Method and device for recognizing user access trace
A user and trajectory technology, applied in the Internet field, can solve problems such as the same user ID, increased management costs, and inability to trace historical data, achieving persuasive and accurate statistical results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
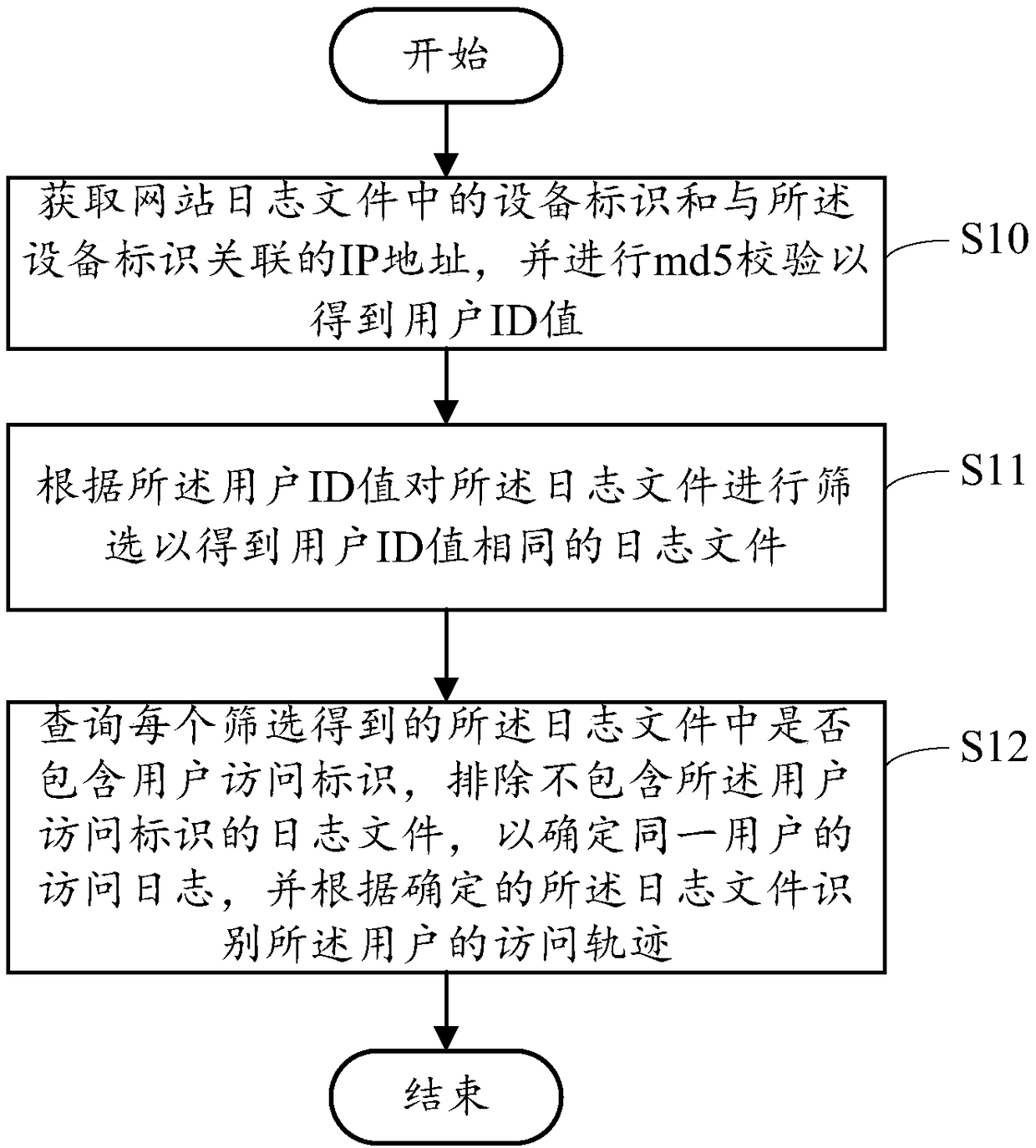
[0019] see figure 1 , is a schematic flowchart of a method for identifying user access traces in an embodiment of the present invention, the method includes:
[0020] Step S10: Obtain the device identifier in the website log file and the IP address associated with the device identifier, and perform md5 verification to obtain the user ID value;
[0021] Wherein, the website log file is the user's log file formed by the web server recording its HTTP log, especially the http_cooki variable when the user accesses the network.
[0022] Taking the nginx server as an example, the settings in the configuration file are as follows:
[0023] log_format super_log`$remote—addr-$server_addr[$time—local]
[0024] $request_method $http—host $request_uri $request_time $status $body bytessent "$http referer" "$http_user_agent" "$http_cookie"';
[0025] Set up in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com