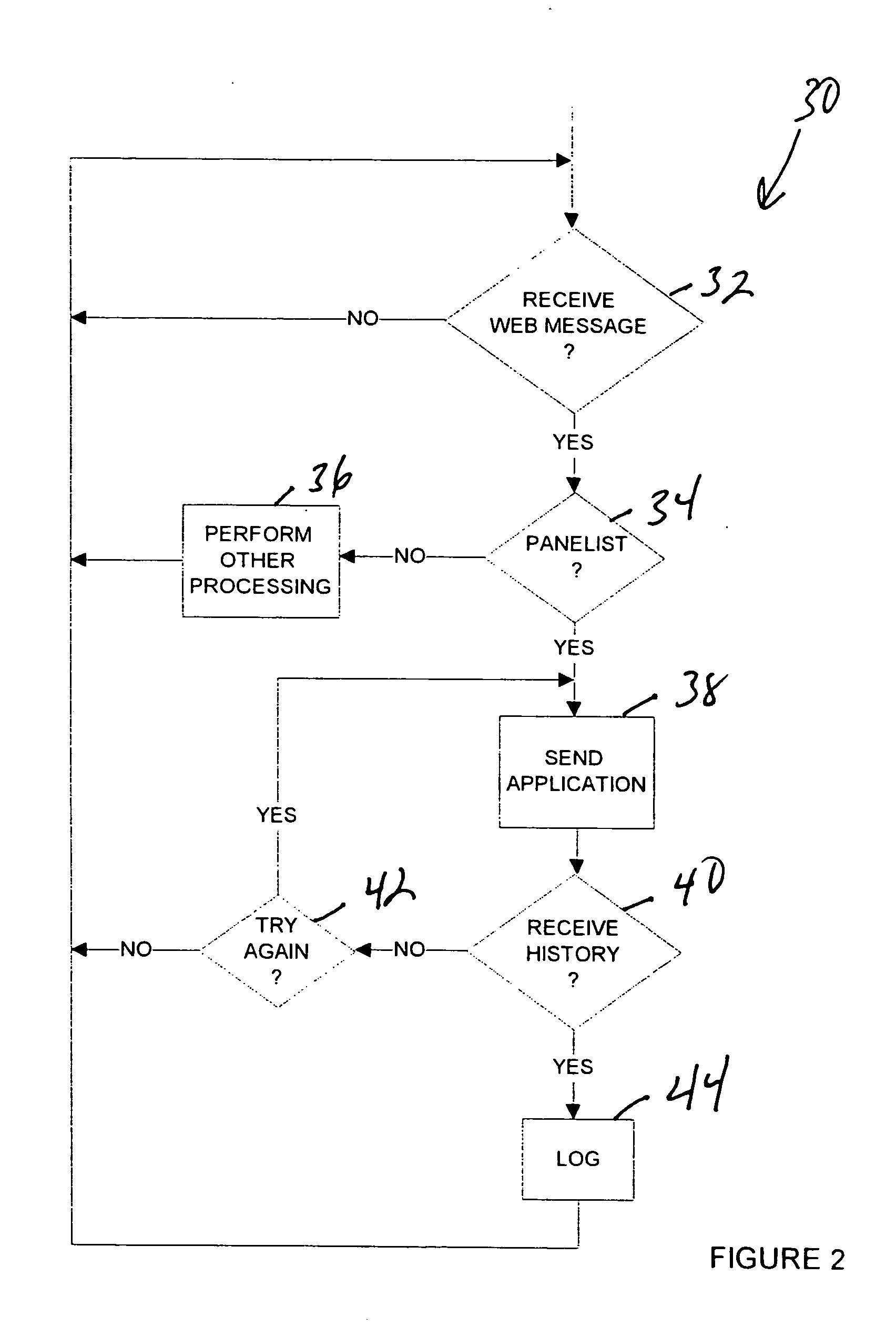
In a method of metering Web usage, a collection program is downloaded from a server to a metered computer in response to a message transmitted from the metered computer to the server, and the collection program is executed on the metered computer in order to collect Web usage history information stored in a history file by a browser running on the metered computer. The collected Web site usage history information is transmitted by the metered computer to the server. The Web site usage history information is stored in the server along with Web site usage history information from other metered computers.
Owner:THE NIELSEN CO (US) LLC
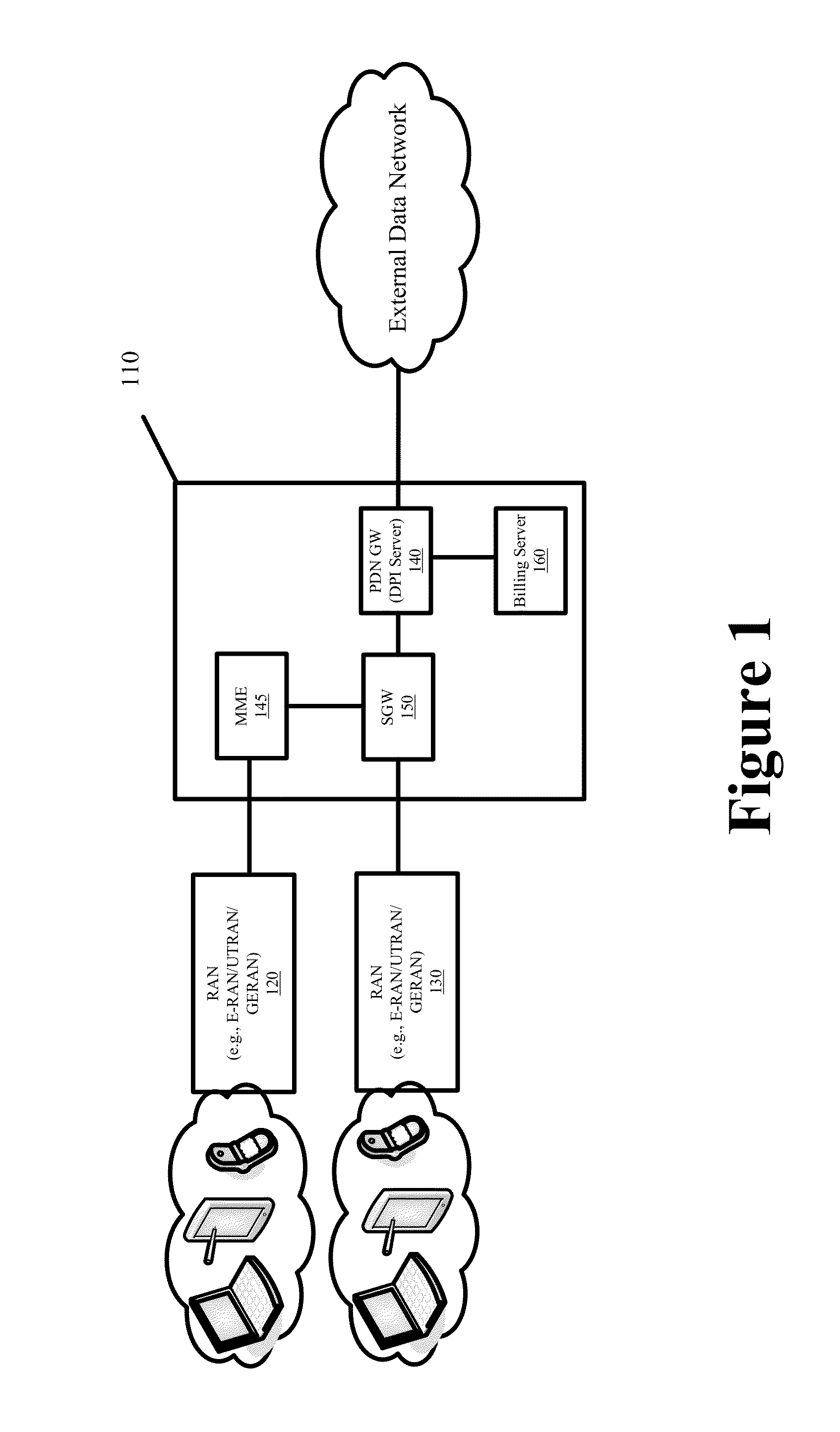
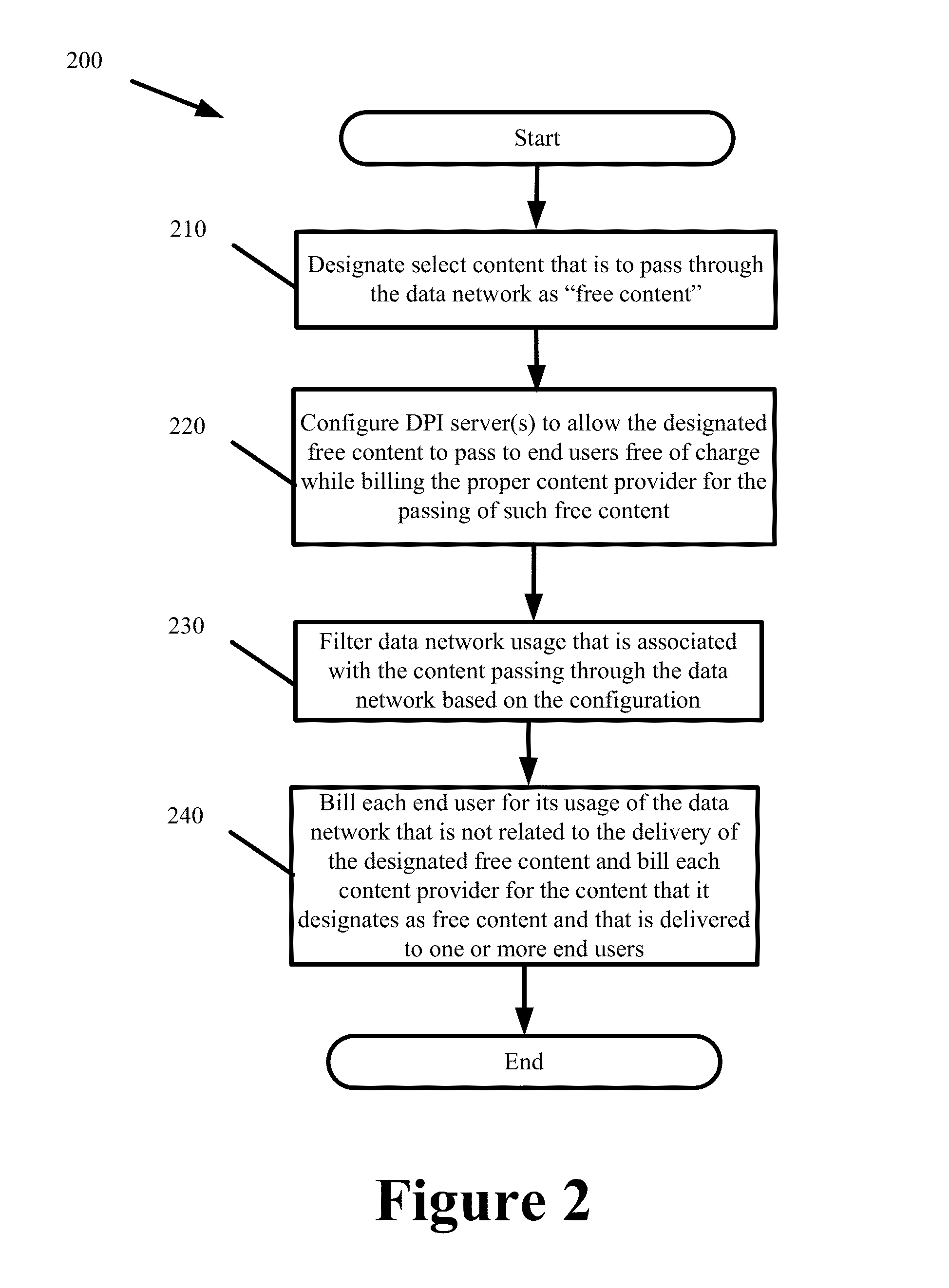
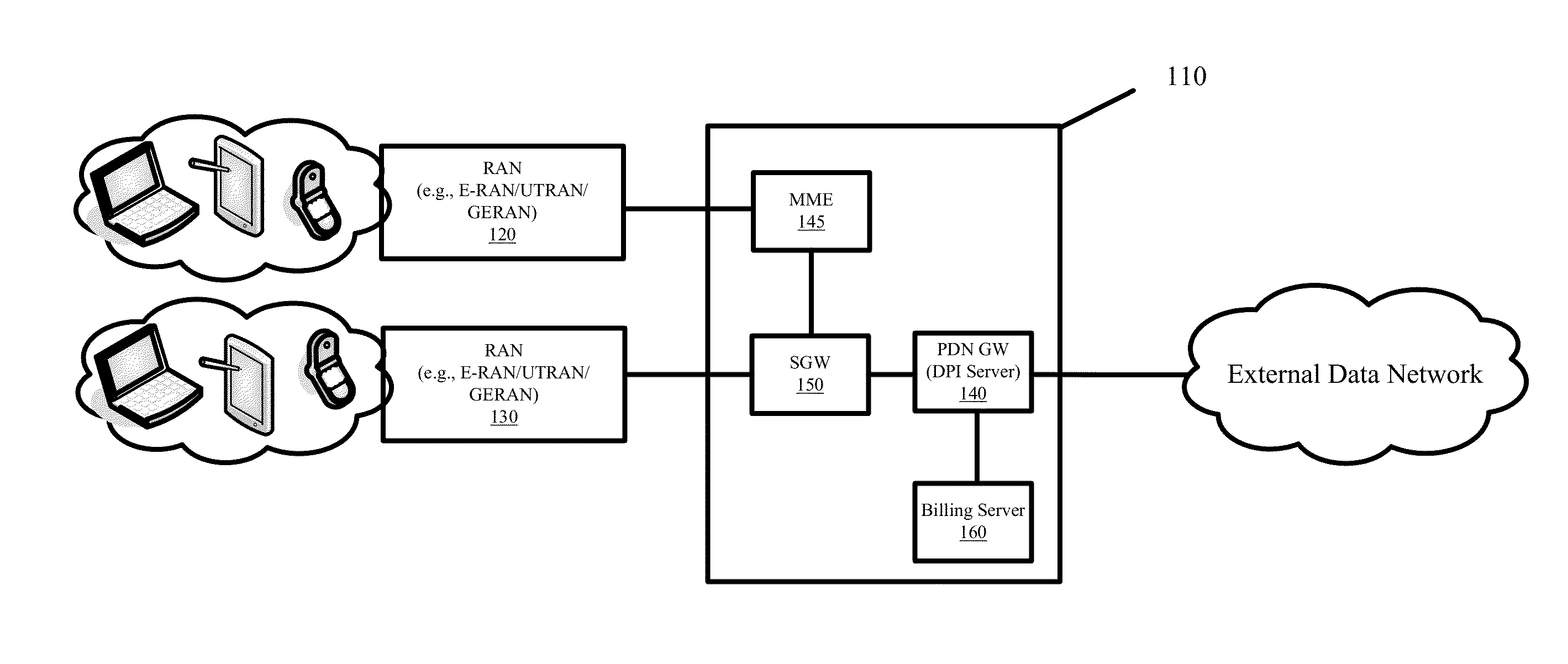
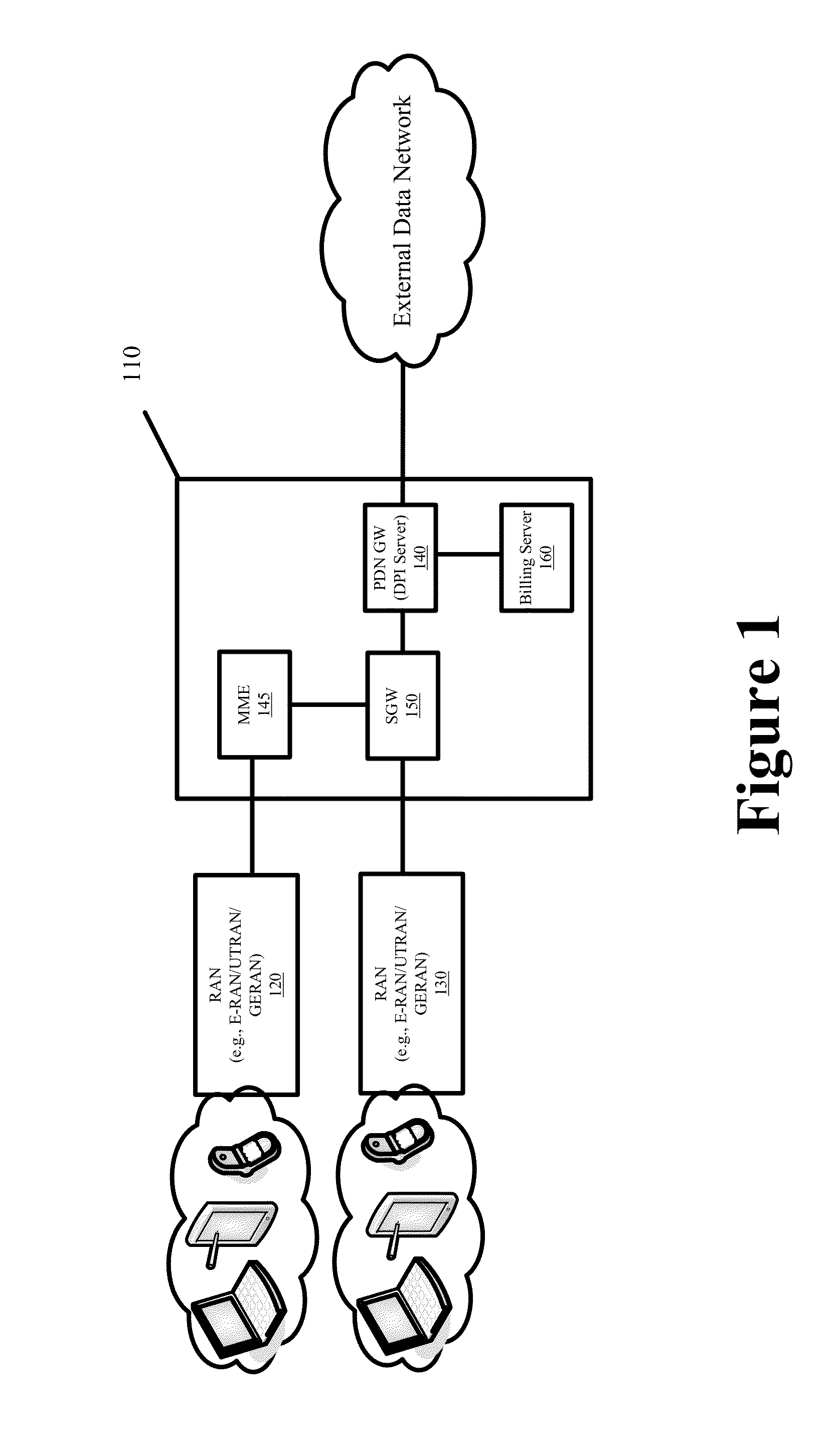
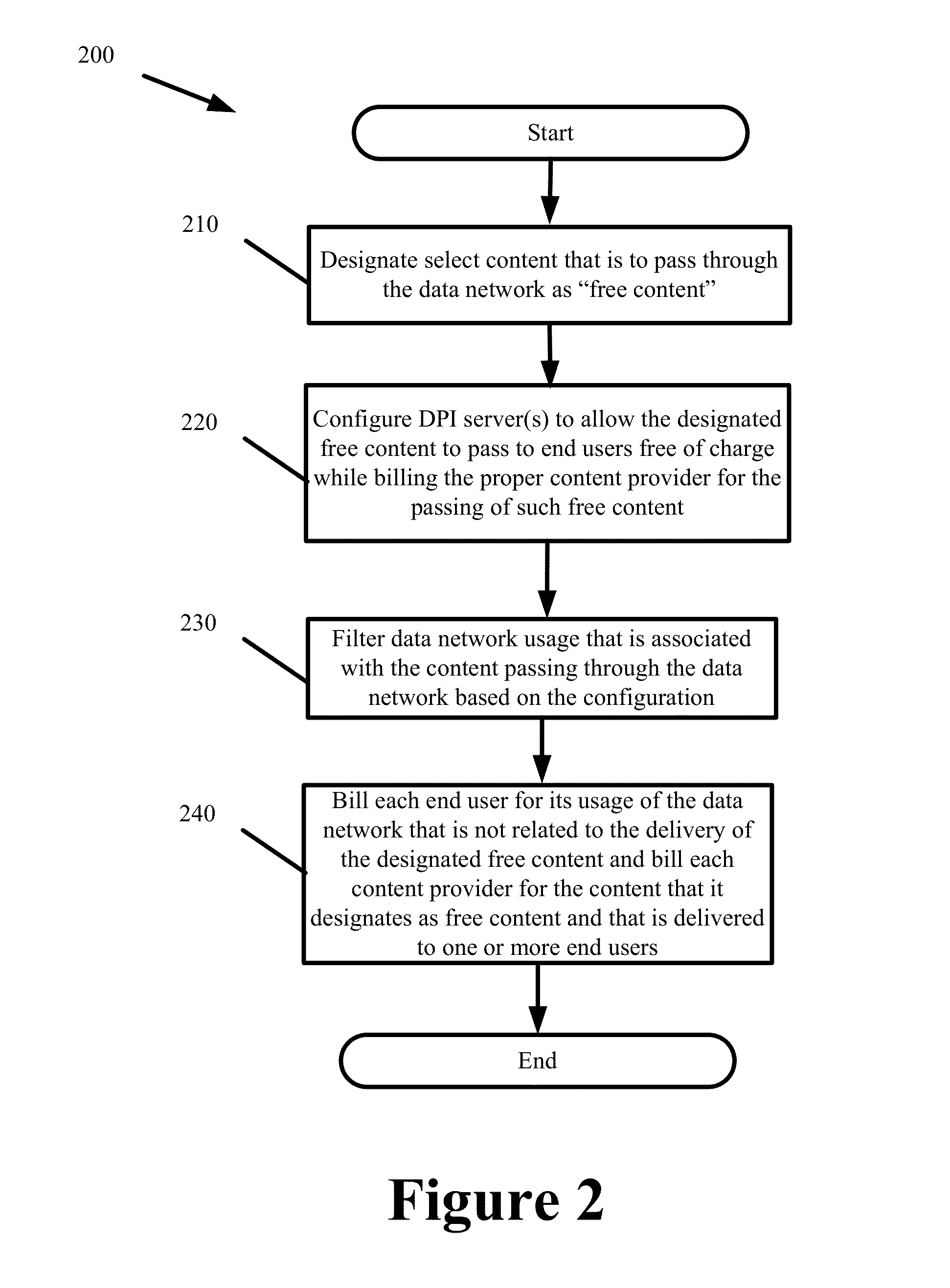
Systems and Methods for Billing Content Providers for Designated Content Delivered Over a Data Network
ActiveUS20130238472A1Generate revenueWithout costComplete banking machinesAdvertisementsEnd userBilling system
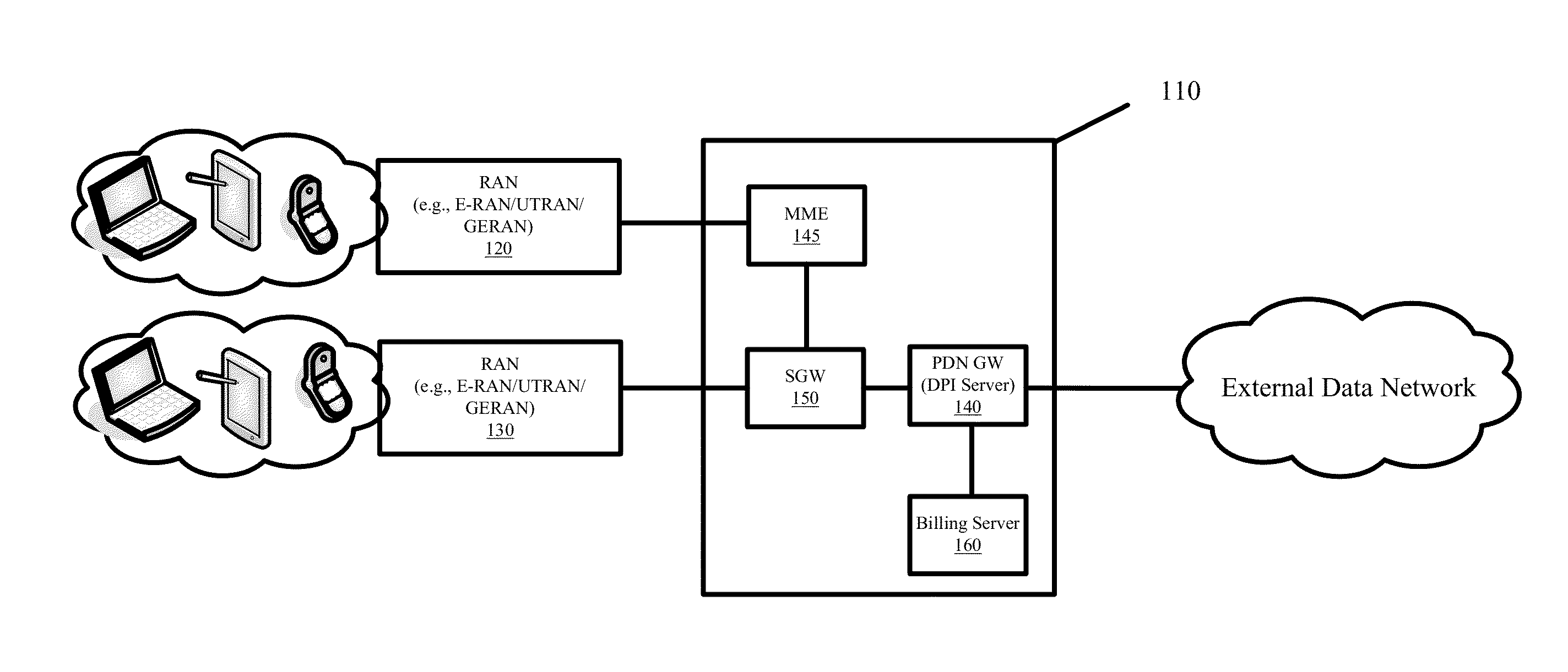
Some embodiments provide multi-tenant billing systems and methods whereby data network usage fees that are associated with delivering select content of different content providers over a data network are passed to the content provider that originates or is the source for that select content instead of the end users that request and receive the select content. A deep packet inspection server or a billing server may be configured with a list of identifiers to distinguish between the network usage that is related to the delivery of the designated free content from the network usage that is not related to the delivery of the designated free content. The network usage can be distinguished by filtering or processing usage logs that track the network usage using the configured list of identifiers. Such filtering or processing can be done in real-time or in a delayed manner in a standalone or integrated system.
Owner:EDGIO INC
Method and apparatus for real-time multi-dimensional reporting and analyzing of data on application level activity and other user information on a mobile data network
A method and apparatus for real-time, multi-dimensional reporting and analyzing of data on application level activity and other user information on a mobile data network. A report manager communicates with a data manager to develop and test real-time reports about aggregate and user-level network usage. The data manager provides a database of non-aggregate, user-specific event data and a set of tables specifying combinations of monitored variables satisfying a set of defined reports. The report manager comprises a report generation module, which receives operator instructions for aggregate usage information. The report module determines whether the requested information can be satisfied by combinations of monitored aggregate variables, or whether it must be retrieved from a non-aggregate, user-specific, event data database. Furthermore, the report module is responsive to operator instructions to add a test report to the set of defined real-time reports.
Owner:RIBBON COMM SECURITIES CORP
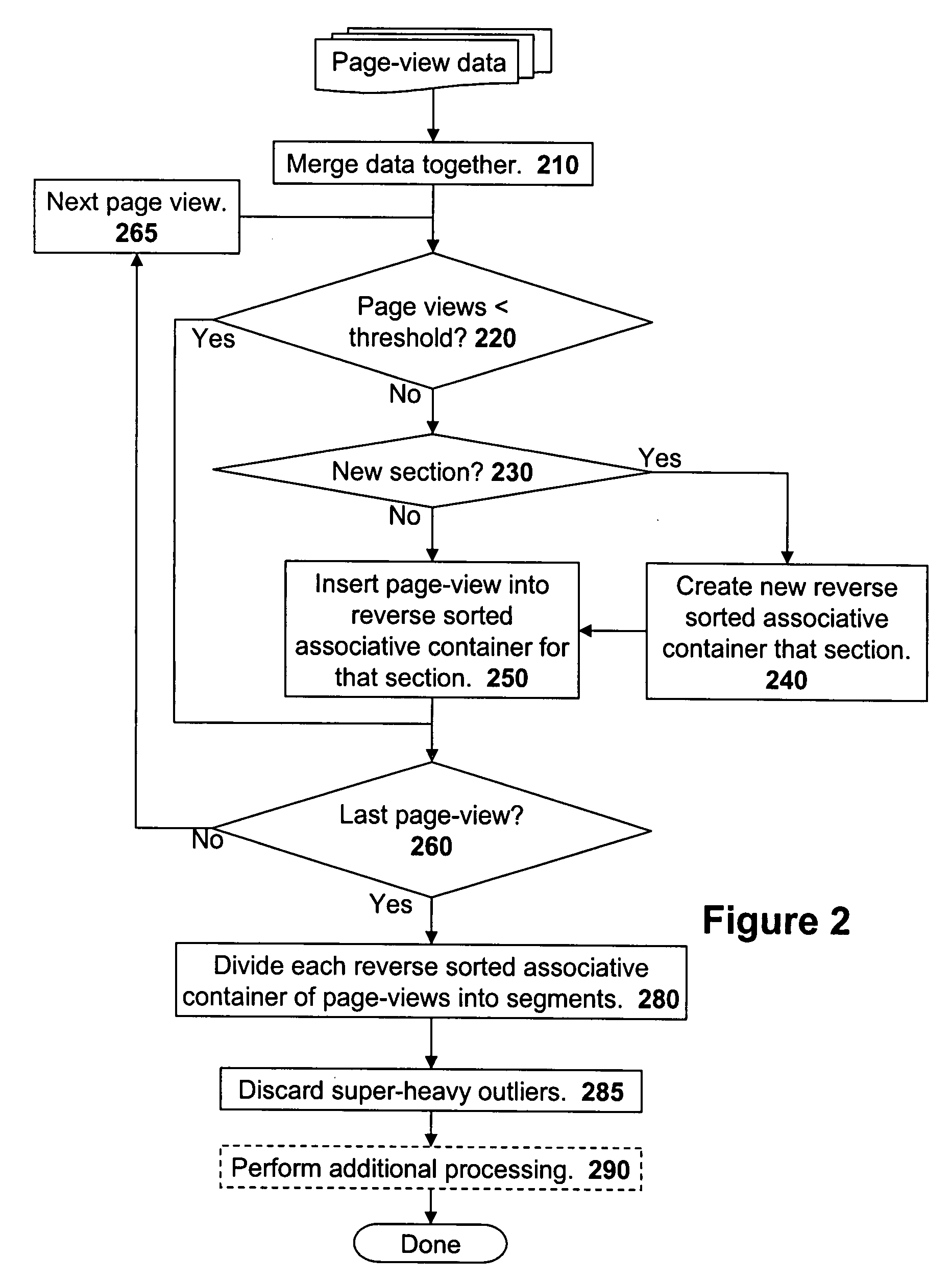
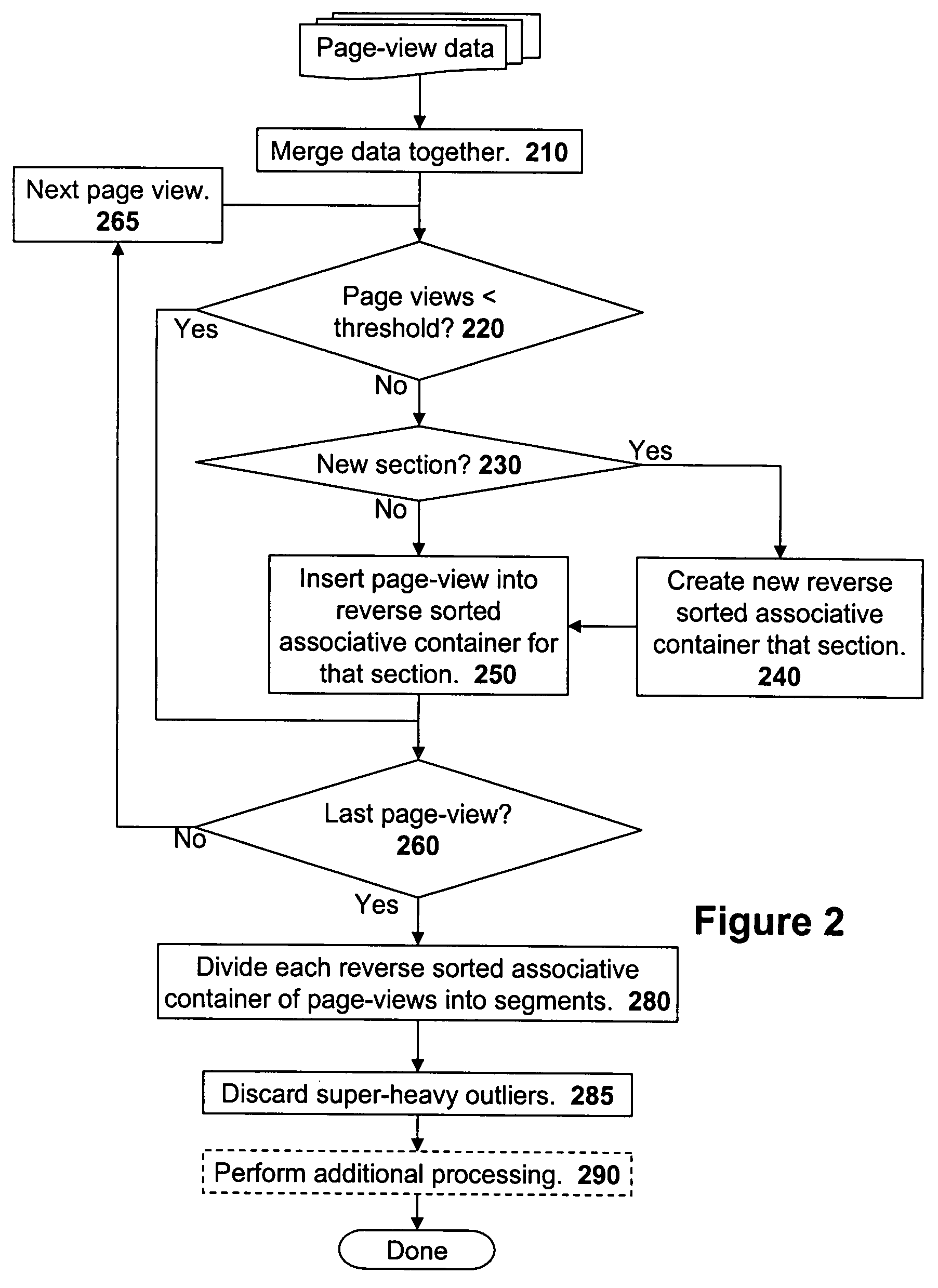
Methods of processing and segmenting web usage information
A massive amount of information is collected when tracking statistics such as web site usage data. To simplify the analysis of such data, it is advantageous to process and segment the web site usage data. One proposed method of segmenting the data is to create a reverse sorted associative container for each different web section of a web site. Page-views, c, sessions, and other web viewing metrics may be used as keys in the reverse sorted associative container and web viewer identifiers are used as values associated with the page-view value keys. After creating the reverse sorted associative containers, each reverse sorted associative container is segmented on a percentile basis.
Owner:R2 SOLUTIONS
Method and system for tracking a user flow of web pages of a web site to enable efficient updating of the hyperlinks of the web site
InactiveUS6954901B1Easy maintenanceSimple processWeb data navigationSpecial data processing applicationsWeb siteHyperlink
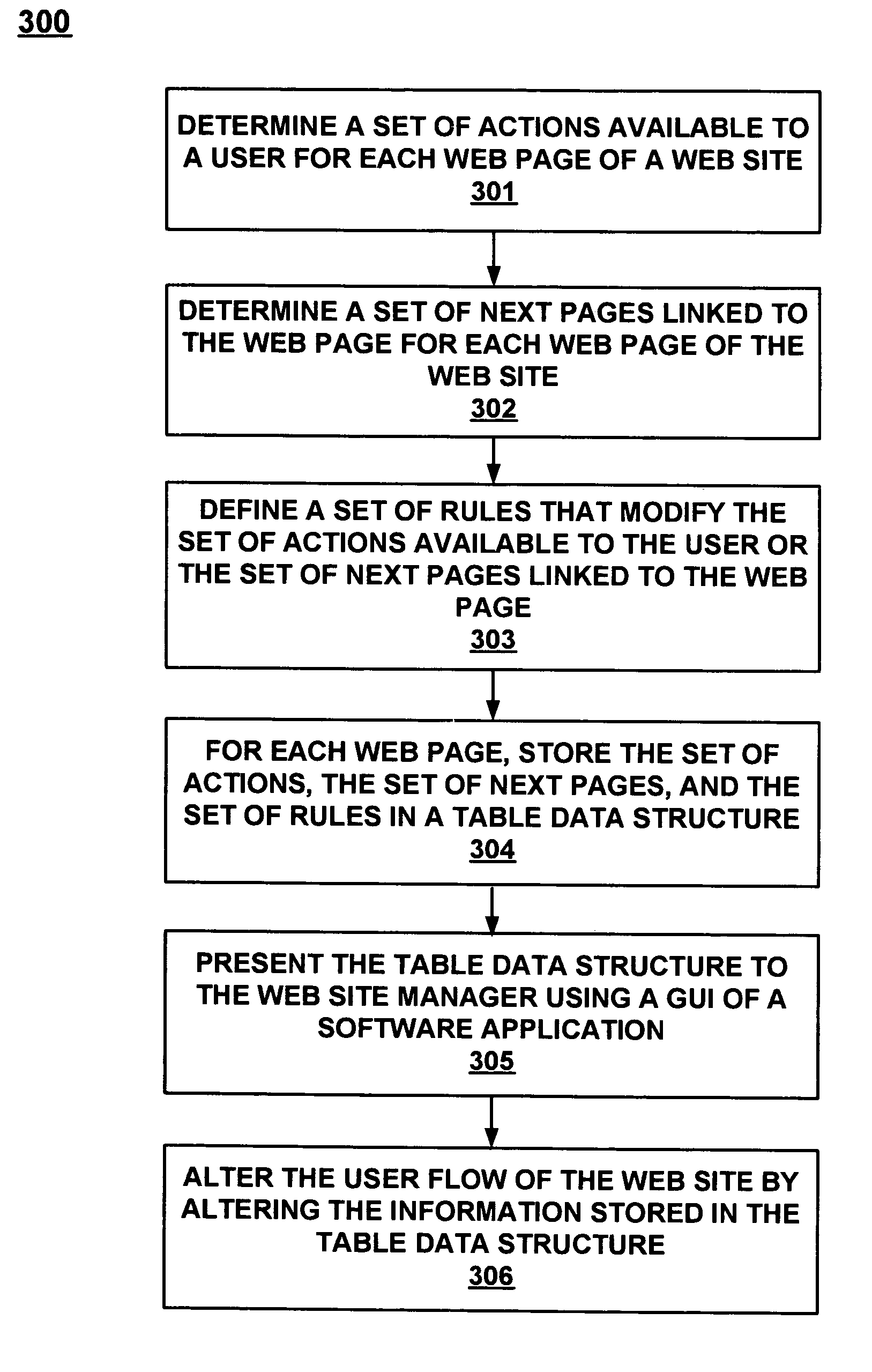
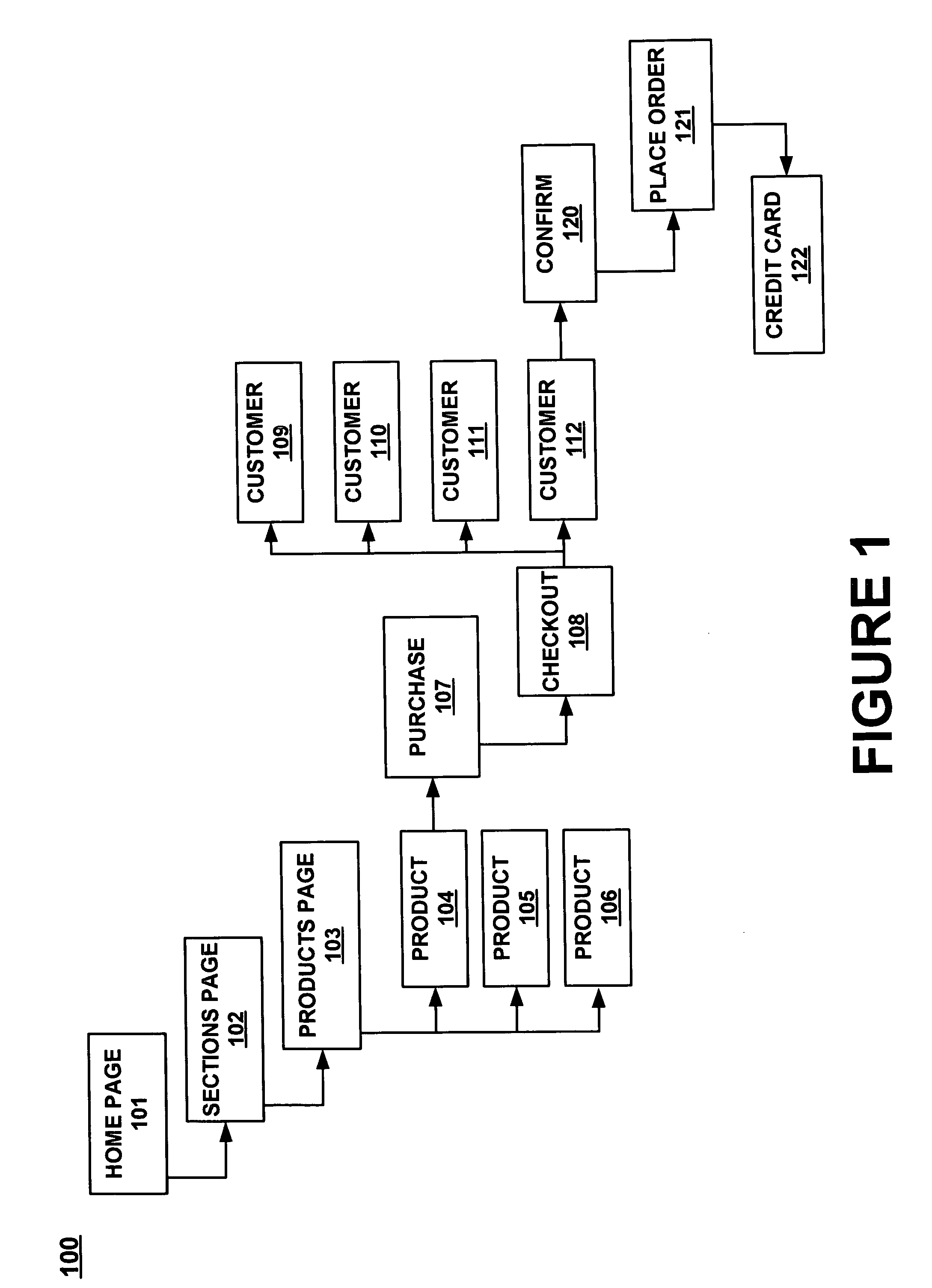
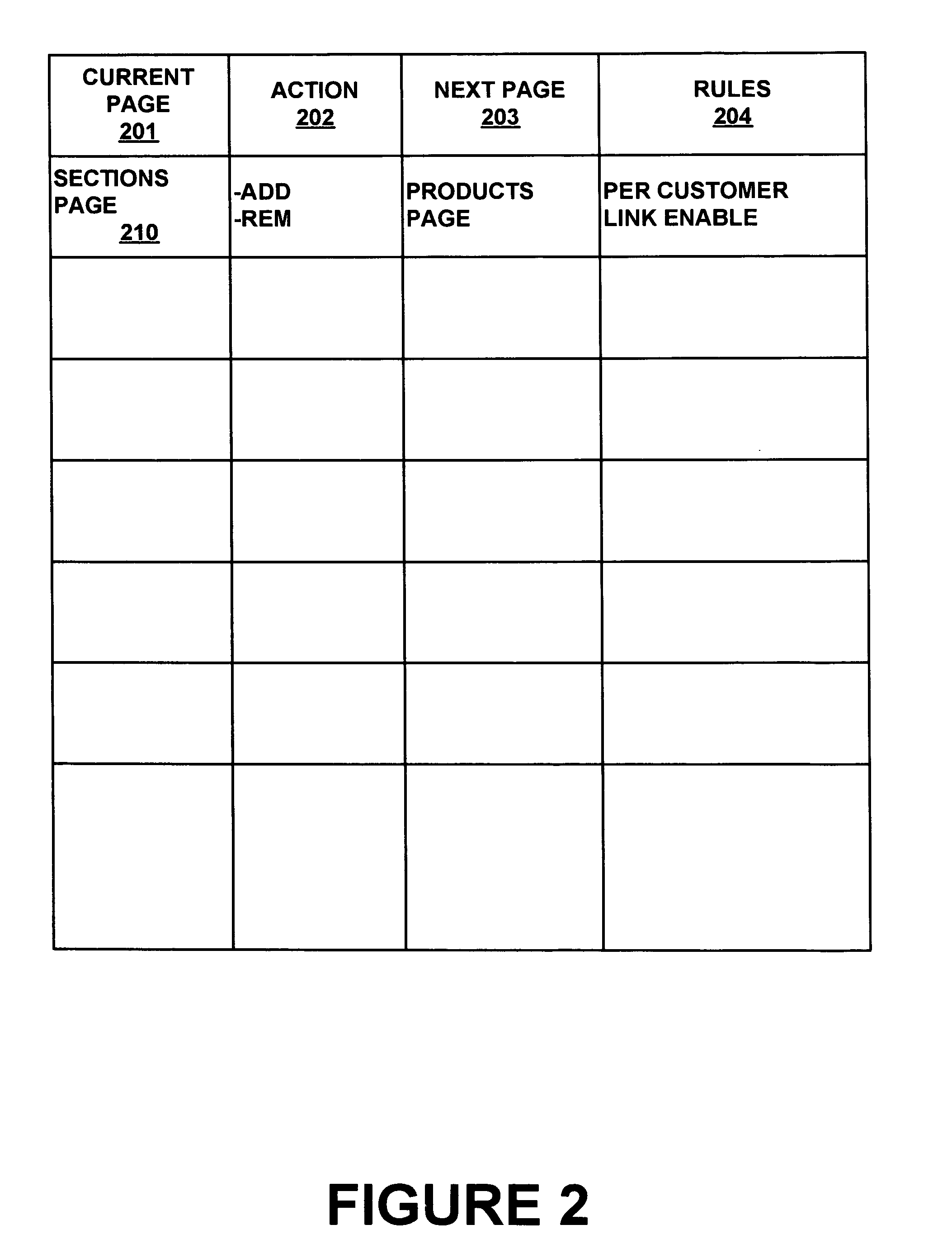
A method for tracking a user flow of Web pages of a Web site to enable efficient updating of the hyperlinks of the Web site. A Web page is accessed out of a plurality of Web pages of a Web site. A set of actions available to a user are determined for the Web page. A set of the next pages linked to the Web page are determined for the Web page. A set of rules are defined that modify the set of actions available to the user or the set of next pages linked to the Web page in accordance with an identity of the user. The set of actions, the set of next pages, and the set of rules are stored in a table data structure for the Web page to track a user flow of the Web page. The table data structure enables the user flow of the Web page to be changed by altering the corresponding set of rules in the table data structure for the Web page. Similarly, the user flow can be changed by altering the set of actions available to the user, or by altering the set of next pages linked to the Web page in the table data structure for the Web page. A plurality of table data structures can be generated for each of the plurality of Web pages of the Web site, and the table data structures can be stored in a matrix to track a user flow of the entire Web site.
Owner:ORACLE INT CORP
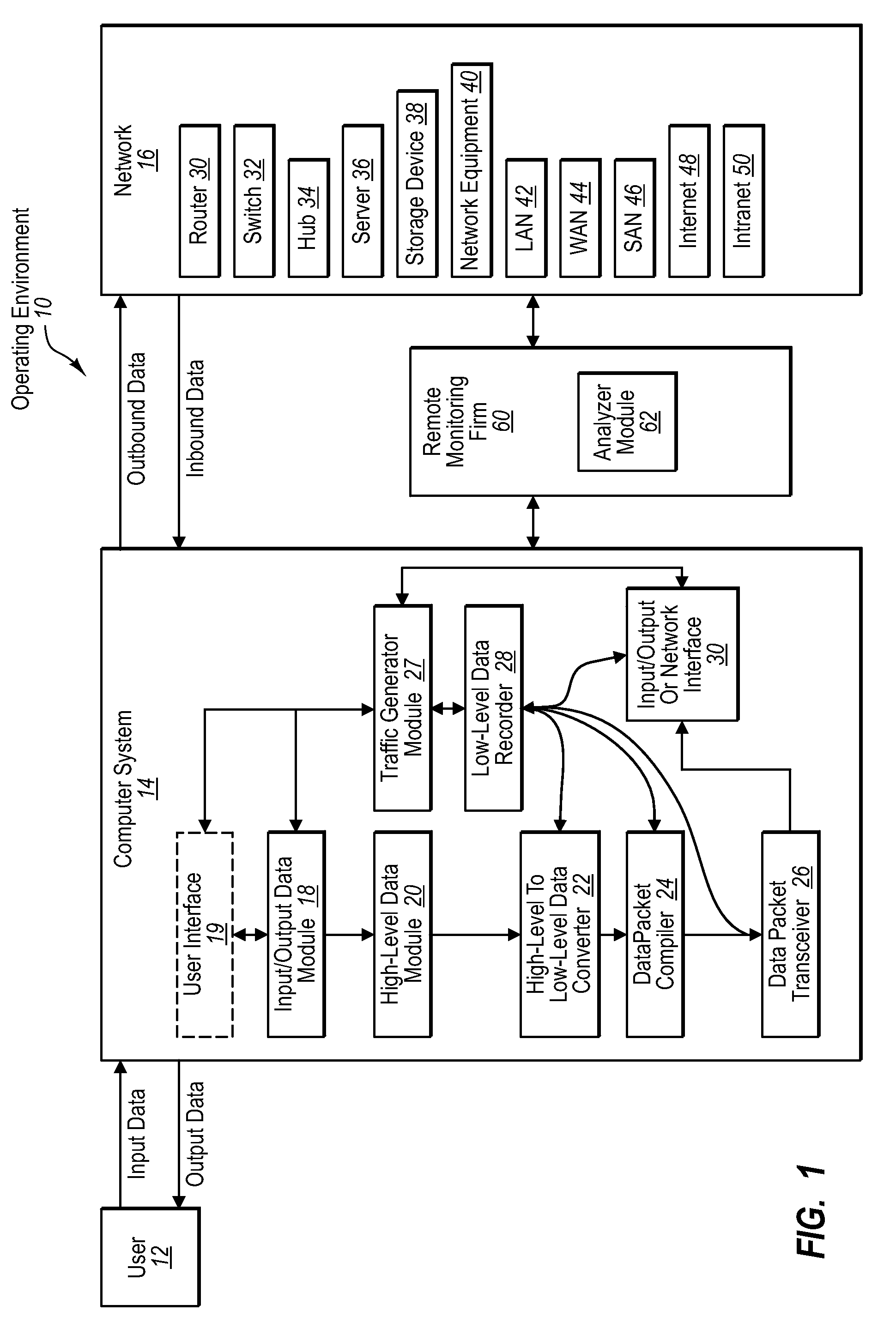
Traffic generator program
InactiveUS20070213966A1Improve of of componentImprove network performanceAnalogue computers for electric apparatusTransmissionTraffic capacityVirtual user
Systems and methods for a traffic generator for use in a network. A computer program product such as a plug in for a browser captures data that is sent over a network. The plug in does not need to understand or capture keyboard or mouse input. Rather, the plug in captures low level network data that is generated in response to high level user input. The captured data can be used to reflect real network usage during the testing of networks and network equipment. The traffic can also be modified to reflect multiple virtual users and test the network or network equipment accordingly.
Owner:FINISAR
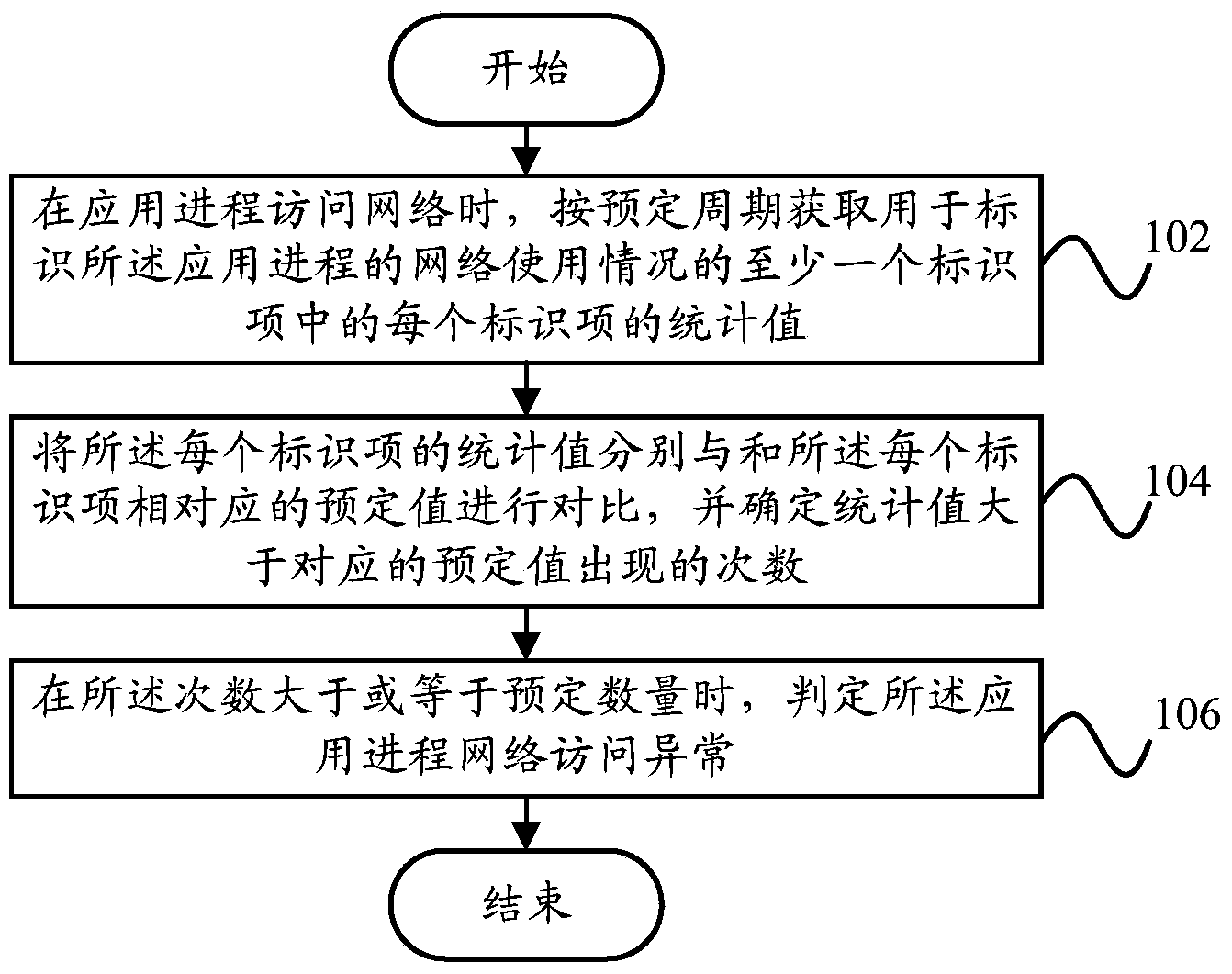
Network access anomaly identification method and network access anomaly identification device
The invention provides a network access anomaly identification method and a network access anomaly identification device. The network access anomaly identification method comprises steps: when an application process accesses the network, the statistical value of each identifier in at least one identifier used for identifying the network usage of the application process is acquired according to the predetermined cycle; the statistical value of each identifier is compared with the predetermined value corresponding to each identifier and the times of situations where the statistical value exceeds the corresponding predetermined value is determined; when the times is larger than or equal to the predetermined number, the application process network access anomaly can be judged. Through the technical scheme of the invention, the application process with abnormal flow consumption can be timely found out, the network connection of the application process is disconnected, a role of protection is thus achieved before the flow exceeds the standard, and the application process normally used by a user is not disturbed.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and system for identifying targeted data on a web page
A method and system is provided that in a fully automated manner crawls web sites and identifies specific types of web pages, then extracts targeted data from those web pages. One or more text nodes containing product-related information on a first web page are first identified, and the locations of those test nodes are described using one or more vectors. The vectors are then analyzed to identify one or more patterns and to generate a model from those patterns that discriminates between text nodes that contain product-related information and text nodes that do not contain product-related information on a second web page. The model can then be used to crawl web sites to identify and extract targeted data, or the model can be installed on a user's computer to identify and extract targeted information from web sites as the user is browsing.
Owner:PERRY BRADLEY JOHN +2
Devices and methods for searching a network of distributed content servers
InactiveUS20080228776A1Digital data information retrievalSpecial data processing applicationsUser deviceWeb browser
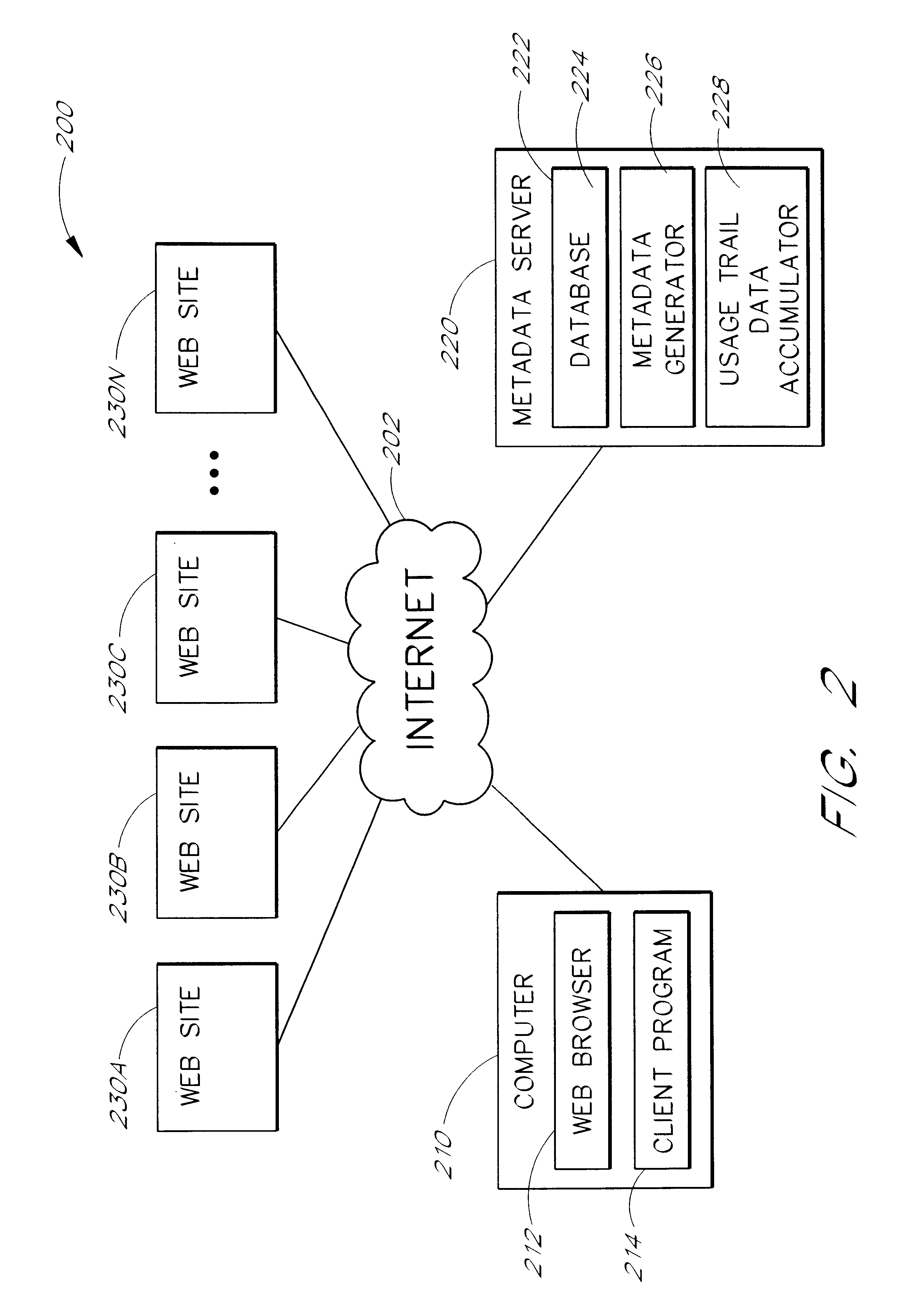
A client user device for communicating with a web of distributed content servers includes a web browser and a web-usage monitor. The web browser is configured to receive web pages of content. The web usage monitor is configured to interface with the web browser and determine web-usage information for content received by the web browser. The web-usage monitor is configured to provide the web-usage information to a search provider.
Owner:EARTHLINK
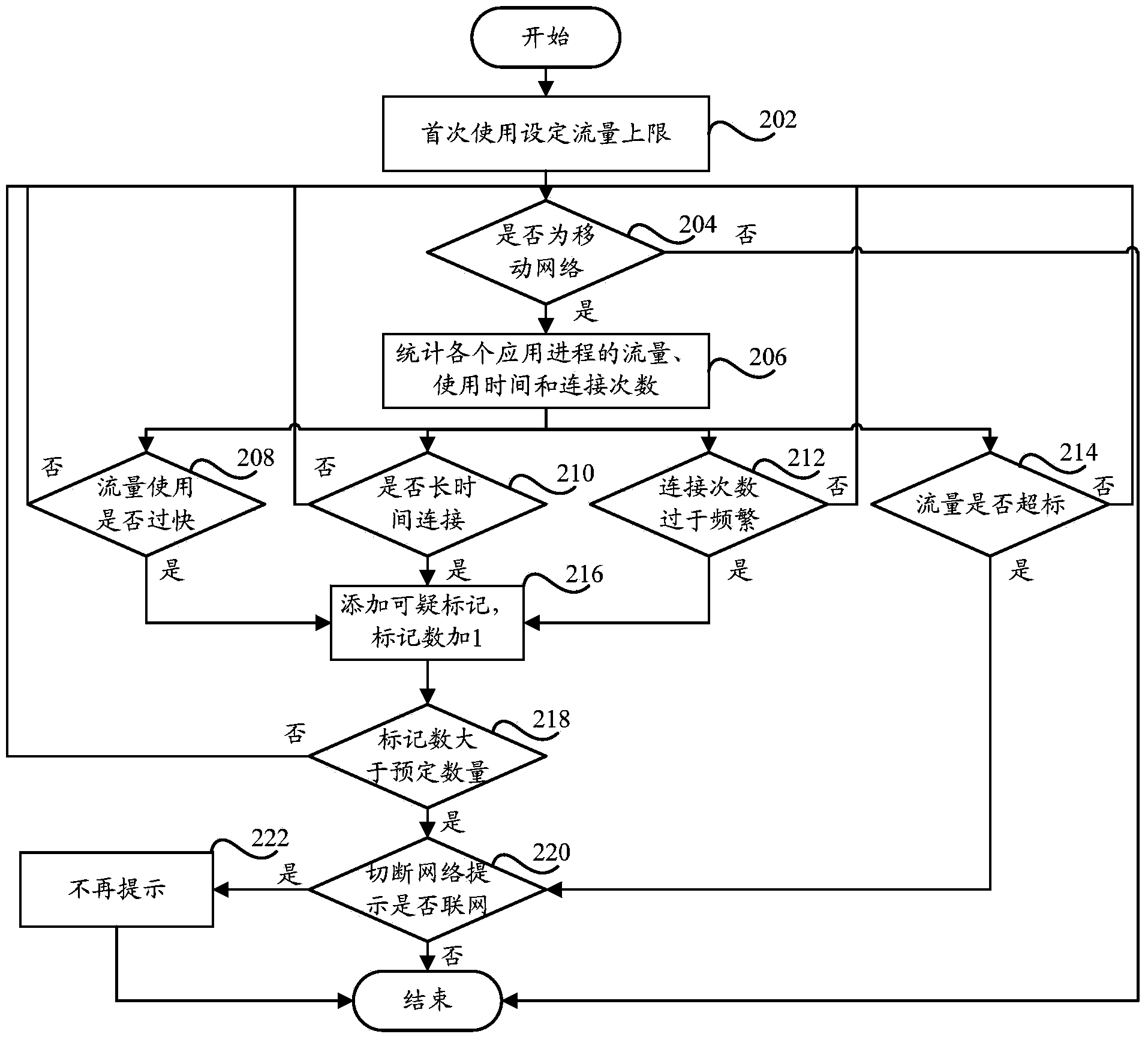
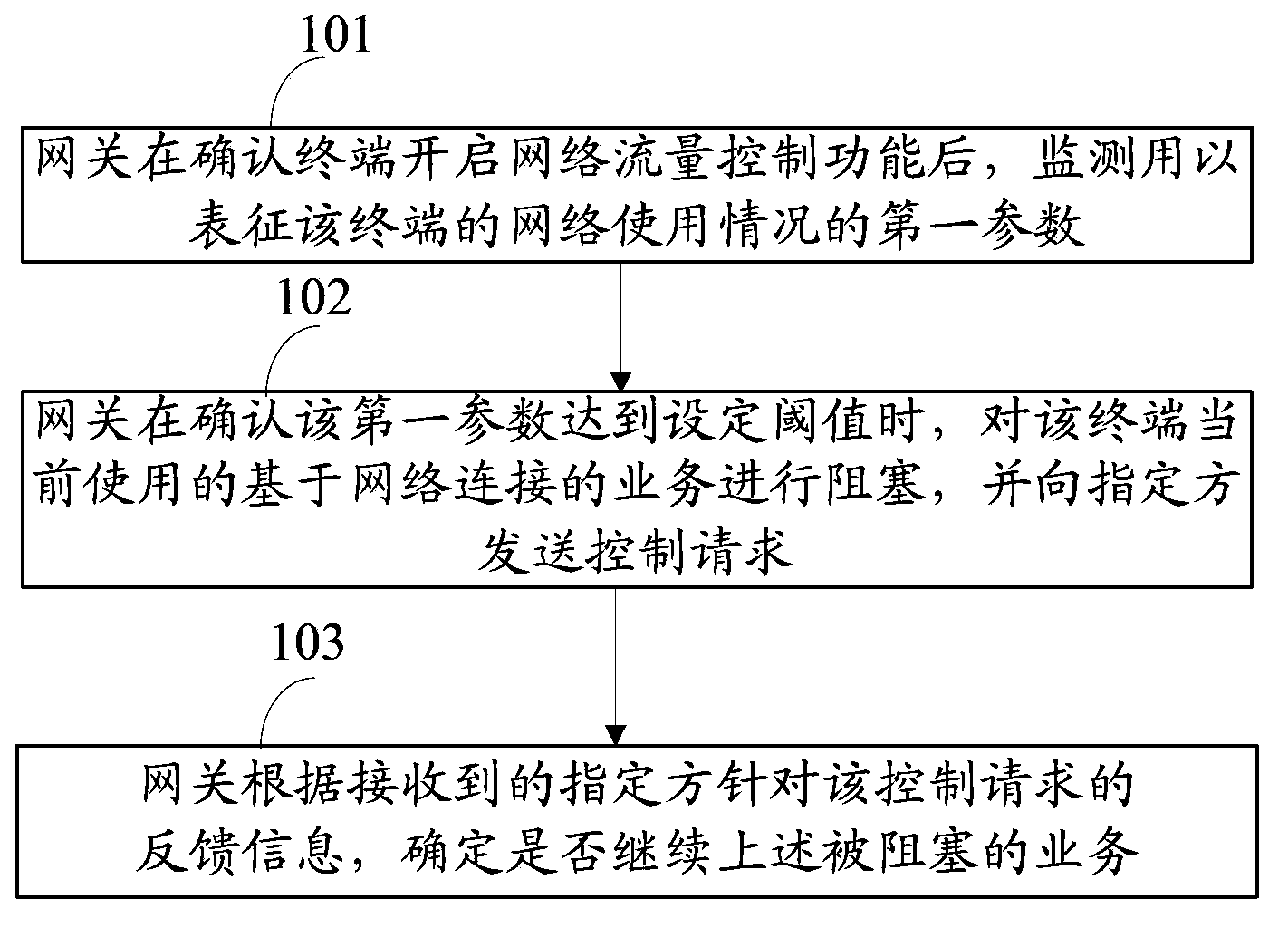
Network flow control method and device
An embodiment of the invention discloses a network flow control method and device. The method includes monitoring a first parameter used for representing the network use condition of a terminal after determining that the terminal starts a network flow control function; blocking business currently used by the terminal and based on network connection when determining that the first parameter reaches a set threshold and transmitting a control request to an assigned party; determining whether to continue the business aiming at feedback information of the control request according to the received assigned policy. The method and device is used for solving the problem in the prior art that the network using behavior of the terminal cannot be controlled accurately due to the fact that the business cannot be suspended before network flow generation or in the network flow generation process.
Owner:CHINA MOBILE GROUP SHANDONG
Use of web usage trail data to identify relationships between browsable items
InactiveUS20040205516A1Digital computer detailsSpecial data processing applicationsWeb browserUniform resource locator
Owner:ALEXA
Systems and Methods for Billing Content Providers for Designated Content Delivered Over a Data Network
ActiveUS20130238473A1Generate revenueWithout costComplete banking machinesTelephonic communicationComputer scienceEnd user
Some embodiments provide multi-tenant billing systems and methods whereby data network usage fees that are associated with delivering select content of different content providers over a data network are passed to the content provider that originates or is the source for that select content instead of the end users that request and receive the select content. A deep packet inspection server or a billing server may be configured with a list of identifiers to distinguish between the network usage that is related to the delivery of the designated free content from the network usage that is not related to the delivery of the designated free content. The network usage can be distinguished by filtering or processing usage logs that track the network usage using the configured list of identifiers. Such filtering or processing can be done in real-time or in a delayed manner in a standalone or integrated system.
Owner:EDGIO INC
Wireless network optimization
ActiveUS20180063002A1Data processing applicationsDetection of traffic movementImpact areaWireless network
Methods and apparatuses are provided for optimizing a wireless network. A description of a traffic incident is received. An impact area is generated from the description. A geographic polygon is generated based on the impact area. The network usage of the geographic polygon is determined. A message including the network usage for the geographic polygon may be transmitted to a mobile network operator.
Owner:HERE GLOBAL BV
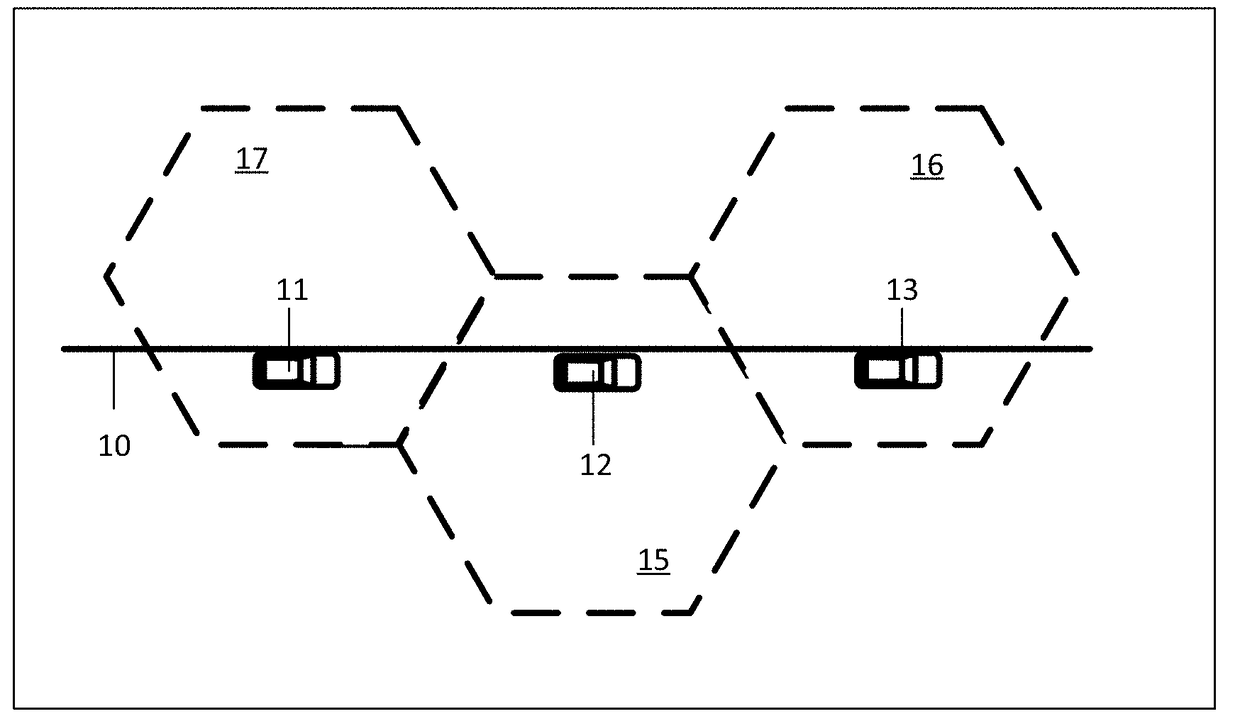
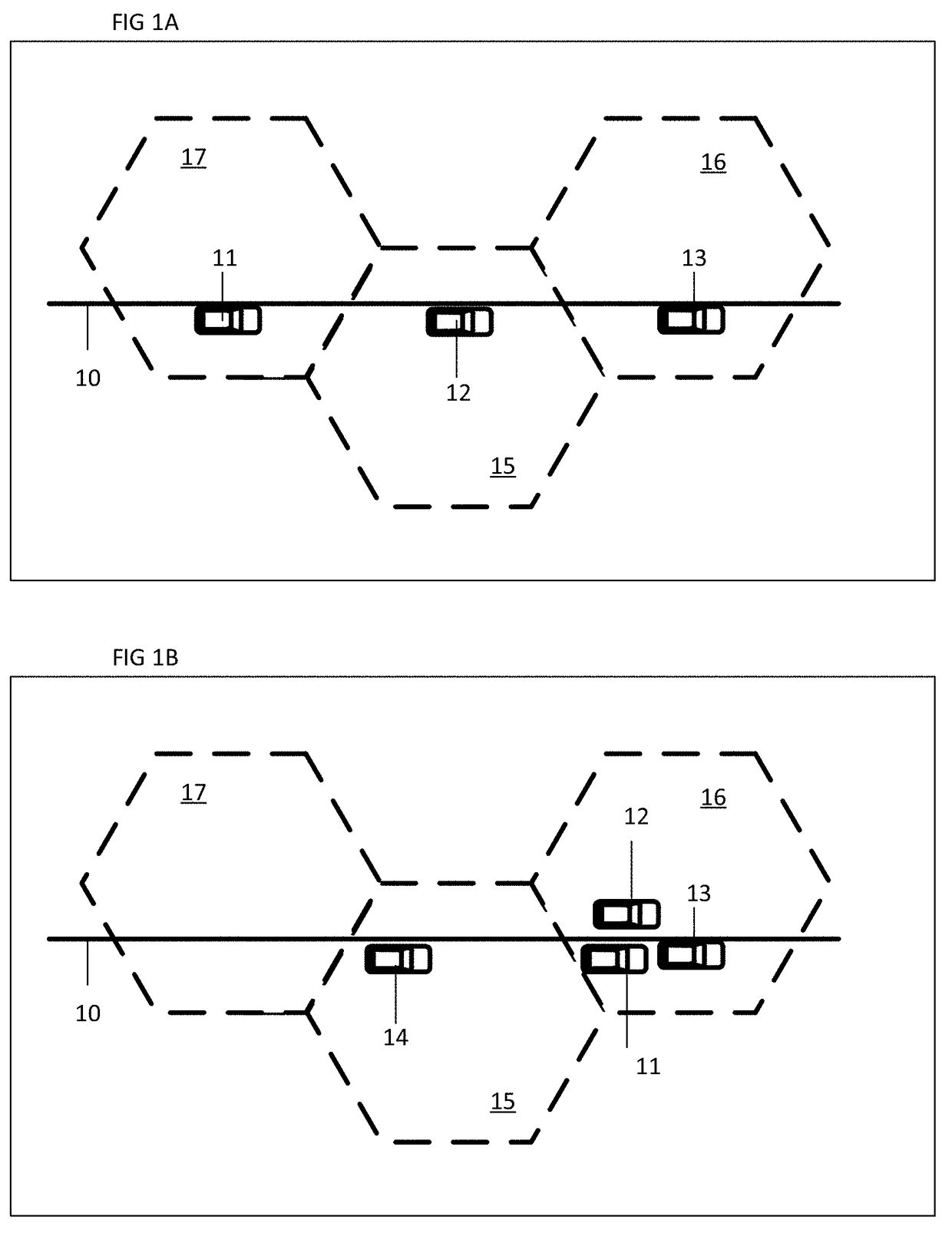
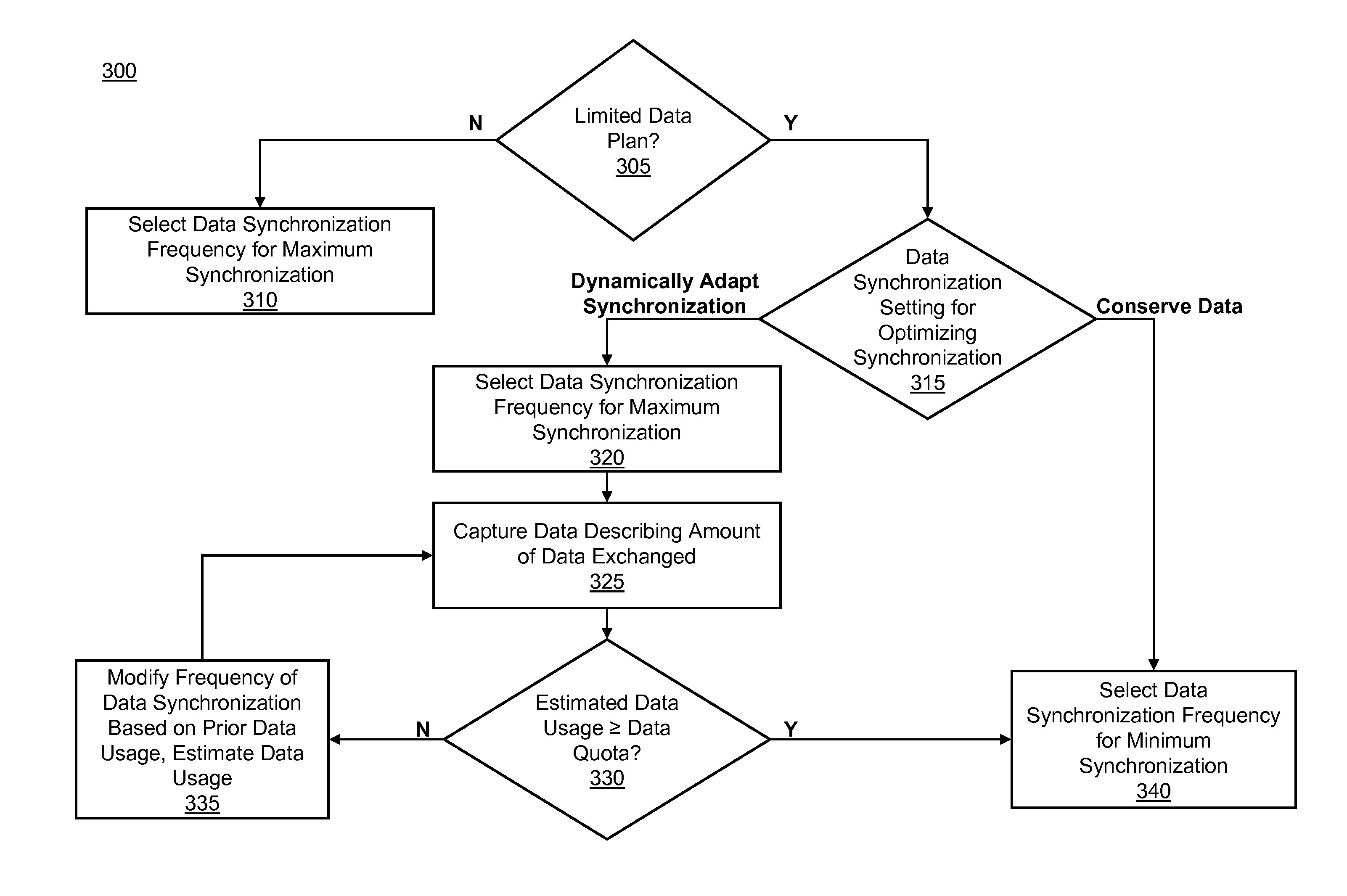
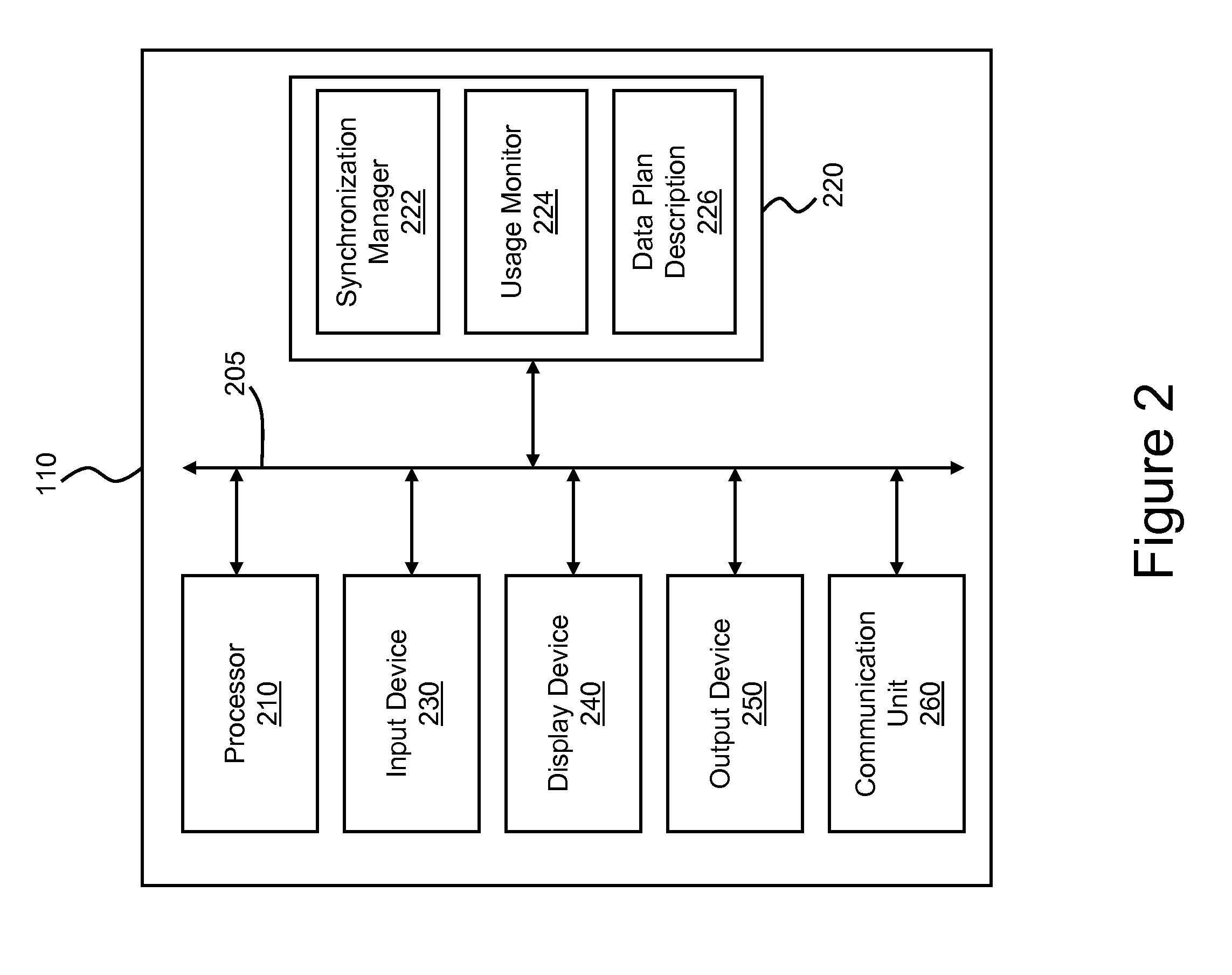
Adaptive data synchronization based on data plan or network usage
ActiveUS20130151658A1Multiple digital computer combinationsTransmissionData synchronizationProgram planning
A method and apparatus for modifying data synchronization of a portable computing device responsive to a data plan associated with an account associated with the portable computing device are disclosed. If the data plan specifies a data quota identifying a maximum amount of data for communication by the portable computing device, a data synchronization setting determines whether to minimize the frequency of synchronization between the portable computing device and a server or to dynamically modify the frequency of synchronization based on data usage. If data synchronization is dynamically modified, the data synchronization frequency is modified based on an estimated data usage of the portable computing device over a time interval. The data synchronization frequency is modified based on the difference between estimated data usage and the data quota and is reduced if the estimated data usage equals or exceeds the data quota.
Owner:GOOGLE TECH HLDG LLC
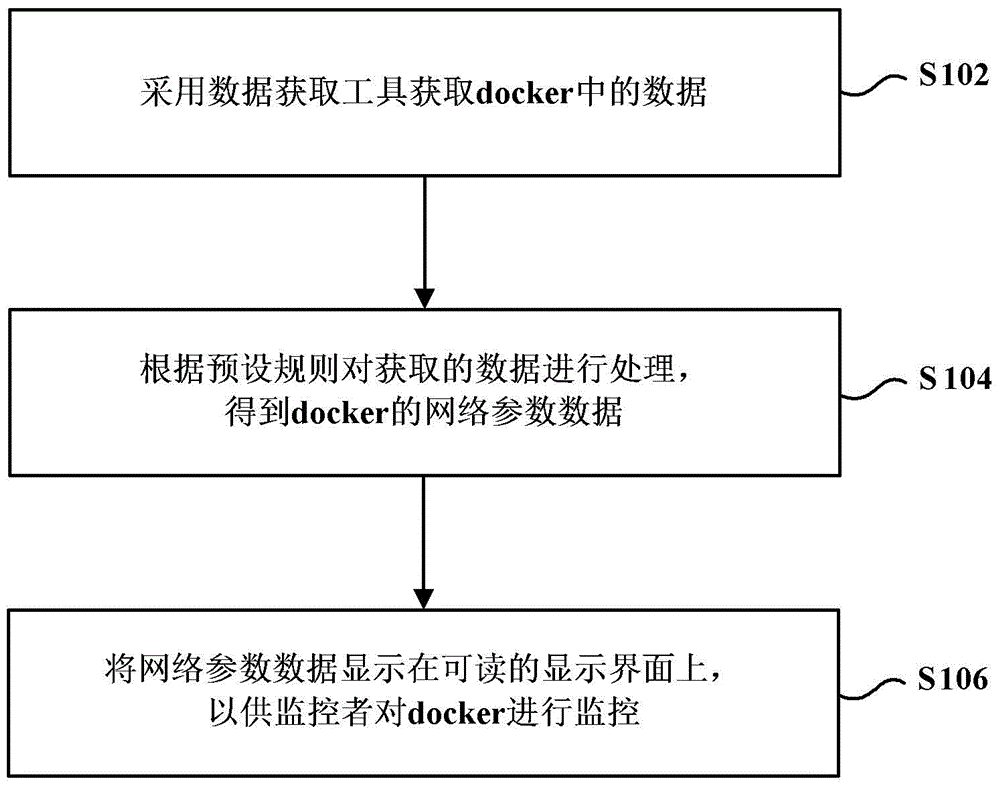
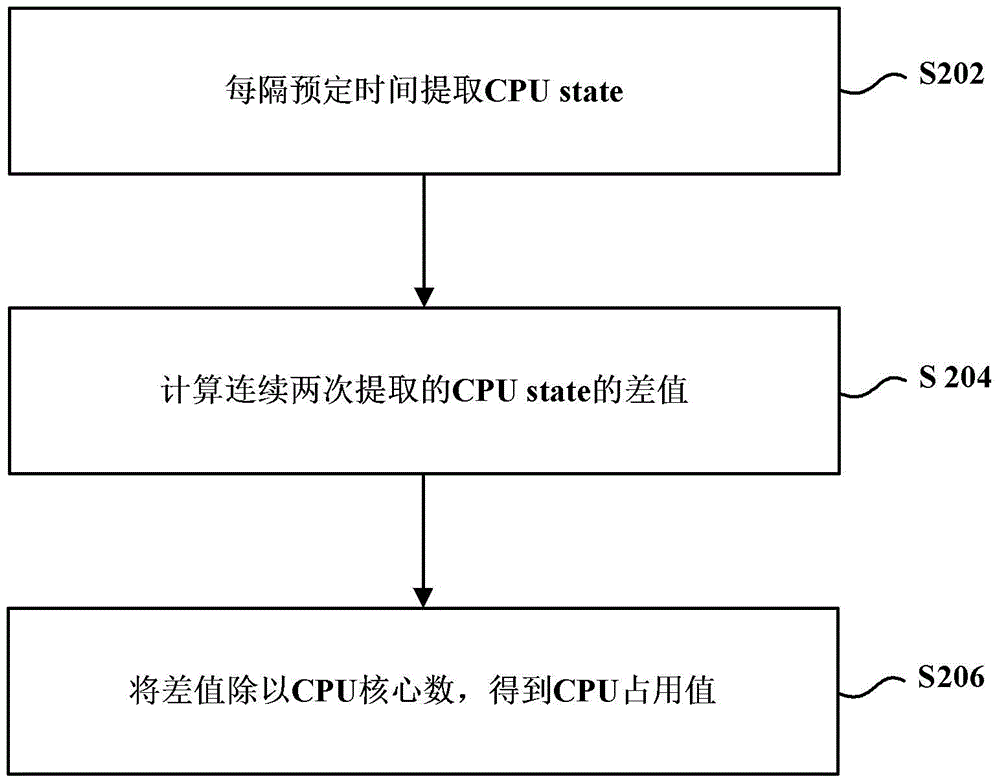
Monitoring method and client for docker
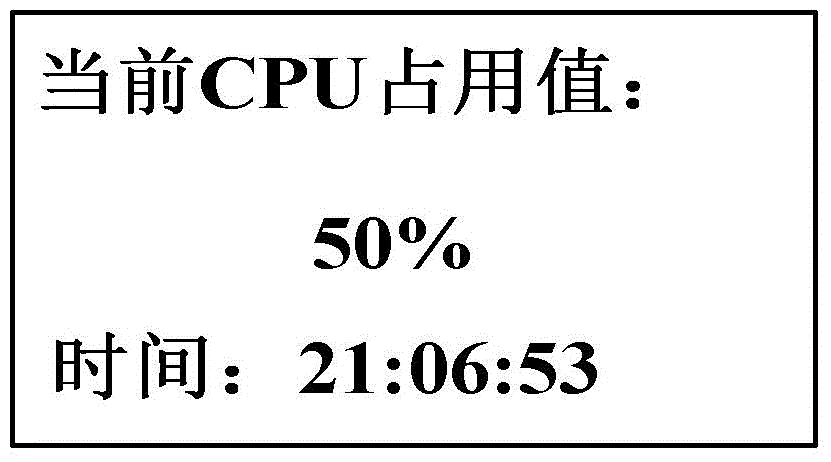
InactiveCN105429813AReasonable allocation and high efficiencyEfficient allocationData switching networksWeb usageClient-side
The invention provides a monitoring method and a client for a docker. The method comprises the following steps: obtaining data in a docker by means of a data obtaining tool, wherein the data at least includes a central processing unit application value CPU state and / or the number of CPU cores; processing the data according to preset rules and obtaining network parameter data of the docker; and displaying the network parameter data on a readable display interface so that the docker is monitored by a monitoring worker. According to the embodiment, the beneficial effects of the invention are that network parameter data of a docker can be obtained and displayed, so a monitoring worker can directly know the situation about how the docker is utilized, and therefore network usage resources can be distributed in a more highly efficient and more reasonable manner.
Owner:BEIJING QIHOO TECH CO LTD +1
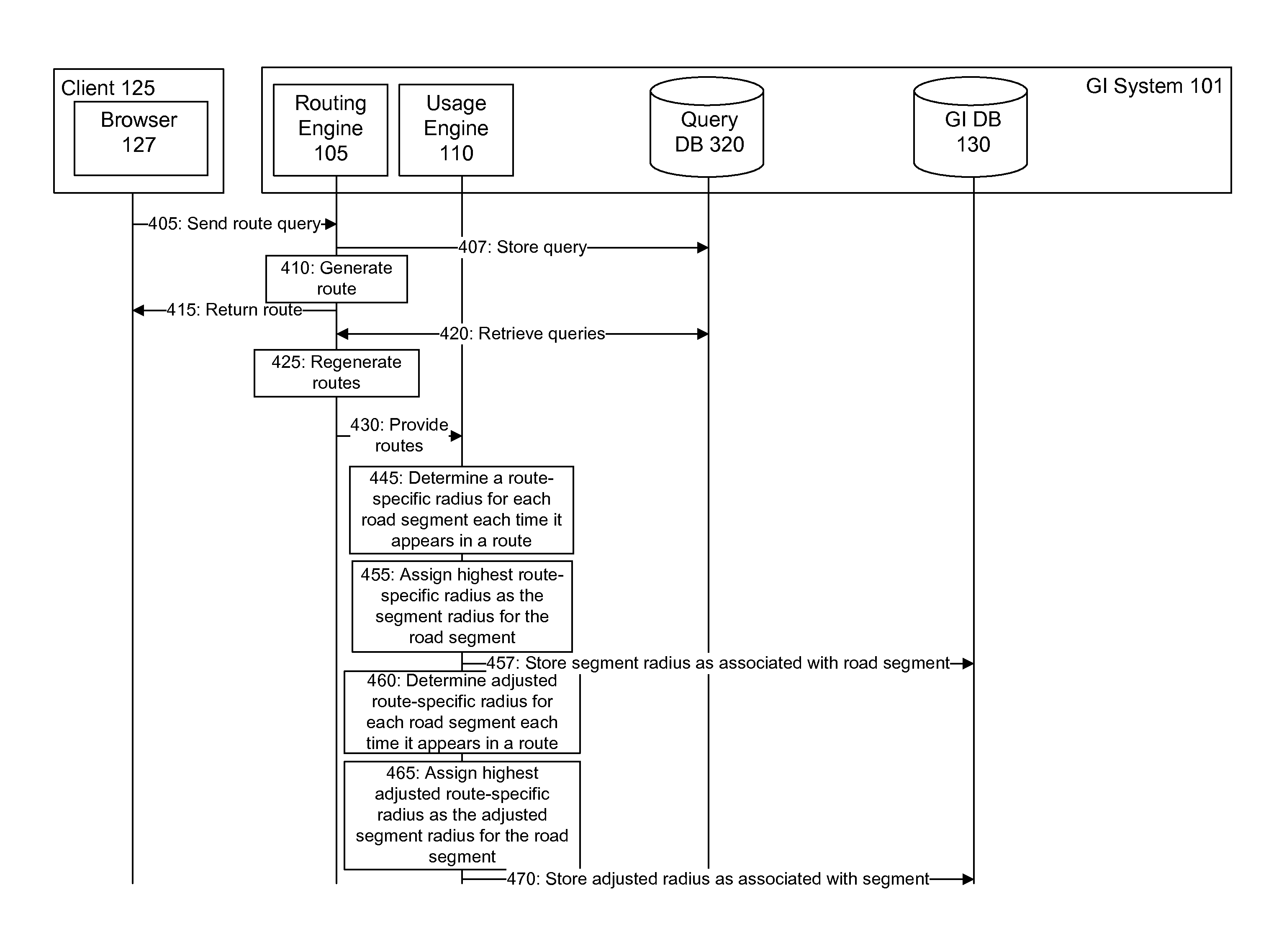
User queries to model road network usage
ActiveUS8825403B1Instruments for road network navigationRoad vehicles traffic controlGraphicsRoad networks
A system and method determines a plurality of scores for a road segment that are related to the total distance traveled when drivers traverse that road segment. The scores are displayed graphically to illustrate the usage of road segments. The scores are also used to determine which road segments to display on a map when determining which roads to display at a given zoom level for a map.
Owner:GOOGLE LLC
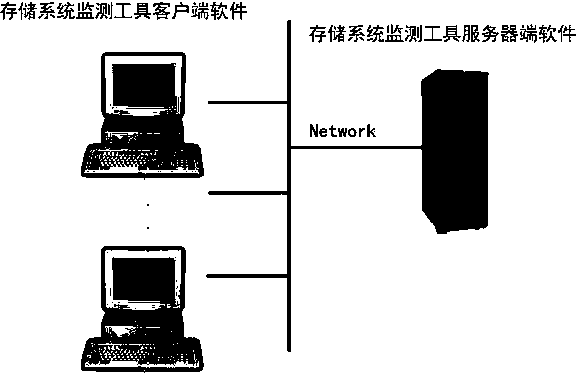
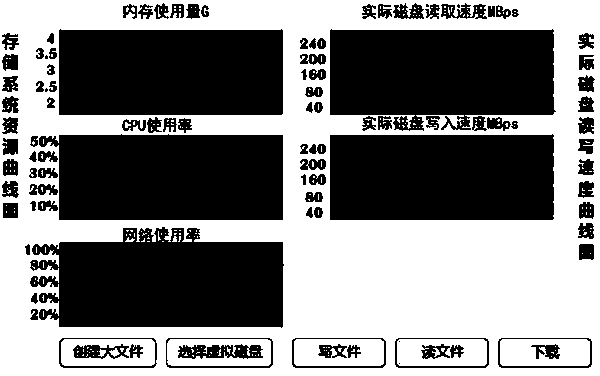
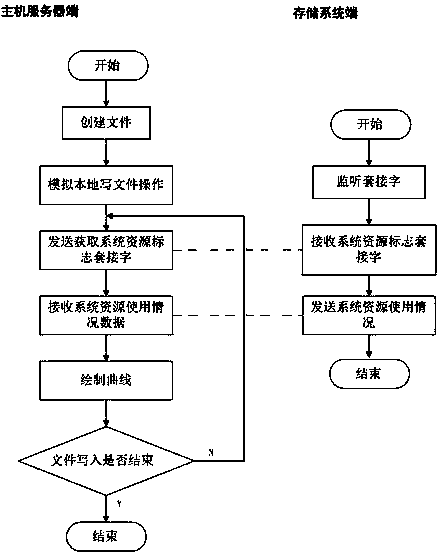
Performance monitoring method of network storage system
InactiveCN103984619AEasy to shareImprove usabilityHardware monitoringService conditionMonitoring methods
The invention provides a performance monitoring method of a network storage system. According to the method, actual file reading and writing are simulated, service conditions of a PCU, service conditions of an internal storage, service conditions of a network and actual io reading and writing speed of the storage system in the process are monitored, and finally the information is presented to a user in a curve graph mode. In the method, the functions of large file establishing, file writing simulation, file reading simulation and curve graph downloading are achieved, and the CUP usage rate, the internal storage usage amount, the network usage rate and a disc reading / writing speed curve graph of the storage system can be displayed. According to practical application, the method provides a new standard for performance evaluation of the storage system, the method is more similar to actual user experience and simple, convenient and practical to operate, a storage designer can find out the bottleneck limiting the performance of the storage system conveniently, and a more comprehensive and more visual storage system performance evaluation method is provided for storage users.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Application servo-actuated intelligent floe control method
ActiveCN106385386AGuaranteed reliabilityTake advantage ofData switching networksFixed positionDistributed computing
The invention relates to a flow control technology, especially to an application servo-actuated intelligent floe control method. Via the method, different applications are distinguished effectively, and dynamic flow control is carried out on different application data according to the network utilization condition. The method comprises the following steps that A) different application data is sent to a client, and identification fields are added to fixed positions in the head portion of a data packet for identification; B) an network access end classifies the application data by identifying the identification fields, and the application data of different classes is placed into data queues of different priority levels; and C) according to real-time statistical flow information of the applications of different priority levels, the corresponding flow control thresholds are adjusted dynamically. The method is suitable for flow control for different applications.
Owner:成都飞鱼星科技股份有限公司
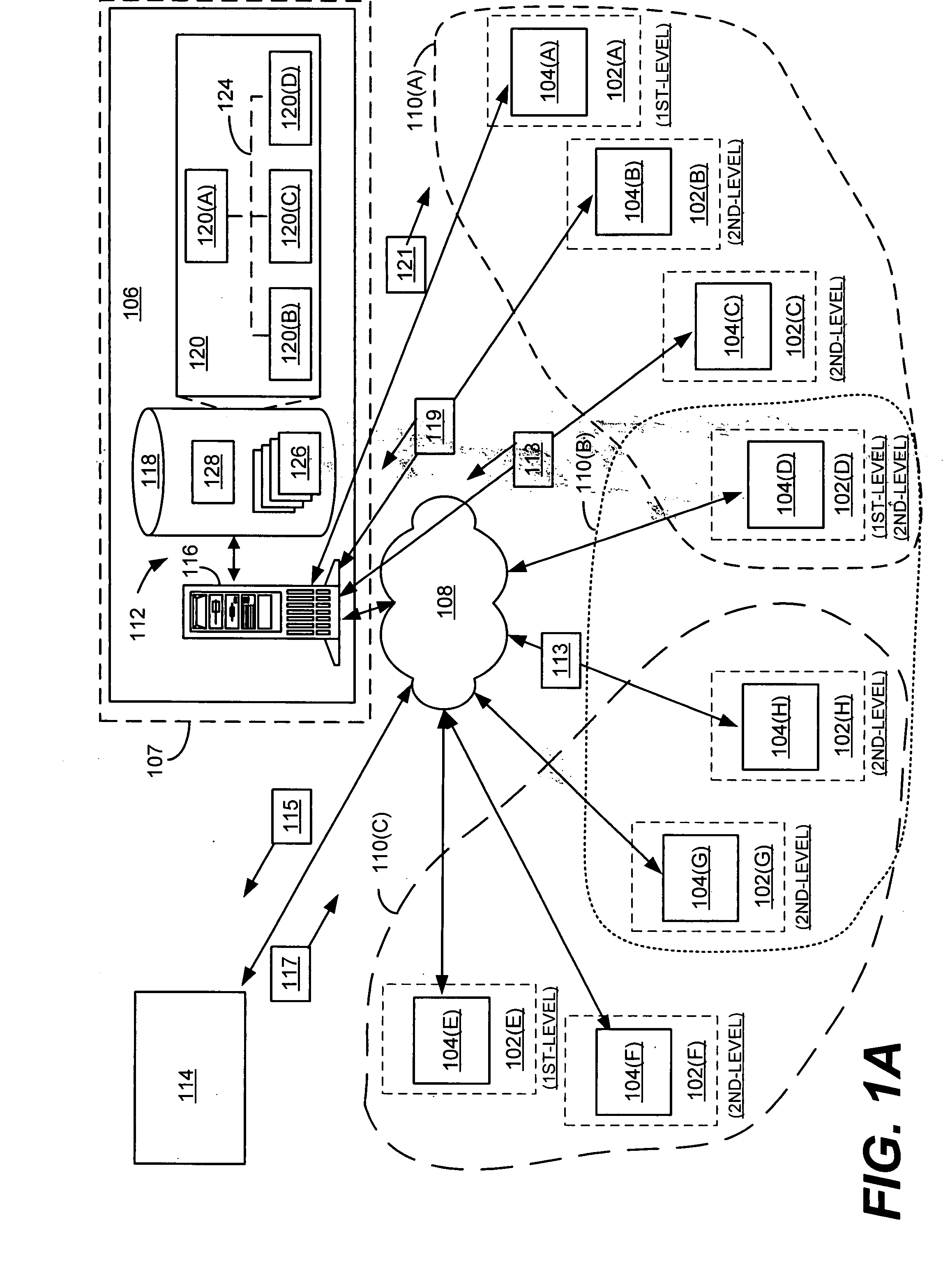
Network usage monitoring device and associated method
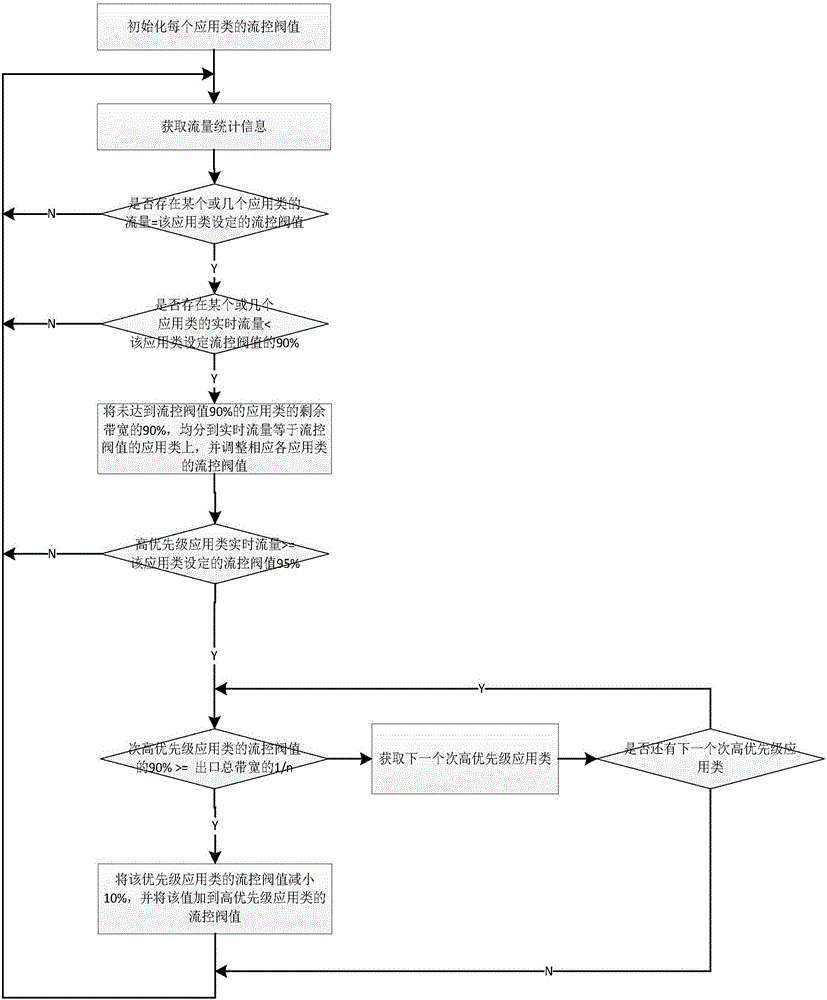
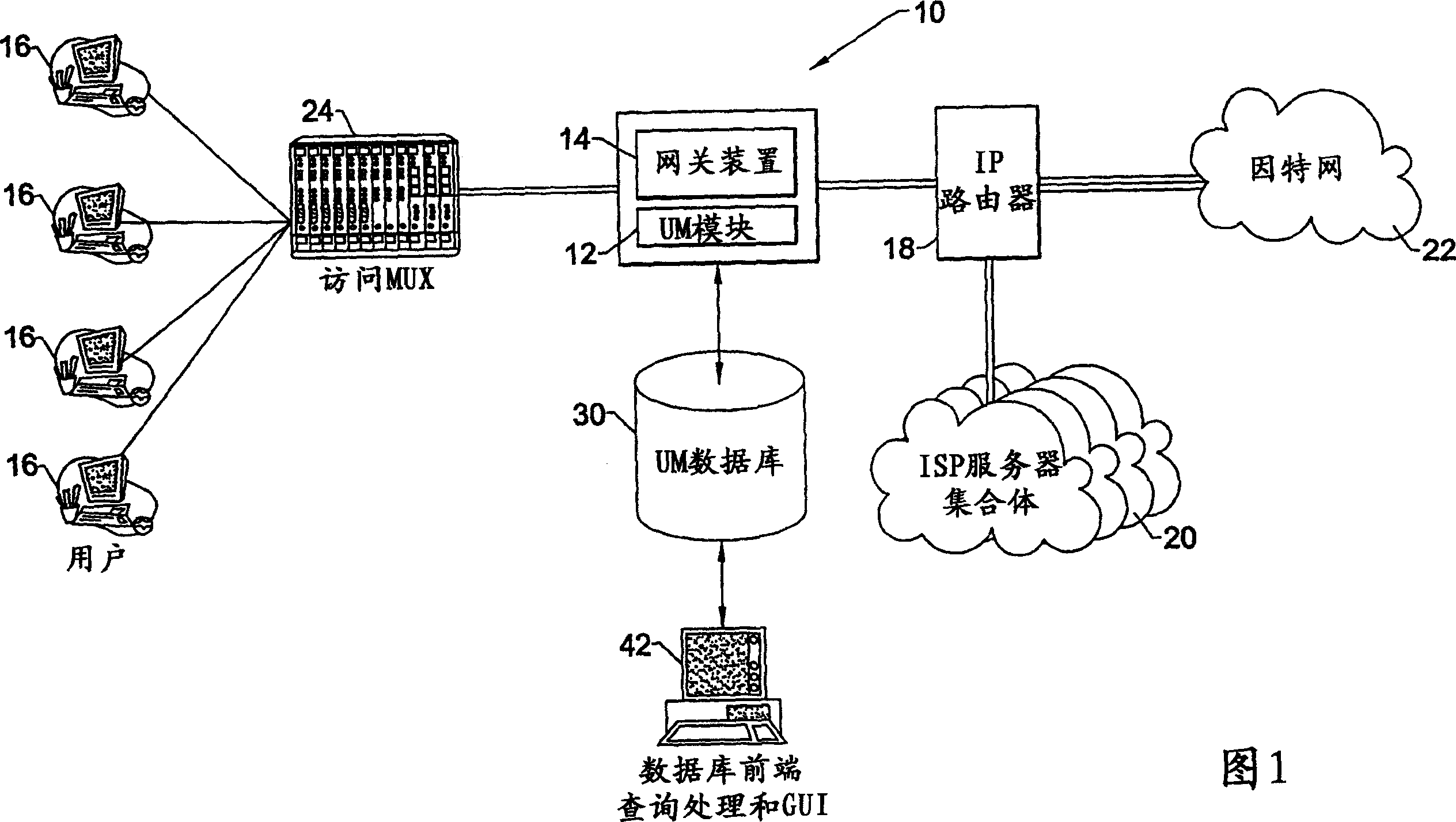
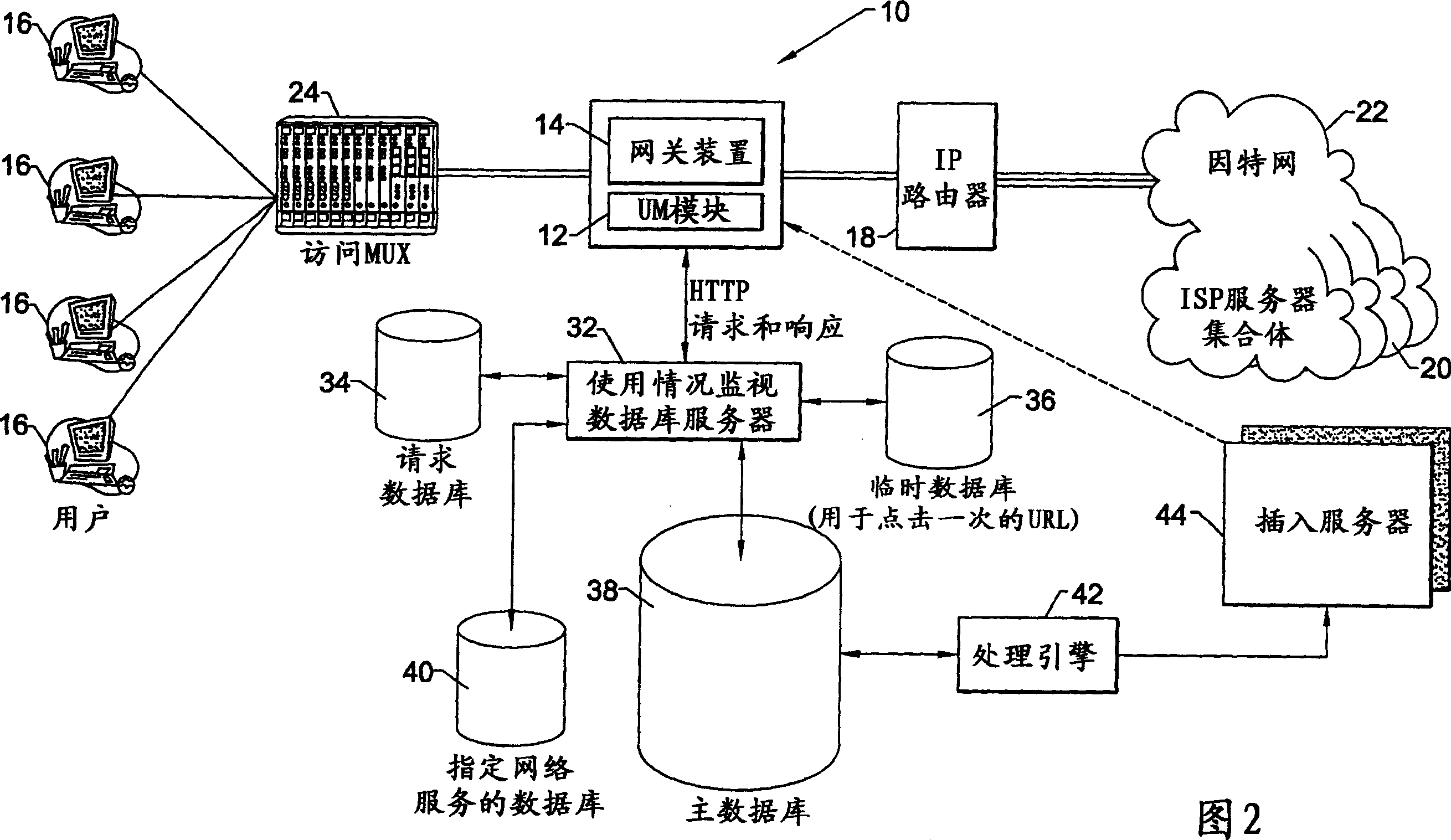
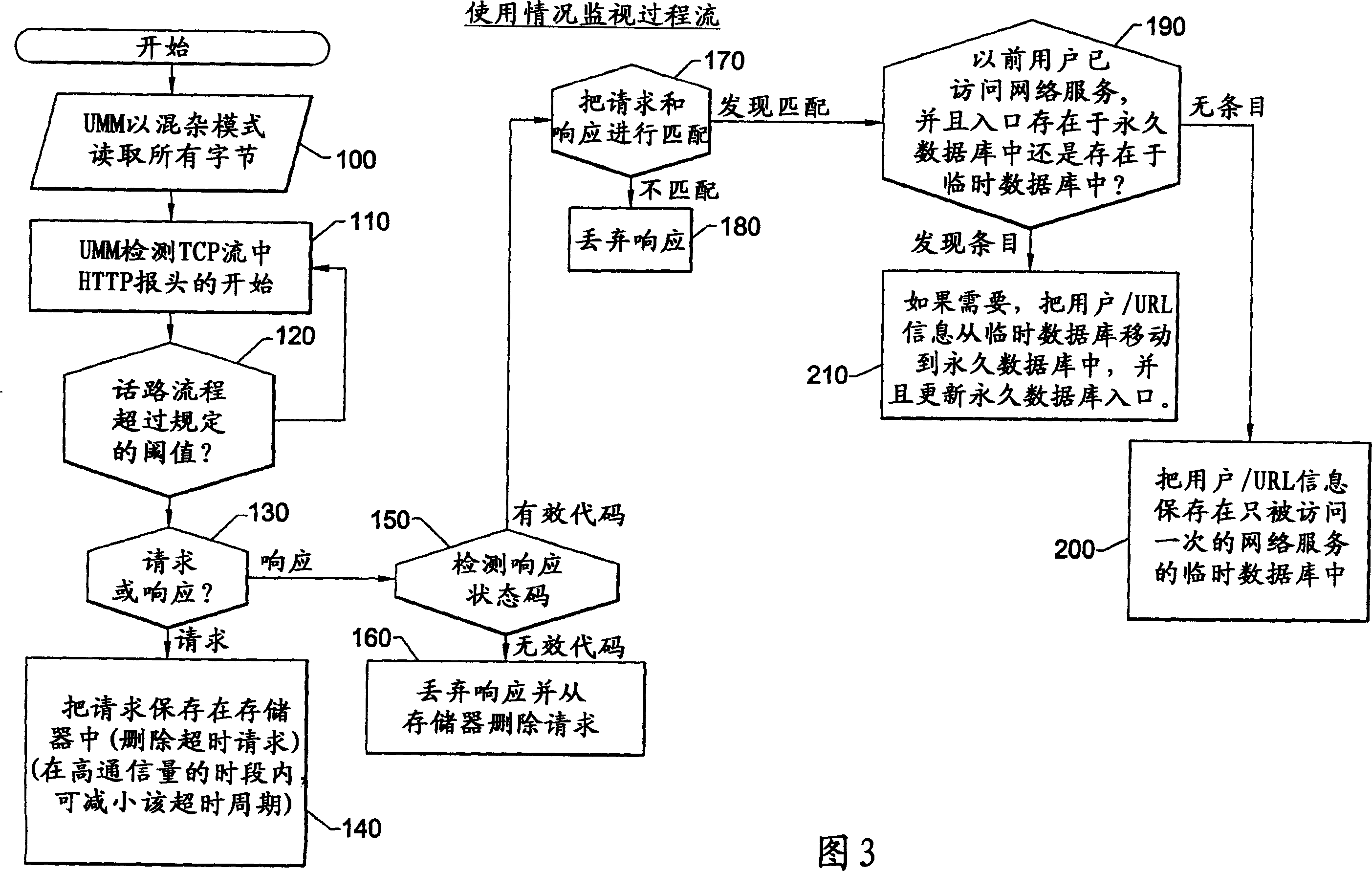
InactiveCN1433615AMonitor querySimplify investigationData switching networksElectric digital data processingNetwork interface deviceComputer module
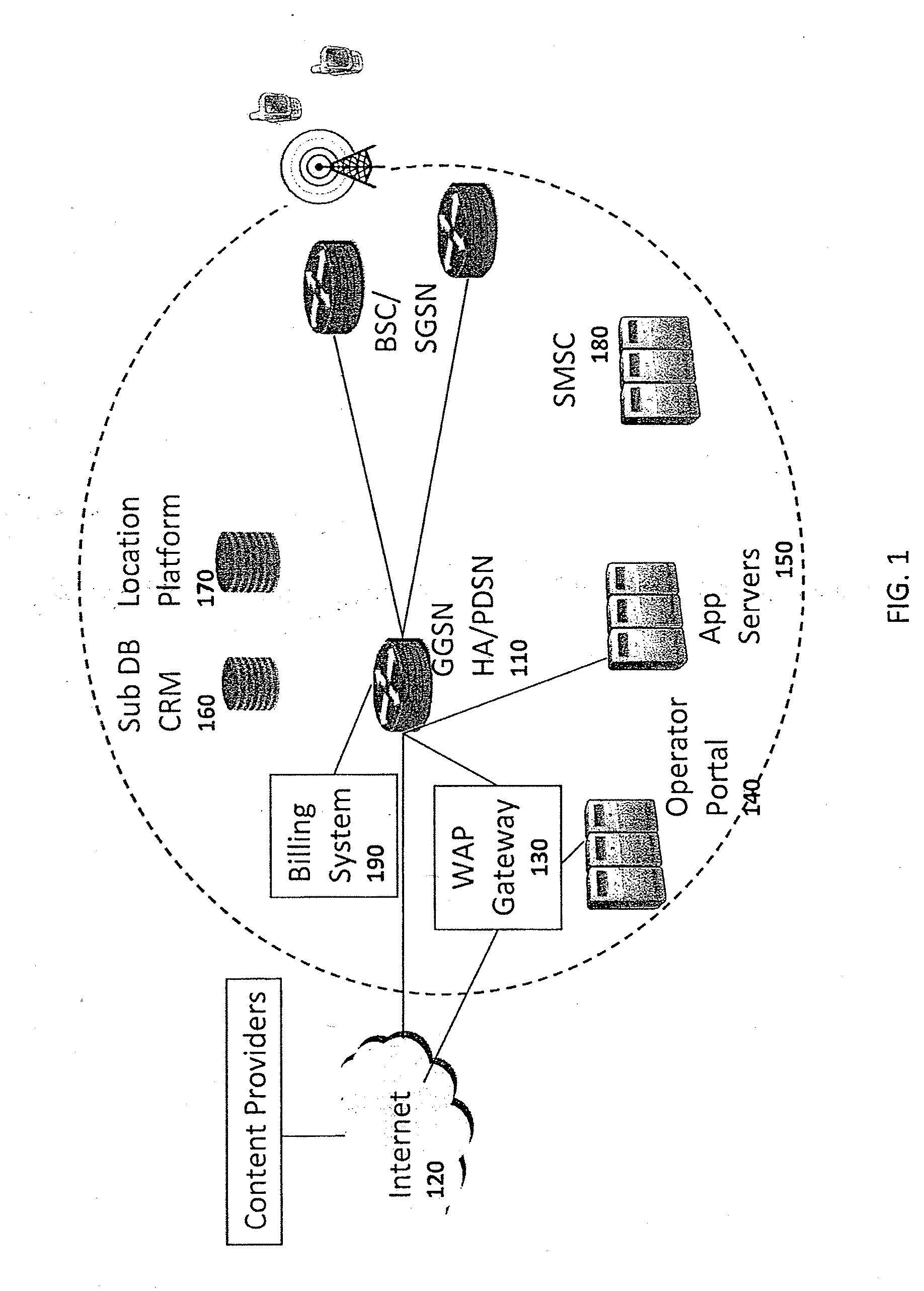
The present invention provides a network usage monitoring module is provided for monitoring network usage at a network access point, i.e. network traffic aggregation point, typically at a gateway device or a similar network interface device. As such, the network usage monitoring module can monitor the usage of a number of network users who are attempting to access various network services provided via the gateway device. Thus, the usage information collected by the usage monitoring module is considerably more robust than that offered by conventional monitoring techniques. As such, the information is considerably more valuable to network service providers, network users, network beneficiaries and the like. In addition, the usage monitoring method and apparatus offers a number of particular features to improve the monitoring process as well as the value of the usage information that is collected.
Owner:NOMADIX INC
End-to-End Content Delivery Network Incorporating Independently Operated Transparent Caches and Proxy Caches
ActiveUS20170344968A1Accurately and comprehensively track and report metricImproves content deliveryDigital data information retrievalDigital computer detailsCache serverEngineering
Some embodiments provide an end-to-end federated CDN solution that assimilates a transparent caching server that is operated by a transparent caching server operator into a CDN that independently operates CDN caching servers. Specifically, the logs from the transparent caching server are assimilated into the CDN by aggregating the logs from the transparent caching server and processing the transparent caching server logs to identify network usage for content of a CDN content provider customer that is delivered by the transparent caching server. The network usage is then combined with the network usage that tracked by the CDN caching servers in order to provide comprehensive report metrics for the content provider customer and to bill the content provider customer for all network usage related to delivering the content provider customer's content irrespective of whether the content was delivered by a transparent caching server or a CDN caching server.
Owner:EDGIO INC
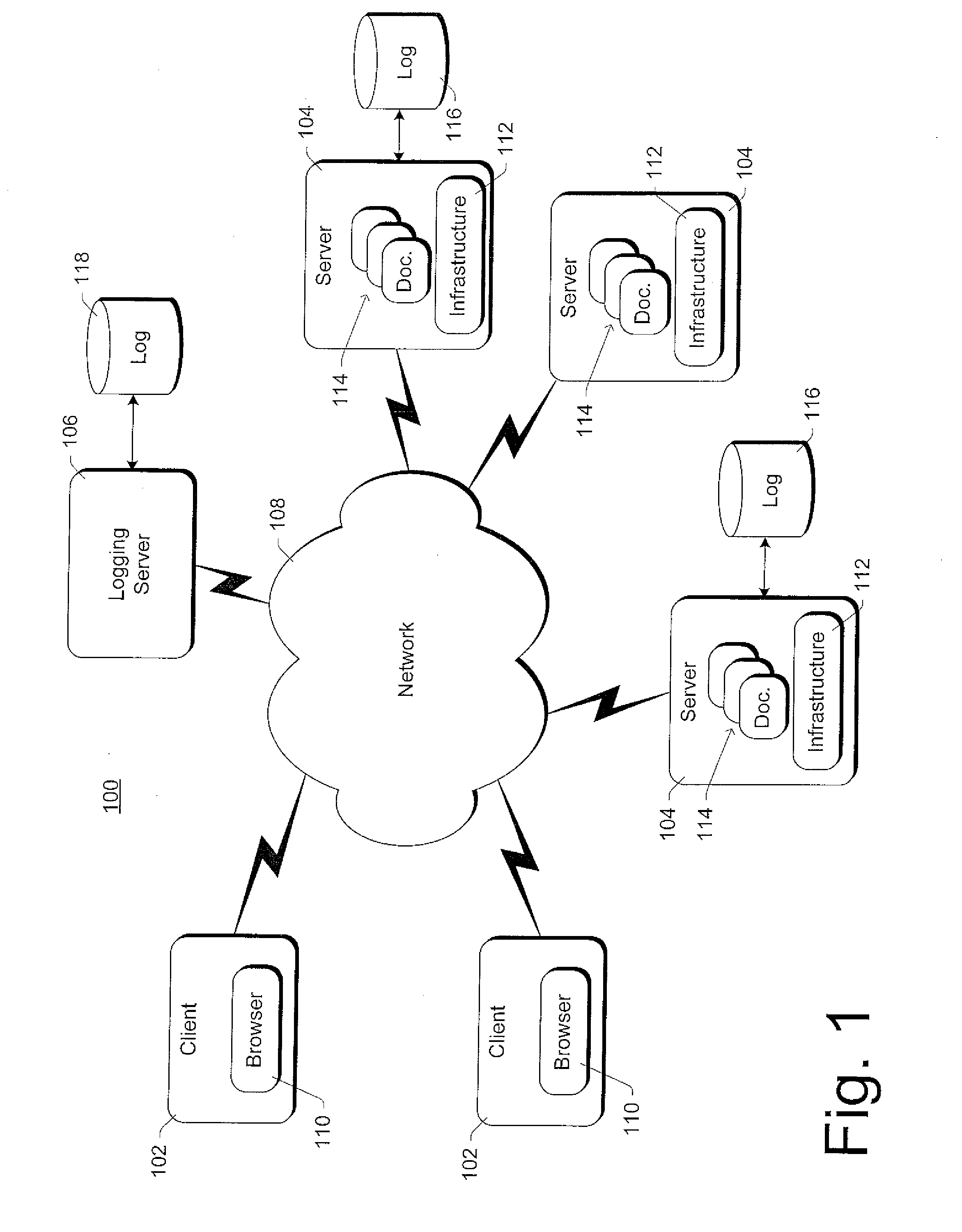
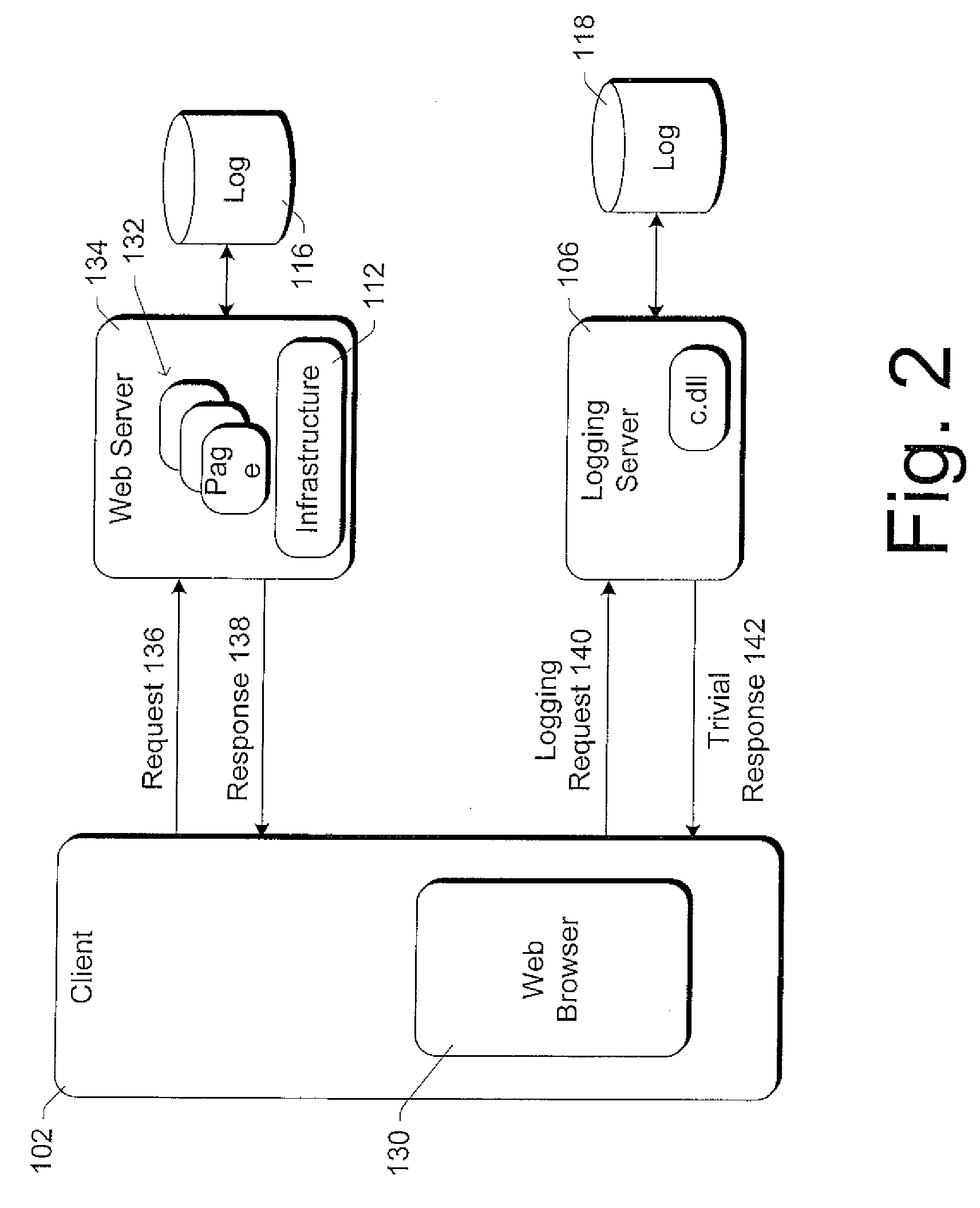
Method and system for providing centralized web usage tracking
Owner:MICROSOFT TECH LICENSING LLC
Methods of processing and segmenting web usage information
A massive amount of information is collected when tracking statistics such as web site usage data. To simplify the analysis of such data, it is advantageous to process and segment the web site usage data. One proposed method of segmenting the data is to create a reverse sorted associative container for each different web section of a web site. Page-views, time-spent, sessions, and other web viewing metrics may be used as keys in the reverse sorted associative container and web viewer identifiers are used as values associated with the page-view value keys. After creating the reverse sorted associative containers, each reverse sorted associative container is segmented on a percentile basis.
Owner:R2 SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com